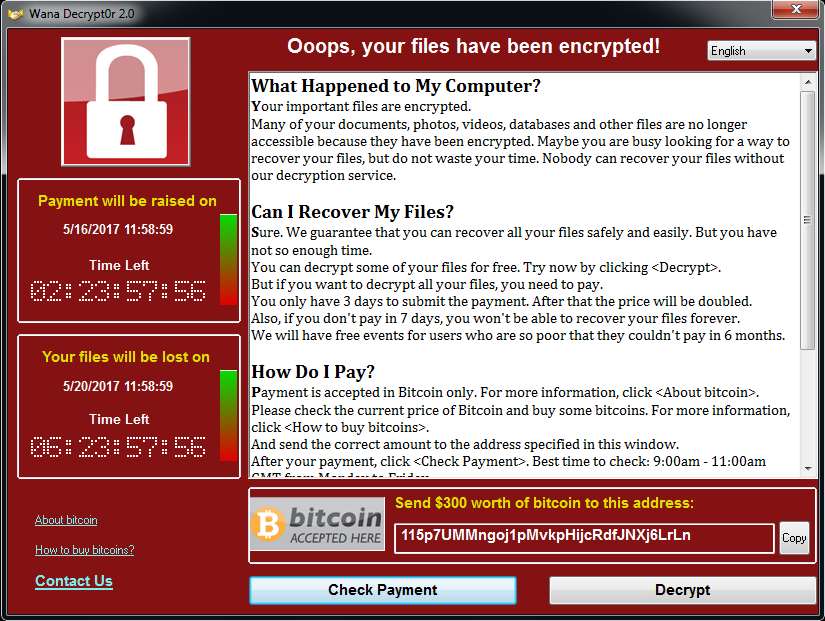
British malware analyst Marcus Hutchins, who was propelled to cyber-stardom after he helped neutralize the outbreak of the WannaCryptor aka WannaCry ransomworm in May 2017, has pleaded guilty to two charges related to creating and distributing malware between 2012 and 2015.
Known online as MalwareTech, Hutchins made a name for himself in the midst of the WannaCryptor outbreak after he inadvertently turned on the ransomworm's ‘kill switch, causing WannaCryptor’s propagation to slow to a trickle within hours. Much to the astonishment of many in the security community, however, he soon faced charges in the United States that he himself had written malware before embarking on a career in cybersecurity research.
Fast forward two years, and the plea deal filed at a court in Wisconsin reveals that Hutchins, 24, has admitted to helping author and sell two Trojans between July 2012 and September 2015. Called ‘Kronos’ and ‘UPAS Kit’, the two pieces of malware were designed to steal people’s banking login information.
Each of the two charges to which Hutchins has admitted guilt carries a maximum of five years in prison and a penalty of up to US$250,000. Meanwhile, eight other counts have been dropped by federal prosecutors.
In a statement on his personal website, Hutchins writes that he assumes full responsibility for and regrets the mistakes he made in his teenage years. “Having grown up, I’ve since been using the same skills that I misused several years ago for constructive purposes. I will continue to devote my time to keeping people safe from malware attacks,” wrote Hutchins.
Hutchins was arrested at the airport in Las Vegas in early August 2017, just as he was about to board a flight home after attending the Black Hat and DEF CON security conferences. Federal prosecutors pressed six charges against him over his then-alleged Kronos’ authorship, before four more charges related to UPAS Kit were added to the case in June 2018. Hutchins was released on bail shortly after being corralled, but was barred from leaving the United States. Until late last week, he denied any wrongdoing.
We have previously published several articles that looked into the WannaCryptor outbreak and its aftermath, so you may want to refresh your memory with any (or all) of these pieces:
WannaCryptor aka WannaCry: Key questions answered
WannaCryptor, aka WannaCry interview with Stephen Cobb and Marc Saltzman
WannaCryptor: Are governments and financial regulators to blame?
EternalBlue: Is your PC patched against the WannaCryptor worm vulnerability?
12 months on, what are the lessons learned from WannaCryptor?
One year later: EternalBlue exploit more popular now than during WannaCryptor outbreak