Every now and then, forensic experts or just curious novices will have to investigate technologies using tools that are not always readily available. For that reason, this post explores simple ways that will help you find the right tools for each occasion.
Of course, you can always do an internet search for what you need, but there is so much information available online that the challenge often lies in knowing how to filter it.
Below we provide some very useful options that will help you find specific software tools from their official repositories.
NIST catalog of IT forensic tools
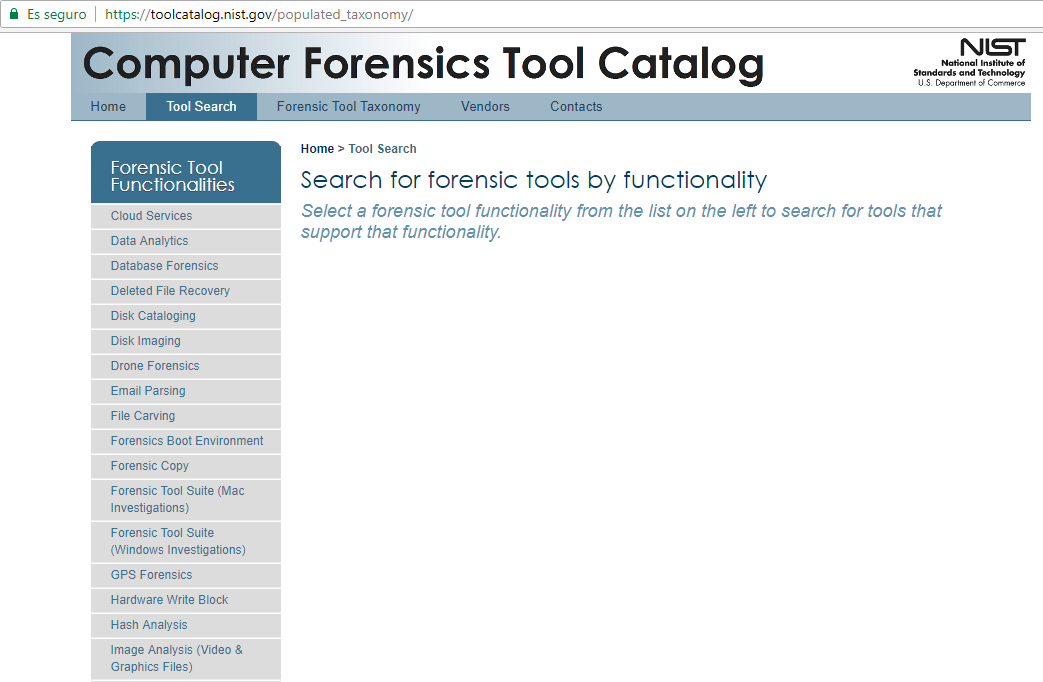
Using the portal of the US National Institute of Standards and Technology (NIST), you will find clear classifications that facilitate easy searches of the different forensic tools filtered by functionality.
As you can see in the image, the catalog can be searched by technical parameters based on specific digital forensic functions, such as Disk Imaging or Deleted File Recovery. Within each category you will find everything from analysis tools for Cloud Services to Drone and Vehicle Forensics, as well as categories such as Data Analytics, Database Forensics, Deleted File Recovery, Disk Imaging, Email Parsing, Hash Analysis, Image Analysis (Video & Graphics Files), Instant Messenger, Memory Capture and Analysis, Mobile Devices, VoIP Forensics, WiFi Forensics, etc.
This catalog was developed jointly by several US agencies, such as the Department of Homeland Security, the Office of Science and Technology Policy, the National Cyber Security Division, and the Computer Forensics Tool Testing Program of the National Institute of Standards and Technology.
The portal is divided into three sections: a search function for finding tools, a page for providers to enter information about their tools, and a description of functions and technical parameters.
