ESET researchers have spotted fake websites that impersonate PayPal and, using social engineering techniques, attempt to trick users into handing over considerably more than ‘only’ their access credentials to the payment service.
The ruse
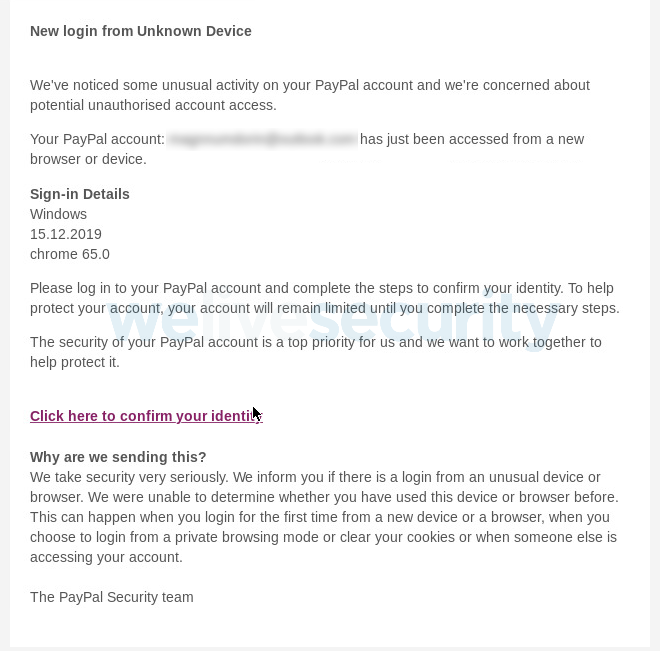
As is commonly the case with phishing campaigns, the attackers use scare tactics that encourage you to take immediate action. The ploy here involves a spammed email alert of ‘unusual activity’ on your account, prompting you to secure it and avoid financial loss.
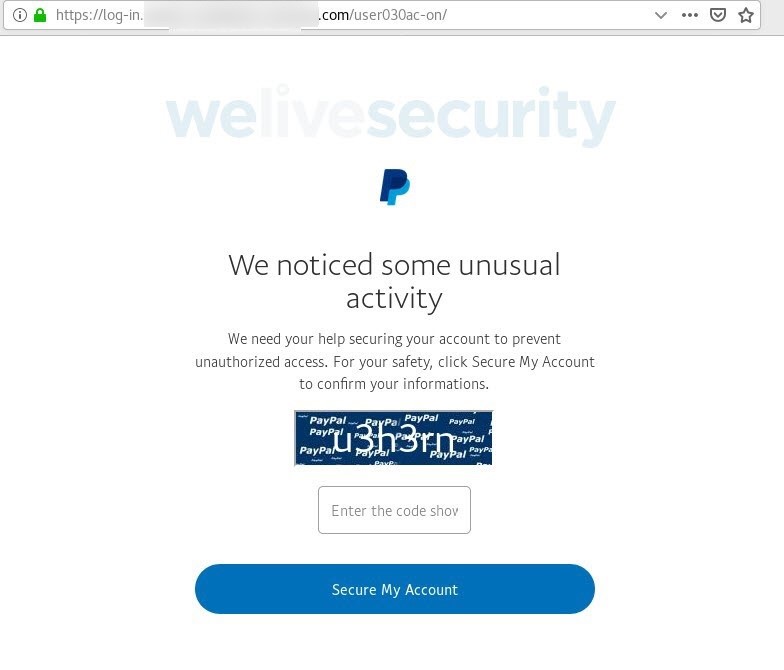
Should you click on the link in the phishing spam message, you are presented with a PayPal-branded page reiterating the claimed account compromise.
The manufactured sense of urgency is not the only telltale sign to tip you off that something is amiss. Other giveaways include the odd URL (though partly obfuscated here for security reasons), substandard English, chopped-off letters, and the use of a CAPTCHA.
