While finishing our analysis on a recent surge in malicious spam targeting Russia, we noticed another, unrelated, JavaScript-fueled campaign reaching new heights in our telemetry. Apparently, the “Love You” malspam campaign from mid-January 2019 has been modified, focusing on Japan.
Based on our telemetry data, this latest “Love you” campaign was launched on January 28, 2019, almost doubling in size compared to the initial waves, as seen in Figure 1. Much like in mid-January, the spam emails distribute a cocktail of malicious payloads, with some updates: we have seen attempts to download a cryptominer, a system settings changer, a malicious downloader, the Phorpiex worm, and the infamous ransomware GandCrab version 5.1.
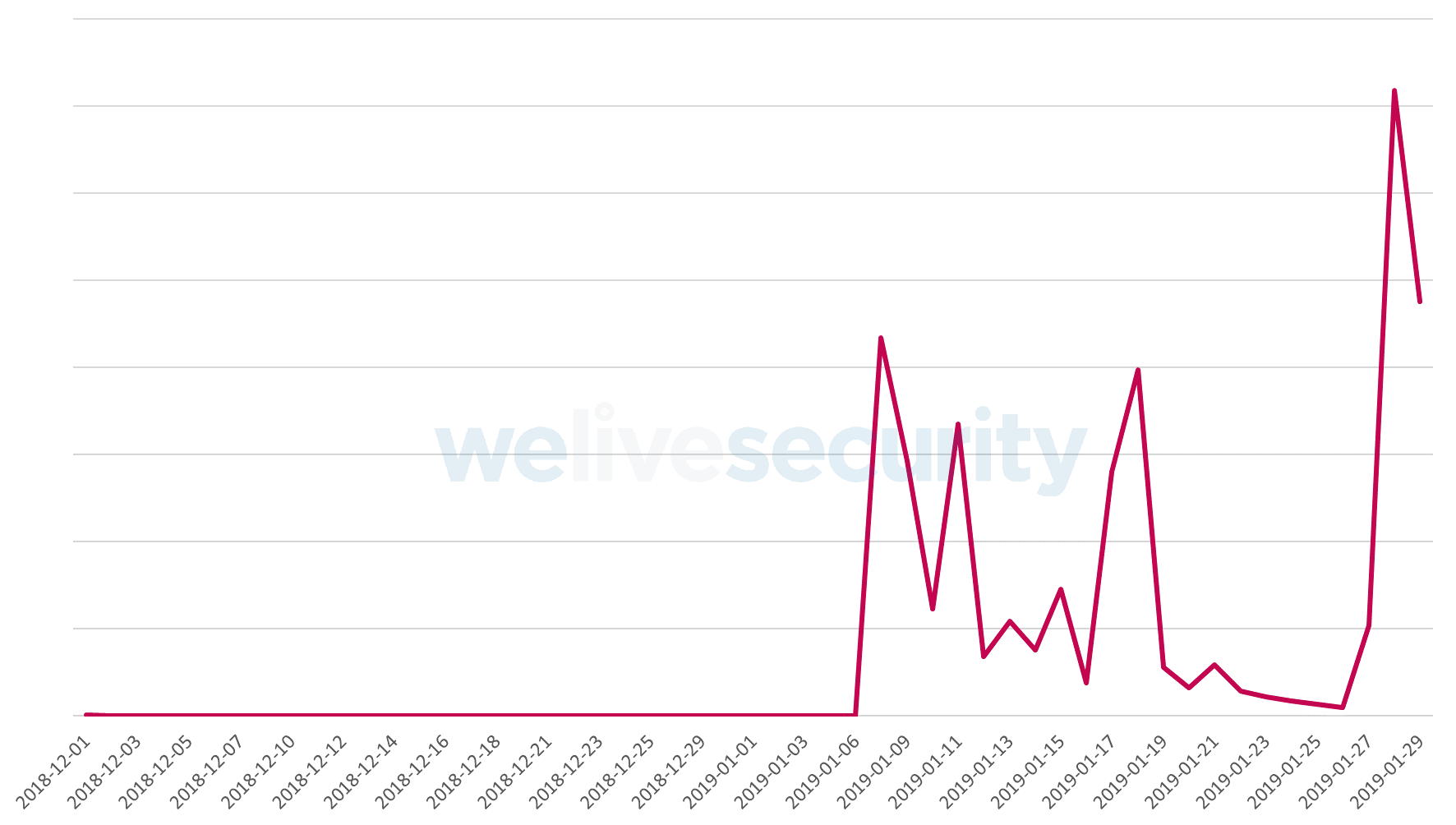
Figure 1 – Detections of malicious JavaScript attachments distributed as part of the “Love you” campaign and its latest wave
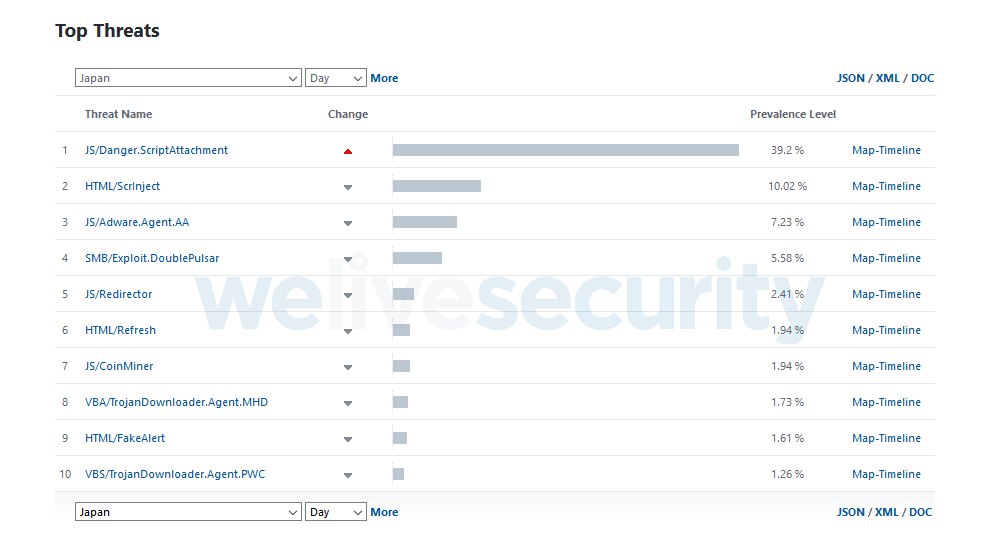
As of January 29, 2019, the vast majority of the detections are in Japan (95%), with tens of thousands of malicious emails detected every hour. On the same day, JS/Danger.ScriptAttachment – the ESET name for malicious JavaScript distributed via email attachments – was the fourth-most-detected threat worldwide and the number one threat in Japan, as seen in Figure 2.
Attack scenario in the Japan-targeted campaign
