Earlier in April, a new sextortion scam campaign was detected making the rounds in countries on both sides of the Atlantic. The spam emails that were detected by ESET’s research laboratory have been trying to dupe unwitting victims by referring to old passwords that have been part of old data breaches.
The campaign is not altogether new, since it repurposes old scams. The first time that scammers made waves with these tactics was in 2018 with a campaign that also included the victim’s password in the subject line. The email itself claimed that the password was obtained by compromising one of the recipient’s devices using malware.
However frightening this may seem at first glance, these are just social engineering and scare tactics, employed by cybercriminals to generate panic in the recipients of these emails. To put it simply, it is highly unlikely that your computer has either been accessed or compromised, at least not by the method suggested in the email, so there is no need to panic.
In fact, a similar campaign has been spotted recently by ESET researchers: it rehashed the content to reflect the current pandemic situation and includes a threat to infect the victim’s whole family with coronavirus.
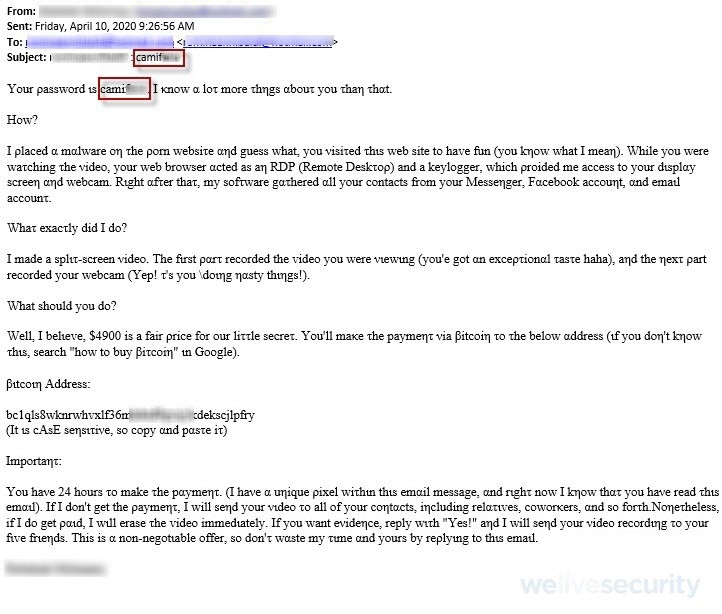
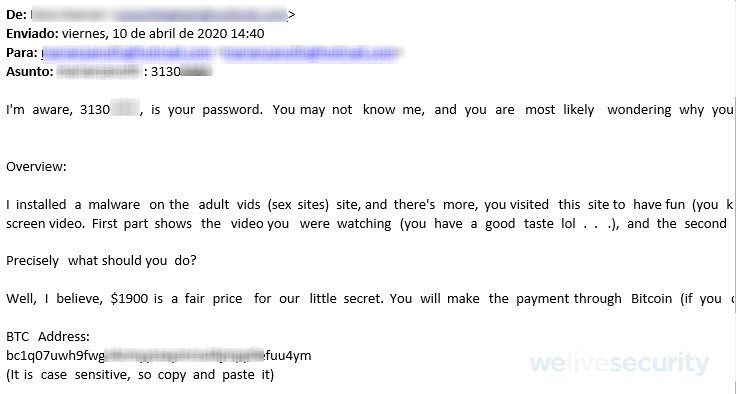
The new extortion campaign borrows, or rather builds upon, the previous versions. The scammers start with an alarming message right off the bat to get the victim’s attention, usually by including one of the victim’s old passwords that was probably stolen as part of a previous data breach. Moving on, the fraudsters claim that the victim’s device was infected by some form of malware when visiting a porn website, and that allowed them to obtain both the victim’s password and access to their device. The scammers then purport to have made a video of the victim and the alleged “not safe for work” content.
Once the cybercriminals have scared their potential victims enough, they demand a sum to be paid within 24 hours or the embarrassing video will be released. They usually want the payment to be made in bitcoin.
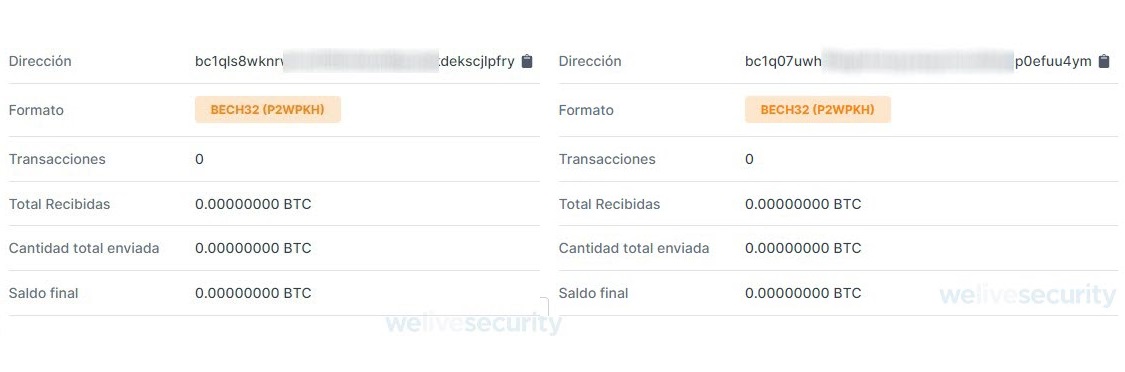
After analyzing some of the cases stemming from this new sextortion scam campaign, ESET researchers found that it probably started sometime around the 8th or 9th of April. They checked the bitcoin wallet addresses shared by the attackers and found that they weren’t faring very well, to put it mildly. By contrast, during the 2018 campaign the scammers were able to trick victims out of almost half a million dollars.
