Online cryptocurrency website MyEtherWallet.com has confirmed that for a period of time yesterday some visitors could have been redirected to a phishing site designed to steal users' credentials and - ultimately - empty their cryptocurrency wallets.
According to reports, whoever was behind the attack may have successfully stolen approximately US $152,000 worth of Ethereum-based cryptocurrency.

However, assuming that MyEtherWallet itself was at fault may be a mistake, as the website explained in its statement:
"This is not due to a lack of security on the [MyEtherWallet] platform. It is due to hackers finding vulnerabilities in public facing DNS servers."
This explanation is confirmed by British security researcher Kevin Beaumont, who described in a blog post that some of MyEtherWallet's traffic had been redirected to a server based in Russia after traffic intended for Amazon's DNS resolvers was pointed to a server hosted in Chicago by Equinix.
For the scheme to succeed, someone pulled off a hijack of a crucial component of the internet known as Border Gateway Protocol (BGP), to reroute traffic intended for Amazon's Route 53 DNS service to the server in Chicago. As a consequence, for some users, entering myetherwallet.com into their browser did not take them to the genuine site but instead to a server at an IP address chosen by the hackers.
The only obvious clue that a typical user might have spotted was that when they visited the fake MyEtherWallet site they would have seen an error message telling them that the site was using an untrustworthy SSL certificate.
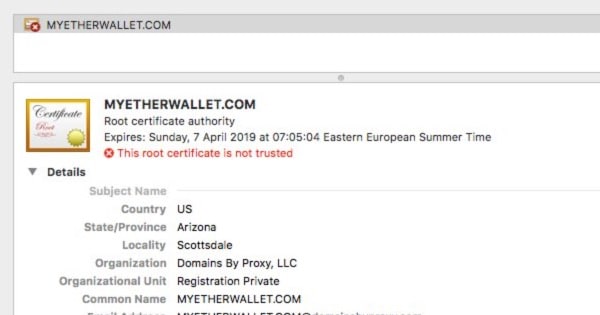
It seems that the attackers made an elementary mistake in not obtaining a valid SSL certificate. Their goof certainly helped alert some users that something fishy was occurring.
All the same, it's somewhat depressing to realise that some users saw an alert message and ignored it. Everybody who had their accounts compromised chose to proceed on the website despite having been presented with a security warning.
Despite making such a simple error with their SSL certificate, the hackers don't seem to have done badly for themselves - both in this attack and in the past. Fascinatingly, the bogus MyEtherWallet website set up by the criminals was moving stolen cryptocurrency into a wallet which already contained some US $27 million worth of assets. Inevitably that raises questions of its own - have the hackers already made a substantial fortune through other attacks, or might their activities be supported by a nation state?
In a statement Equinix confirmed that a customer's equipment at its Chicago data center was used in the hackers' hijacking of Amazon's Route 53 DNS service:
"The server used in this incident was not an Equinix server but rather customer equipment deployed at one of our Chicago IBX data centers... We generally do not have visibility or control over what our customers – or customers of our customers – do with their equipment."
For their part, a statement from Amazon points a finger of blame at others:
"Neither AWS nor Amazon Route 53 were hacked or compromised. An upstream Internet Service Provider (ISP) was compromised by a malicious actor who then used that provider to announce a subset of Route 53 IP addresses to other networks with whom this ISP was peered. These peered networks, unaware of this issue, accepted these announcements and incorrectly directed a small percentage of traffic for a single customer’s domain to the malicious copy of that domain."
With no-one keen to accept responsibility for what occurred, my advice to cryptocurrency fans is to take matters into their own hands. You have to be responsible for the security of your investments, and perhaps the most sensible thing to do is to keep your cryptocurrency wallets offline if you're worried about them being plundered by cybercriminals.
Personally I would advocate not only avoiding putting your cryptocurrency wallet online, but also keeping them off your smartphone or computer and perhaps invest in a hardware wallet instead.