In this latest campaign, the attackers have altered the messaging of the malicious emails, switching from the romantic theme of the initial mid-January "Love You" campaign to Japan-relevant topics. What has remained the same is the heavy use of smileys in both email subjects and body texts.
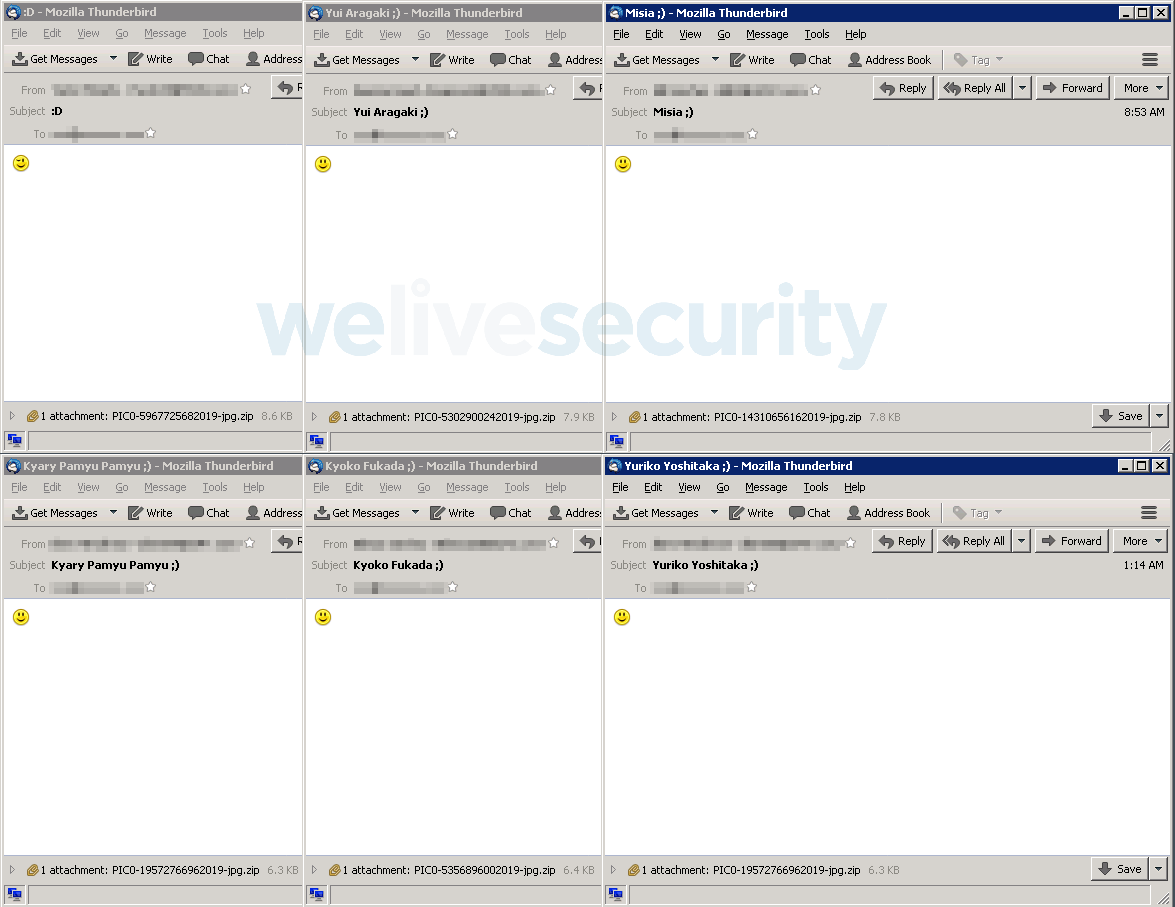
The emails we have seen during our analysis have the following subject lines:
- :D
- Yui Aragaki ;)
- Kyary Pamyu Pamyu ;)
- Kyoko Fukada ;)
- Yuriko Yoshitaka ;)
- Sheena Ringo ;)
- Misia ;)
(Note: These are all popular Japanese entertainers)
The malicious attachments in the analyzed emails are ZIP files masquerading as image files, with names in the format “PIC0-[9-digit-number]2019-jpg.zip”. Figure 3 shows examples of such malicious emails.
The ZIP archives contain a JavaScript file with the same name format, only ending in “.js”. Once extracted and launched, the JavaScript file downloads the first-stage payload from the attackers’ C&C server, an EXE file detected by ESET products as Win32/TrojanDownloader.Agent.EJN. The URLs hosting this payload have had paths ending with “bl*wj*b.exe” (note: filename redacted) and “krabler.exe" and these payloads were downloaded to “C:\Users\[username]\AppData\Local\Temp[random].exe”.
This first-stage payload downloads one or more of the following final payloads from the same C&C server:
- The GandCrab ransomware, version 5.1
- A cryptominer
- The Phorpiex worm
