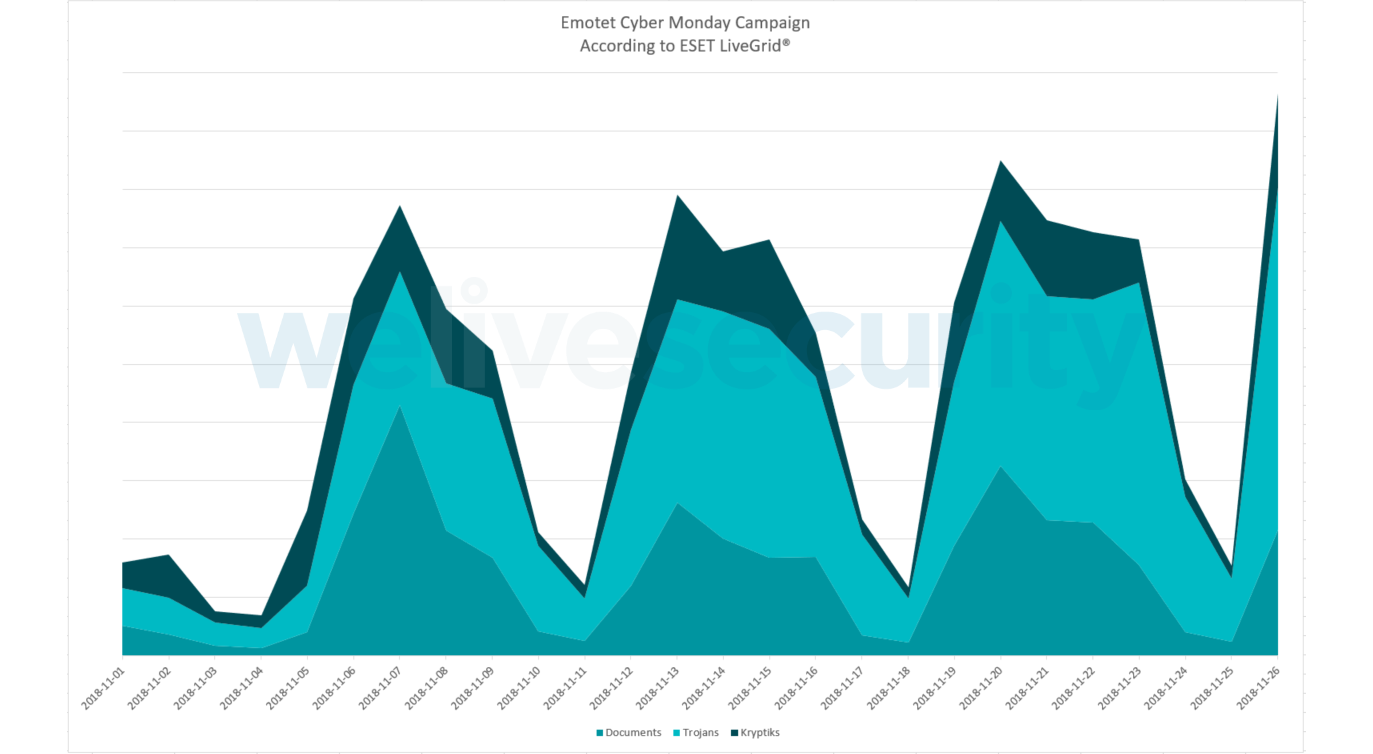
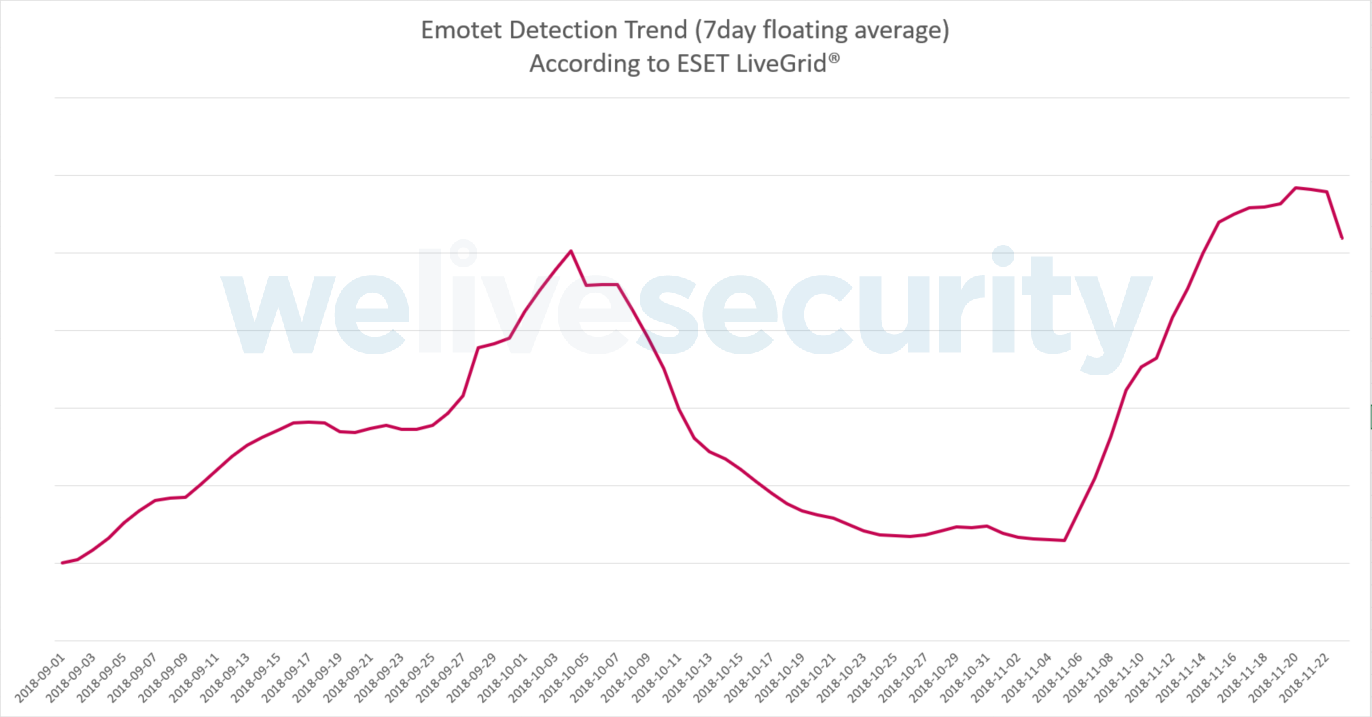
UPDATE (27 November 2018): Even after Black Friday peak, Emotet operators are keeping up the heat. During the large spike seen on Black Friday, black-hats behind Emotet added a new payload, namely the Gootkit banking malware. On Cyber Monday, the attackers doubled down on the online shoppers in the US, Canada, Germany and Mexico, by launching another massive campaign, with detections in the hundreds of thousands. Similar to previous spikes, Emotet is using spam campaigns as the primary distribution channel. ESET is detecting the threat via its multiple protective layers, including ESET Advanced Memory Scanner (Trojans in the chart), ESET DNA Detections (Kryptik), as well as ESET Cloud Malware Protection System and algorithmic detections (Documents).
ESET has detected another large Emotet campaign, probably connected with the increased online shopping and email correspondence around Black Friday. Compared to the previous attacks, the operators have slightly modified their modus operandi. Emotet is still being distributed via spam emails containing attachments with malicious macros or links to such files. Around Black Friday, however, the attachments and links have been serving XML files with a (misleading) .doc extension instead of the previously observed PDF and (actual) DOC files.
As to the secondary payloads, Emotet is currently distributing various banking malware families, including Ursnif, TrickBot and most frequently IcedId. The latter also downloads another payload, Azorult (ESET detects this malware as Win32/PSW.Delf.OSF), known for its ability to steal passwords, credit card details and access to cryptocurrency wallets. TrickBot, on the other hand, has upped its game by adding multiple UK and German banks to the list of its targets. This corresponds with German and English subject lines of the spam emails and their contents that ESET described in its latest blog about Emotet.