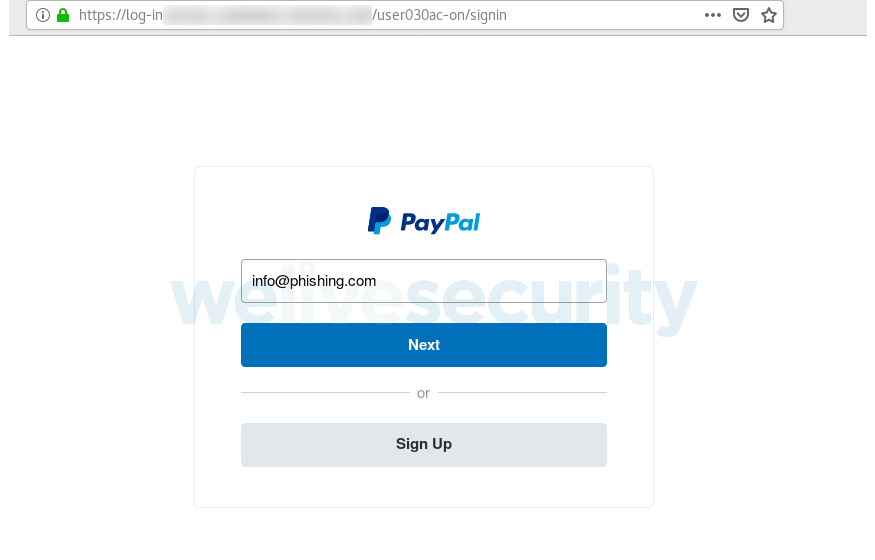
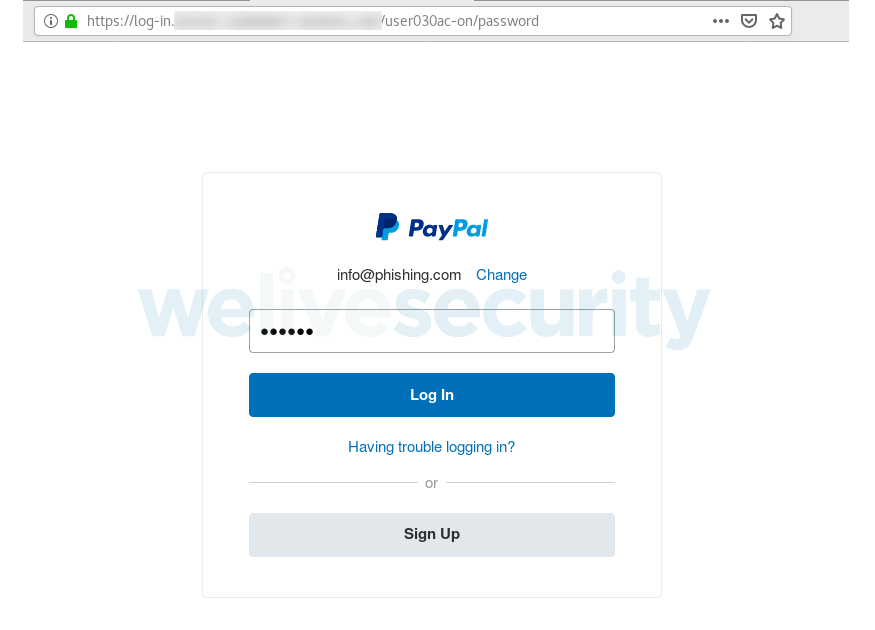
If you do fall for the ploy, however, you’ll be taken to a login interface that was created to look the part of the genuine two-step PayPal login process.
