Reboot your router! That is the advice put out on May 25, 2018, by one of the world’s most widely known law enforcement agencies: the US Federal Bureau of Investigation (FBI). But should you follow this advice? And if you do follow it, do you know how to do so safely? This article provides some answers, both long and short.
Here are eight short answers, for those who already know what a router is, what a router reboot means, and have experience performing a router reset. If you need to refresh your knowledge of what routers do and how they fit into your network, scroll down to: What is a router?
- What’s going on? As many as 500,000 routers in more than 50 countries were found to be compromised by malware dubbed VPNFilter.
- What should I do? Rebooting your router – turn it off, wait 30 seconds, turn it on again – will help to defeat this particular malware.
- Who is affected? This threat mainly affects small office and home office (SOHO) routers. A list of models known to be impacted is located at the end of the article.
- What if my router is not on the list? It may still be at risk from VPNFilter, so current advice is for all SOHO routers to be rebooted.
- Is a reboot the same as a reset? NO! A reset wipes out configuration information and returns the router to factory defaults. Do not reset your router unless you know how to configure it and have a record of the configuration information, e.g. admin password, SSID, and so on (see rest of the article for more details).
- What if my router is supplied by my ISP? You should contact them for instructions if they have not already alerted you and provided instructions.
- What other defensive measures can I take? Consider upgrading your router to the latest firmware, changing the default password, and disabling remote administration. At the end of the article is a table of links to instructions for doing this work on known at-risk routers, along with links on how to reset them to their factory defaults.
- Does ESET detect this malware? Yes, it is detected as Linux/VPNFilter. However, ESET recommends that you go ahead and reboot your router – read on for more details.
What’s a router?
While techno-snobs may gasp at the idea that there are still people on the planet who don’t know what a router is, I’m going to provide a brief description anyway. I know plenty of bright and well-educated people who have used the internet in their home or small business via a router from many years without ever needing to know what one is or how it works. Some of these folks are now shocked to learn that, not only is their router a computer, it’s a computer that criminals may try to exploit in numerous ways.
The term router comes from the fact that these devices direct traffic between networks: they literally route data from one digital device to another. For example, when you use your laptop in your home to read your email, the messages typically get to your laptop through equipment that came with your internet service, or which you purchased when you set up internet service.
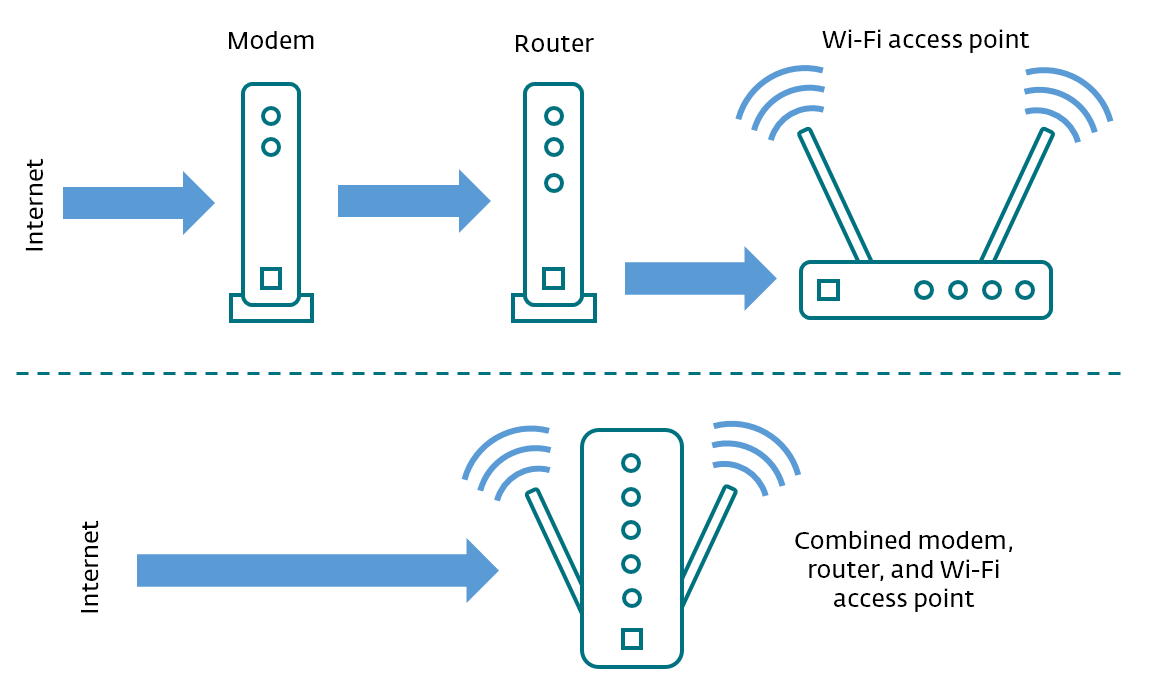
While there are many possible equipment configurations, most include the following functions: modem, router, Wi-Fi (wireless) access point. As shown in this diagram, these functions may be performed by separate devices, or they can be combined into a single box:
The modem takes the signal from your ISP (internet service provider) and converts it to standard network traffic (Ethernet). When your incoming email reaches the router, it decides where to direct it. In the “old days” before Wi-Fi there would be an Ethernet cable going from your router (or modem/router) to your laptop. Today, many homes and small offices are using wireless connections. In that case the traffic, like that email coming to your laptop, or your tablet, or your smartphone, gets routed through the wireless access point.
