Starting today, Twitter is disabling SMS-based two-factor authentication (2FA) for all but paying users following a decision that, not unlike other recent moves by the social media giant, has been met with controversy that has reverberated far beyond the Twitterverse.
“While historically a popular form of 2FA, unfortunately, we have seen phone-number based 2FA be used – and abused – by bad actors,” reads Twitter’s statement announcing the change in the middle of February.
Over the years, the company and many of its users – including one-time Twitter CEO Jack Dorsey – have learned the hard way that phone numbers don’t make for good identifiers and text messages are vulnerable to hijacking.
Fast forward (almost) to the present and the platform’s current CEO Elon Musk had this to say on Twitter's dropping 2FA: “Twitter is getting scammed by phone companies for $60M/year of fake 2FA SMS messages.”
Before you say, ‘good riddance to SMS 2FA’, however, consider that using any 2FA method is far better than relying on your password alone. This then begs the question: have you prepared for the demise of free SMS 2FA so that you avoid putting your Twitter account at heightened risk for hacking? In recent weeks, Twitter has been nudging users away and to another two-step login method, but if those haven’t done the job, now is really the time to act.
Here’s how you can enhance the security of your Twitter account without SMS 2FA – and keep it more secure than ever before. Even if you belong to the 0.2 percent of Twitter users who are paying for subscriptions to the platform, keep reading – much of this advice may actually come in handy for you, too.
How 2FA authentication works – and how it fails
As you probably know by now, 2FA adds a valuable layer of protection to your account and is particularly useful if your password is stolen. It’s unfortunate, then, that only 2.6 percent of active Twitter accounts had at least one 2FA method enabled in the second half of 2021 (up from an even more meager 2.3 percent a year prior). Of those, three-fourths used text messages as their second authentication factor.
This form of 2FA – which was first developed in the mid-1990s (back then, they used pagers for that) – has become by far the most popular 2FA method across email and social media platforms, online stores and banks.
Obviously just waiting for a text with a code and entering the code after inputting your password is a convenient way to enhance your account security. But while any second factor is far better than none, 2FA over text messages is long known to be susceptible to various attacks as incoming texts are unencrypted and can be intercepted, read or redirected by determined attackers with relative ease. Back in 2016, the United States’ National Institute of Standards and Technology (NIST) called for SMS-based 2FA to be phased out.
Recent years have seen a bevy of reports of attackers gaining access to people’s online accounts following, for example, successful SIM swap scams. These scams involve criminals tricking phone carriers into porting their target’s phone number to a device under their control. From there, they can break into the victims’ banking, social media and other accounts that use the same phone number for 2FA. None other than former Twitter head Jack Dorsey fell victim to this attack in 2019.
RELATED READING: 7 steps to staying safe and secure on Twitter
Over the years, security researchers, including those at ESET, have found many examples of malware that is capable of circumventing people’s 2FA protections.
For example, way back in 2016, ESET researchers spotted an Android banking trojan that was stealing login credentials for 20 mobile banking apps. It bypassed SMS codes, the malware passed all received text messages on to the criminals. Three years later, ESET discovered malicious apps that leveraged novel techniques to read notifications with one-time passwords (OTPs) popping up on the device’s screen.
Twitter’s own 2FA protections and security posture came under scrutiny in 2020 when a vishing attack on its staff led to the hijacking of some 130 accounts belonging to prominent figures. In the hack, the attackers subverted Twitter’s 2FA protections and used the accounts of Barack Obama, Elon Musk and Bill Gates and others to peddle a Bitcoin scam.
To perpetrate the hack, criminals mimicked Twitter’s legitimate VPN website where employees enter their credentials. As soon as attackers entered login credentials into the real Twitter VPN and waited for employees to receive one-time passwords. Once the victims filled in the password in the phony VPN, the hackers were in.
So, what are your 2FA options on Twitter now?
There are two other main types of 2FA authentication that Twitter supports and that are more secure than text messages.
First, you can use an on-device authenticator app such as Microsoft Authenticator or Google Authenticator, which provides solid security and is more flexible than a hardware key (more on that later).
Authenticator apps generate a one-time code that you use to confirm your identity when logging into a website or app. This might not sound too different from SMS 2FA authentication, but the app’s advantage is that instead of having a code sent to you via a text message, the code appears in the app and is linked directly to the device, rather than to your phone number.
As a corollary, app-based authentication significantly complicates things for anyone who wants to read or steal your code. (Malware that can steal authenticator codes isn’t unheard of, however.)