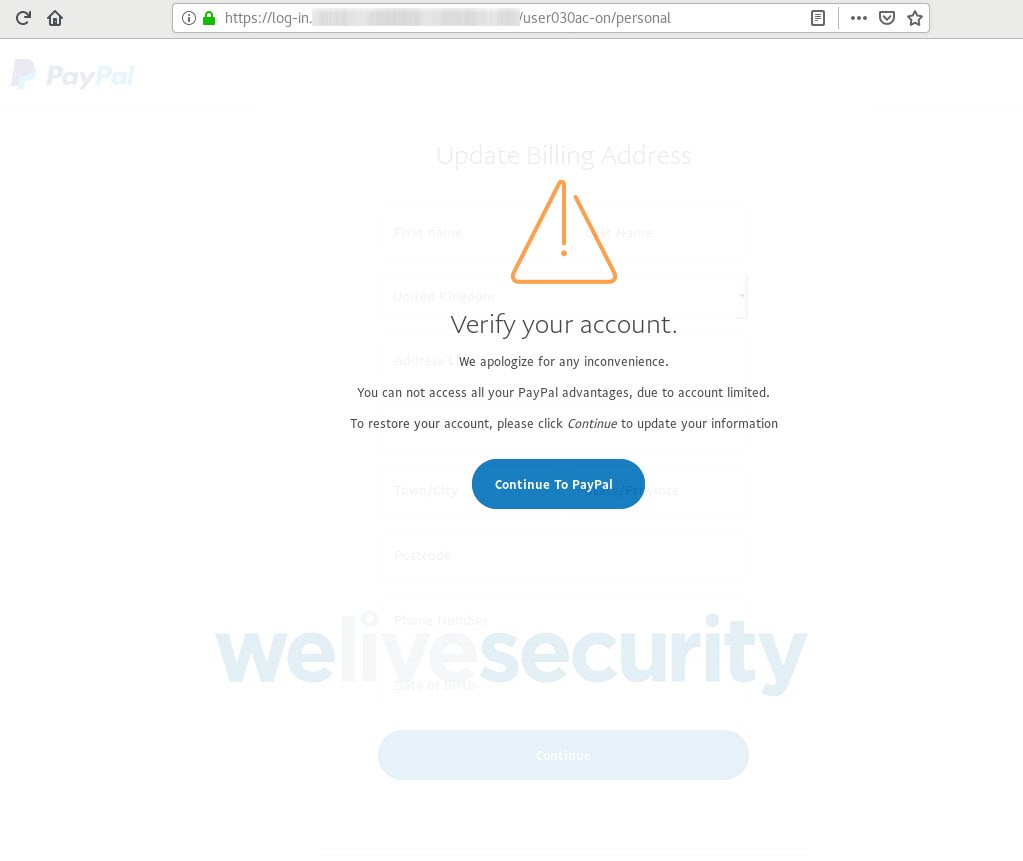
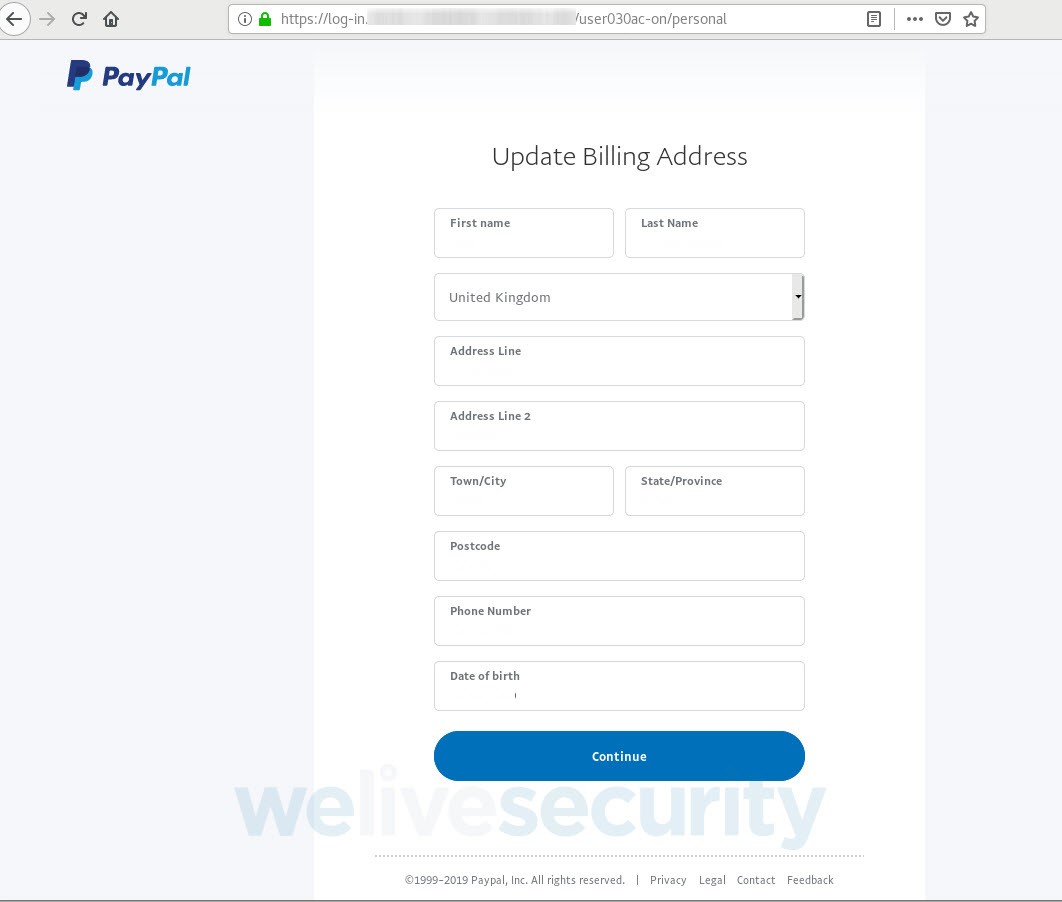
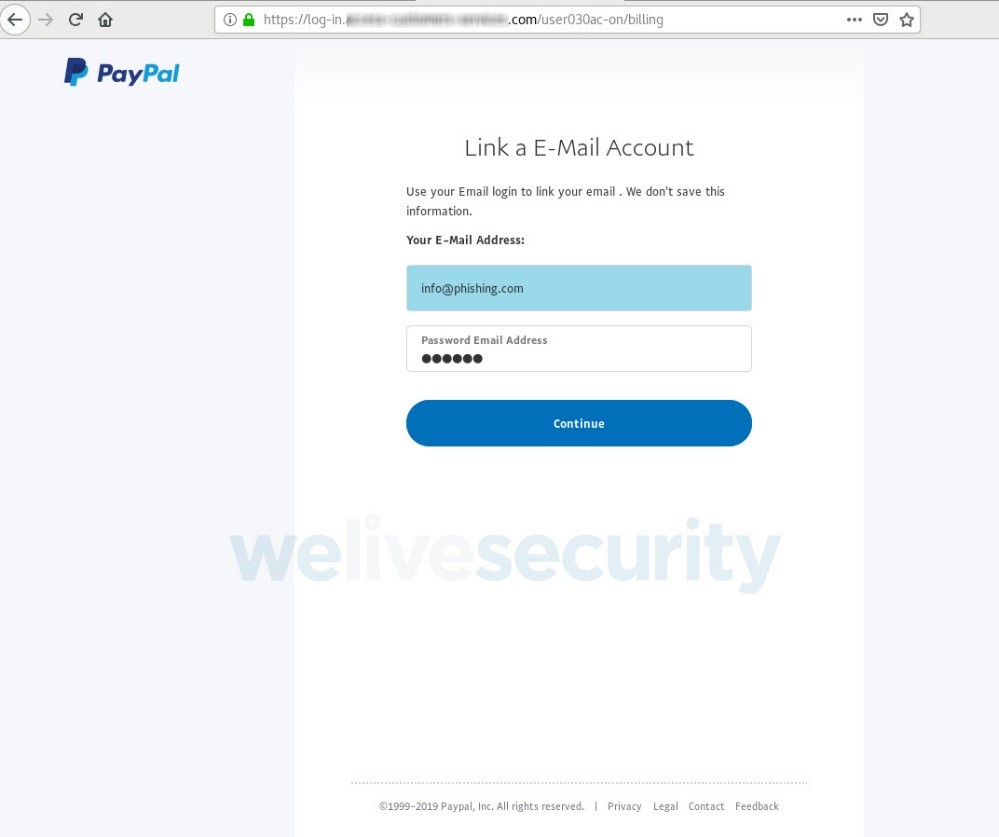
Once you’ve supplied your username and password, you’re asked to ‘verify your account’ by providing additional personal information.
