It all starts innocently enough - as always - with an SMS message containing a link to a page that looks like the Canada Revenue Agency, but is in fact a form that sends all the information entered to a malicious fraudster.
We have investigated several such phishing attempts and have found that this is not the first attempt at this type of scam by this gang: it seems that they have been active since early 2017. The most common way in which they try to get personal and financial information from victims is to let them think they have received an online Interac transfer (Interac provides a popular online money transfer service in Canada) for a “refund” from either the Canada Revenue Agency or a popular Canadian public utility service such as Hydro One, Hydro-Québec or BC Hydro.
I personally received such a message, in French, in November 2017, on my cell phone in the 514 area code.
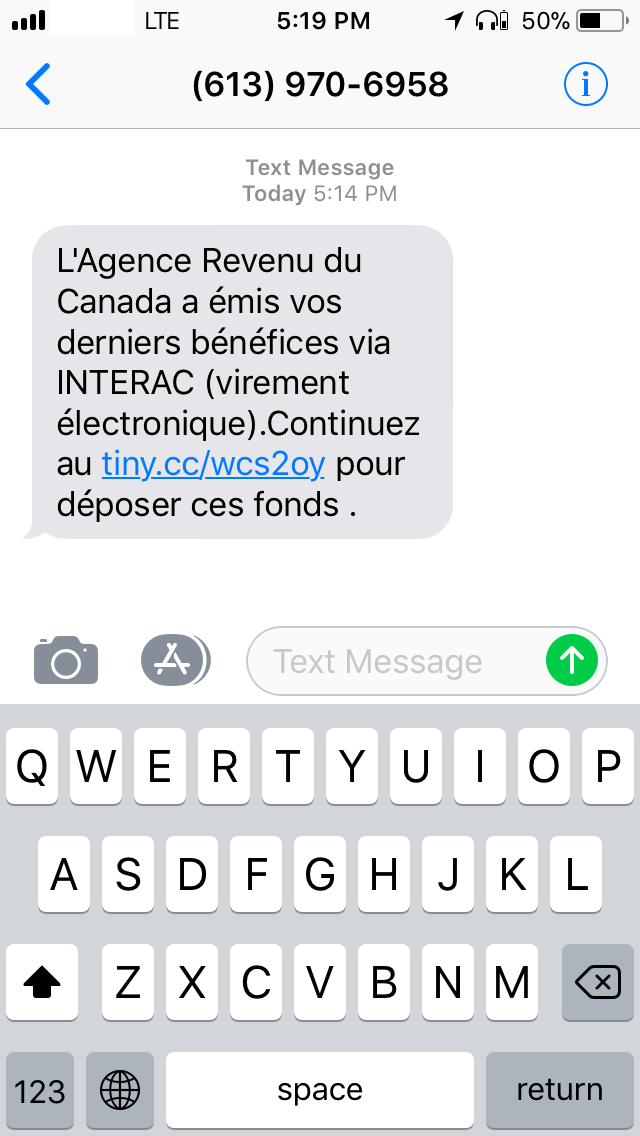
Figure 1 — SMS message from a fraudster. Translation: “Canada Revenue Agency issued your benefits via INTERAC (electronic transfer). Continue to XXX to deposit the funds.”
There has been some media coverage (in French) of this fraud by Radio-Canada in early 2017 and Journal de Montréal in April 2018.
Let’s take a closer look at the fraudsters' activities and infrastructure.
The schemes
As already mentioned, these phishing attempts use one of two fake cover stories to lure their victims. We will look into the details of each of these.
