The ability to confirm your identity using your fingerprint or face is something we have already become accustomed to. Most of us carry a piece of this technology in our pockets: Our phones are able to recognize not only our facial features and fingerprints, but also our voices, sleep patterns, and heart and respiratory rates.
As biometric identification becomes more common and reliable, it is also increasingly used as a default authentication technology. Chances are, you’re already using your fingerprint or face to unlock your phone, open the door of and start your car, or to manage your bank account. But are we ready to give away all our unique biometric traits in exchange for (a promise of) better security?
In this article, we’ll look at some of the most established types of biometric authentication and examine the pros and cons of this ubiquitous technology.
What are the most common types of biometric authentication?
1. Fingerprint recognition
Many countries have been using fingerprints on our ID cards and when applying for travel visas, and authorities have long been used (fingerprints and other) biometric features to identify criminals and solve crimes. Fingerprints have been used for centuries. But it was when Apple incorporated a fingerprint sensor into its iPhone 5S in 2013 that this technology first became widely used.
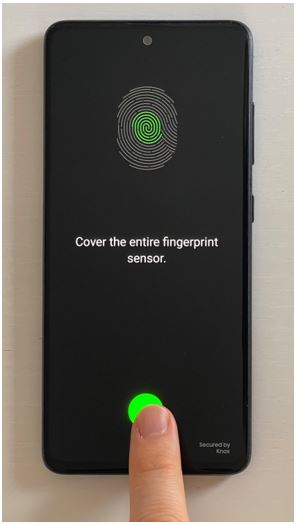
Figure 1. Fingerprint authentication in an iPhone
