When it comes to wrapping a chain of defensives around an organization’s information systems and the valuable data that they process, it is often said that “employees are the weakest link” in that chain. In fact, I am participating in a webinar this week titled: Cybersecurity Training in the Workplace - How to Fix Your Weakest Links (check here for more details).
But some people have argued that the “weak link” label is unfair to employees. In this article I will explain why they might be right, and then talk about the best way forward so we can all be strong links in the information security chain. (I will also discuss the online cybersecurity training that your organization can use at no charge by going to this address: eset.com/us/cybertraining.)
Whose fault is it that you didn’t know this?
Consider this scenario: an employee opens an email attachment despite a warning, displayed on their screen, that doing so is unsafe. If opening that attachment results in a malware infection that compromises the organization’s network, then management may see that employee as a weak link.
But what if that employee was not trained to heed those warnings? What if they were not aware of the very nasty consequences that such clicks can produce? You could argue that the lack of training and awareness is management’s fault, and therefore management is the weak link.
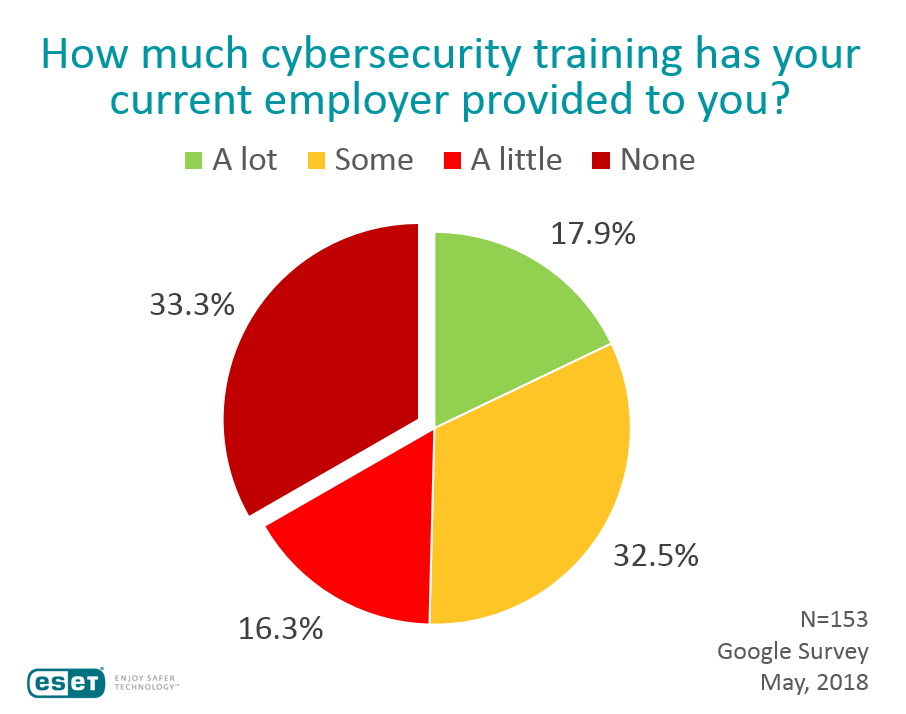
If you are wondering what the chances are that an employee in 2018 has received no cybersecurity training from their employer, I have an answer: based on the survey we ran earlier this month, the chances are a rather alarming one in three. In other words, one third of the respondents identified “None” as the amount of cybersecurity training that they had received from their current employer. You can see the results here:
While the sample was small, the results were not inconsistent with larger studies that I will describe in a moment. Bear in mind that the people we surveyed were all US adults who said that they use a computer in their work. Think about this – a third of employees are using computers despite having received no cybersecurity training from their current employer. This is problematic for multiple reasons beyond the obvious one that untrained employees are more likely to cause or enable security breaches. Here are a few more reasons:
Standard of due care: if a cybersecurity incident at your organization results in any kind of lawsuit or insurance claim, it is pretty much inevitable that the question of how much cybersecurity training was provided to employees will come up. I am fairly certain that “none” fails the “reasonableness” test, meaning the organization will be judged to have taken less than due care to protect its systems.