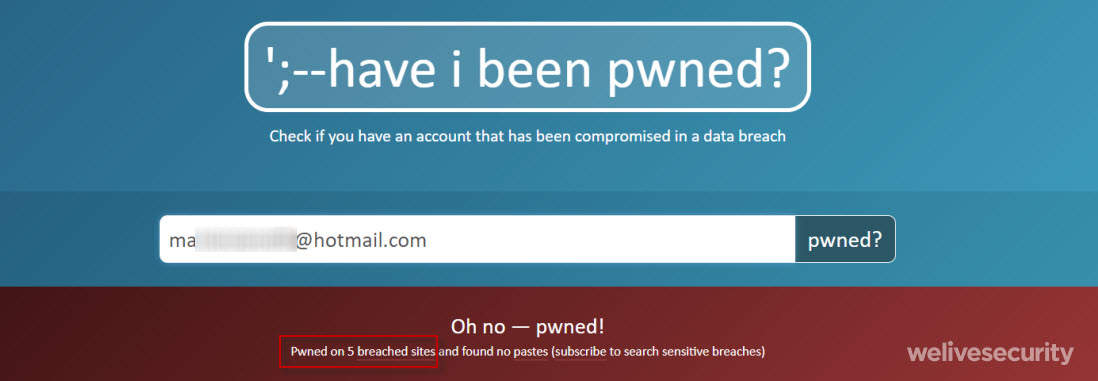
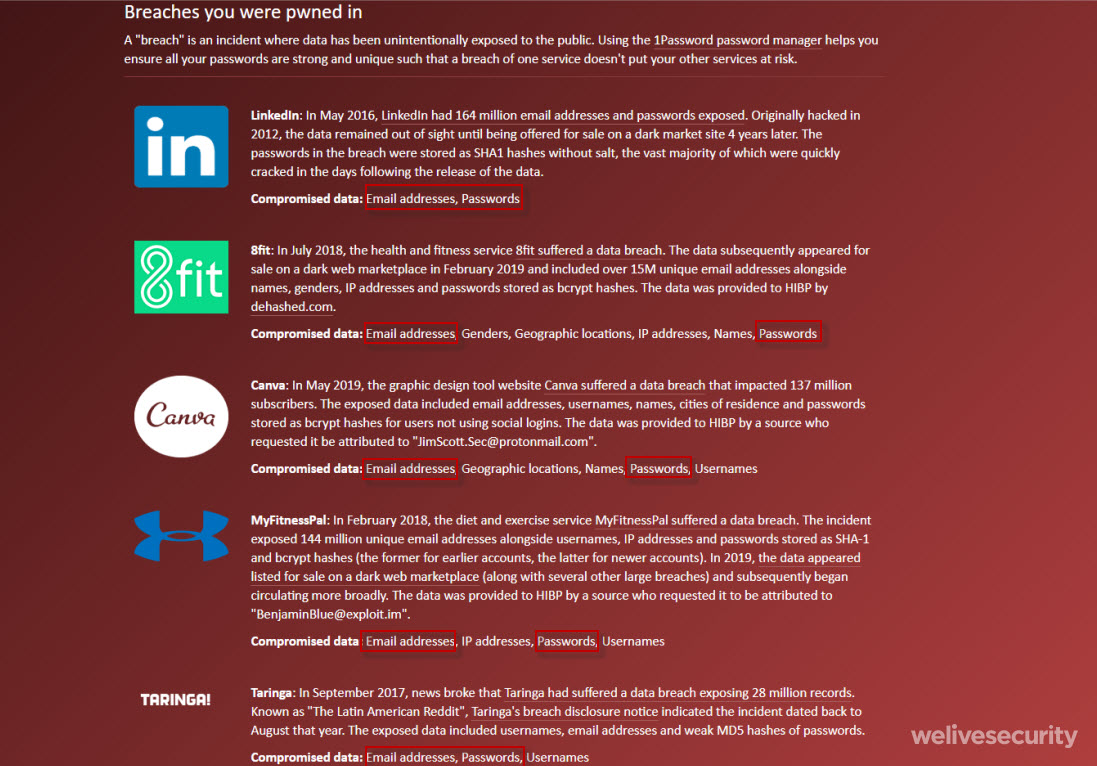
To reiterate, it is important to note that the password did not come from the potential victim’s compromised machine. All of the breadcrumbs indicate that the campaign leverages credentials taken from large data leaks and older breaches, which, unfortunately, aren’t a rare occurrence. ESET researchers entered some of the victims’ email addresses into to the Have I been pwned? website, and indeed found that their passwords and emails were gathered from services that suffered data breaches such as LinkedIn, Taringa, MyFitnessPal or Canva, among others.
What can I do?
Before you fly into a frenzy, you should take a step back and think about the whole scam. Have you ever visited a porn site? If the answer is no, well, you know the email is fake and you have nothing to worry about. And even if you did (and it’s safe to say you weren’t alone), at best it could be embarrassing to you if the secret were revealed. But to reiterate, the cybercriminals have no evidence whatsoever, video or otherwise, of a potential victim’s intended activities.
Another thing you can do is use Google or whatever search engine you prefer and enter the word scam, in quotes, along with an interesting phrase from the scam email. You can then scroll through the results, of which there may be a few thousand, and see if anything seems vaguely familiar. Quite often you will find examples of similar scams that have been floating about and have already been scrutinized by a number of researchers and experts in the field.
If you’re still not sure what you’re dealing with you can check out a list of other steps compiled by ESET researcher Bruce P. Burrell.