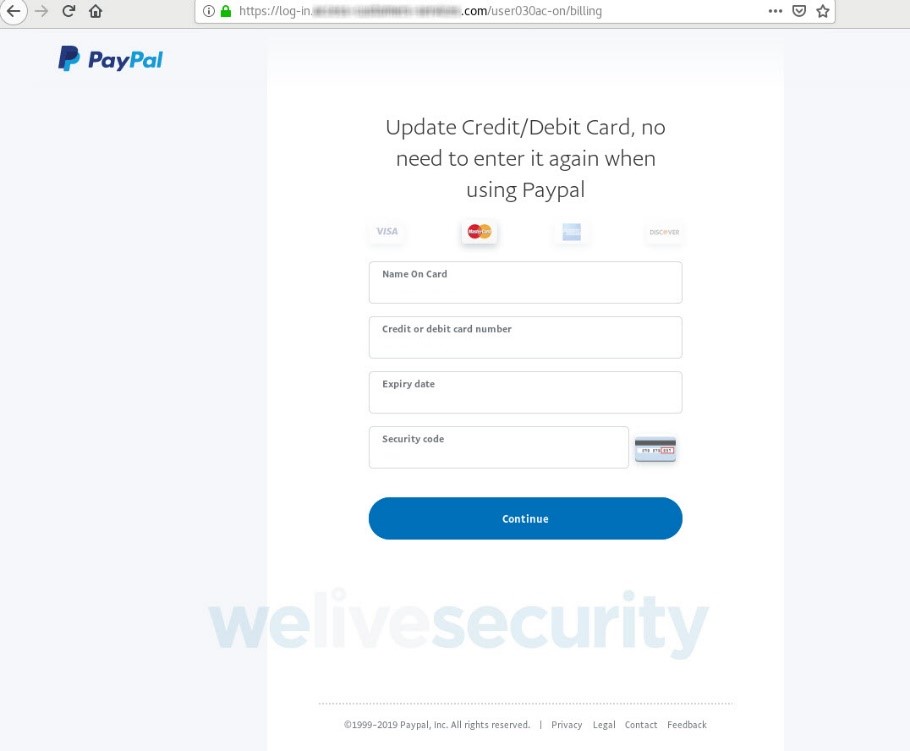
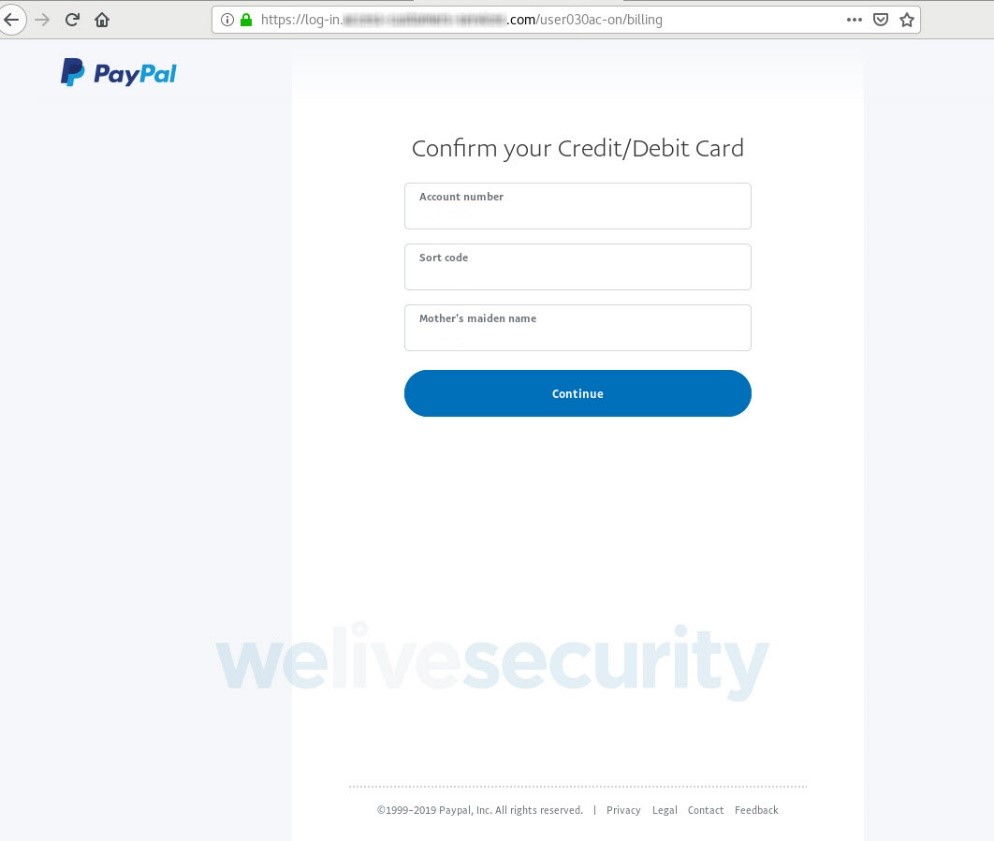
By this stage, you have already handed over your PayPal login credentials; nevertheless, the scammers attempt to collect far more than that. As Figures 6 to 9 show, in a series of steps you’re asked to surrender a range of sensitive information, including your credit or debit card data, access credentials to the bank account linked to the card and, lastly, the login to your email account.