Over the years, these technology has developed from the physical iPhone’s Home Button with integrated capacitive sensor capable of generating electric charge when in contact with the fingerprint ridges to map the user’s finger and recognize it.
More recently, however, it’s on Android phones that fingerprint sensors have been thriving. Different brand have different approaches for their models, using similar capacitive sensors, under-the-screen optical sensors that use light to create images on the fingerprint or, more recently, ultrasound sensors that bounce a pulse of inaudible sound against the finger to create a complex 3D image.
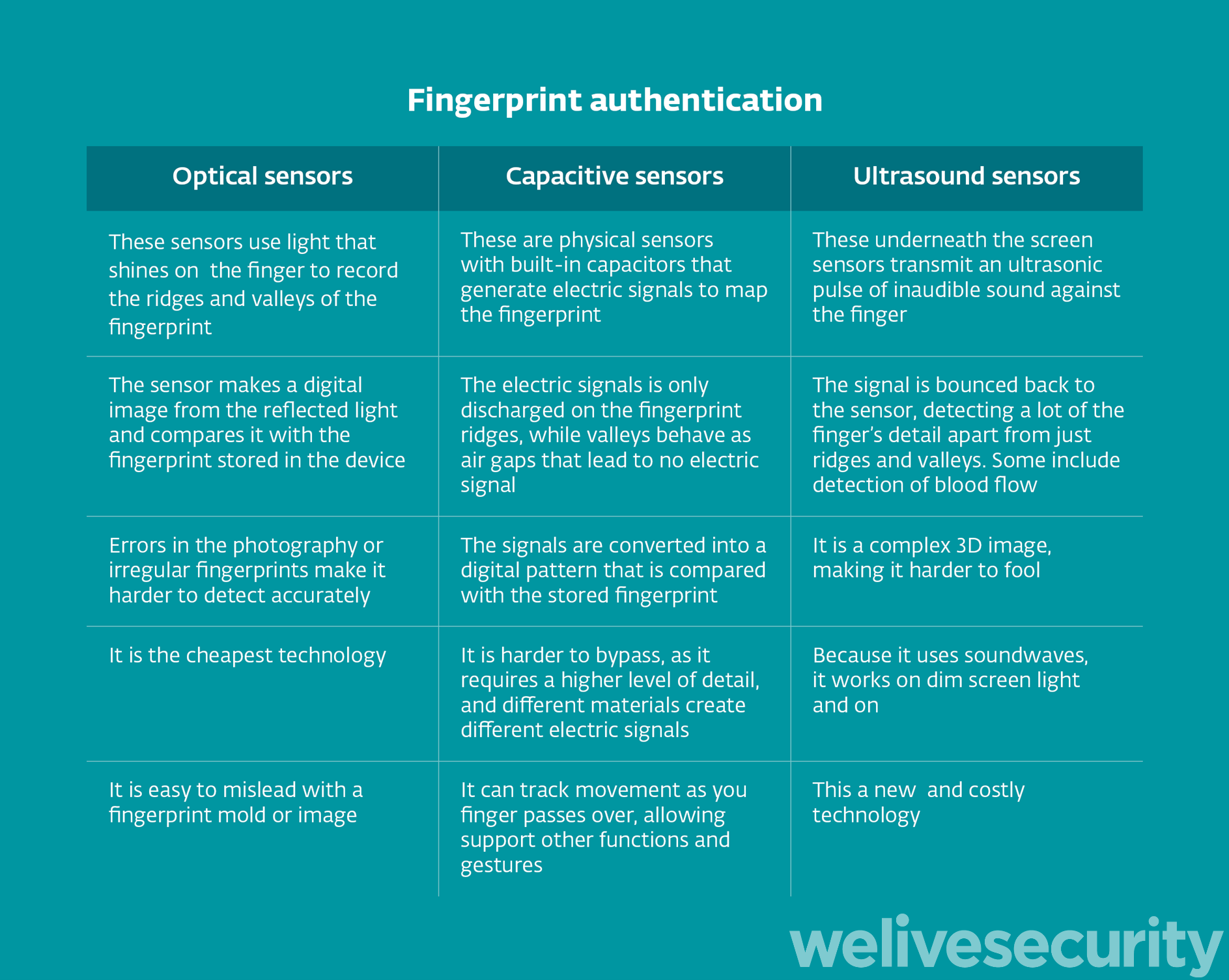
Figure 2. Three types of fingerprint sensors in phones
While fingerprint recognition is quite a safe authentication method unless someone steals your fingerprint – or your finger – it all comes down to the reliability of the device you’re using. When it comes to data protection, most big manufacturers, such as Apple, Google or Samsung, store your fingerprint locally and not online. So even when you use your fingerprint to log in to a service or account on your phone, that app will only receive a digital key and not your fingerprint details.
2. Face recognition
What seemed science-fiction not long ago is today another common method of identity verification. Our facial features are now enough to open doors, unlock our smartphones, validate payments and access all the credentials stored in our password manager apps. Face recognition can work in different ways: simple image comparison, video sequences, three-dimensional data, or image composition by multiple cameras.