(Most of today’s home and small office internet connection equipment supports both wireless and wired connections, so there may be a wire from your router to your printer or a Network Attached Storage (NAS); many smart TVs use a wired routed connection to stream video from the internet.)
Clearly, your router is doing a lot of work – handling traffic that ranges from email to web surfing, printing, streaming music and video, and enabling online gaming. A router is also how most IoT (Internet of Things) devices connect to the internet, things like smart thermostats, alarm systems, and security cameras.
To do all that work, computing power is required. That is why routers have evolved to become specialized computer systems in their own right; which brings us to the FBI’s advice about rebooting routers.
What did the FBI say about routers?
On May 25, the FBI issued a statement with this headline: “Foreign cyber actors target home and office routers and networked devices worldwide”. This was in response to the discovery that “cyber actors” had used malicious code (malware) to compromise a whole bunch of routers and other equipment, like NAS devices.
In this context, the term "compromise" means these “cyber actors” executed their code on people’s devices without their permission. This malware, which has the ability to collect information flowing through the device but can also render the device inoperable, has been dubbed VPNFilter by the researchers in the Talos threat intelligence group at Cisco (their first report on VPNFilter has many of the technical details).
Fortunately, the part of VPNFilter that could be used to spy on your router traffic, and/or disable the device, can be removed with that classic IT move: turn it off and on again. So the FBI issued this recommendation:
“The FBI recommends any owner of small office and home office routers power cycle (reboot) the devices.”
As you may know, booting is the technical term for powering on a computing device, thereby activating basic code that is stored on chips in the device. The very first code to run is that stored in what we call “firmware”, meaning it is considered part of the hardware. Think of the code in firmware as hard to change (in some cases it is practically impossible).
The next code that runs in the boot process is that which has been stored in something called non-volatile memory, a type of memory that retains data even when the device is powered down. That is different from volatile memory, the regular kind of memory that gets wiped clean when you power down your computer (or suffer a power outage).
Remember, your router is a computer, with firmware and memory, both volatile and non-volatile. When a router is compromised by VPNFilter malware, chunks of malicious code are loaded into volatile memory. Rebooting or power cycling your router will clear that out, and that is what the FBI would like you to do.
For some people the easiest way to reboot the router is to unplug the power supply, wait 30 seconds, then plug it back in again. Alternatively, there may be an on/off switch on the back of the router, in which case you can use that to turn it off, wait 30 seconds, and then turn it on again. However, you shouldn’t do that unless you are sure the switch you are using is the on/off switch.
Reboot vs. reset
How could you be confused about the on/off switch? Some routers have multiple switches on them; for example, the router on my desk right now has a “Wi-Fi” on/off button as well as a power switch and something called a WPS button. Also, your router may have a reset switch or “Restore Factory Settings” button. Resetting your router and thereby restoring it to the factory configuration is very different from rebooting it.
