
Vox Emptoris:
"Voice of the Customer"
For more than 30 years, I've had the privilege of assisting people get rid of viruses and other malicious software. In the course of doing so, I've often been asked questions about computer security-related topics that are not product-specific. Some are simple or easily answered; some are complex or require careful explanation and additional research. In this column, I'll address questions I've been asked, and that you may ask, that don’t fall into the kind of categories answered in product manuals or KnowledgeBases. Whether or not you are an ESET customer, feel free to ask and I'll give it my best shot to answer!
In July 2018, ESET North America started getting queries from people (Fred, Bunny M., and others) who had received emails claiming that their computers had been hacked, and that the attacker had videos of them watching "adult content." These were examples of so-called "sextortion scams"; we wrote about it in July 2018, in a post entitled I saw what you did…or did I?
Over the past few days, we've started getting new reports of similar, but noticeably different, blackmail attempts; indeed, I've received several in my own personal mailbox (Ha! Nice try). So it's time to revisit this; thanks to Barry G., Tim R., and others for bringing these to our attention.
When we wrote about this scam before, it was a case of "teach you to recognize a particular phish, and you'll be safe from that specific attack"; today and in a few follow-up posts, I'll try to teach you to recognize all phishes, so you'll be safe from any similar attack. [No, technically these aren’t phishing attacks, but they do try to extract money from their intended victims, so: "close enough." Maybe we'll do a series on recognizing actual phishes in future posts.]
Since the scammers are always rolling out new traps to try to ensnare their intended victims, this will be a process that needs regular updating; indeed, to cover all I want to discuss and not make it into War and Peace, I'm breaking this discussion up into more-easily digested sections. This may be an ongoing project for Vox, so let's get started.
First, let's look at blackmail in general – it's pretty much the same for cyberspace as it is in-person. Blackmail requires several elements: (a) something the intended victim would want to keep secret, (b) some kind of proof that the blackmailer has that "something", (c) a threat, and (d) a way provided by the blackmailer for the intended victim to "avoid" that threatened action – usually money, though there are other possibilities.
With that in mind, here's an example of one of the recent sextortion emails:
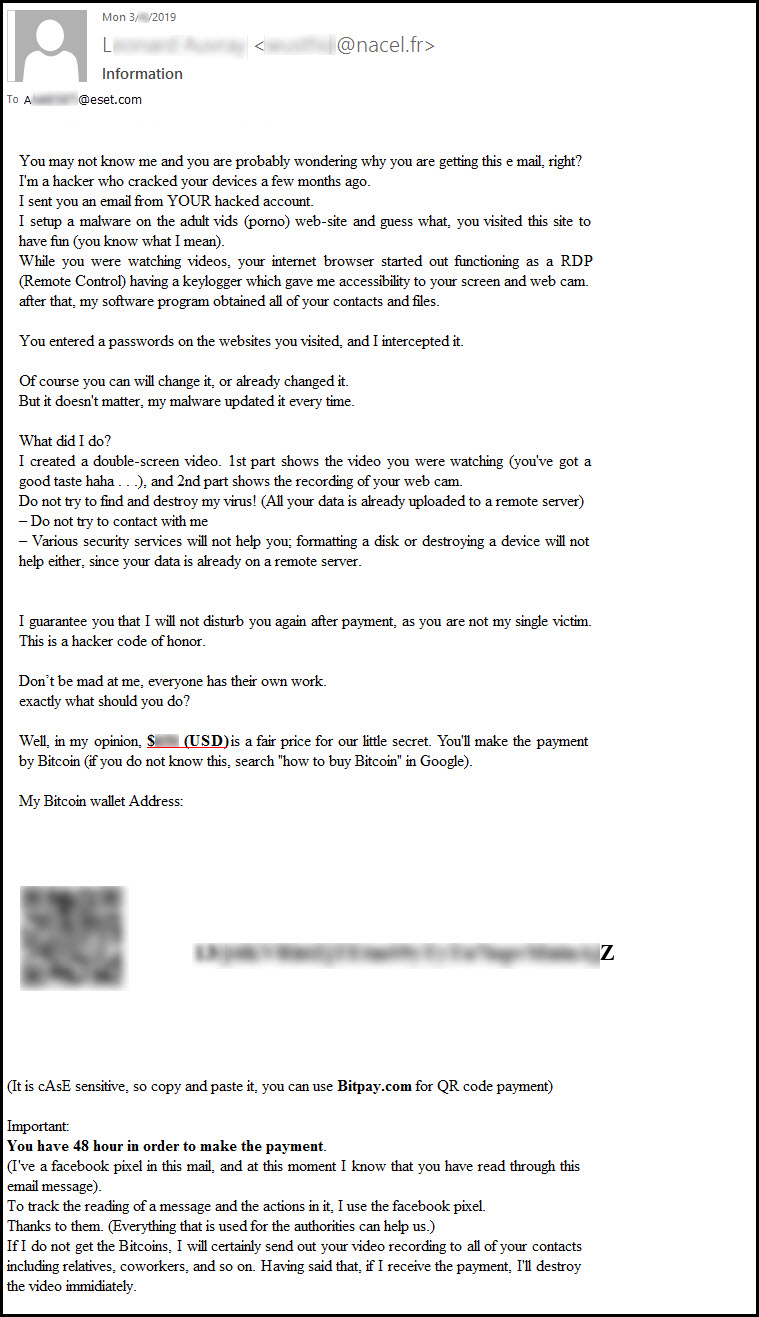
Figure 1: New sextortion scam, March 2019
The Secret
Here, the secret is that the intended victim is accused of viewing adult material that is, at best, embarrassing if revealed to family, co-workers, etc. In our example above, we have:
Figure 2: The Secret