The simplest systems, usually found in cheaper phones, might only compare your face to a previously stored face image, other systems use metrics such as the distance between your eyes, the measure from your forehead to your chin, or the shape of the contours of your lips, however, not always seamlessly.
However, things can go rather sour if the technology is used maliciously. While it is up to us whether or not we use this technology on our phones, it might be hard to opt out from CCTV cameras managed by companies or the government, creating a problem of loss of anonymity in public spaces.
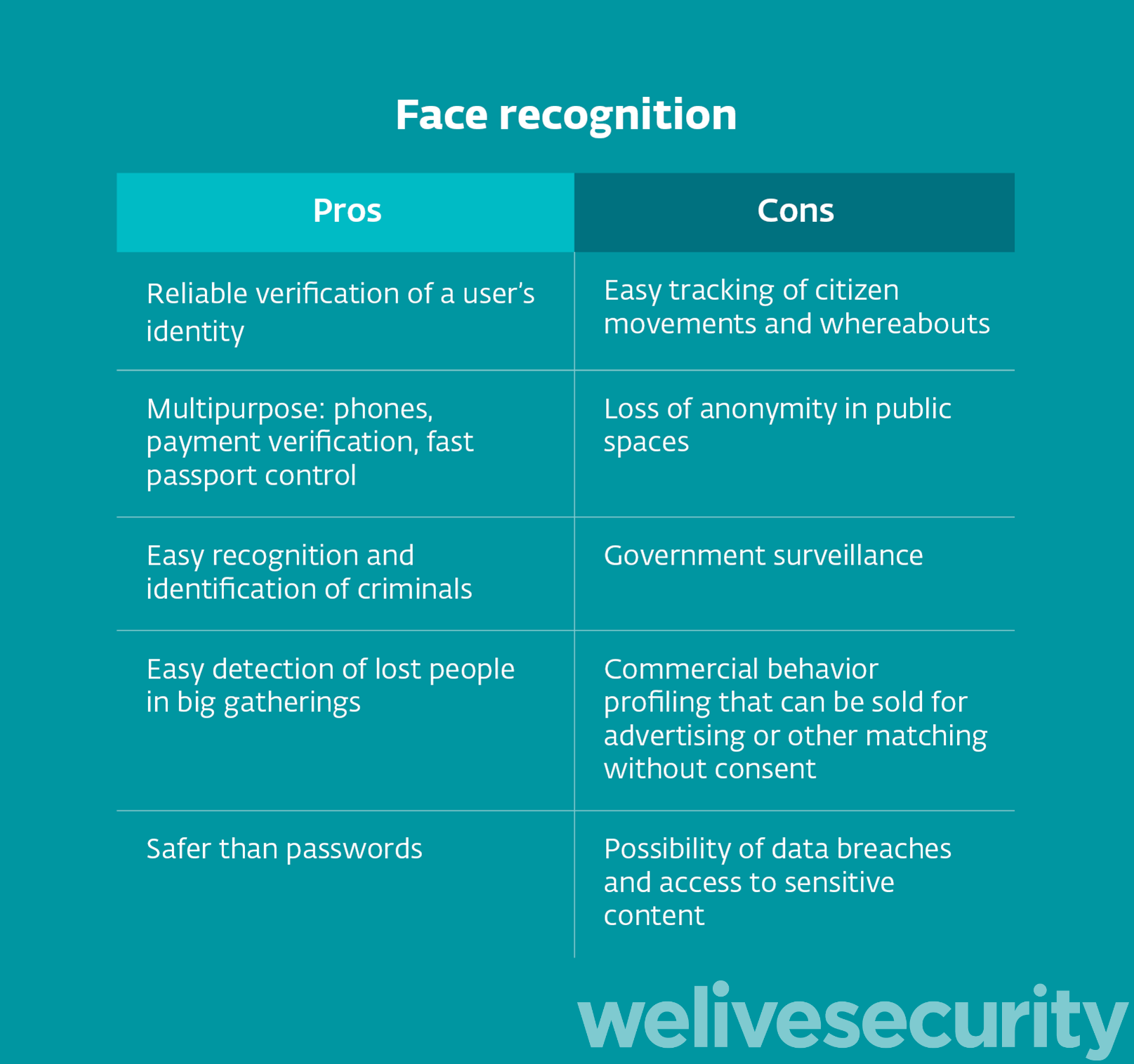
Figure 3. Face recognition – pros and cons
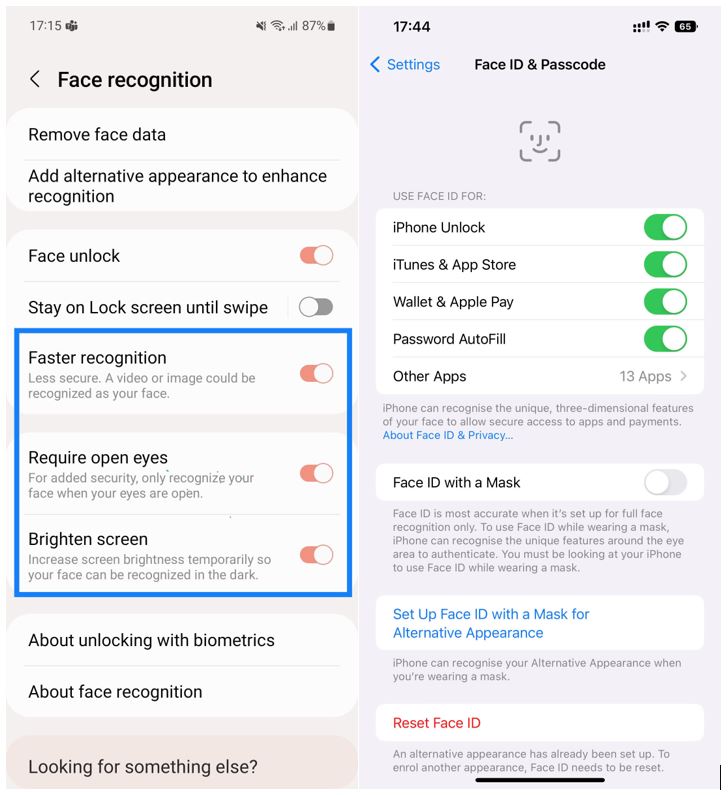
Figure 4. Face recognition options in Android and iOS
3. Voice recognition
“Hey Google” or “Hey Siri” are simple commands you can use to interact with your phone’s voice assistant. In fact, these are voice recognition systems, responding only to your specific voice commands. When setting up your phone, you are asked to say some sentences out loud, allowing the algorithm to learn voice patterns that it will continue learning through real-world use. The more you talk to a virtual assistant, such as Google, Siri, or Alexa, the more it will recognize your voice patterns.
