Is yet another data breach newsworthy enough to write a blogpost? Probably not, unless there is a personal connection or something interesting. In the case of Blackbaud, for me, there are both. The majority of Blackbaud’s customers are non-profit organizations such as universities, one of which held data relating to someone I know. That university, as required by the European Union’s General Data Protection Regulation, sent an official notification of the breach to my friend, which they immediately forwarded to me, realizing its significance and that I might have an opinion. They were right – especially as the notification states the recipients of the notice need to do nothing but remain vigilant and report anything suspicious.
Blackbaud, a cloud software company, disclosed that they had been the victim of an attempted ransomware attack. Between their cybersecurity team, a forensics expert and law enforcement it was successfully thwarted. Unfortunately, the perpetrator, before being locked out, copied a subset of data which they then offered to delete for an undisclosed sum of money. Blackbaud paid the ransom-to-delete and received confirmation the data had been destroyed. They claim to have taken this action because “protecting our customers’ data is our top priority”.
Funding cybercriminals in this way has many consequences: they may come back later knowing you have a willingness to pay, it may encourage others to attack, and notably it funds this bad actor to launch an attack on the next victim. As with the current pandemic, it’s only when we all work together that we can rid the world of the bad stuff, like cybercriminals, and the actions of Blackbaud or any company paying cybercriminals could be viewed as self-serving.
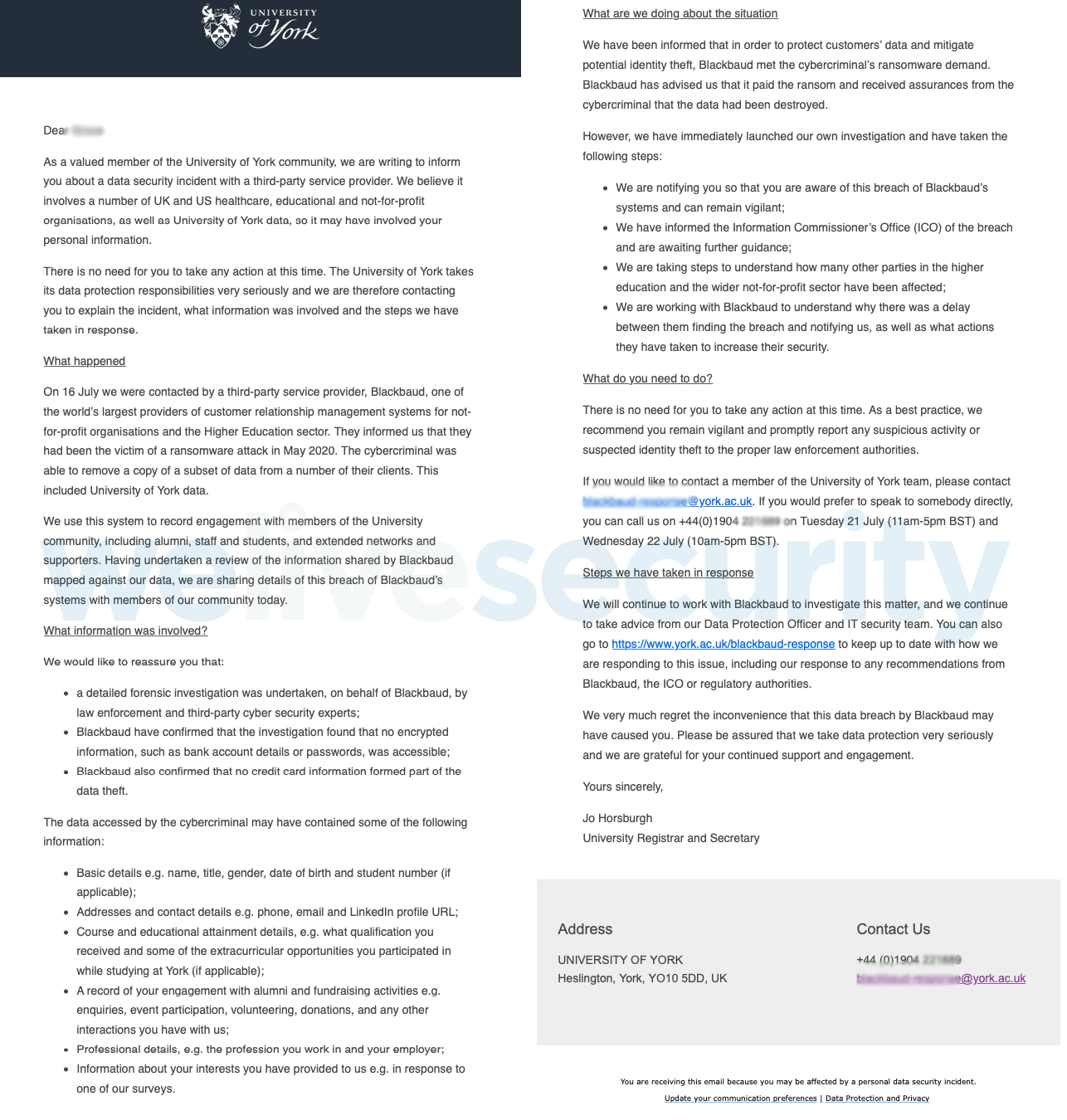
The email notification from the University of York in the United Kingdom, notifying one of the true victims of this crime (my friend), whose data has potentially been breached. The university provides a detailed explanation of the situation and numerous ways to contact it for assistance.
The notification gives a detailed list of the types of information involved: name, gender, date of birth, email address, phone number, and many other personal data elements such as extracurricular activities, profession, employer and educational attainment. Data with this level of detail could be used in a variety of ways – identity theft and spearphishing being among the most likely. A well-crafted phishing email leveraging personal information about an interest, activity, occupation, or employer or competitor is likely to yield a higher click-through rate and potential credential theft for a cybercriminal than a more generic phishing spam email.
What’s missing?
As you can see in the email, the advice is to do nothing other than stay vigilant and report any suspicious activity. Providing some guidance on the types of threat that could be potentially unleashed would seem to be the minimum any organization should offer. An option that many companies suffering a data breach take is to offer identity theft monitoring, either through a specialized company or a credit monitoring agency.
