The latest hype around the FaceApp application has attracted scammers who want to make a quick profit.
The FaceApp application, which offers various face-modifying filters, is available for both Android and iOS. While the app itself is free, some features, marked as “PRO”, are paid. Recent concerns about FaceApp privacy issues have generated a huge wave of media attention.
Scammers have been trying, to various ends, to exploit this wave of interest, using a fake “Pro” – yet free – version of the application as a lure. The fraudsters have also made an effort to spread the word about this fictitious version of the currently-viral app – at the time of writing this blogpost, a Google search for “FaceApp Pro” returns some 200,000 articles.
We have seen two ways the scammers try to make money from the non-existent “Pro” version of FaceApp.
Fake websites
In one of the scams we have seen, attackers have used a fake website that claims to offer the “premium” version of FaceApp for free.
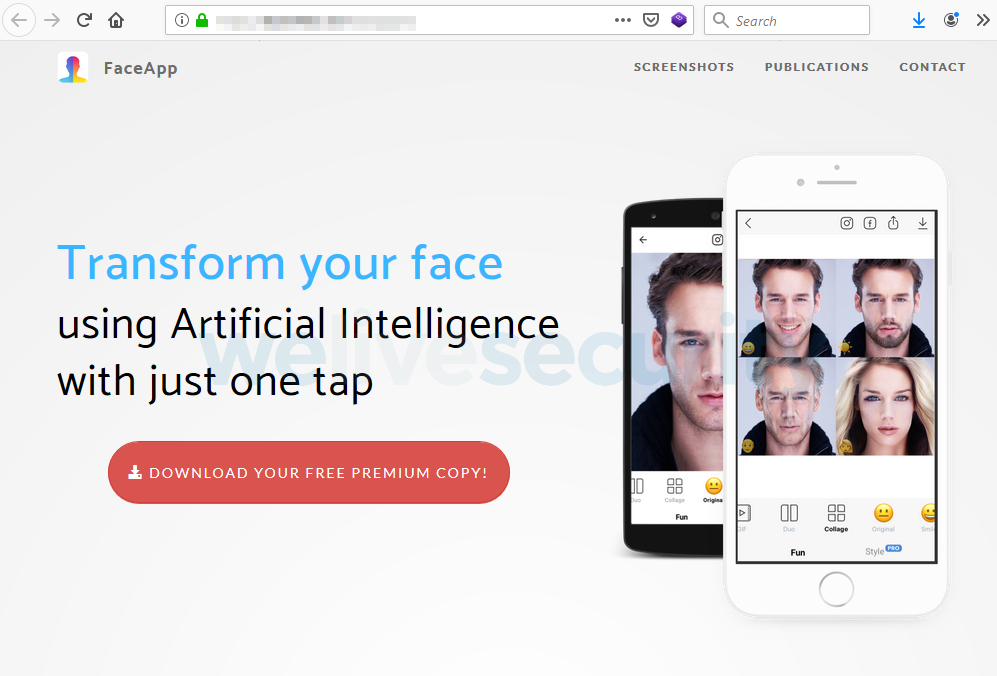
Figure 1. A fraudulent website used in one of the scams
In reality, the scammers trick their victims into clicking through countless offers for installing other paid apps and subscriptions, ads, surveys, and so on. Victims also receive requests from various websites to allow displaying notifications. When enabled, these notifications lead to further fraudulent offers.
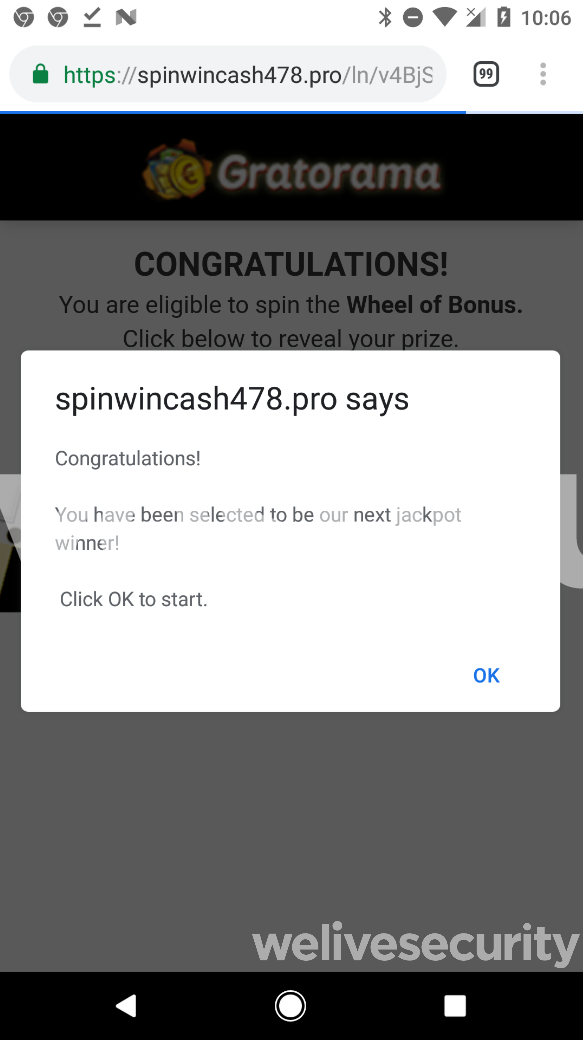
Figure 2. Notifications from the browser lead to further scams
During our test, we ended up with the regular, free version of FaceApp that is also available on Google Play. However, instead of using Google Play as the source, the app was downloaded from a popular file-sharing service (mediafire.com), as seen in Figure 3. This means users could easily end up downloading malware if that was the attackers’ intention.