So: is the secret real? Well, if you never have visited a porn site (on purpose, anyway), or someone who hasn't visited such a site more recently than, as the attacker states, "a few months ago", then you KNOW the email is a scam, and hence you can ignore it.
But what if you're someone who does view adult content, at least occasionally? Then, according to 'Net statistics, "Welcome to the club." And what if, as reported in the Wall Street Journal's Twitter feed in 2013, you are one of the "40 million Americans [who] are regular visitors to porn sites – including 70% of 18- to 34-year-olds"? Then the threat is still fairly empty. Here's why: The mere fact that so many people view adult material, and that it is considered taboo in many circles, makes this secret one that the potential victim may well want to keep secret, and hence it is an attractive target for the blackmailer: the attacker can make a claim that may not be based on fact in any way, but that sounds convincing, and many potential victims will have cause to believe the attacker's claims. So the attacker can just "spray and pray" that some potential victims get hooked on the bait. But to test whether this is the case here – that the attacker actually knows the secret – we need to dig more deeply.
The "proof"
In our example, the supposed proof is threefold:
- there's the "fact" that the email came from the victim's own email account (and the implication that the attacker controls that account),
- that the attacker claims to have hacked into your computer, and
- that the cyber-blackmailer recorded evidence of "your activities".
In our example, we have, for the first "fact":
Figure 3: Email To: and From:
In this case, there's a classic fail – the attacker, or more likely, the sextortion kit the cybercriminal purchased on the Dark Web – didn't even appear to send the email from the victim's account. Indeed, neither the To: address's name, nor domain, match that of the From: field. But other examples I've seen do have what appear to be matching To: and From: fields.
So: for cases not so obviously bogus: is this real?
Not likely – the From: field of email is trivial to forge; we'll look at this in more detail in a future Vox post. Suffice it to say that a claim that one's email account has been hacked, based solely on the From: field, is vacuous. While potential victims might not know this, even the least competent attacker should, so that attacker would be inclined to provide better, or at least more, evidence if the account actually had been hacked. So ignore this so-called "proof" – but it's not a bad idea to change the password on your email account anyway, to a unique, difficult-to-guess password. This uniqueness is key; we'll come back to this later. And you can always contact your email provider to ask if there has been any unusual activity over "the past few months." Note that if you are able to change your password, there's an increased chance that there has been no attack: if I were a cybercriminal and I owned your account, I'd probably be inclined to change the password so that YOU couldn't change it, and thereby lock me out.