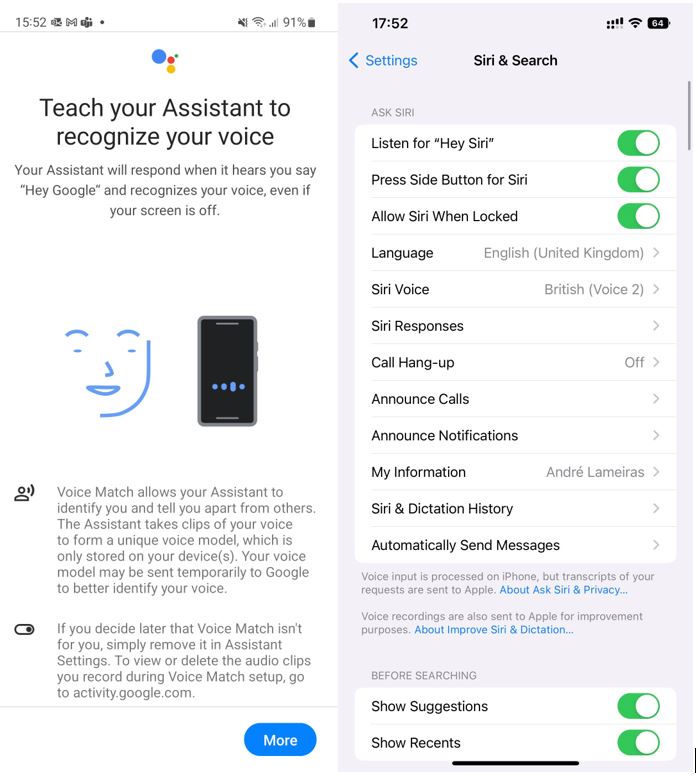
Figure 5. Voice recognition on Android and iOS
Biometrics at a glance – pros and cons
Biometric authentication is convenient, but it poses new challenges to our privacy and safety. While these technologies can replace long and hard-to-remember passwords, they can also be a way of giving away our personal biometric data without always being certain about how it will be used.
Data breaches mean that hackers can access and sell information to malicious actors who might, for example, create molds of our fingerprints and use them to access buildings or devices without our knowledge or consent.
And even if we consider how hard these personal features are hard to bypass, other technologies as face recognition expose us all the time. And while governments use the argument of safety to use face