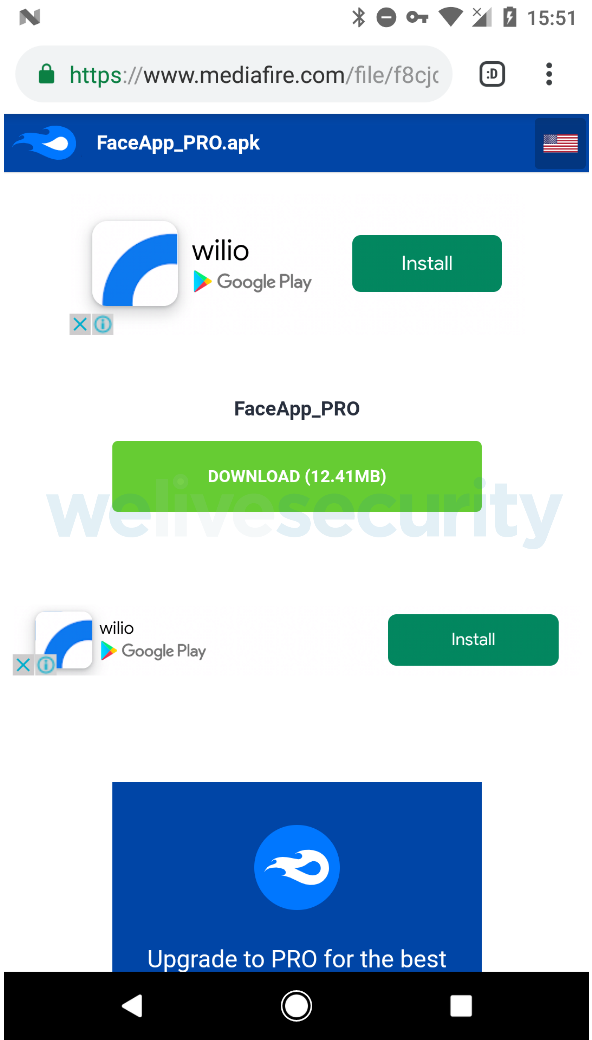
Figure 3. FaceApp presented as “FaceApp PRO” and downloaded from an unofficial source
YouTube videos
The second type of scam includes YouTube videos, again promoting download links for a free “Pro” version of FaceApp. The shortened download links, however, point to apps whose only functionality is to make users install various additional apps from Google Play. One of the YouTube videos, seen in Figure 4, has over 150,000 views at the time of writing.
While this type of scam is typically used merely to deliver ads, the shortened links could lead to users installing malware in just one click. We have seen this happen in the past, for example with Fortnite used as a lure.
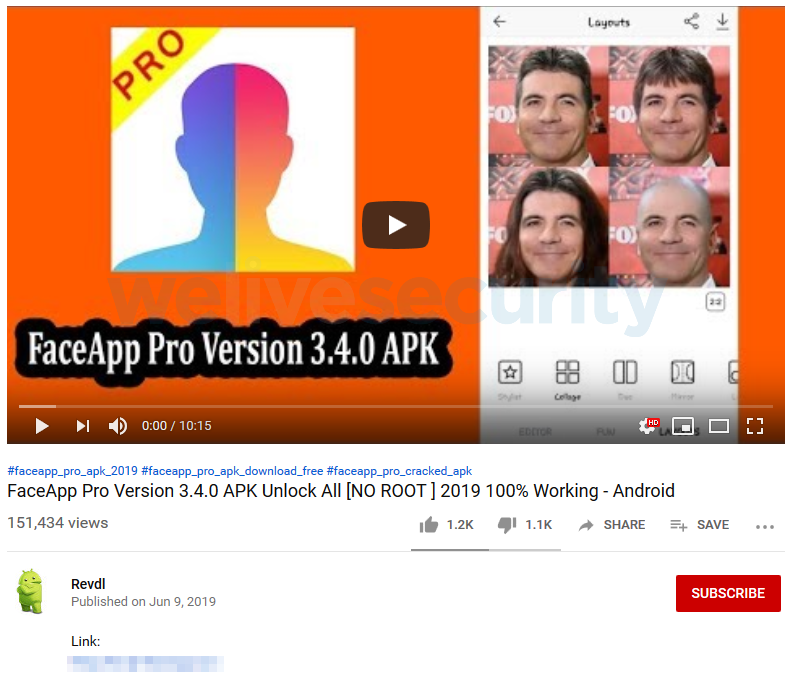
Figure 4. A YouTube video claiming to offer a link for downloading the installation package (APK) for a “FaceApp Pro” application for Android
The mentioned link was clicked over 96,000 times; this, however, doesn’t tell us much about the number of actual installations. (But still, serious businesses don’t even dream of such a high click rate.)