- A language-locale-specific downloader (set to download further payloads only if the language settings of the affected computer suggest the victim is located in China, Vietnam, South Korea, Japan, Turkey, Germany, Australia or the UK)
- A system settings changer
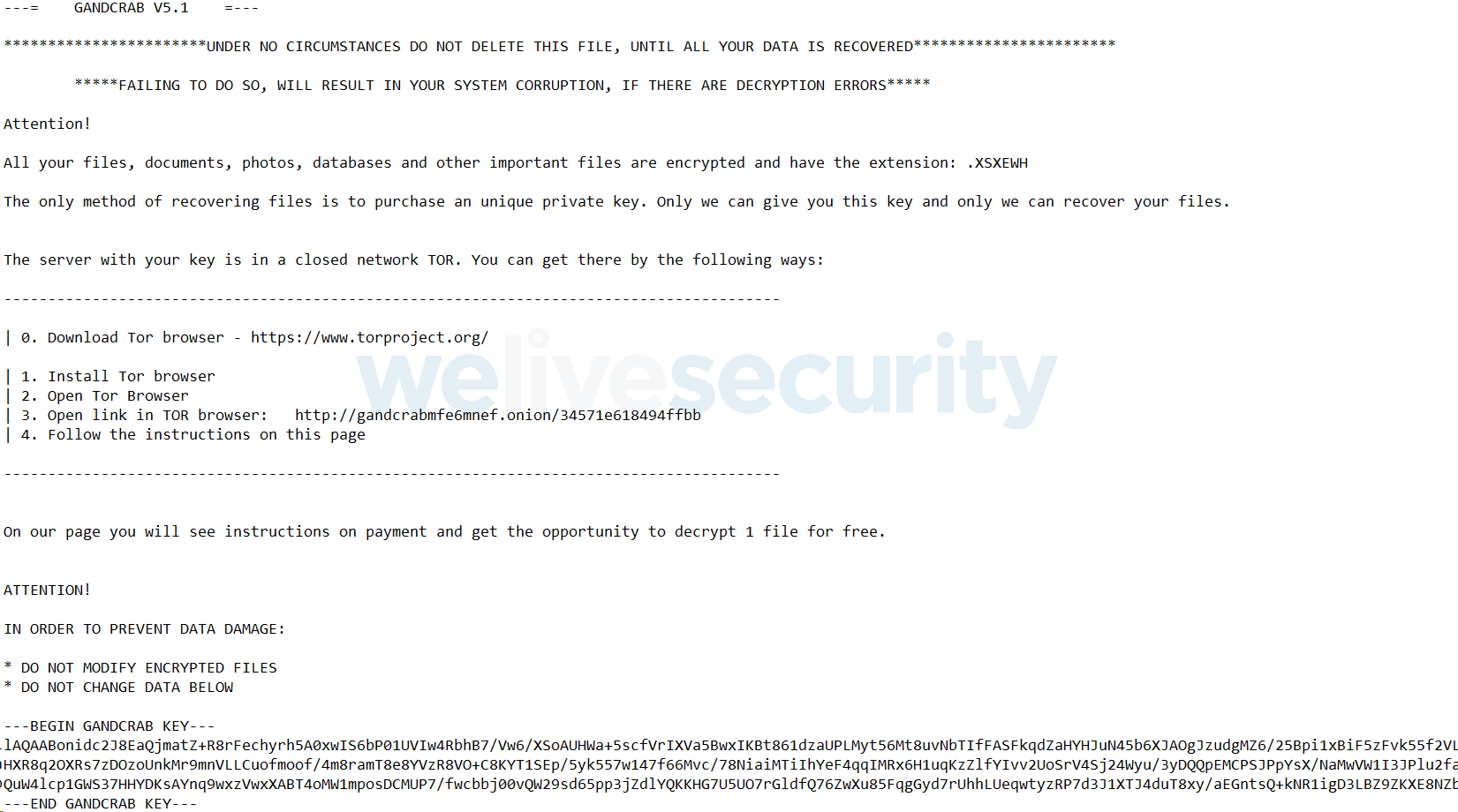
The 5.1 version of the GandCrab ransomware encrypts files and appends a random 5-character extension to their names. Ransom notes containing that extension in both their filenames and their contents are created in every affected folder.
The payloads in this updated campaign are downloaded from the IP address 92.63.197[.]153, which appears to be located in Ukraine, and has been used in the “Love you” campaign from its start in mid-January.
How to stay safe
To avoid falling victim to malicious spam, always verify the authenticity of emails before opening any attachments or clicking on links. If necessary, check with the organization seemingly sending the email using contact details provided on their official website.
For Gmail users, it may be useful to know that Gmail has been blocking JavaScript attachments in both received and sent emails for almost two years now.
Users of other email services, including company mail servers, must rely on their awareness, unless they use some security solution capable of detecting and blocking malicious JavaScript files.
Several different modules in ESET security products independently detect and block these malicious JavaScript files and/or the objects they subsequently fetch.