recognition cameras, it is hard to know exactly who are the people they will target and how those images can be used in the future.
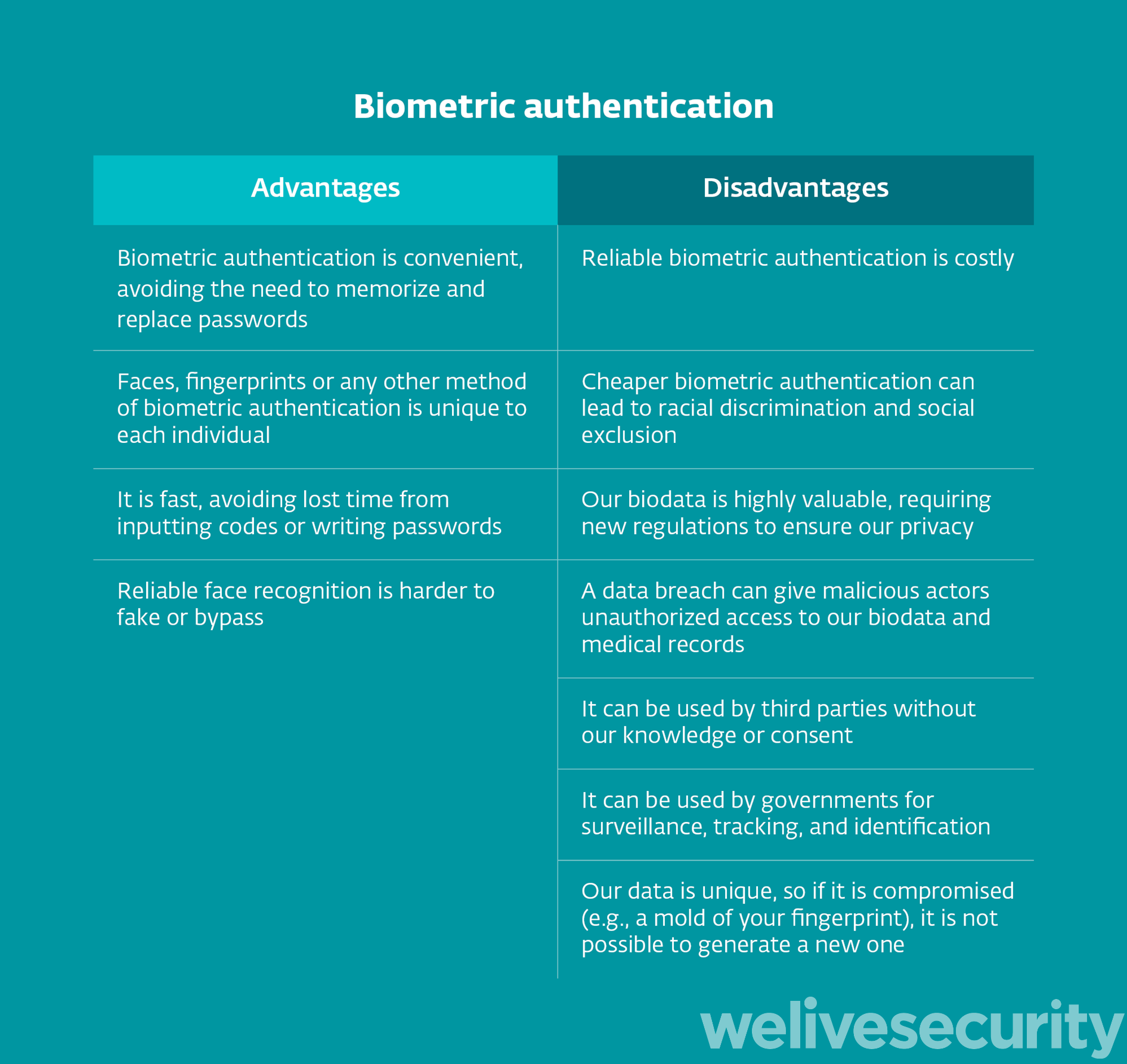
Figure 6. Biometric authentication – pros vs. cons
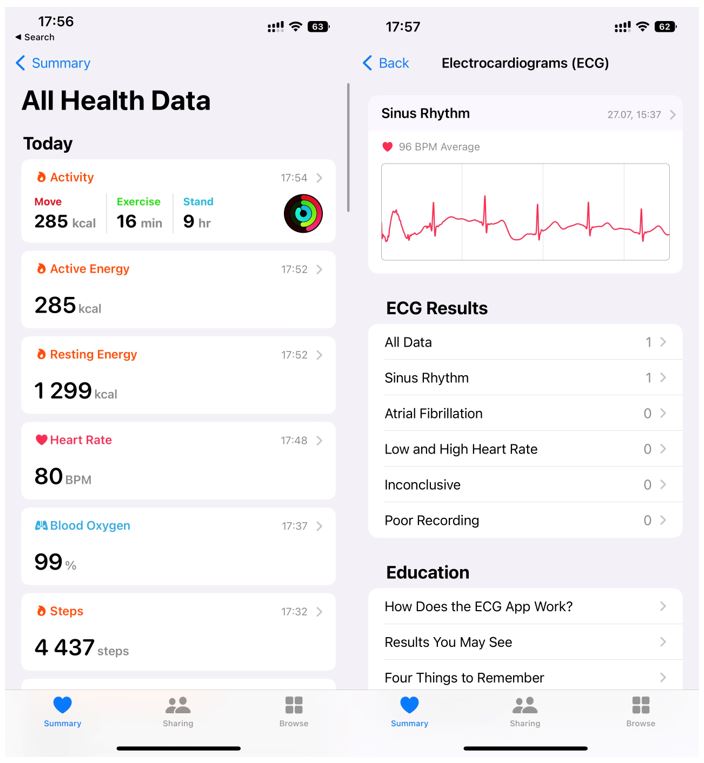
Figure 7. Health data on an iPhone
And it’s just the beginning
Wearables, such as fitness trackers and smartwatches, are increasingly knowledgeable of our heartbeats, sleep patterns, respiratory rates and even walking steadiness. Soon, even behavioral biometrics, like the way our hands move to take our phones out of our pockets or how we walk, might be enough to identify us. While these technologies are a dive into what we imagine a sci-fi future looks like, their use requires a thoughtful discussion around technological developments, security, and privacy.





