Our world is becoming more impersonal as it becomes more digital-centric. And because we can’t see the person or organization at the other end of an email, social media message or text, it’s easier for scammers to pretend to be something or someone they’re not. This is impersonation fraud, and it’s fast becoming one of the highest earners for cybercriminals. According to the FTC, scammers impersonating businesses and governments made $1.1 billion from their victims in 2023.
Impersonation fraud can take many forms, but with your eyes on the tell-tale signs of a scam, your personal information and hard-earned money will remain under lock and key.
What does impersonation fraud look like?
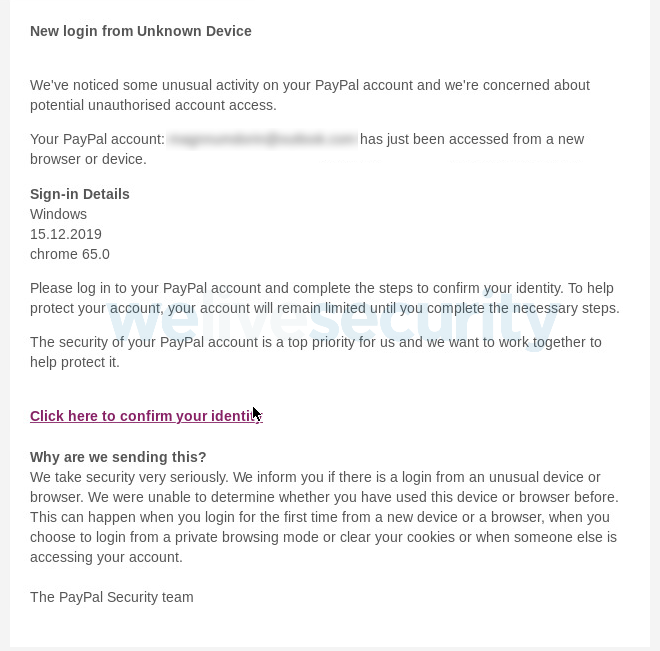
Like most fraud, impersonation scams are designed to get you to send the bad guys money, or personal/financial details which they can either sell on the dark web or use themselves to commit identity fraud. Phishing is perhaps the most obvious flavor of impersonation fraud: a scammer contacting you pretending to be a trusted entity requesting money or information.
But there are other varieties. Fake social media accounts are a growing challenge; used to spread scam links and too-good-to-be-true offers. And fake mobile apps might impersonate legitimate apps to harvest personal info, flood your screen with ads or enroll you in premium-rate services.
Impersonation scams are also evolving. According to the FTC, they increasingly blur channels and techniques, so that “a fake Amazon employee might transfer you to a fake bank or even a fake FBI or FTC employee for fake help.”
How to spot the scammers
Contrary to popular belief, it’s not just the elderly who are at risk from impersonation scams. Research in the UK found that people under 35 are more likely to have been targeted by and fallen for this type of fraud. With that in mind, look out for these warning signs:
- Requests for money: A message on email, text or DM from someone purporting to be a close family member or contact. They’ll request urgent financial assistance due to some excuse such as they’re stranded overseas or needed medical help. Fraudsters can hijack legitimate social media and email accounts to make it seem as if it’s really your friend/family member contacting you.
- Remote access: In tech support fraud, an official from a tech company, telco or other legitimate-seeming organization requires access to your computer for some made-up reason such as it is compromised with malware.
- Access to your account: A police officer or government official contacts you out of the blue claiming money in your account needs to be analyzed as part of an investigation into money laundering, drug smuggling or some other serious crime. They offer to ‘keep it safe’ by moving it elsewhere.
- Pressure: The person on the other end of the phone, email, text or social media channel pressures you to act immediately. They’ll try to panic you into making a decision without thinking – such as sending money to a friend in danger, or transferring urgently to a government official. It’s a classic social engineering technique – sometimes even conducted in person or with a potentially frightening twist courtesy of AI tools that can be co-opted to perpetrate virtual kidnapping scams.
- Fake couriers retrieving money: An official offers to send a courier to come to your home address to pick up cash, cards, valuable items or PINs under all sorts of fake pretexts, such as helping your relative get out of trouble or to resolve a dodgy payment on your bank card.