Fake Interac transfer
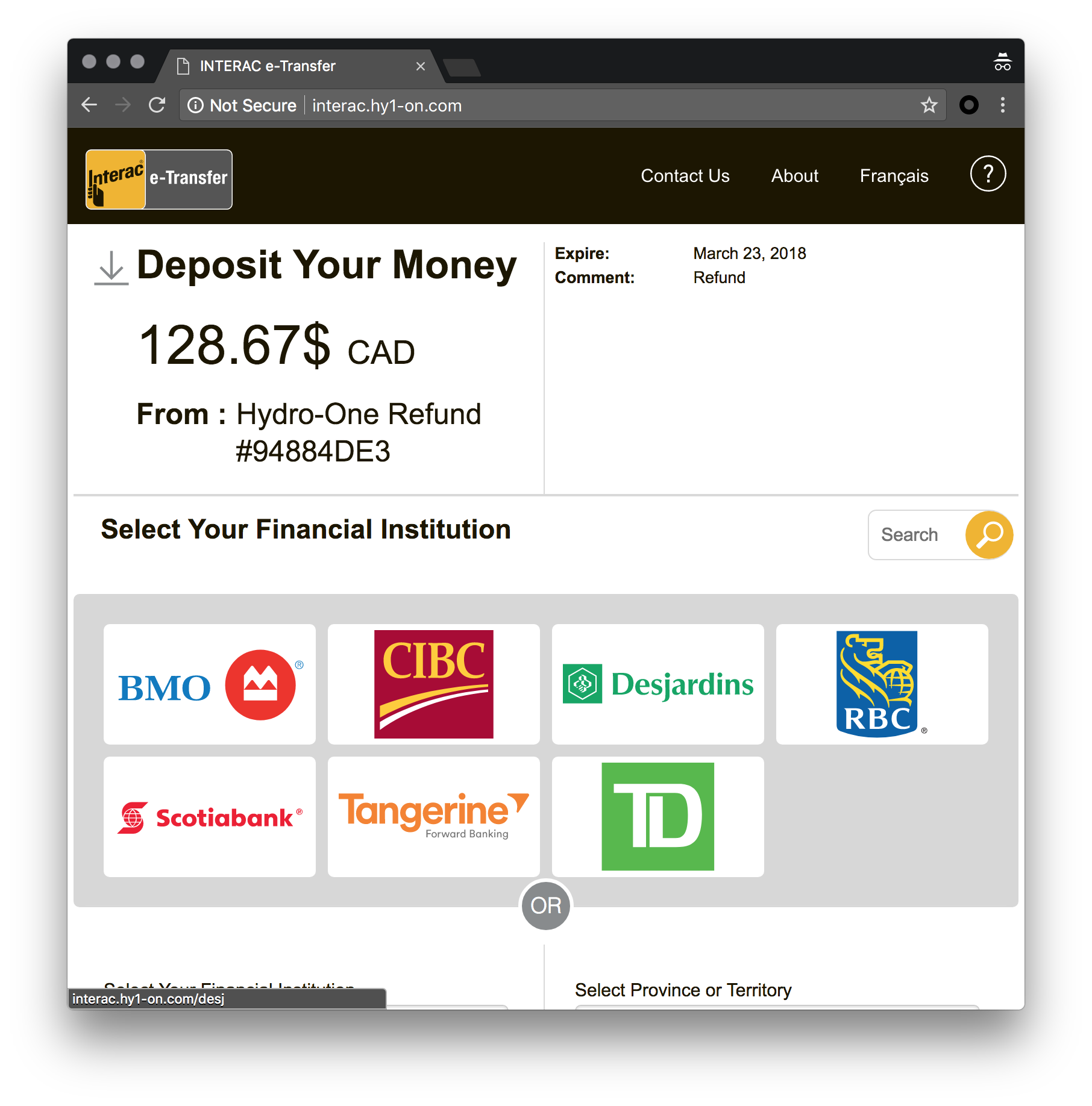
This scheme starts with either an SMS or email reputedly about the reception of an Interac payment. The domain in the URL mimics the legitimate organization and usually starts with the the interac or transfer subdomain. In the example in Figure 2, the URL (http://interac.hy1-on[.]com) pretends to be from Hydro One but is in fact a web page controlled by the scammers.
Victims who visit the link arrive at a page where they are prompted to choose the financial institution to receive the funds. Interac e-Transfer is a popular way in Canada for individuals to send money by email or SMS, and that works with almost all financial institutions. The fake page is very similar to the page displayed when receiving a legitimate Interac transfer, except it offers fewer financial institutions where to deposit the funds.
