On May 12th, 2017, WannaCryptor (also known as WannaCry and WCrypt) wrought havoc on computer systems across the globe to a degree never seen previously. The cryptoworm propagated through an exploit called EternalBlue that targeted a critical vulnerability in an outdated version of Microsoft’s implementation of the Server Message Block (SMB) protocol, via port 445, which is mainly used for file- and printer-sharing in enterprise networks. During such an attack, a cybercriminal scans the internet for machines with an exposed SMB port, and launches the exploit code against any vulnerable machines that are found. If the exploit succeeds, the blackhat will run a payload of their choice; in this case, it was the WannaCryptor.D ransomware.
Fast forward to 2020
Three years later, WannaCryptor is still a strong player on the ransomware field. According to the ESET Threat Report for the first quarter of 2020, WannaCryptor still dominates the ransomware family rankings, accounting for 40.5% of ransomware detections. Its dominance at the top of the table didn’t stop in April either, although it did drop by less than one percentage point compared to the previous month. This is quite disconcerting, considering that it had been almost three years since the largest recorded outbreak in May 2017. For most of the first quarter of 2020, WannaCryptor detections were attributed to widely recognized samples that spread in regions with potentially high numbers of unpatched machines, such as Turkey, Thailand, and Indonesia.
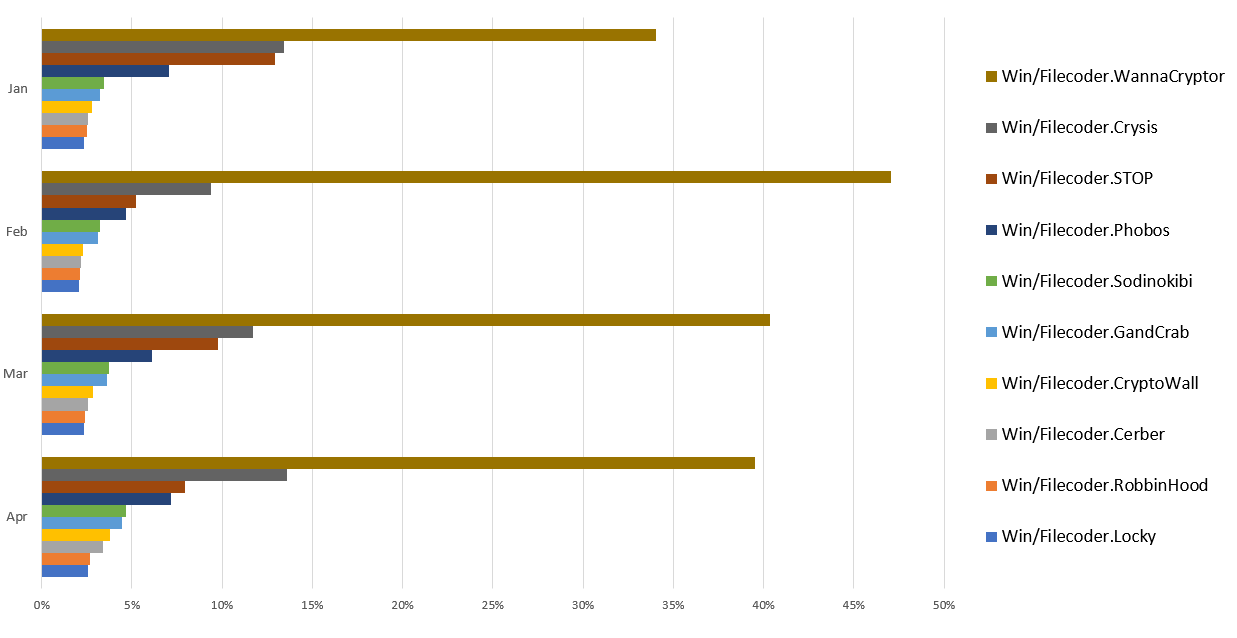
Figure 1. Top 10 ransomware families (% of ransomware detections), January to April 2020
Let’s now focus on the exploit that facilitated the whole WannaCryptor crisis: EternalBlue. Attempted attacks using the infamous exploit were on the decline throughout Q1. In fact, by the end of the first quarter of 2020 it was at half of the historical high it reached in the second quarter of 2019. Although the statistics may seem encouraging: three years on, EternalBlue remains a relevant threat with hundreds of thousands of attack attempts taking place daily.
According to Shodan, meanwhile, there are still about one million Windows machines with the SMBv1 protocol exposed to the internet (Figure 2). That means that there are potentially one million machines that are susceptible to attacks using the EternalBlue exploit.

Figure 2. Data from Shodan (as of May 4th, 2020)
Compared with last year, there was a reshuffle of where most of the affected devices are located. While the United States still leads the pack with the greatest number of vulnerable devices, Russia has overtaken Japan for second place. South Africa is a noteworthy addition since last year it wasn’t even on the list and now it has taken fourth place.
It’s worth noting that although EternalBlue gained infamy for enabling WannaCryptor, that is not by any means the only high-profile attack that leveraged it. Both the Diskcoder.C (aka Petya, NotPetya and ExPetya) and BadRabbit ransomware campaigns are attributed to the exploit, dumped online by the Shadow Brokers group after allegedly being purloined from the US National Security Agency (NSA).
Lessons learned?
Looking back, it’s safe to say that the outbreak was avoidable and could have been stopped dead in its tracks if users worldwide had taken the necessary steps. The vulnerability was disclosed to Microsoft and a critical security update was released as part of a typical “Patch Tuesday” update a full 59 days before the global outbreak began.
Furthermore, the Redmond giant deemed the first version of SMBv1 protocol – which is now over thirty years old and contained the EternalBlue vulnerability – deprecated in 2013, indicating then that it should have been considered obsolete and not used anymore. And even if a patch wasn’t installed, then some basic security configurations could have prevented WannaCryptor from infecting devices altogether. So has the cyberworld learned anything from one of the worst ransomware outbreaks in history?
Although you would think that the EternalBlue-enabled WannaCryptor crisis instilled a valuable lesson in netizens, unfortunately, that doesn’t seem to be the case. To quote the Spanish philosopher George Santayana: “Those who cannot remember the past are condemned to repeat it.”
Those words especially ring true, since starting in the middle of last year, cybersecurity experts started sounding the alarm about BlueKeep, a Remote Code Execution (RCE) vulnerability found in Remote Desktop Services (RDP) that every enterprise administrator should have patched ASAP. Yet, the first attacks were recorded months later. [ESET released a free utility last year to check if a Windows computer is vulnerable to attacks exploiting BlueKeep.]
Final thoughts
The major takeaway remains that three years on, many people still underestimate the value of patching their computer systems as soon as a patch is available, and apparently they do not adhere to best security practices. Keep your software patched and up to date, and combine that practice with a reputable multi-layered endpoint security product. This will go a long way toward protecting you against ransomware … and all kinds of other malicious attacks.