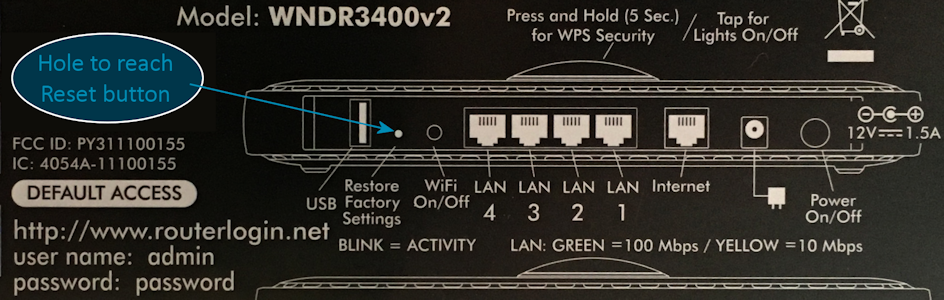
Performing a reset will erase both volatile memory and non-volatile memory. The latter is where your router stores any changes you have made to its configuration. For example, most routers come with a default administrator name and password that you should change to prevent attackers taking it over. How could they do that? Because the default user names and passwords are widely known. They are often printed on the back of the router and may be discoverable via a Google search based on your model number. For example, on my desk I have a Netgear WNDR3400:
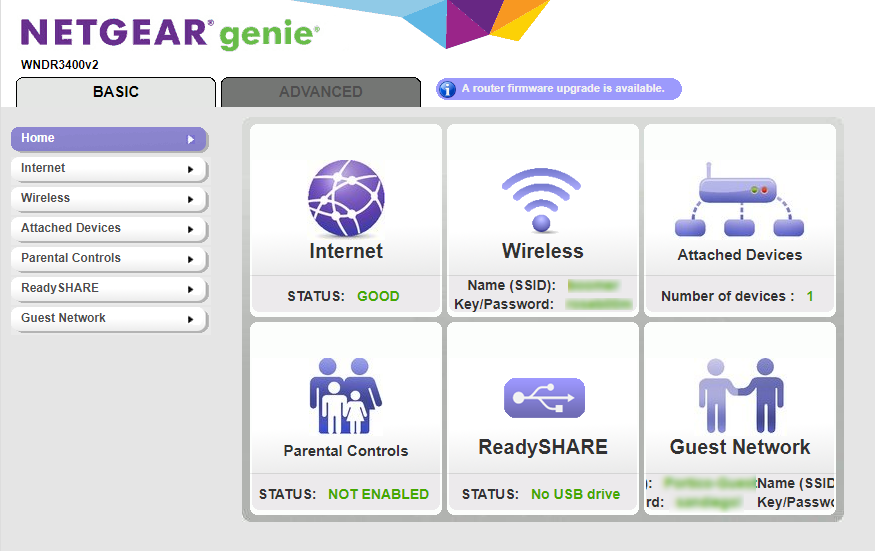
This model, like many others, has a browser-based control panel that you can use from your computer (typically by using a URL like http://192.168.1.1). The interface enables you to change any settings that are then stored in the router's non-volatile memory. My router control panel looks like this:
Note that I have blurred out the settings for user name and password and SSID (the name of the wireless access point). I have also written these down on a piece of paper so that, when I reset the router I can reenter the settings and restore the configuration.
Why would I want to perform a router reset? When your router is compromised by VPNFilter malware, part of the code is written into non-volatile memory, so it does not go away when you simply reboot. That remaining code enables the device to reach out to a web domain after a reboot and download fresh malware into memory … except the FBI now controls that domain. So, even if you have not removed VPNFilter code from non-volatile memory, it is currently prevented from downloading fresh malware.
How do you perform a router reset?
Taking control of a malware domain is called “sinkholing” and this was clever work by the FBI. However, you may decide that you want to reset your router anyway. This should remove the last of the VPNFilter code from the device.
