Back in May 2023, I wrote the blogpost You may not care where you download software from, but malware does as a call to arms, warning about the risks of running software downloaded from so-called “trusted sources” of pirated software. Of course, those files were anything but trustworthy and contained malware, such as ransomware or infostealers, specifically targeted at that demographic. My hope was that by educating the public about the risks involved, people would learn about how to avoid such dangerous apps and seek safer alternatives.
In the year or so since that blogpost, things haven’t gotten much better: From reading the ESET Threat Report for the first half of 2024, we have seen a marked increase in the number of information stealers being detected. And this time, they are not just embedded in pirated Windows games, cracks, and cheating tools, but also impersonating generative AI tools. Nor are they limited to Windows, either. The GoldDigger family of information-stealing malware runs on Android OS, and the long-running Ebury malware campaign has been active in stealing credit cards, cryptocurrencies, and SSH credentials for over a decade on UNIX-like operating systems.
Looking at infostealer detections over a two-year period, from August 2022 to August 2024, shows they remained active throughout this period, although there were noticeable drops in activity around December and January of each year.
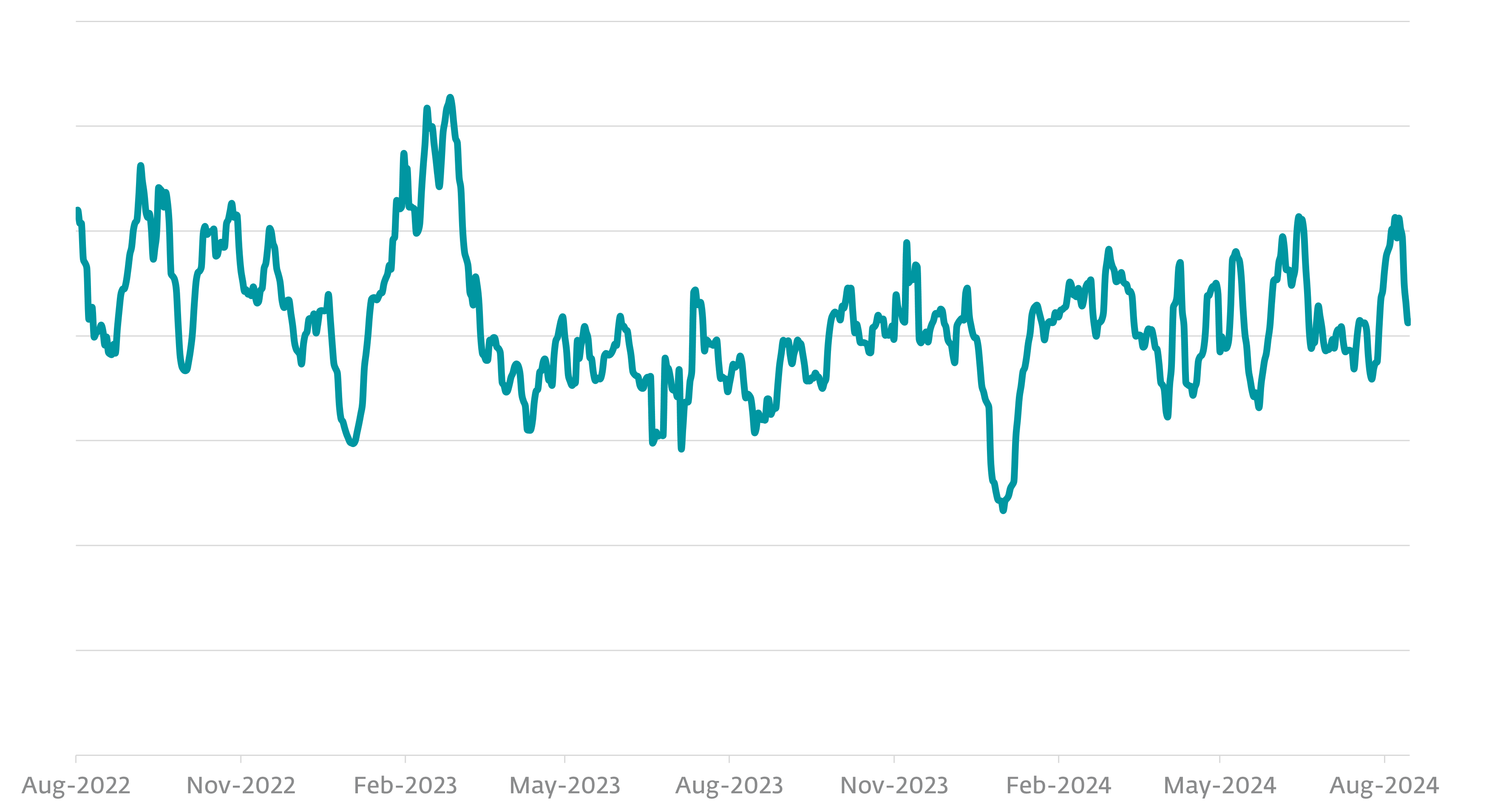
We are uncertain of the exact reason for this, but speculate that it may be due to decreased computer usage by the victims or their attackers taking a break for the holidays, which has become common as individual criminal hackers have morphed into organized criminal enterprises, resembling something like businesses.
