In the official trailer to a 1965 horror-thriller film, a series of land-line telephone handsets (remember them?) are shown ringing, and the voice-over says in an increasingly urgent voice, "Don't answer it!!"
The movie is about two bored teenagers who make random prank phone calls. Eventually, they make several calls where, when the victim picks up the receiver, the teens say "I saw what you did, and I know who you are!" All this mischief is harmless enough, until they have the misfortune of calling a man who has just killed his wife ... then more murder and mayhem ensue.
Skip forward over fifty years -- we don't use the land line phone much these days, and email wasn't around back then. In what probably is not an homage to I Saw What You Did, cybercriminals have taken a page – or a snip of celluloid – from this movie, but changed the roles of the players: now the "prank caller" is inflicting the horror on the recipient of an unpleasant email, where the attacker claims to know something the potential victim would not want to be revealed.
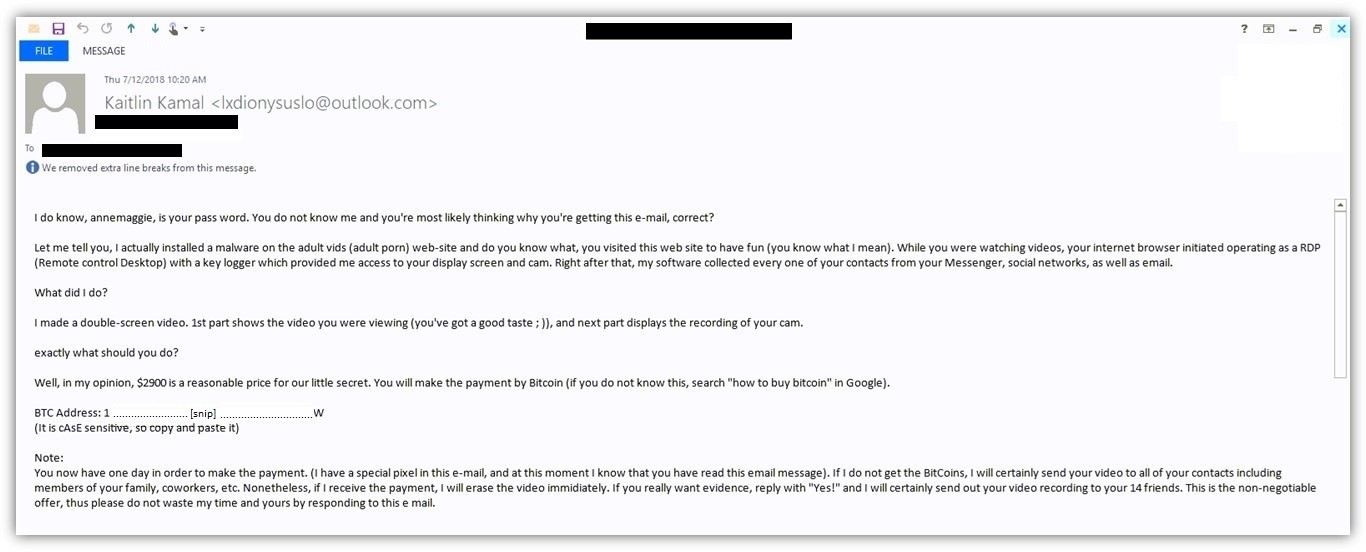
In this case, it's a variant of older scams categorized as "Scareware", where the attacker claims (falsely) to have evidence that the email recipient has visited a website with adult content. We've seen these before, perhaps more cleverly posed, in web pages that sometimes lock the computer and display a message that law enforcement is charging a penalty for a violation. Moreover, some variants used geolocation to display the local law enforcement authority for the location of the computer, e.g., the FBI for computers in the US, the RCMP for machines in Canada, etc.
What's new about this variant, which ESET has been detecting and blocking for about a week, is that it sends the password of one of the recipient's accounts, in order to establish more legitimacy:
If the attacker has your password, after all, s/he must know everything you've done, right?
Well, not quite.
As we've documented on WeLiveSecurity throughout the years, data breaches are an all-too-common occurrence, and they often compromise millions of accounts. Some of these breaches include both email address and some sort of password … not necessarily affiliated with the email address. That is, the password might be for your Gmail account – or it might be for your computer login, or banking PIN, or whatever; typically, it's not clear exactly how the data in the breach are related, except that they "go together."
Anyway: yes, the attacker knows a real password used by the targeted individual, but it may be the password for an account where the password was changed long ago, or even for an account that no longer exists. It's just a shot in the dark or, to go with the horror movie metaphor, a wild stab.
What can you do to protect yourself? Several things – we'll consider those in considerable depth in a follow-up piece to appear here on WeLiveSecurity within the next couple of days. But the quick-and-dirty answer is "If the password and email address 'match', then the attacker probably got them both from a breach, such as the recent one at Equifax; if the text looks anything like the example text above, it's almost surely bogus." In the aforementioned follow-up piece, we'll investigate, among other things, how to check to see if the email address was indeed part of a known breach, and what to do if it is.
Bottom line: If you receive a suspicious email, even if it appears to be from someone you know and trust, that advice from half a century ago still holds true: "Don't answer it!"
Acknowledgement: Props to my colleague Peter Lieu for bringing this to my attention and providing the screenshot. Thanks, Peter!