Next, there's the assertion that the attacker hacked into your computer:
Figure 4: Claim of having hacked the victim's computer
Notice that this is different from hacking into your email account, since they do have unique (and hence: different), difficult-to-guess passwords, right??? Regardless: the attacker is claiming to have broken into your computer as well as your email account, which leads us to two cases:
- If real, and the attacker compromised the email account first, there is no direct way to tell what computer is associated with you, given your email address. This is why you can send and receive Gmail, for example, using your home computer, your phone, your work computer, and the public computer at your local public library. So how did the attacker, once s/he hacked your email account, then figure out what your computer was in order to hack into it? Answer: "S/he didn’t."
- If real, and the attacker hacked into your computer first, then sure: it would be easier to know what your email address is, of course. But in order to hack into your computer (or "devices"), the attacker would have to get past your computer security software. While the main purpose of computer security software (the anti-malware type everyone has installed – and you DO have top-quality, up-to-date, updated security software on all your devices, correct?? If you're reading WeLiveSecurity, surely you do…) ... where was I? Oh, yes: the main purpose of such software is not to protect against human attacks but rather against automated attempts to compromise your computer, but it also offers at least some protection against the tools an attacker might use to try to break into your machine. So unless the attacker used a zero-day exploit against you, there's a very good chance that the hacking attempt would have failed. And unless your attacker has the budget of a G7 nation, and you are very interesting, 0-days wouldn't be wasted for mere sextortion attempts.So again: how did the cybercriminal hack into your computer? Signs point to "S/he didn't."
Finally (for this example), there's the assertion that your webcam was used to capture video of you and your actions. If, like me, you have a piece of double-sided black electrical tape covering your camera(s), then again: the fraud is exposed. Also, several computer security suites, including ESET, include webcam protection. So get some sort of webcam cover (commercial ones exist, and are inexpensive, if you don't like the electrical tape idea) and consider using security software that includes this protection if you don’t have it already.
What if these tipoffs do not apply to you? Then we proceed to the next phase.
The threat
In our example, the sextortionist threatens to "send out your video recording to all your contacts including relatives, coworkers, etc." unless payment is received. If you still think this email may be true (though we can prove that, in this example, it is not), then ask yourself: "Would this embarrass me?" Apparently, adult content is becoming more and more socially acceptable, so if you are one of the increasing number who aren’t concerned if others know that you access adult content, then again: the cyber-blackmailer, even in cases where the attacker actually has what otherwise would be compromising information, is negated.
On the other hand, if such a release would be embarrassing, then look for these key points: is there a brief time to pay the blackmail demand? Is the email vague? Does it use "computer mumbo-jumbo"? If so, then it's odds-on that the threat is not real. In this case: while the words below do have some meaning, they're intended more to scare than to convince.

Figure 5: The mumbo-jumbo
Also, it's worth noting that properly-configured computer security software is very good at catching keylogger software, so it's pretty unlikely that an attacker could get that on your system without your security software noticing. Another strike against the cybercriminal.
The payment
In this case, the payment demand is for bitcoin – virtual currencies are often used by cyber-criminals. Here, it may shed some light to look at the amount requested: if someone had actually hacked into your machine, then the attacker would probably have some idea of your financial position. Does the dollar amount fit your economic situation? Probably not. And the attacker wants to get paid – if the attacker had real evidence, the cybercriminal might try to rush you, but probably wouldn’t set a deadline. Or at least would try to contact you again if you didn't respond, perhaps setting different terms. But attackers know that people go on vacation and are away from email for various other reasons, so that their requests might not even be seen in the "critical period" … and hence they would be likely to try again, perhaps with more convincing proof. For example, in the case of ransomware – a real threat indeed – the attackers put ransom notes all over the computer (Desktop, Documents folder, etc.), so it's very hard to miss. If the attacker in this case actually had hacked into the victim's computer, rest assured that a similar model would be in use.
Oh, and note that blackmailers almost never settle for "one-and-done." If they can get you to pay once, they'll keep knocking on your inbox to get more out of you. So even if this were real, it would be a fool's errand to pay – and for the fake ones, be sure that victims who respond will be put on a list of those who are prone to fall for such attacks.
What next?
If none of the above "tells" convince you that this (or whatever email you might have received) is a scam, there are other techniques we can use. We'll take a look at these in our next Vox post – some of which are decidedly easier than the specific ones we've presented here.
About Vox
Got a computer security question that's not product-specific? Leave us a comment here or use our AskESET form on the Contact Us page.