Contract violation: many companies include cybersecurity-related training requirements in contracts with vendors. Here is a real world example from a pre-deal checklist encountered by a small software company trying to close a sale to a big financial institution:
| Are the vendor’s employees required to be trained on privacy and potential fraudulent activity? | [ ] Yes [ ] No |
|---|---|
| Are the vendor’s employees educated on what information can and cannot be transmitted via email? | [ ] Yes [ ] No |
| Are security policies and procedures disseminated to all the vendor’s employees? | [ ] Yes, if so, is there an awareness program? [ ] No |
While the term “cybersecurity” is not used, keep in mind that this “initial due diligence form” dates back to 2011 – the questions in today’s equivalent are likely to be greater in number and specificity. So, if management has signed off that it is doing employee training and awareness, the reality should be that all employees can confirm this to be the case if they get asked to testify on this matter it in the wake of a breach.
Regulatory risk: organizations that don’t provide employees with cybersecurity training run the risk of sanctions and even fines under various laws and regulations. In America, these include HIPAA, PCI, and even state laws, like Massachusetts 201 Cmr 17.00: Standards for the Protection of Personal Information of Residents of the Commonwealth. This requires any company that processes personal information about Massachusetts’ residents to provide: “Education and training of employees on the proper use of the computer security system and the importance of personal information security.”
Assumptions and reality
That Massachusetts law has been in place since 2010. Security training requirements in vendor agreements also have been around since at least then. There has been some progress. Consider one survey result we got in 2012: 68% of consumers said they’d never had any classes or training about protecting their computer and/or their personal information, not at work or anywhere else. By the time we did this survey in 2017 only 30% of respondents said they received no cybersecurity training at their organization.
I still find that a scary number, but I admit to feeling sympathetic to employers who assume that new hires will come to them with some level of security awareness and education (after all, as previously noted, it is 2018 already).
But you know what they say about assumptions: they can really mess up your organization. When I look at the 33.3% of employers who provided no training, I wonder if they thought to ask new employees on day one: do you have all the knowledge you need to fulfill your responsibility to protect the organization’s information systems and the data they process?
Maybe all the employers did ask that question, and all the new hires said yes, and that’s where the 33% comes from; but I rather doubt that. I think there are multiple reasons for the situation depicted in that chart, starting with cost. This is the excuse/objection that I hear most often in discussions with organizations about why they provide a less than optimal amount of cybersecurity training to their employees.
Good news
Fortunately, there is some good news on the cost front: your organization can now get some free online cybersecurity training from multiple reputable sources. I say “some” because free training is typically not customized to your organization, and every organization should provide some cybersecurity training that is specific to its own needs. For example, generic content can train employees to spot social engineering attacks, but it won’t tell teach them the right way to report them in your organization. That varies by organization, or even location within the organization.
That said, there is a lot of common ground in basic cybersecurity that all employees need to know, regardless of where they work. As a first round of training, a free online resource can be a great start. You can then supplement it with organization-specific details. Beyond that, for more advanced and ongoing company-specific training, you can engage a security training specialist (or designate someone in-house to fulfil that role).
A good example of free cybersecurity training can be found here: eset.com/us/cybertraining. Okay, so I might be a little biased, but I think ESET has done a great job with this training, starting with the way it fits into the needs of organizations.
When you use a free online course to train your employees you need to do more than send them to a web address; you need to track which employees complete the course. The ESET training enables you to do that. When you sign up as a manager you get a link to the training that you can send to employees. Each employee who goes to the link and completes the training gets a certificate they can download and forward to you to document that the training has been done.
But will they do the training? Employee reluctance is often cited right after cost as an excuse for not offering cybersecurity training. But there is good news on this front too. First of all, I noticed a significant increase in employee enthusiasm for cybersecurity education some years ago, about the time that internet use by US adults passed the 80% mark (around 2012 according to Pew Research).