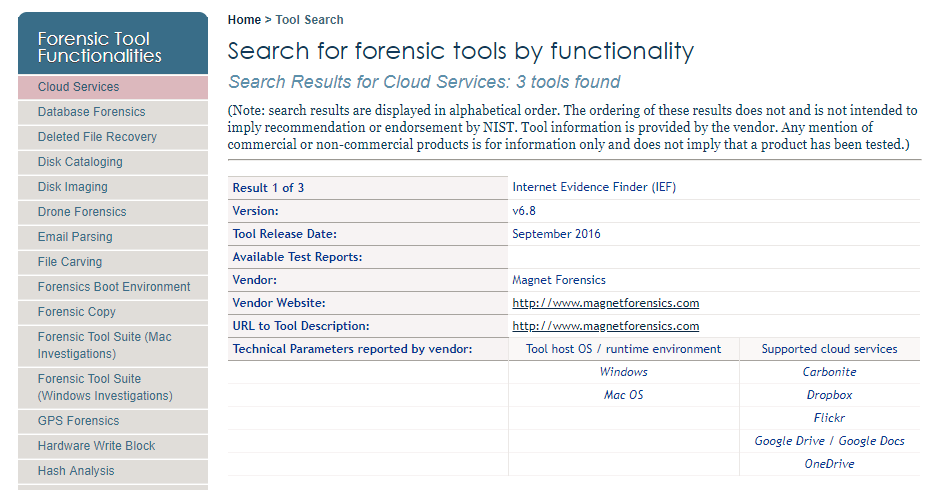
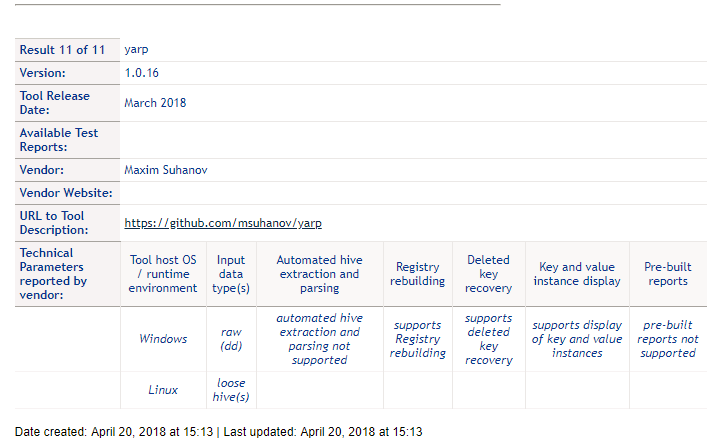
In the image above you can see the search result for forensic analysis tools for cloud services, and in the image below, a result linked to the Microsoft Windows Registry.
It should be noted that the providers enter the information for each tool. The portal clarifies that any mention of a product, whether commercial or not, is for informational purposes only and does not imply that a product has been tested.
This compendium of tools also provides a general overview of digital forensic analysis tools, and shows where gaps exist; i.e., functions for which no tools have been developed so the analysis may be more complex or purely manual.
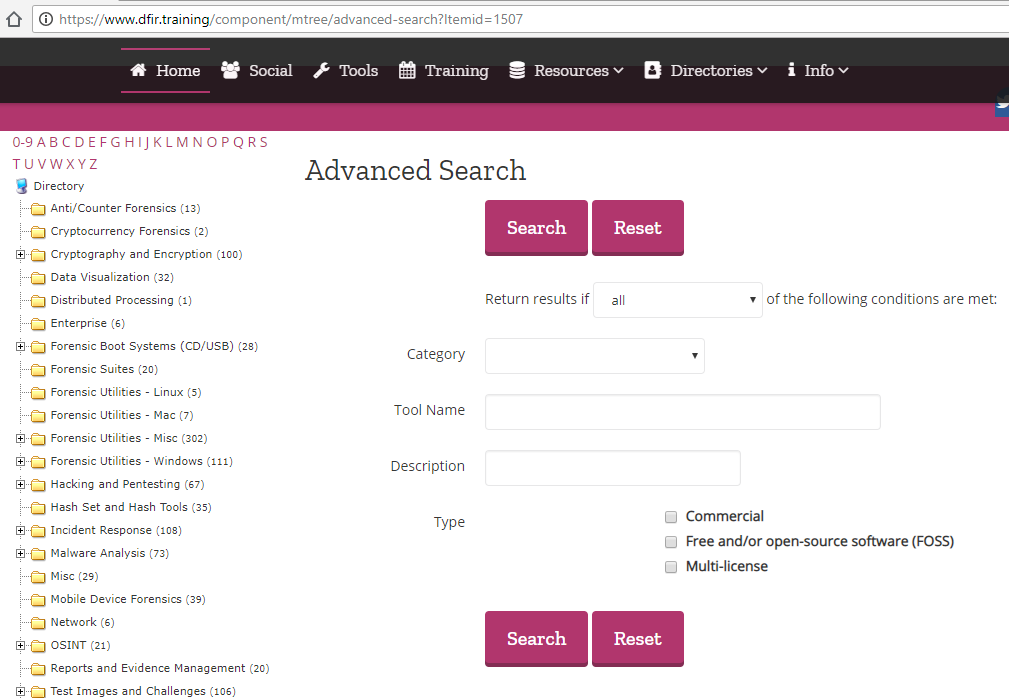
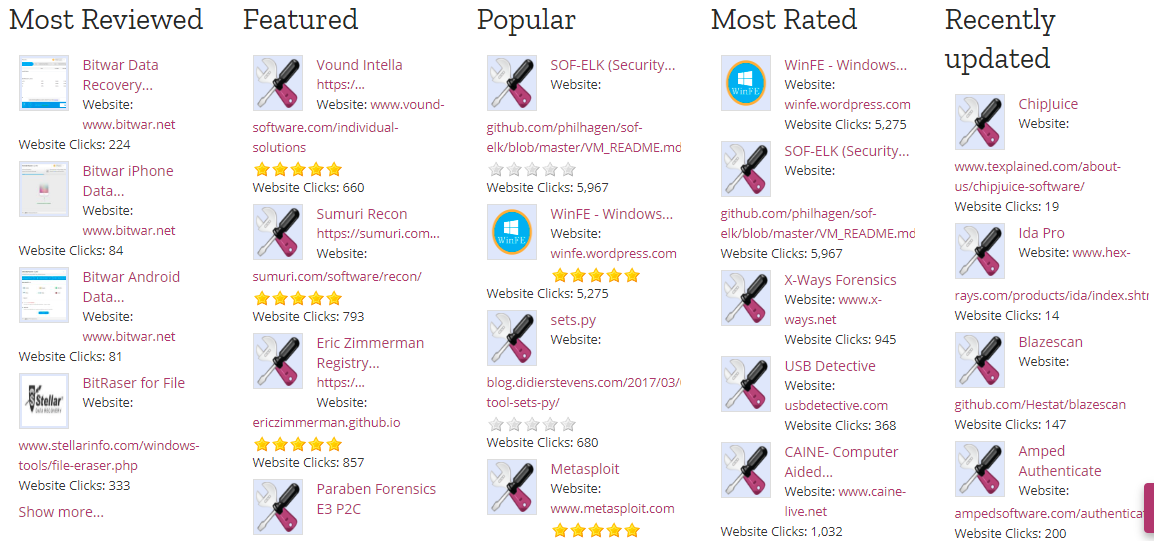
DFIR Training catalog of IT forensic tools
Another very interesting option is available from the DFIR community, which offers a very comprehensive portal with a large amount of resources for responding to forensic incidents. In addition to a search option with a very user-friendly graphical interface, it allows users to leave reviews of the tools available.