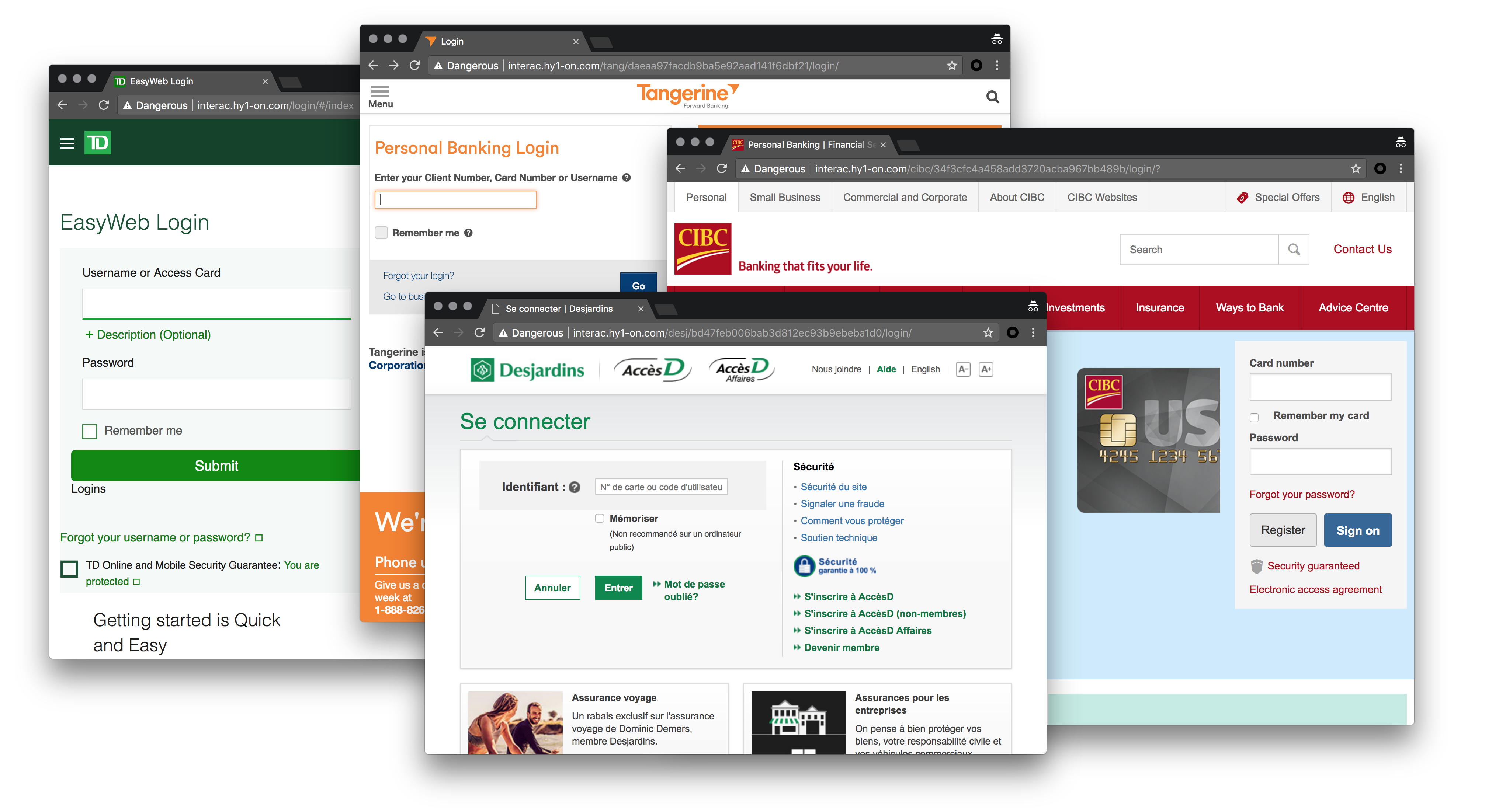
After choosing a financial institution, victims are taken to a copy of its login page.
When clicking the “submit” button, anything typed into these forms is sent to the fraudsters. After submitting the username or account number and password, another form is shown requesting further information — to get even more details about the victims, such as their secret questions, email addresses and passwords, credit card details, etc.