That percentage is now 90%. In other words, just about every person who has a job also has their own personal connection to the internet – be it laptop, tablet or smartphone – and that gives them a personal as well as professional interest in protecting data. ESET actually documented this last year: close to half (49%) of respondents to our survey indicated that they would take a cybersecurity training course at their organization, even if it were optional and they were not compelled to attend.
That shift in attitude may explain why ESET’s free online cybersecurity training has racked up some impressive numbers in the first 12 months: 11,432 people registered; over 10,000 logged in; and nearly 9,000 completed the training, passed the test, and got their certificate.
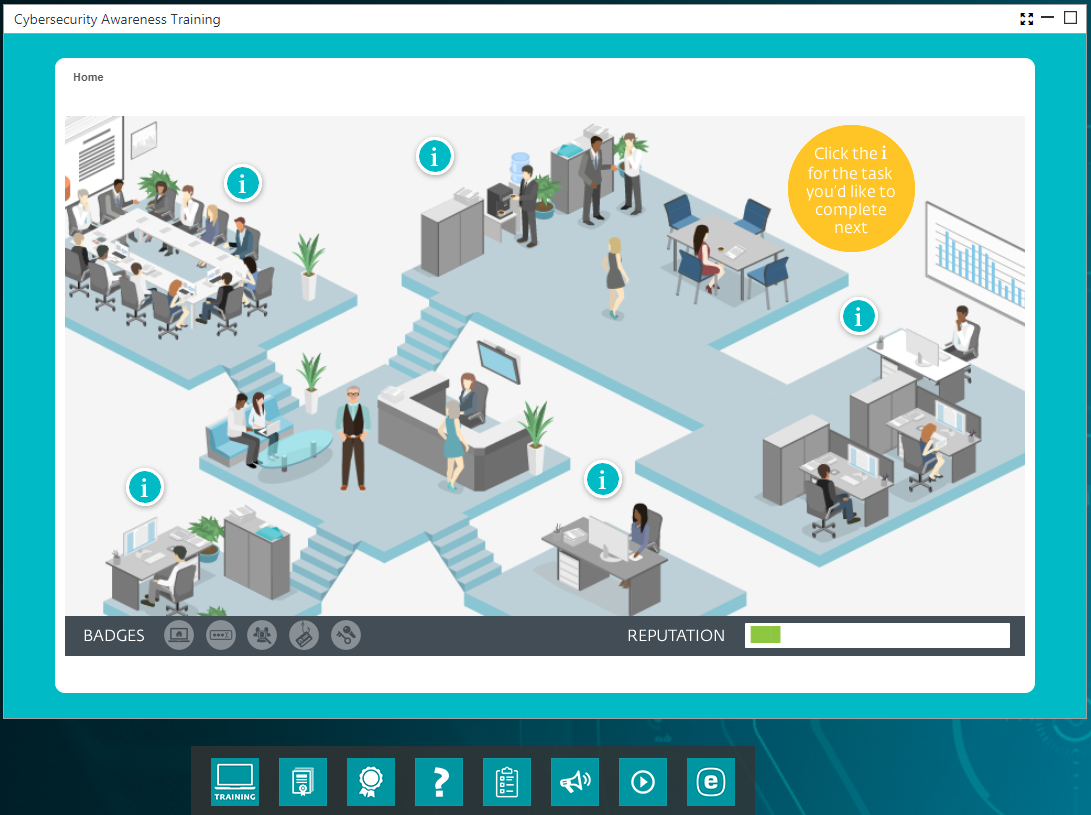
However, even though the feedback that ESET received was overwhelmingly positive, the content has recently been updated, and so has the way it is delivered. There is now a more engaging, game-style approach. I encourage you to check it out and let me know what you think. Rather than a purely linear program, the new style allows employees to decide the order in which they progress through the modules, using an avatar navigating an office, as shown here:
The modules are as follows: Safeguard your email communication; Stay safe while going online; Steer clear of malware; Shield yourself from social engineering; and, Fortify your accounts with secure passwords. Each one includes instructor-narrated content and challenge-style quizzes that earn badges. There are additional resources that employees can click for more help.
The goal is to help employers drastically reduce the number of employees who have no security training; that in turn should greatly improve security at those organizations which participate.