It also has a utility for viewing applications with the most ratings, the most downloaded, the most up-to-date, etc.
On top of that, it has plenty of resources for testing tools, as well as quick guides and infographics.
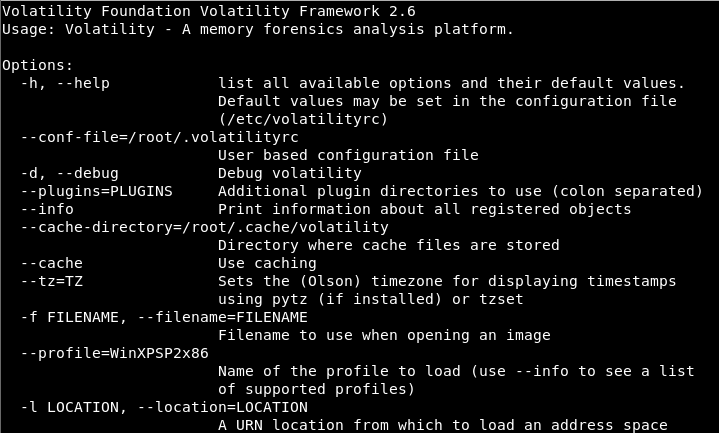
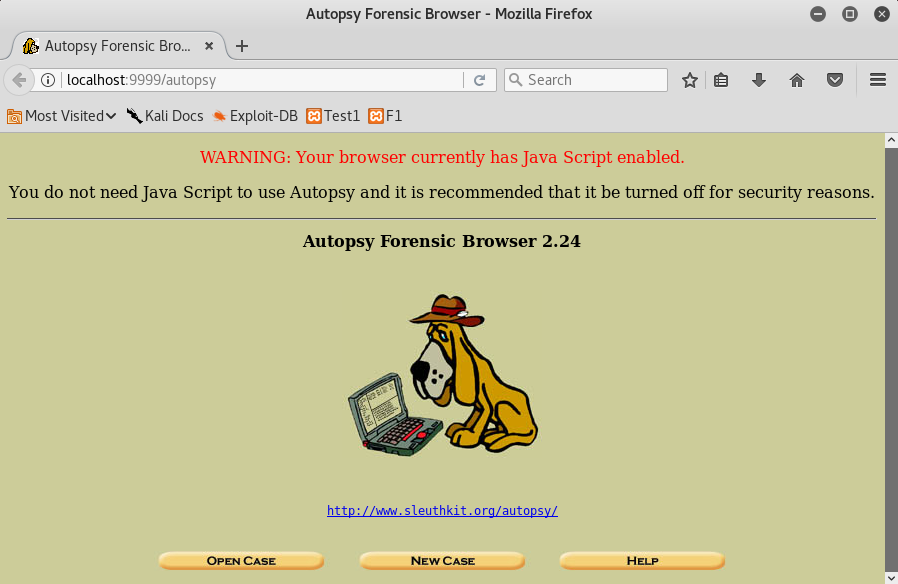
And we mustn’t forget to mention that many of the Linux distributions aimed at pentesting have the most used tools, as you can see in the images below.
Lastly, it is important to remember that in many cases, the tools that you need are already configured and preinstalled on distributions more specifically aimed at forensic analysis, such as DEFT. Before using them, I recommend that you read up a little about how to use them, best practices, and update to the latest version available.
And so you have no more excuses. Throughout this post we have shown you where to find the tools and resources you need to start practicing or perfecting your skills in this exciting world of forensic analysis.