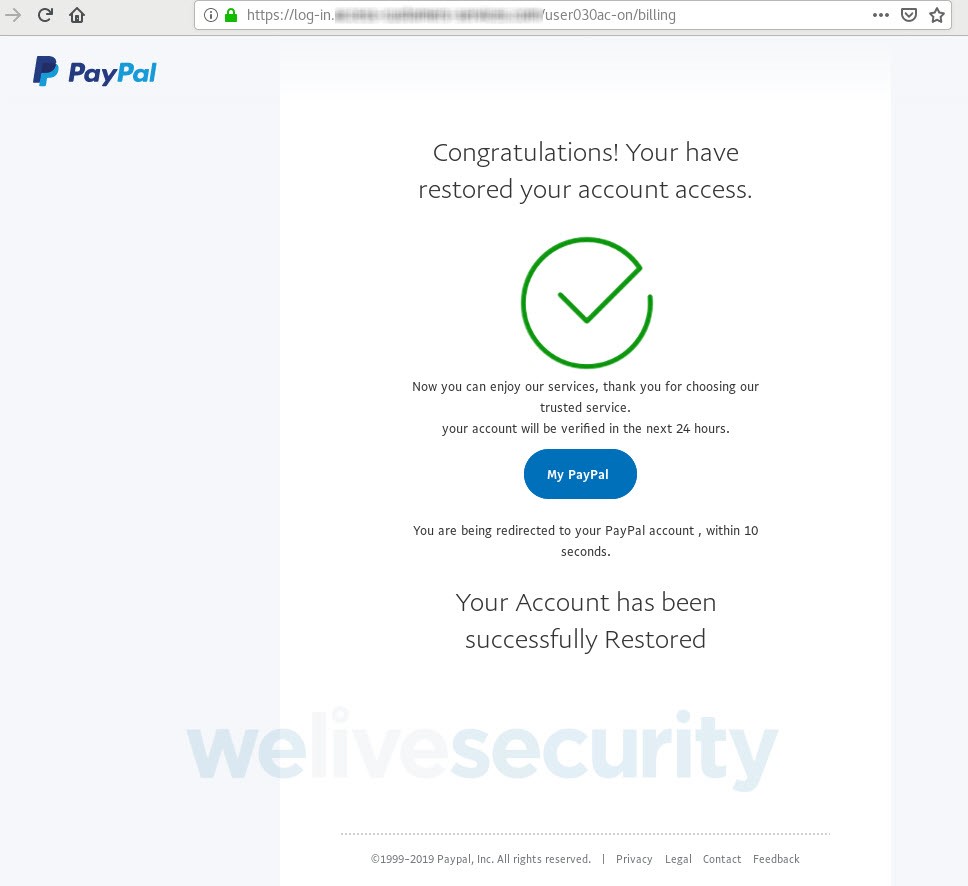
In the end, you’re told that access to your PayPal account has been restored. Nothing could be further from the truth now that a big chunk of your (digital) life is in the hands of the criminals, who can use it for identity theft and all manner of fraud, both on and off the internet.
