Five major US wireless carriers – AT&T, T-Mobile, Verizon, Tracfone and US Mobile – are susceptible to SIM swap scams, a danger apparently looming large especially over prepaid accounts, a study by Princeton University researchers has found.
SIM swapping attacks, also known as port-out or SIM swap scams, have been a serious and growing problem of late, with its victims including Twitter CEO Jack Dorsey. It has previously been shown that attackers can, with relative ease, execute these attacks to commandeer control of people’s phone numbers. From there, they can break into the victims’ banking, social media and other accounts that use the same phone number for multi-factor authentication.
To test the carriers’ resilience to this type of fraud, the researchers created 10 simulated identities with all the bells and whistles, including names, dates of birth, and addresses. For each identity, they registered a prepaid account with all five wireless carrier providers, totaling 50 phone numbers. They then created a trail of phone calls and text messages, giving the accounts an aura of credibility.
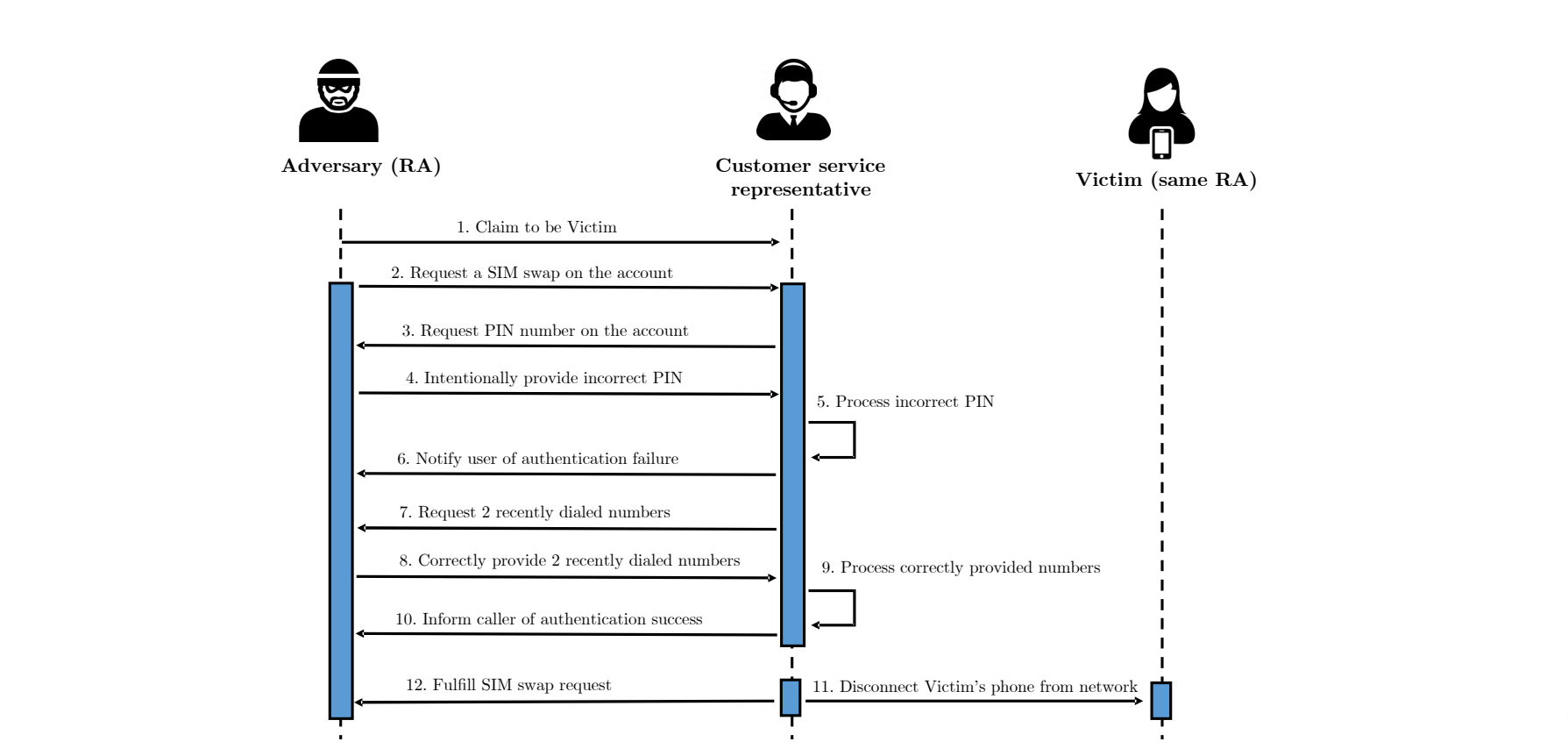
Research assistants (RAs) then went on to pose as bad actors and called in the companies’ customer support representatives, trying to hoodwink them into unwittingly completing successful SIM swap fraud. If the “scammers” weren’t able to provide correct responses to the authentication challenges, they would feign ignorance and intentionally provide false answers. This hardly mattered in the end, however.
“When providing incorrect answers to personal questions such as date of birth or billing ZIP code, RAs would explain that they had been careless at signup, possibly having provided incorrect information, and could not recall the information they had used,” reads the paper.
The customer service staff then resorted to other methods of authentication, some of which turned out to be easily subvertible. The questionable methods included asking about recently dialed numbers or recent payment information. When it comes to prepaid accounts, this is easily bypassed if you use a refill card.
Worryingly, the would-be scammers needed to pass only one of the tests to be authenticated, even if they had failed several previous challenges. In the researchers’ own words, “attackers generally only needed to target the most vulnerable authentication challenges, because the rest could be bypassed”.
RELATED ARTICLE: Simple steps to protect yourself against identity theft
The carriers were notified about the shortcomings of their authentication procedures so that they could respond appropriately. T-Mobile, for one, said it had “discontinued the use of call logs for customer authentication”, reads the study.
In addition, the researchers also analyzed 145 websites that use phone-based authentication to determine how SIM swap scams could help an attacker compromise a user’s account. They found that 17 of them could be compromised with just a SIM swap.
On a related note, one day before the research was published, members of the United States Congress happened to send a letter to Federal Communications Commission (FCC) chairman Ajit Pai. The letter urged the FCC to require mobile carriers to bolster the security of users against SIM swap fraud.