At the bottom of this article is an expanded list of routers believed to be at particular risk from the malicious code known as VPNFilter, according to ongoing research by Cisco’s Talos Intelligence Group. These latest findings underscore the importance of rebooting routers, as described at length in this WeLiveSecurity article.
With 56 additional models and five new vendors impacted, it is increasingly likely that even more will be identified. This reinforces previous advice: you should take action regardless of the make or model of router you are using (unless you have received solid assurances from your ISP or vendor that your specific router is not vulnerable).
What’s going on here?
Hundreds of thousands of routers in more than 50 countries have been compromised by malware dubbed VPNFilter. When placed on a router, this malicious code can spy on traffic passing through the router. The malware can also “brick” the device it runs on, rendering it inoperative.
Like a lot of malware, VPNFilter is modular and can communicate over the internet with a Command and Control (C2) system to download additional modules. Research into VPNFilter’s capabilities is ongoing.
Routers are specialized computing devices that direct traffic between networks, for example, between the network in your office and the global network known as the internet. Routers have three places to store code and information: regular memory, which is “volatile” and loses its contents when it loses power; non-volatile memory that retains its contents even when the power is turned off; and firmware, the contents of which are relatively difficult to change.
Much of VPNFilter’s code resides in volatile memory and is wiped out by a reboot or “cycling the power” (i.e. power it off – wait 30 seconds – then power it on again). That is why the security experts and the FBI recommend rebooting your router.
However, a reboot does not remove code that VPNFilter may have written to non-volatile memory. Clearing non-volatile memory requires a device reset, but you should NOT perform a reset unless you know what you are doing (see the instructions and advice in this related WeLiveSecurity article).
If your router is supplied by your ISP you should contact them for instructions if they have not already alerted you and advised you of the situation.
Other steps to consider are upgrading your router to the latest firmware, changing the default administration password, and disabling remote administration. Instructions to perform these functions can be found on the router maker’s website.
Yes, you probably do have a router
I am sure there will be more articles related to VPNFilter and router security on WeLiveSecurity in the coming days. We already get the sense, based on questions from readers so far, that knowledge of routers and how to secure them varies considerably within the population of router users.
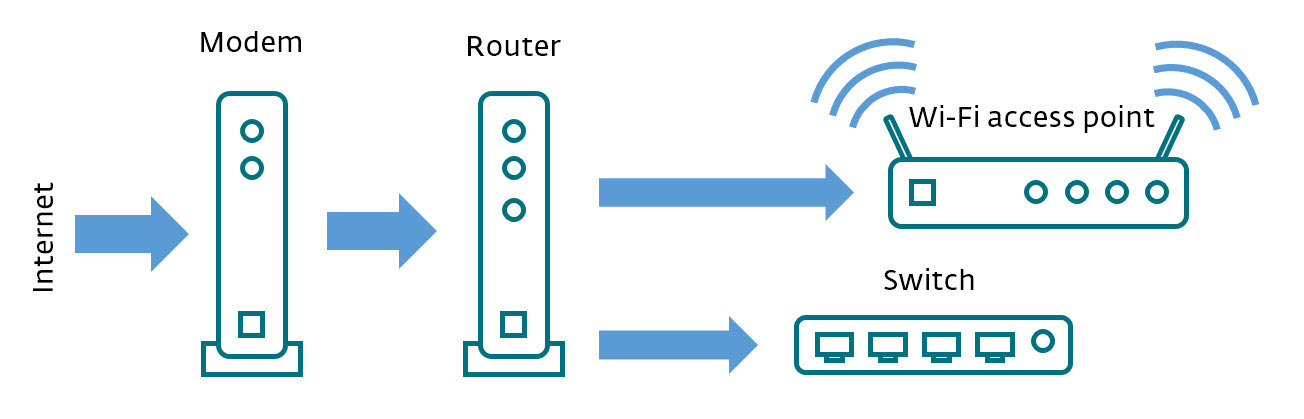
One basic question – do I have a router? – is actually trickier to answer than you might think. Many homes and small offices have a variety of boxes that work together to deliver the internet to their computers, smartphones, tablets, smart TVs, clever thermostats, and so on.