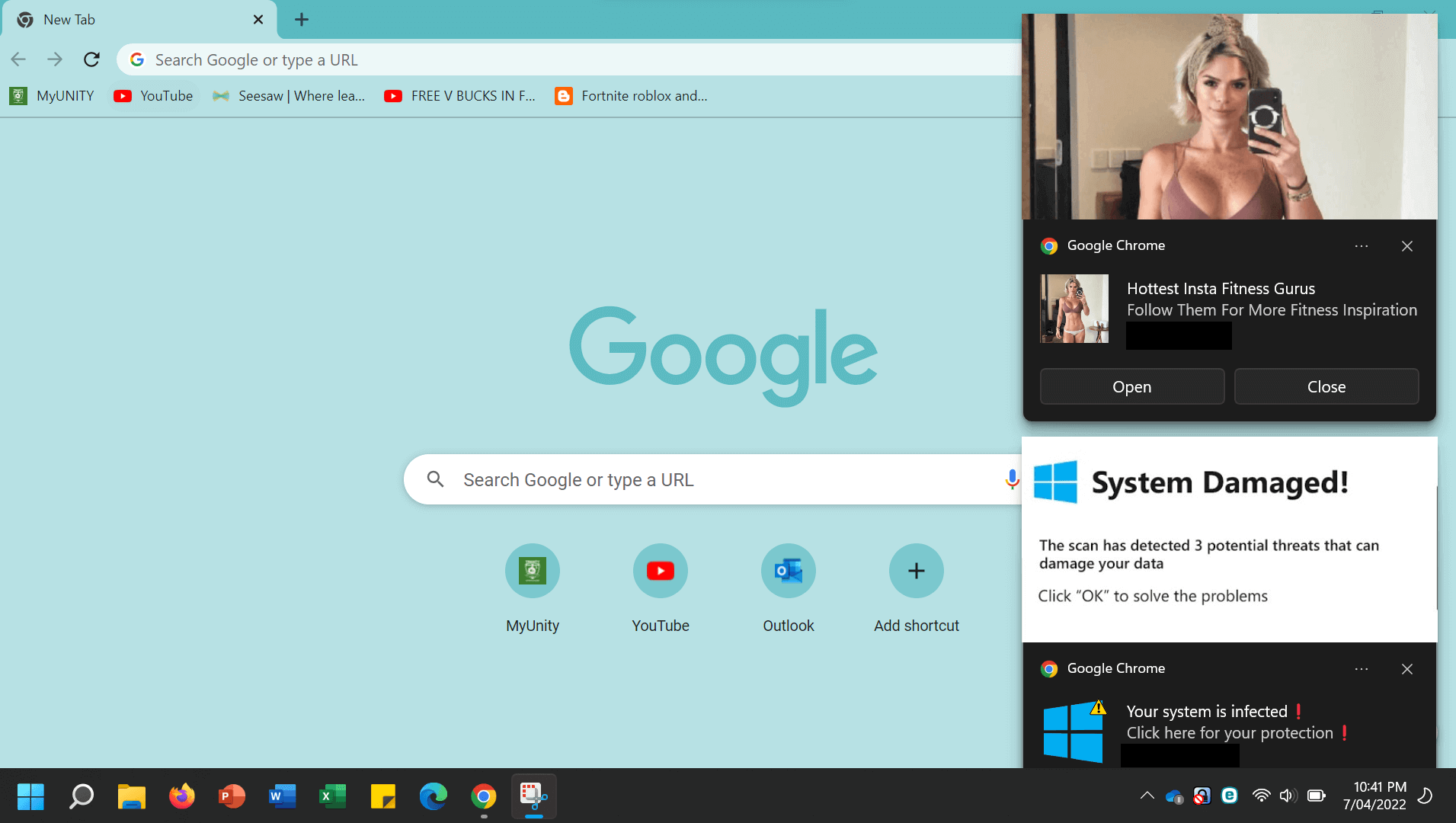
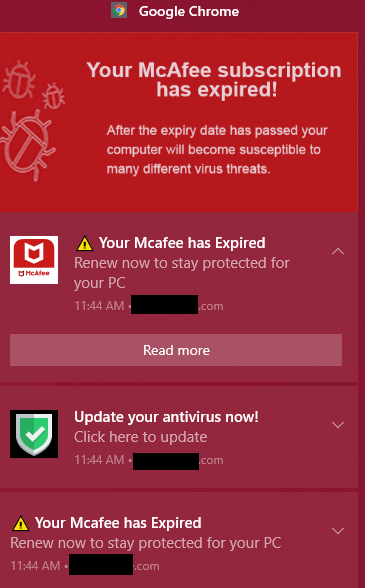
- Account security alerts: These fake notifications often require you to ‘confirm’ your details first – another way for scammers to get hold of your personal and financial information.