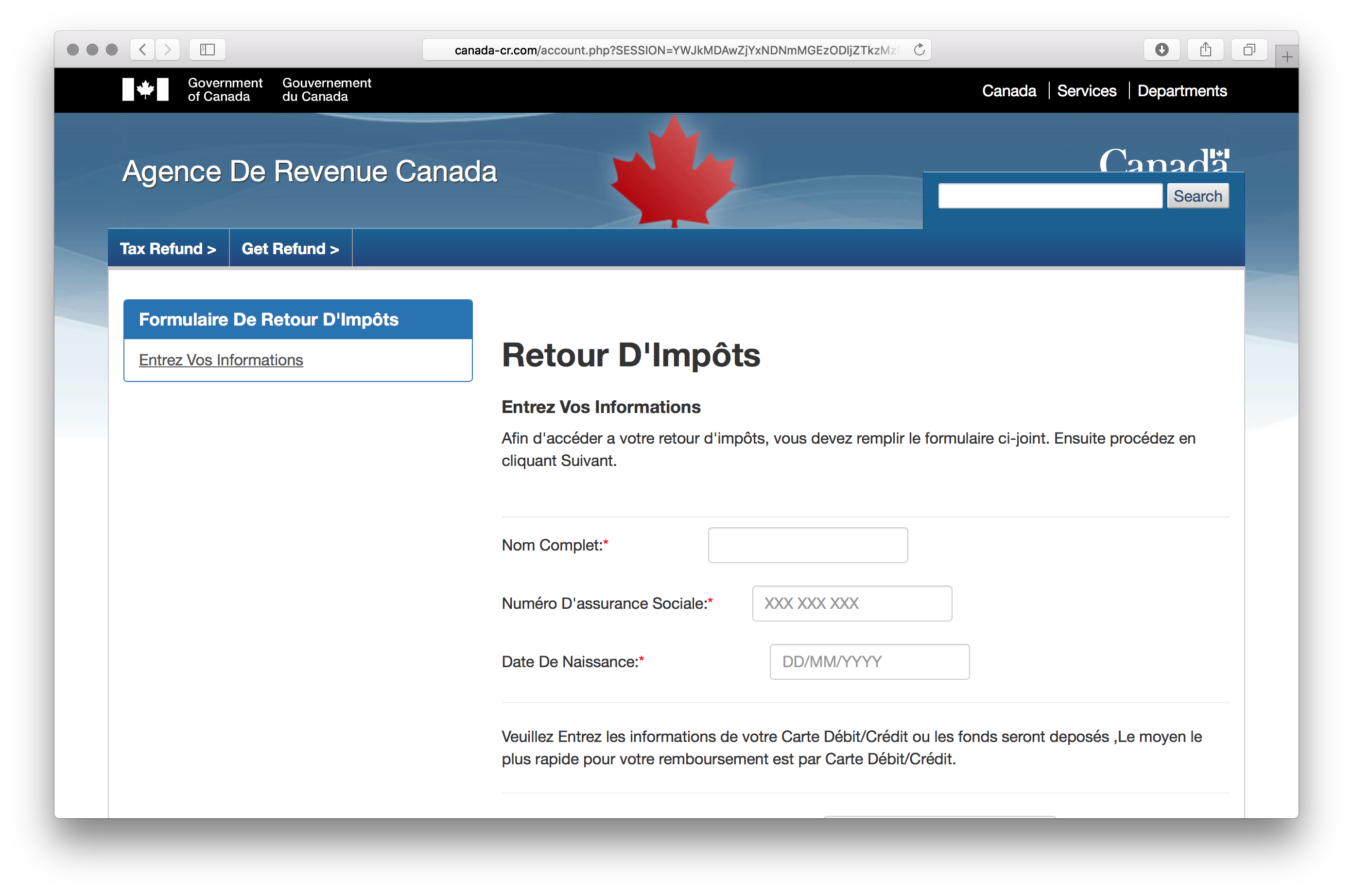
Fake tax refund from Canada Revenue Agency
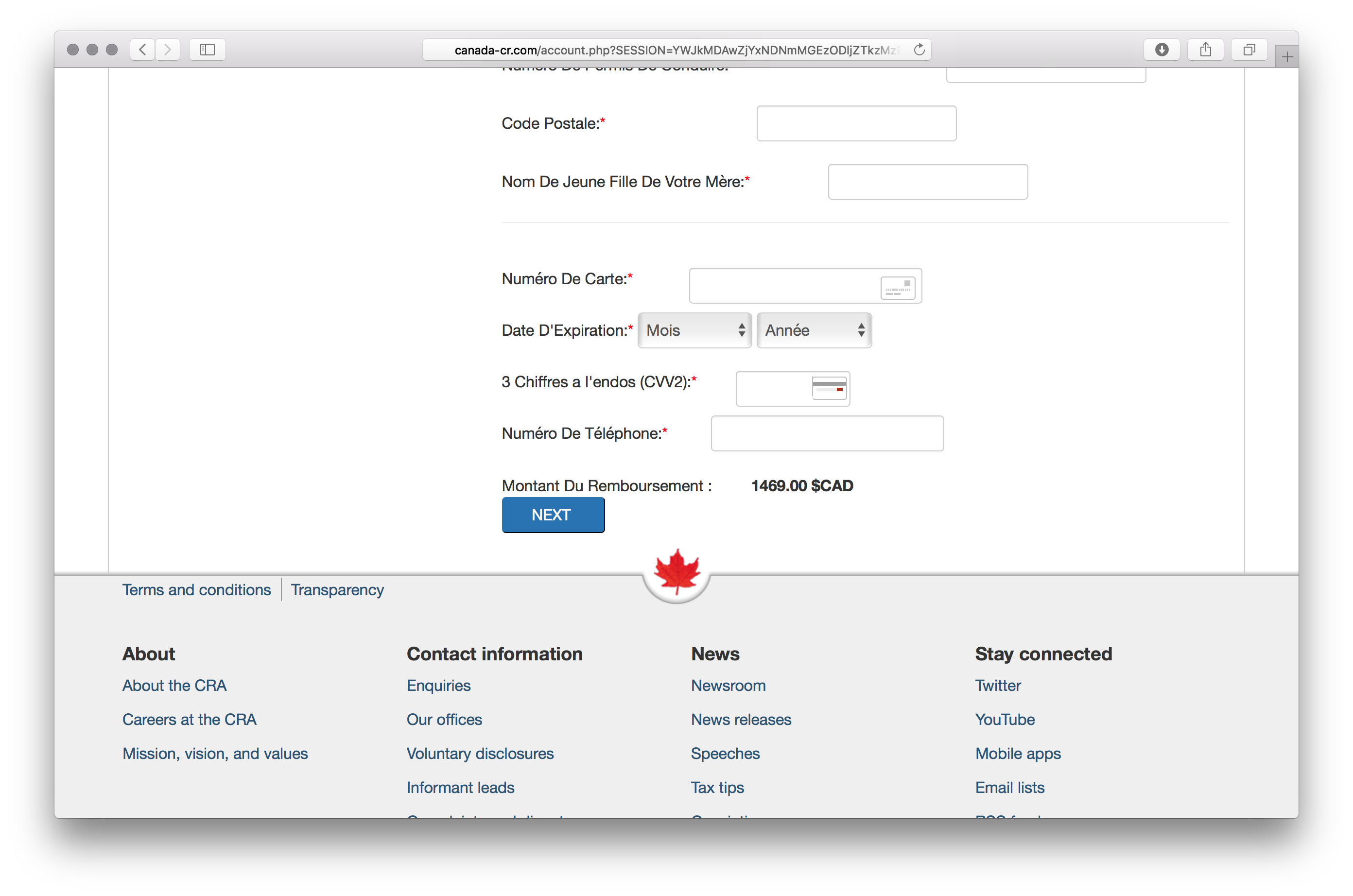
Two domains were registered using the same fake identity information that was used for the Interac scam domains listed in a later section. These were, on April 15th and 16th respectively, cra-can[.]com and canada-cr[.]com. The latter had a page asking for a lot of personal information including SIN (Social Insurance Number), credit card details and mother’s maiden name.
Unlike the Interac template page, the HTML source of the CRA page employed an interesting obfuscation. All of its content is decrypted by a JavaScript implementation of AES.
<html><head><script src='hok.js'></script><script>
var hea2p =
('0123456789ABCDEFGHIJKLMNOPQRSTUVXYZabcdefghijklmnopqrstuvxyz');
var hea2t =
'Gf3hMlcM2lq7ZB[…~32kB redacted…]HFaqBinZ82Pg==';
var output = Aes.Ctr.decrypt(hea2t, hea2p, 256);
document.write(output)</script></head></html>
Once the decryption script runs, the variable output here contains the full, unencrypted HTML page. This is not a novel technique. Searching the internet for “hea2t” or “hea2p” reveals that it is used in other phishing pages as well.
Of course, it's quite easy to decrypt it and reveal the real source code. In the unencrypted source of the fake CRA form, the author of the phishing template added a comment, at the end of the form, that we're unable to explain: “Toufa lena” could mean “He died for us” in Arabic.
[...]