While ESET recognizes many families of infostealers, the top ten account for just over 56% of those detected by ESET, with Agent Tesla at the top, with 16.2%.
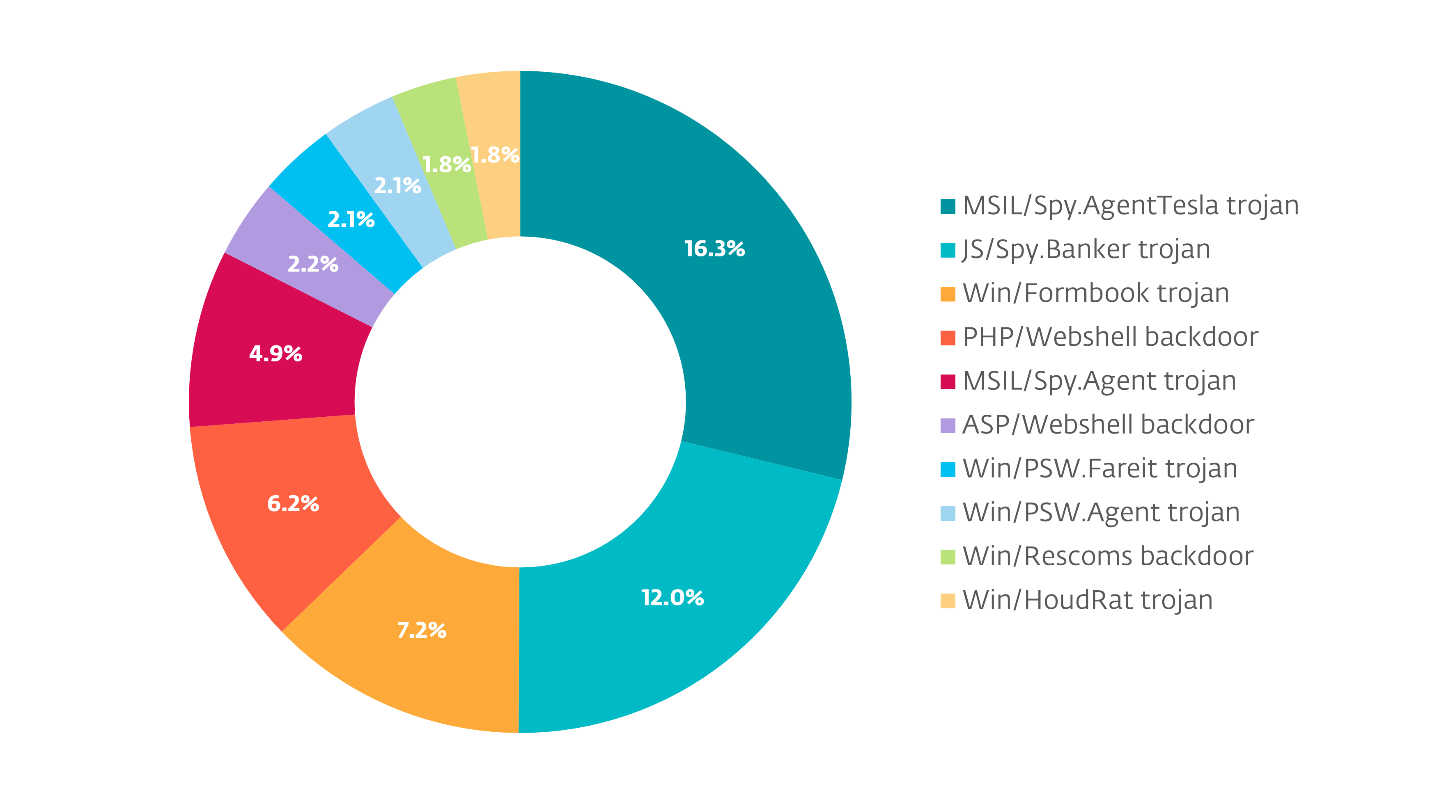
One thing to keep in mind is that while most of these detections are for Windows-based malware, there are information stealers that are web based as well. Although they had lower encounter rates, it is possible that they were able to successfully steal information from people not running ESET software, so their impact may be greater.