Identity theft monitoring services scour the dark web looking for information such as email addresses or social security numbers and alerts you if someone attempts to get credit in your name. The offering of such a service that would normally cost the victim upwards of US$100 per year for a base service shows responsible behavior, good will and I am sure pacifies regulatory bodies investigating the breached organization’s behavior.
RELATED READING: Simple steps to protect yourself against identity theft
In this instance no identity theft protection monitoring service was offered, so I advised my friend to ask if the university or Blackbaud intended offering it. Sure enough, the university came back nearly instantly with the details of how to sign up and the offer for a no-cost, one-year subscription. I wonder how many of the victims are knowledgeable enough to know that such a service exists or that they should be asking for it? In my opinion it should be a mandatory offering to all victims.
Let me recap; no action needed and no identity theft protection offered – unless you request it. I hope you can feel the frustration in my words!
The broader picture
Getting an email stating your data has been involved in a data breach is not unusual, but just how many breaches are there and how many people do they affect?
Under the California Consumer Privacy Act, all businesses and state agencies are required by law to notify a California resident if they suspect or know that unencrypted personal information has been acquired by an unauthorized person. The law also requires a copy of the notification to be provided to the California Attorney General if it has been sent to more than 500 California residents. In the 30 days of June 2020, there are 38 such notifications listed on the website, some of which do relate to the Blackbaud data breach.
If we assume this rate is typical and scale based on California and world population estimates, we would expect approximately 7,500 data breaches per month. According to statista, between 2005 and 2019 inclusive, data breaches in the US averaged a little over 155,000 records per breach. I know this is a flawed way of calculating a statistic but indulge me… If we apply statista’s average records per breach to our estimate of 7,500 breaches per month worldwide, we get an estimate of an annual total of just under 14 billion records breached. Another way to view this is that every person’s data is breached almost twice a year.
There are so many data breaches that it’s hard to keep up with just how many times your personal information may have been stolen by a despicable, low-life cybercriminal. Maybe there should be an award each year for the person that has been the victim of the most data breaches and an award for the person that has not been part of any breach, if such a person exists.