- Unusual messages: Phishing emails often contain inconsistencies which mark them out as impersonation fraud. Scammers will try to spoof the display name to impersonate the sender. But by hovering over the name, you can see the masked email address underneath, which may be an unofficial-looking one. Be aware, however, that scammers can also hijack legitimate email accounts and use caller ID spoofing to make it harder to tell the real from the fake.
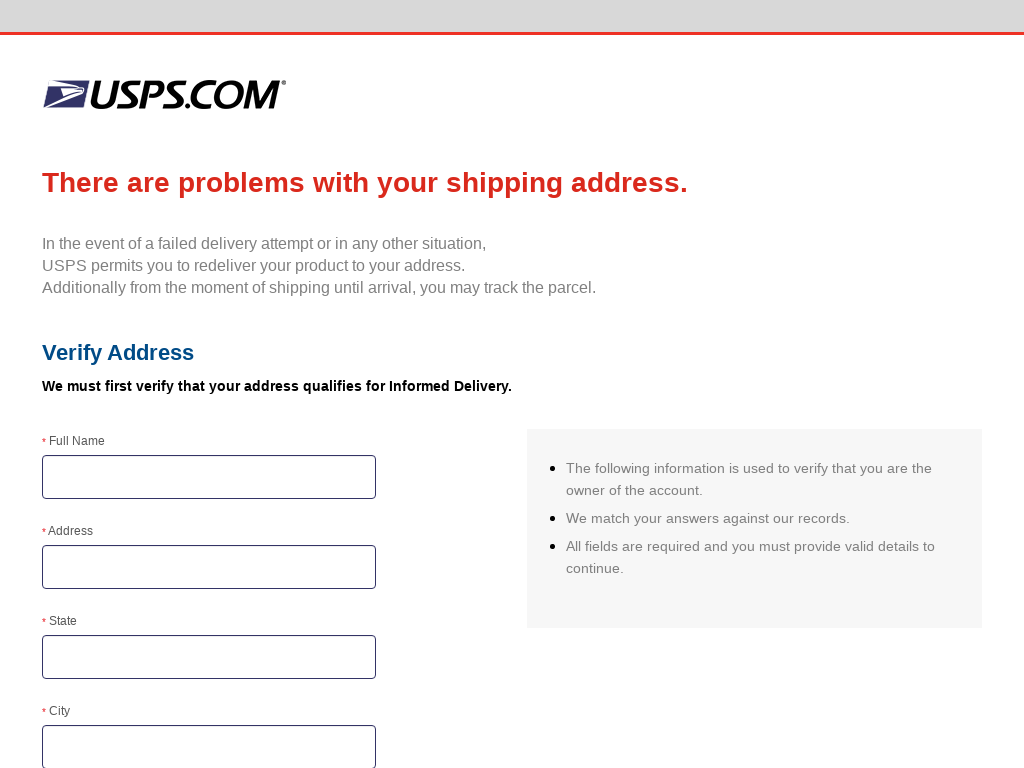
- Fake delivery issues: Legitimate-looking postal/logistics firms demand that you pay a small fee or hand over bank details to enable safe delivery of your non-existent parcel. In other scenarios, fraudsters will pose as a well-known delivery service and alert you of ‘problems’ with your package.
- Gift cards: You’re asked to pay fines or one-off fees by buying high-value items or gift cards. The scammer wants you to do this rather than a bank transfer, as it’s far more difficult to trace.
- Fake subscription renewals: These may require you to connect the scammer to your computer to renew your subscription or process a non-existent refund.
- Fictitious giveaways or discounts: These require you to pay a small ‘fee’ in order to claim them. Needless to say, there is no reward or discount as this is merely a variation on the advance fee fraud.
- Unusual language: Another tell-tale sign of phishing attempts could be poor grammar and spelling or imprecise language in messages – although with fraudsters using generative AI to create their fake messages, this is becoming less common.
Stay alert
Remember, impersonation scams are constantly evolving, so the above is certainly not an exhaustive list. The next evolution in such scams is coming thanks to AI-powered deepfakes, which can mimic the voice or even appearance of a trusted individual. These are already tricking office workers into making big-money corporate fund transfers to accounts under the control of cybercriminals. And the technology is being used to impersonate trusted individuals on social media in order to trick followers into making rash investments. As deepfakes become cheaper and more accessible, they could also be used in smaller scale fraud.
With any impersonation fraud, the key is: be skeptical, slow down, and independently verify they are who they say they are. Do this by reaching out to the organization or individual directly, don’t reply to an email or phone number listed on the initial message. And never hand over money or personal information unless you’ve confirmed the contact is legitimate.