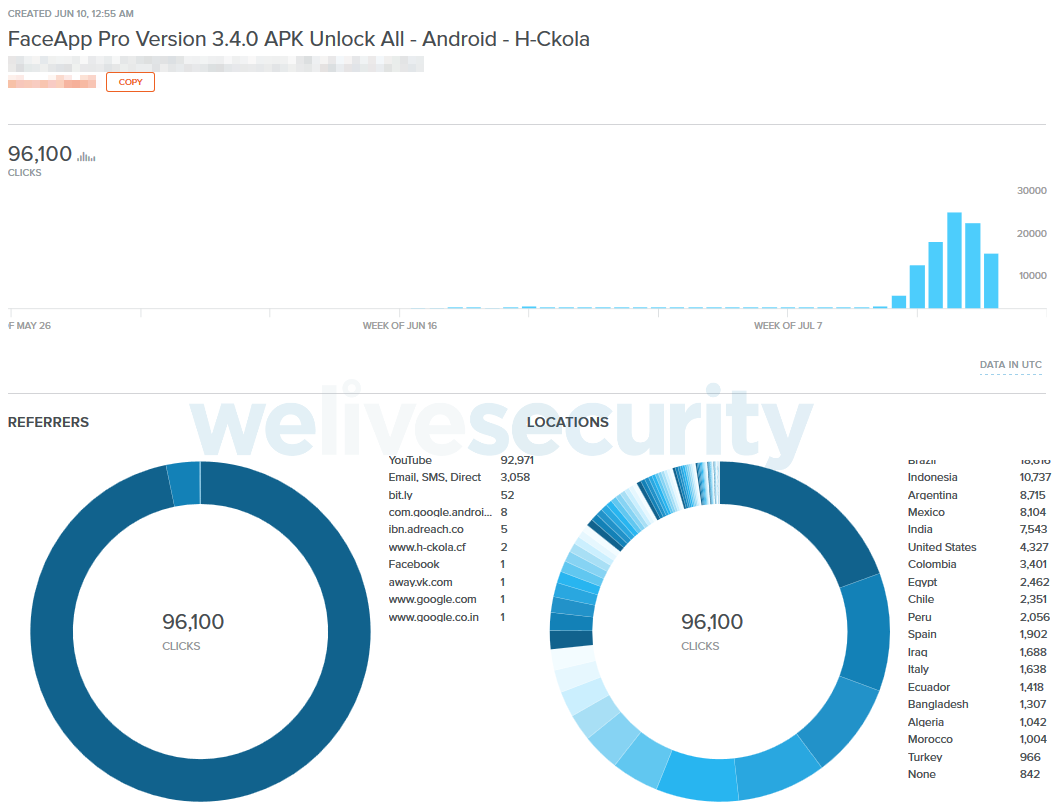
Figure 5. Statistics for the link leading to the fake “FaceApp Pro” installation package referenced in the YouTube video above
Conclusion
Hype attracts scammers, and the bigger the wave, the higher the risk of falling victim of a scam. Before joining the hype, users should remember to stick to basic security principles.
Regardless how exciting the topic is, avoid downloading apps from sources other than official app stores, and examine available information about the app (developer, rating, reviews, etc.). Especially in the Android ecosystem, there are fakes around every popular app or game; fortunately, the chances are good for security-conscious users to tell the fakes from genuine offerings. As insurance for the case the user falls victim to a scam, having a reputable security app installed on a mobile device can help prevent some negative consequences.
Indicators of Compromise (IoCs)
| Hash | ESET detection name |
|---|---|
| 73b3a89f073d15ac374676a8f32c591e7425959f | Android/ScamApp.BX |
| 28c7401c30c563da9e8bd0eb68574e1882c0e170 | Android/ScamApp.BY |