Looking at the geographical distribution, Latin American (LATAM) countries seem to be amongst the most affected – with Mexico, Ecuador and Argentina leading the list (with hundreds of thousands of detections). The United States is in the top five targeted countries, while the UK and South Africa have also made the top ten.
Indicators of Compromise (IoCs)
Emotet payloads
| 02b614654f27b67aa3efcf94dcad3875696315ab | TrickBot |
|---|---|
| cda88d48c26afd383a996fe2c0ef87514389c189 | IcedId |
| 0977692f1accd541dd7c23eb76f5272d4321d868 | IcedId |
| 3b000e5e6de4d91443563792d69caac95b1038f0 | TrickBot |
| 086bc2718521e6e4aead498b57d20d3b2ec812e9 | Ursnif |
| 202604e7dc6c29ae75ad9f707ebbc8bf5367a631 | TrickBot |
| 844e6a4c31ae473702781603d8cdd5f9b3aa63c5 | IcedId |
| 6481172f509f80ee059b7dc20a2bf995b38aafd2 | TrickBot |
| 9e8972dd0130481e1e42504c7fdda1ffa353e473 | IcedId |
| db82d173e5afe207eeebacb65bd76cdbb67b5955 | TrickBot |
| 350e6b2f5728a17578923ab5a7640e0b57101447 | IcedId |
| 638d2c5b3331cdc2267d1036a9ff8e2efd08b316 | IcedId |
| 3c3624bfd75285c0d69f4867cc2adc5fb538888f | IcedId |
| f75e600d29189065208d116602a2a6fccebf1927 | IcedId |
| e38d371e17eeb34b6f94d05a208d0eb8a3b88f37 | IcedId |
| 765c272f914e85332d6e6a16e62645764f417379 | TrickBot |
| ea24d6f25077f8a82c5a09e0b22040293b8a50d6 | IcedId |
| d5d1c5c1af7c4e0346367cc1fdef0e788f25f1a6 | IcedId |
PSW.Delf.OSF – AZORult
| 3e435f2d58616e28972ad2c422f54e27680fb452 | Win32/GenKryptik.CRSJ trojan |
|---|---|
| f17a455dc012027486ad39c134984cadbe7e31ef | Win32/Kryptik.GMUX trojan |
| 00169e624343cfda397d7a6df77b3e776b54e5ec | Win32/Kryptik.GNEF |