Indicators of Compromise (IoCs)
Example hashes of malicious ZIP attachments
| 8551C5F6BCA1B34D8BE6F1D392A41E91EEA9158B |
|---|
| BAAA91F700587BEA6FC469FD68BD8DE08A65D5C7 |
| 9CE6131C0313F6DD7E3A56D30C74D9E8E426D831 |
| 83A0D471C6425DE421145424E60F9B90B201A3DF |
| 57F94E450E2A504837F70D7B6E8E58CDDFA2B026 |
| ESET detection name: JS/Danger.ScriptAttachment |
Example hashes of JavaScript downloaders
| cfe6331bdbd150a8cf9808f0b10e0fad4de5cda2 |
|---|
| c50f080689d9fb2ff6e731f72e18b8fe605f35e8 |
| 750474ff726bdbd34ffc223f430b021e6a356dd7 |
| 1445ea29bd624527517bfd34a7b7c0f1cf1787f6 |
| 791a9770daaf8454782d01a9308f0709576f75f9 |
| ESET detection name: JS/TrojanDownloader.Agent.SYW aka JS/TrojanDownloader.Nemucod.EDK |
Example hash of the first-stage payload
| 47C1F1B9DC715D6054772B028AD5C8DF00A73FFC |
|---|
| ESET detection name: Win32/TrojanDownloader.Agent.EJN |
Example hashes of the final payloads
| Payload | SHA-1 | ESET detection name |
|---|---|---|
| GandCrab ransomware | 885159F6F04133157871E1D9AA7D764BFF0F04A3 | Win32/Filecoder.GandCrab.E |
| Cryptominer | 14E8A0B57410B31A8A4195D34BED49829EBD47E9 | Win32/CoinMiner.BEX |
| Phorpiex worm | D6DC8ED8B551C040869CD830B237320FD2E3434A | Win32/Phorpiex.J |
| Downloader | AEC1D93E25B077896FF4A3001E7B3DA61DA21D7D | Win32/TrojanDownloader.Agent.EEQ |
| System settings changer | 979CCEC1DF757DCF30576E56287FCAD606C7FD2C | Win32/Agent.VQU |
C&C server used in the campaign
| 92.63.197[.]153 |
|---|