Keeping in mind that these statistics are derived from ESET telemetry data, it is possible that other security companies’ data may show different results. This is not due to any one being better than another but the result of factors such as classifying threats differently, having different customer bases with very different risk profiles, usage under different circumstances, and others.
All of which means we can all report different encounter rates for various kinds of malware, such as information stealers.
One of the things I was curious about was whether ESET’s data was similar to that of other security companies. As one example, in their malware trends report for the second quarter of 2024, sandbox vendor ANY.RUN noted that information stealers dropped from first place to fourth place from the preceding quarter. Now, this does not mean that there is any difference in data quality between ESET and ANY.RUN. There is a broad ecosystem of security tools out there, and with each company’s tools used in quite diverse ways, these types of variances in reporting are to be expected.
Information stealing for fun but mostly profit
ESET classifies information stealers under their own separate threat category of Infostealer. Originally, they were categorized under more general names such as Agent or Trojan until the volume of programs engaging in information-stealing activity increased to the point that it made sense to cluster them under their own nom de plume. Other security software developers may classify them more broadly as remote access trojans or spyware, which is perfectly acceptable, too. The point of detecting malware is to prevent it first and foremost. The naming of those threats and the taxonomies under which they are classified is typically unimportant outside of research activities or marketing activities in response to a mass malware outbreak, such as WannaCryptor.
So, with all of that in mind, what exactly is an information stealer, and what happens when you run one?
As the name implies, this type of malware steals any information it can find on your computer that its operator considers of value. This consists not just of usernames and passwords for various websites accessed via the web browsers installed on your PC, but also those for applications. Game accounts can be stolen, looted of valuable items, used to make gift purchases, or resold in their entirety. Streaming media can be resold, as can email and social media accounts. As an “added bonus”, the latter can use your account to entice online friends into downloading and running the information stealer, becoming new victims to it, and having its puppeteers spread it from those accounts as well, ad infinitum.
It’s not just usernames and passwords that get stolen, either. Wallets for cryptocurrencies can be especially lucrative, as can account session tokens. For that matter, the information stealer may even take a screenshot of the desktop at the time it was run so that its operator can sell the screenshot and email address to other criminals for sending scam extortion emails later.
In case you’re wondering what a session token is, some websites and apps have a “remember this device” feature that allows you to access the service without having to log back in or enter your second factor of authentication. This is done by storing a session token on your device. One can think of it as being a specialized form of web browser cookie that tells the website being visited (or service being accessed through an app) that the user has been successfully authenticated and to allow them in. Criminals look for and target these, because they allow them to log into an account, bypassing the normal checks. As far as the service is concerned, it just looks like you’re accessing it from your previously authorized device.
The business of information stealing
Information stealers are a type of malware that is often sold as a service, so what exactly it did while on a computer is going to vary a bit based on what the criminal who purchased it wanted it to look for and steal. Often, they remove themselves after they have finished stealing information in order to make it harder to determine what happened and when. If the victim is feeling so overwhelmed by the invasion of their privacy that they delay taking immediate action, it gives the criminals more time to use or fence the information stolen from the computer.
But since information stealers are crimeware-as-a-service, it is also possible that it was used to install additional malware on the system in order to maintain access to it, just in case the criminals decide to come back to the computer in the future and see if there is anything new to steal from it.
Recovery from an information-stealing attack
Unless the computer’s drive(s) need to be preserved as evidence, the first thing to do would be to wipe the computer’s drive and reinstall its operating system. That assumes the computer was backed up regularly, so erasing its drive(s) and losing all the information stored on it (them?) isn’t a big deal, since it is already backed up elsewhere. If that’s not the case, and there is valuable, important data stored on the computer, it may make sense to remove its drive(s), replace it with a blank one, and perform a clean installation of the operating system to that. Getting some kind of external case to put the drive in later to copy the non-backed up data off of it will be important as well.