The domain name
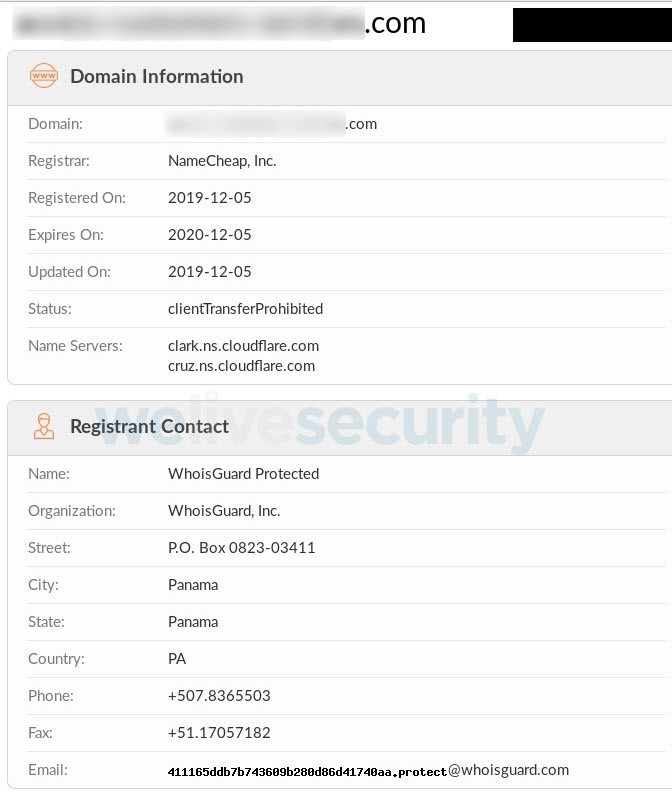
Despite being clearly distinguishable from the impersonated service, the names of the malicious websites seen in this scam seek to give a sense of being an actual touchpoint for PayPal users who are experiencing problems accessing their accounts. Several such fake domain names have been used – this discussion will focus on the first we saw and from which the screenshots here are taken.
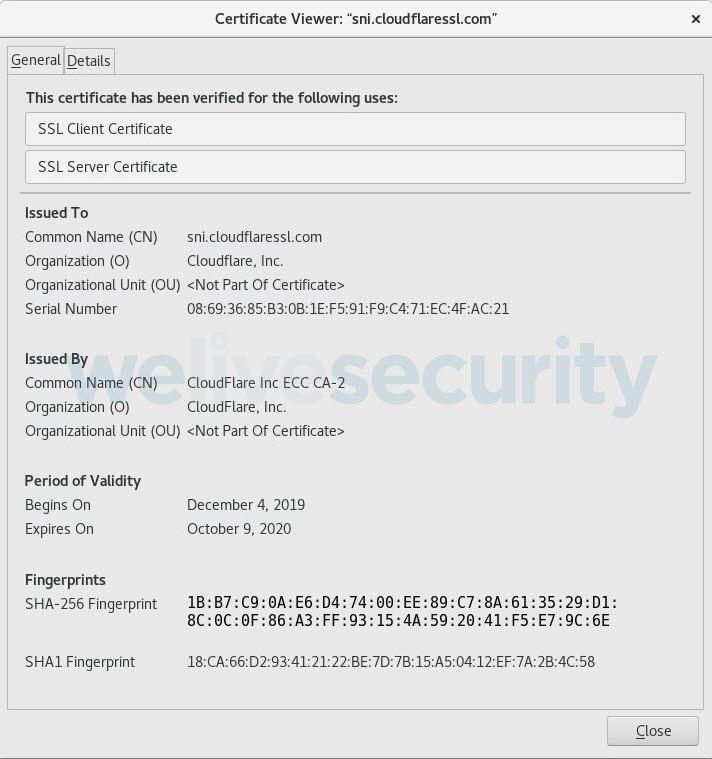
Additionally, the presence of the green padlock to the left of the URL bears witness to a recent trend, where countless phishing sites use authentic SSL (Secure Sockets Layer) certificates in order to boost their aura of legitimacy. As shown in Figures 11 and 12, one of the domains hosting the scam was registered and received a valid SSL certificate earlier this month.
Conclusion
Much like other threats in cyberspace, phishing attacks come in various shapes and sizes and continue to evolve. As the example shows, however, social engineering tactics remain at the heart of such scams. After all, by preying on human weaknesses, cybercriminals usually take the path of least resistance. For the victims, even a momentary lapse in judgment or a short moment of distraction can have far-reaching and deleterious consequences.
It’s worth noting that we’ve found no evidence that this campaign results in the installation of malicious software on victims’ machines. And, as this scam starts with a phishing email, the usual precautions will go a long way towards helping you stay safe.
For starters, you should treat with utmost caution any out-of-the-blue notifications to input your sensitive information, and resist the urge to click on links or download attachments. Watch out for any irregularities in the URL where you enter your sensitive data. Indeed, for added reassurance, it never hurts to type the website’s name into the browser manually, or use a previously saved bookmark.
Read also our takes on other PayPal scams and PayPal security, as well as on how to avoid falling victim to phishing attacks in general:
Phish Allergy – Recognizing Phishing Messages
5 simple ways you can protect yourself from phishing attacks
Phishing unravelled