A team of academics has uncovered a new vulnerability in the Bluetooth wireless communication protocol that exposes a wide range of devices, such as smartphones, laptops, and smart-home devices, to the so-called Bluetooth Impersonation AttackS (BIAS).
Since the attacks are made possible by the flaws in the Bluetooth Classics specification, any standard-compliant Bluetooth device can be expected to be vulnerable, according to Daniele Antonioli, Kasper Rasmussen, and Nils Ole Tippenhauer, who made the discovery and described their findings in a technical paper.
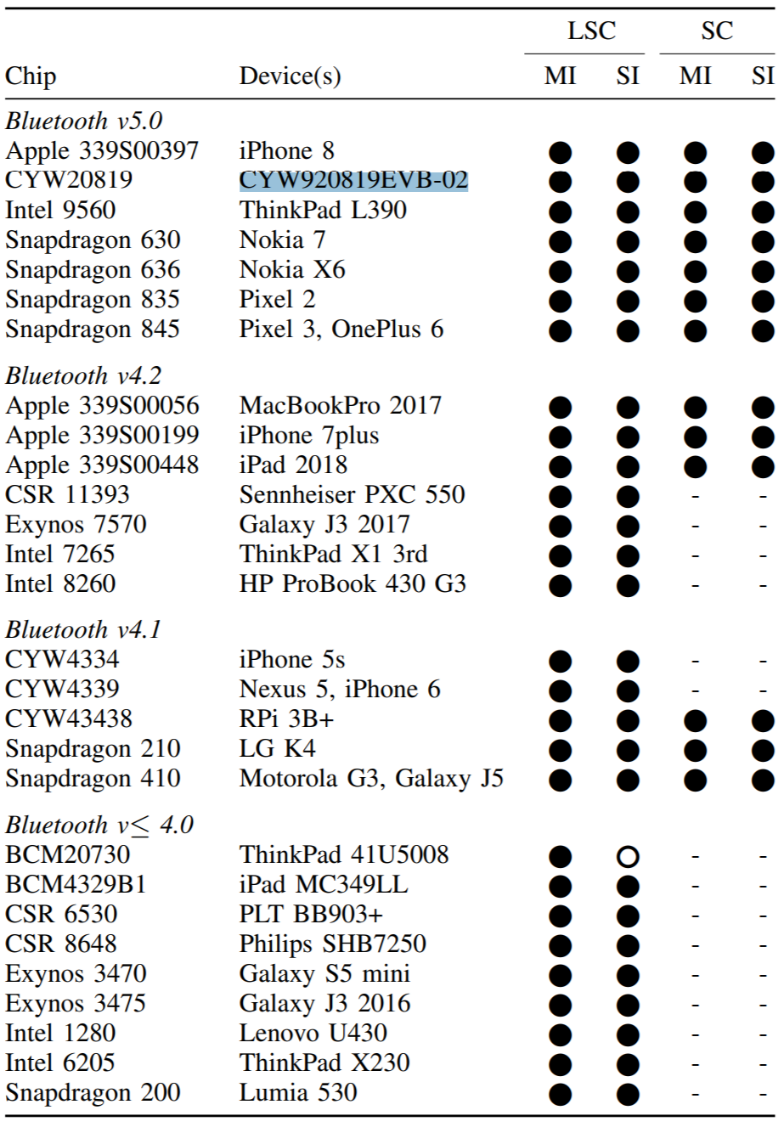
The researchers tested the security weakness on a variety of devices, including laptops, tablets, and smartphones from popular consumer brands that were equipped with different versions of the Bluetooth protocol. “We conducted BIAS attacks on more than 28 unique Bluetooth chips (by attacking 30 different devices). At the time of writing, we were able to test chips from Cypress, Qualcomm, Apple, Intel, Samsung and CSR. All devices that we tested were vulnerable to the BIAS attack.”
Here's the list of the devices tested:
Source: francozappa.github.io
BIAS attacks are the first type of attacks that were successfully able to bypass Bluetooth’s authentication procedures that take place during the establishment of a secure connection, said the team. The flaws that are exploited in the attacks include lack of integrity protection, encryption, and mutual authentication.
During the pairing of two devices, a long-term key is generated that connects the devices together. Once they have done that: each time a secure connection is established, it uses a different session key that is extrapolated from the long-term key and other public factors.
Using the flaw, the attacker is then able to impersonate one of the devices that has gone through the authentication process and paired with the other device, without knowing the long-term key. The attacker can then take control of or steal sensitive data from the other device.
An example of how BIAS attacks work can be viewed in the video below:
In the spirit of responsible disclosure, the researchers contacted Bluetooth Special Interest Group (Bluetooth SIG). The organization, which oversees the development of Bluetooth standards, acknowledged the flaw. If you’re unsure whether your device is vulnerable, the team offers the following clarification:
“After we disclosed our attack to industry in December 2019, some vendors might have implemented workarounds for the vulnerability on their devices. So, the short answer is: if your device was not updated after December 2019, it is likely vulnerable. Devices updated afterwards might be fixed.”
Antonioli, Tippenhauer and Rasmussen have a history with Bluetooth vulnerabilities, since they found and disclosed the Key Negotiation of Bluetooth (KNOB) attack in August 2019. The researchers theorized that a BIAS and KNOB attack used in tandem could have serious consequences. Describing the combination as novel and powerful, they plotted out an example of such an attack, saying: “For example, the attacker can impersonate the recipient of a sensitive file and recover the plaintext, or impersonate an unlocker and unlock a device by sending encrypted commands.”
Earlier this year, a critical bug was discovered in Android’s Bluetooth implementation that allowed remote code execution without user interaction. Google rolled out an update to the bug.