After wiping the computer, installing Windows, installing security software, and getting all of that updated, one can then start accessing the internet using the computer to change the passwords for all of the online accounts that were ever accessed from it.
Each password should be changed to something that is not only complex but also different for each service. Simply replacing Summer2024 with Autumn2024, or P@ssW0rd123 with P@ssW0rd1234 is something an attacker could easily guess after reviewing all of your stolen passwords. That way, if one is lost (or guessed), the attacker won’t be able to make guesses about what the other passwords might be. Some of ESET’s subscriptions come with a password manager, or your web browser may have one that’s built into it. ESET also offers a free tool for generating complex passwords.
Enabling two-factor authentication (sometimes referred to as multi-factor authentication) for all of the accounts that support it will make it exponentially harder for attackers to compromise in the future, even if they know the passwords to them.
When changing passwords, it is important to make them unique or different from any previously used passwords: if the new passwords are similar enough to the old passwords, a criminal who has all the old passwords will very likely be able to make all sorts of educated guesses about what the new passwords might be for the various services. So, make sure you’re not cycling through similar-sounding or previous passwords.
As mentioned earlier, it’s not just passwords you have to change, but session tokens as well. These are targeted by information-stealing malware because they allow criminals to impersonate you by hijacking one of your previously authorized sessions. Some websites and apps have the ability to show you other active sessions or devices on which you accessed them, but also to log out or disconnect those other active sessions. Do that as well.
At the risk of sounding somewhat repetitive, it is important to do this for every single online service. Even ones that are no longer regularly used. This is extremely important for any financial websites, online stores, social media, and email accounts, since these are among the most valuable to criminals. If there were any reused passwords or even similar themes between them, the criminals who stole the credentials are going to try spraying them against all the common stores, banks, and services.
Two of the underlooked activities when recovering from an information-stealing attack are to (1) file a report with the police; and (2) notify your financial institutions. Making law enforcement aware that a crime has occurred may be helpful in recovering stolen accounts. In the case of financial institutions, having a police report to share with them can increase the chances of getting back stolen funds. Even if you are not in the United States, filing a report with the Internet Crime Compliant Center (IC3) can help law enforcement agencies identify and track information-stealing criminals.
Defensive strategies
Dealing with the aftermath of an information stealer attack is a long and painful process that can drag on for days, weeks, or even months. While we have presented the basics needed to start the process of recovering from such attacks, information stealers are neither the sole nor the most widely occurring method of having one’s accounts stolen. The locks and keys for our online identities are usernames (which are often email addresses) and passwords, and data breaches involving these have become increasingly common.
Having identify theft protection can help mitigate some of the worst aspects of this kind of violation, but like having an insurance policy (or backups of their computer’s data), it is something a lot of people do not consider until after something bad happens to them.
One excellent source of finding out whether your email address has been involved in a data breach is Troy Hunt’s Have I Been Pwned (HIBP) website, which constantly receives updated information about data breaches that have occurred all around the world and will notify you if your email address has been found in any of them. While that does not necessarily mean your email account itself is in any danger, it could mean the account could be on the service from which it was leaked. The HIBP service is free for individuals.
Data breaches can be difficult to avoid, since they are the result of securing issues involving third parties. Information stealers, on the other hand, tend to be the result of engaging in risky behavior. Here are some steps you can take to reduce the impact and recover more quickly from these types of attacks:
- Use long and different passwords for each website and application. A password manager can greatly ease this complex process for you.
- Enable two-factor authentication for all services that allow it. Hardware tokens or smartphone apps are more secure than email or SMS notification, as an attacker may have access to your email or smartphone.
- Some services let you see all the devices logged into your account. Periodically review these and disable ones that you do not recognize or have not been active for a while.
- Use a data breach monitoring or an identity theft protection service to notify you of compromised accounts.
- Do not use pirated software, cracks, keygens or similar tools no matter how trustworthy you consider them. It is trivial to make these appear safe and trusted when criminals have stolen the accounts rating them.
- Keep your operating system and applications up to date with the latest fully patched versions.
- Use the latest version of security software from trusted, established vendors.
- Keep up to date on the latest security trends, issues and news from your favorite information security blogs.
Following these can reduce the chances of becoming a victim, or help you recover more quickly in the event that you have become one.