<b> 1469.00 $CAD </b></div>
</fieldset>
<div class="alignCenter"><input required type="submit" name="submit" class="btn btn-primary" value=" NEXT " id="submitButton"/></div>
<!--/ FIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIILED TOUFA LENA --------------------->
</form>
</div>
<script src="./JS/gatrack.min.js" style="vertical-align: top; min-height: 0px;"></script></div>
[...]
Infrastructure
There are several similarities in the infrastructure employed by both these scams.
Domains
We found most of the domains in these campaigns were registered using a fake identity and the email address rokers0001[at]gmail.com. We found more than 60 domains registered with this email address since December 2017. All of them are related to phishing targeted at Canadians.
Registrant Name: Jean Marc
Registrant Organization:
Registrant Street: 4547 rue bourbonniere
Registrant City: montreal
Registrant State/Province: Quebec
Registrant Postal Code: H1X4S4
Registrant Country: CA
Registrant Phone: +1.5146604512
Registrant Email: rokers0001[at]gmail.com
Registration Service Provided By: DOMAINS4BITCOINS.COM
Note that neither the street address nor the postal code exists in Montréal. The H1X postal code area exists, but 4S4 isn't one of its subareas.
We also noticed that the registrar chosen to register the domains is known to accept cryptocurrencies. This could make it more difficult for law enforcement to identify the person behind this registration.
Hosting
After gathering a list of domains used by this gang, we realized almost all of them pointed (or used to point) to servers located in so-called “offshore hosting” providers. One of them is located in the Netherlands (146.185.253.0/24), but their favorite seems to be in Panama (190.14.37.0/24 and 190.14.38.0/24).
Here is the list of these domains, grouped by their current or past IP addresses:
| IP address | Domains |
|---|---|
| 146.185.253.20 |
|
| 146.185.253.123 |
|
| 146.185.253.149 |
|
| 146.185.253.158 |
|
| 146.185.253.171 |
|
| 146.185.253.206 |
|
| 190.14.37.12 |
|
| 190.14.37.56 |
|
| 190.14.37.253 |
|
| 190.14.38.25 |
|
| 190.14.38.29 |
|
| 190.14.38.30 |
|
| 190.14.38.42 |
|
| 190.14.38.43 |
|
| 190.14.38.44 |
|
| 190.14.38.50 |
|
| 190.14.38.65 |
|
| 190.14.38.100 |
|
| 190.14.38.104 |
|
| 190.14.38.238 |
|
| 198.251.83.27 |
|
| 51.15.37.2 |
|
U-Admin
On some of the scam webpages, we found the following script at the end of the page:
<script type="text/javascript">
var link = "rbc.ca";
var bb_link = "https://www1.royalbank.com/cgi-bin/rbaccess/rbunxcgi%3FF6=1%26F7=IB%26F21=IB%26F22=IB%26REQUEST=ClientSignin%26LANGUAGE=ENGLISH?_ga=2.223587993.3443842.1512767868-1221977710.1512093019";
var query = "";
var full_url= "http://interac.hy1-on[.]com/rbc2/";
var dir_url ="http://interac.hy1-on[.]com/rbc2/6ef559237e49a8fe0ca936bed5bf33ab/login/";
var bid = "6ef559237e49a8fe0ca936bed5bf33ab"
var texts={};
var lng="en"
var device = {"isMobile":false,"isTablet":false,"isiOS":false,"isAndroid":false}</script>
<script type="text/javascript" src="form.js?v=5ae22c8f3b8b5"></script>
This is known to be part of the U-Admin phishing kit. This kit has been documented before in 2016 by Kafeine, and recently by Remco Verhoef in the Internet Storm Center diary. U-Admin is an administration panel for phishing and malware that can be bought on underground forums.
Who is behind this?