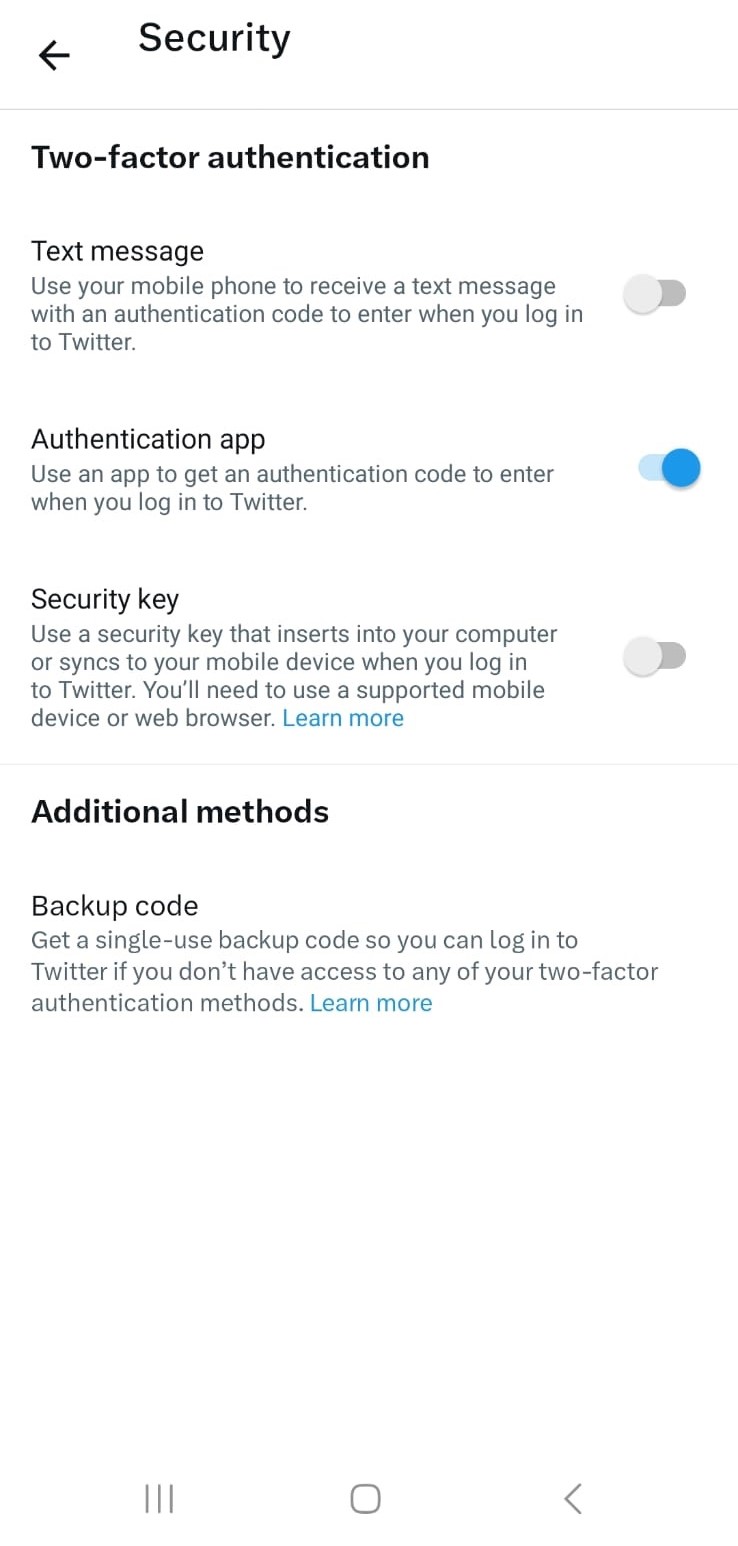
Twitter app 2FA settings before the change
If you want to raise your security game further still, consider getting a hardware security key that you connect via USB, NFC or Bluetooth. Physical keys provide a high level of security, especially because the codes cannot be intercepted or redirected. In order to break into your account, criminals would have to steal the key as well as get ahold of your login credentials.
One possible downside is that you have to carry the key every time you want to log in. Moreover, currently available keys are not universally supported by all devices and platforms. Also, be prepared for prices starting at around US$25. More advanced versions, such as those with fingerprint recognition, may set you back for more than US$100.
What else can you do to improve your Twitter security?
While switching away from SMS-borne 2FA, make sure to review your account security and privacy settings. Among other things, set a strong and unique password (if you don’t use one already) and consider taking these steps to staying safe while using the platform.
And if you already are, or plan to become, a Twitter Blue subscriber, you’re clearly best off ditching SMS 2FA in favor of an authenticator app or a hardware key.
FURTHER READING:
Mastodon vs. Twitter: Know the differences