How you perform the reset varies by make and model. I strongly suggest you go the website of the router manufacturer and get the instructions from there, specific to your model. Exercise caution if you decide to Google the instructions for your device because there may be attempts to poison search results relating to this issue. You can restrict results to pages found on the manufacturer's website by using the "site" parameter like this: Netgear WNDR3400 factory reset site:netgear.com.
What follows is a generic guide that you use at your own risk.
For many routers the reset operation is more than flipping a switch, it involves the classic “paper clip poker” and a small hole on the device. This may be referred to in the manufacturer’s documentation as “Restore Factory Settings” or something similar. It is often printed on the back of the device, along with the default values, like this:
To proceed with the reset, first make sure:
- You know the default user name and password for the device because you will need these to access the device after the reset.
- You have recorded any adjustments you made to the factory settings, like changing the router password, as well as the wireless SSID name and password.
- The router is powered on.
- You have warned everyone who is using the network to save their work.
- The router is disconnected from the internet (if the reset reverts the router password to a known default and the router is on the internet it instantly becomes a soft target).
Now grab your poking implement – a straightened paperclip, or something similar, like the pin you got with your smartphone or tablet to pop the microSD card or SIM-tray – and follow these three steps to perform the reset:
- Gently insert poker into the reset hole where you can feel it depress a button.
- Hold the button down for 10 seconds
- Release.
This will cause the lights on the router to flash a lot, but after a minute or so they will settle down. However, before reconnecting the router to the internet you should log into the router to change the router admin password from the default and make other changes, like setting the wireless SSID name and password.
Summary
Summing up: the VPNFilter malware poses a serious threat to the security and availability of small office and home office networks. Even if you are not using one of the routers in the list below, you need to take action. The following is the minimum response:
- If your router is supplied by your ISP, turn it off and then back on again, then check for further advice from your ISP.
- If you own/maintain a router, reboot it, change the default password, and check if any firmware updates are available from the router manufacturer; if so, install them.
If you are someone who knows their way around network hardware you may also want to do the following:
- Disconnect your router from the internet and perform a router reset.
- Re-install the most recent firmware.
For ongoing protection – and hopefully, it goes without saying these days – you need to run reputable security software on all your networked devices like laptops, PCs, Macs, Android tablets, smartphones, and yes, even your smart TV.
In addition, everyone should stay tuned for further news about VPNFilter and other malicious code that targets network connected devices. I hope you are already following WeLiveSecurity. I can also recommend: Krebs On Security, Security Week, Bleeping Computer, and Morning Cybersecurity.
Finally, if you would like your government to do more to prevent attacks like this in the future – and I firmly believe there is a lot more that governments could be doing – consider sending a message to your elected representatives demanding action.
Resources
Links to instructions and updates from affected router vendors.
| Reset to factory defaults | Upgrade to latest firmware | Change default password | Disable remote admin | Advisory | |
|---|---|---|---|---|---|
| Reset | Upgrade | Change | Disable | VPNFilter Malware Update | |
| Reset | Upgrade | Change | Disable | VPNFilter official statement | |
| Reset | Upgrade | Change | Disable | Security Advisory for VPNFilter Malware on Some Routers | |
| Reset | Upgrade | Change | Disable | Security Advisory for VPNFilter Malware | |
| Reset | Upgrade | Change | Disable | VPNFilter Malware Security |
List of router models known to be at risk (but there could be more)
Linksys: E1200, E2500, WRVS4400N
Mikrotik Routeros Versions for Cloud Core Routers: 1016, 1036, 1072
Netgear: DGN2200, R6400, R7000, R8000, WNR1000, WNR2000
QNAP: TS251, TS439 Pro, other QNAP NAS devices running QTS software
TP-LINK: R600VPN
More articles about routers on WeLiveSecurity:
Five ways to check if your router is configured securely
How to secure your router to prevent IoT threats?
Secure your router: How to help prevent the next internet takedown
Password-stealing security hole discovered in many Netgear routers
FTC IoT privacy and security push points out D-Link router and webcam flaws
CERT warns Netgear routers can be easily exploited
900,000 Germans knocked offline, as critical router flaw exploited