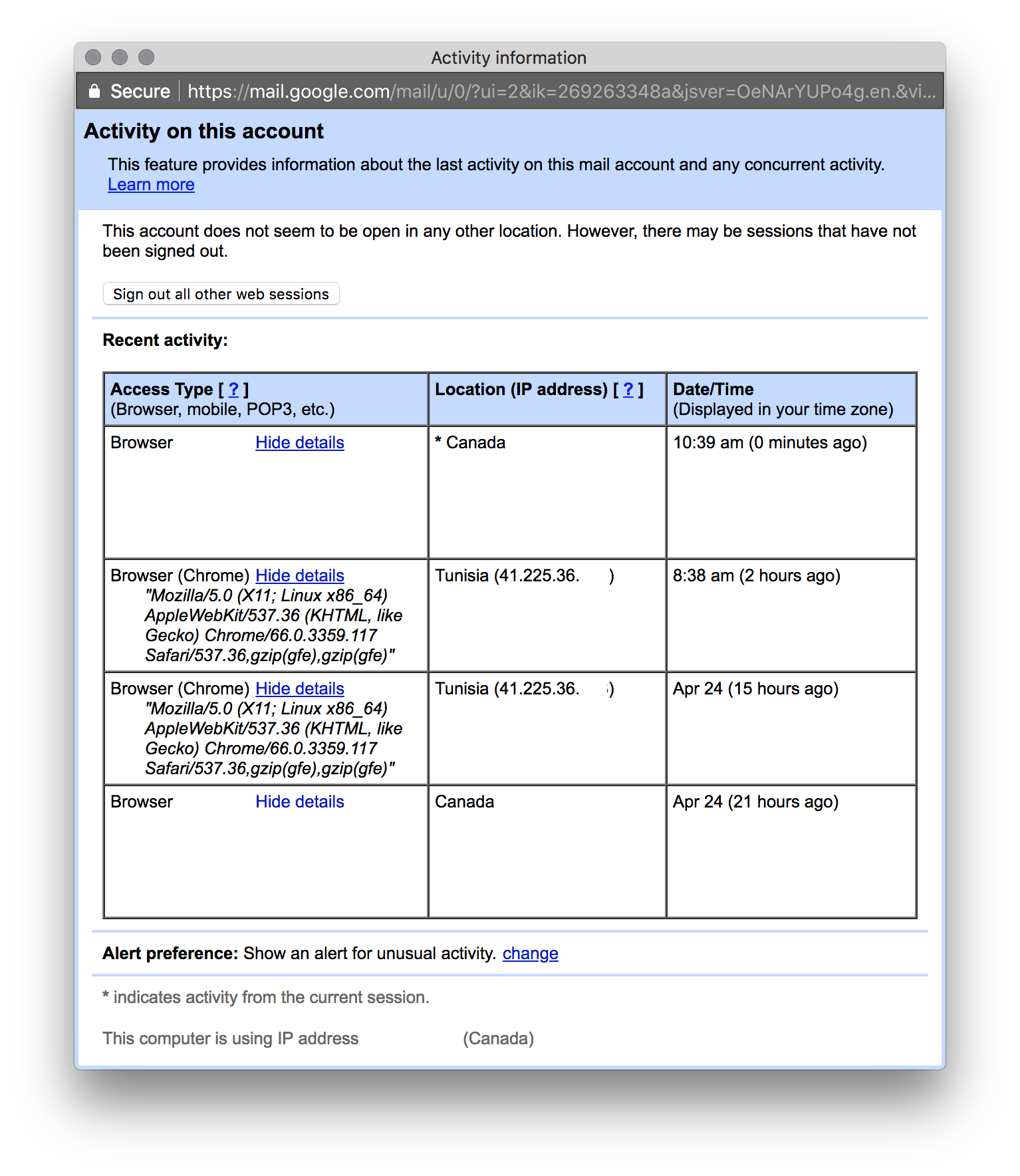
We wanted to know a little bit more about how the scammers use the account data they obtain. On April 24 we leaked a Gmail account's credentials on one of these phishing pages. The goal was to find information on who would try to use it and how. Six hours later, someone logged in using an internet connection from Tunisia:
Since the account was freshly created and did not contain anything, we haven't seen any more activity on the account.
Although this is an interesting fact, we cannot conclude whether the perpetrators are Tunisian. The credentials could have been sold to another group. Another possibility is that the criminals could have used a compromised computer in Tunisia and proxied through it to log into the account.
Prevention
Phishing via SMS, sometimes called smishing or SMShing, isn’t something new. Canadian utilities and the Canada Revenue Agency never send refunds via Interac transfer. When receiving a money transfer you do not expect, contact the person or organization via a trusted channel, separate from that informing you of the transfer, to ascertain whether it’s really from that party.
ESET products detect and block the domains and URLs above as phishing.
Conclusion
This isn’t particularly sophisticated or technically advanced: these scammers have simply bought administration panel software, manage HTML templates, buy domains, and send SMS and email phishing messages. It also reinforces the age-old advice to be careful about SMS and email messages received from unfamiliar sources.