That delivery can be wireless, via a Wi-Fi access point, or wired through Ethernet cables, via a switch. The signal from your ISP may need to go through a modem before the router sends it onward to the right device. The following diagram might help visualize this:
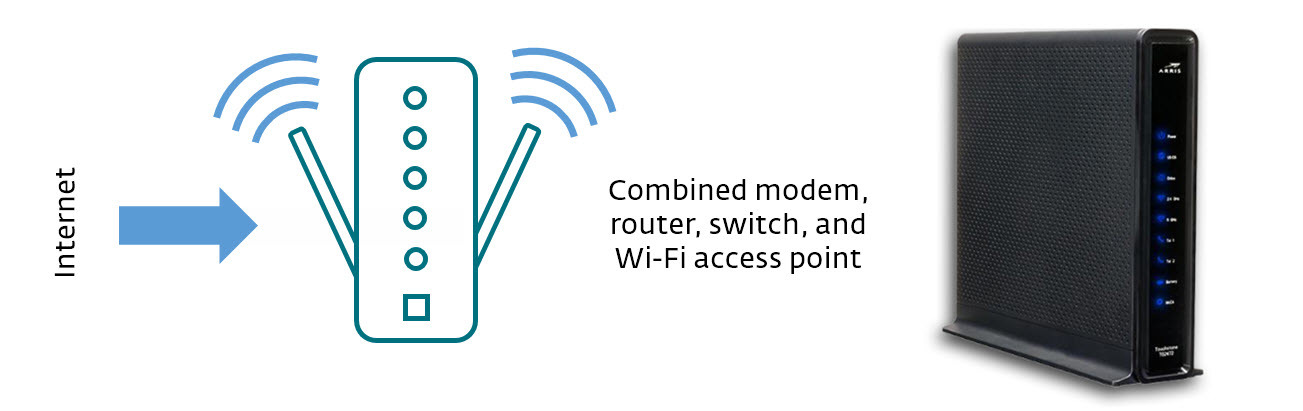
Fortunately, but sometimes confusingly, all of that functionality can be provided by a single box, which may not be called a router, even though it has router capabilities (and it may have wireless capability even though it does not have antennae – like the example on the right below, which is similar to the one in my living room).
Hopefully these basic descriptions will help you identify your current setup and you can proceed to reboot the box that is doing the routing. To be honest, if you have multiple boxes instead of one, it won’t hurt to turn them all off and then back on again. Indeed, you may have been told to do that the last time you called your ISP to complain about your internet connection underperforming.
I don’t mean to make light of this threat – VPNFilter is clearly very nasty malware which we now know has man-in-the middle (MITM) attack capabilities (see Talos update). That means not only can it capture traffic passing through a compromised router, including things like the password you use to log into your online bank account, it can also modify information sent to you, for example, displaying an incorrect balance in your account. So don’t put off that router reboot, and consider a reset, once you have read up on how to do that safely.
Important note to enterprises
Reporting on this very powerful and very nasty VPNFilter malware has stressed that the “at risk” devices are home office and small office routers, but that doesn’t mean enterprises have nothing to fear. Experience tells us there are likely to be some of these devices on most big company networks or connecting to those networks. They could be a part of the “shadow IT” that haunts every enterprise, or installed in branch offices where policies that prohibit the use of such devices are not well enforced.
And then there is the question of employees working remotely, connecting to your internal network, logging into servers for maintenance, and so on. Now would be a good time for your cybersecurity folks to study the details of the VPNFilter malware and determine if it poses a risk to the confidentiality and integrity of those connections.
Important note re: Modbus and SCADA
So far, the focus of VPNFilter coverage on WeLiveSecurity has been defensive measures - router reboot/reset - for home office and small office users. However, as we learn more about the modular capabilities of this malware, the need to alert different user communities will likely expand. For example, the energy and manufacturing sectors need to be aware that VPNFilter can monitor network traffic for Modbus TCP/IP packets. This suggests that the folks behind the malware are interested in discovering SCADA (supervisory control and data acquisition) systems like those used in power generation, transmission, and distribution plants (and their interest is unlikely to be benign).
Expanded list of devices known to be at risk
Asus: RT-AC66U, RT-N10, RT-N10E, RT-N10U, RT-N56U, RT-N66U
D-Link: DES-1210-08P, DIR-300, DIR-300A, DSR-250N, DSR-500N, DSR-1000, DSR-1000N
Huawei: HG8245
Linksys: E1200, E2500, E3000, E3200, E4200, RV082, WRVS4400N
Mikrotik: CCR1009, CCR1016, CCR1036, CCR1072, CRS109, CRS112, CRS125, RB411, RB450, RB750, RB911, RB921, RB941, RB951, RB952, RB960, RB962, RB1100, RB1200, RB2011, RB3011, RB Groove, RB Omnitik, STX5
Netgear: DG834, DGN1000, DGN2200, DGN3500, FVS318N, MBRN3000, R6400, R7000, R8000, WNR1000, WNR2000, WNR2200, WNR4000, WNDR3700, WNDR4000, WNDR4300, WNDR4300-TN, UTM50
QNAP: TS251, TS439 Pro, Other QNAP NAS devices running QTS software
TP-Link: R600VPN, TL-WR741ND, TL-WR841N
Ubiquiti: NSM2, PBE M5
Upvel: according to Talos, malware targeting Upvel as a vendor has been discovered, but researchers have not yet determined which devices are targeted.