Researchers have discovered a new piece of ransomware that holds the victim’s files hostage. This one, however, comes with a rather peculiar demand in return for recovering the files, according to a Bleeping Computer report citing research by MalwareHunterTeam.
When executed, this ransomware – called “PUBG Ransomware” and detected by ESET as MSIL/Filecoder.HD – encrypts files and folders “only” on the user's desktop and adds the .PUBG extension to them.
Then, a splash screen is displayed that contains the ransom note. It turns out that, in order to set the victim’s digital belongings free, all that the rather benign ransomware wants is that the user spend an hour playing a game called PlayerUnknown's Battlegrounds (commonly known as PUBG, hence the ransomware’s name).
Or so the ransom note says. In fact, however, it was found that simply running the PUBG-associated executable for three seconds is enough to trigger the decryption.
Either way, if you’re not in the mood even to touch the game, the ransomware seems to let users off the hook: the ransom message includes the “restore code”, apparently with no strings attached.
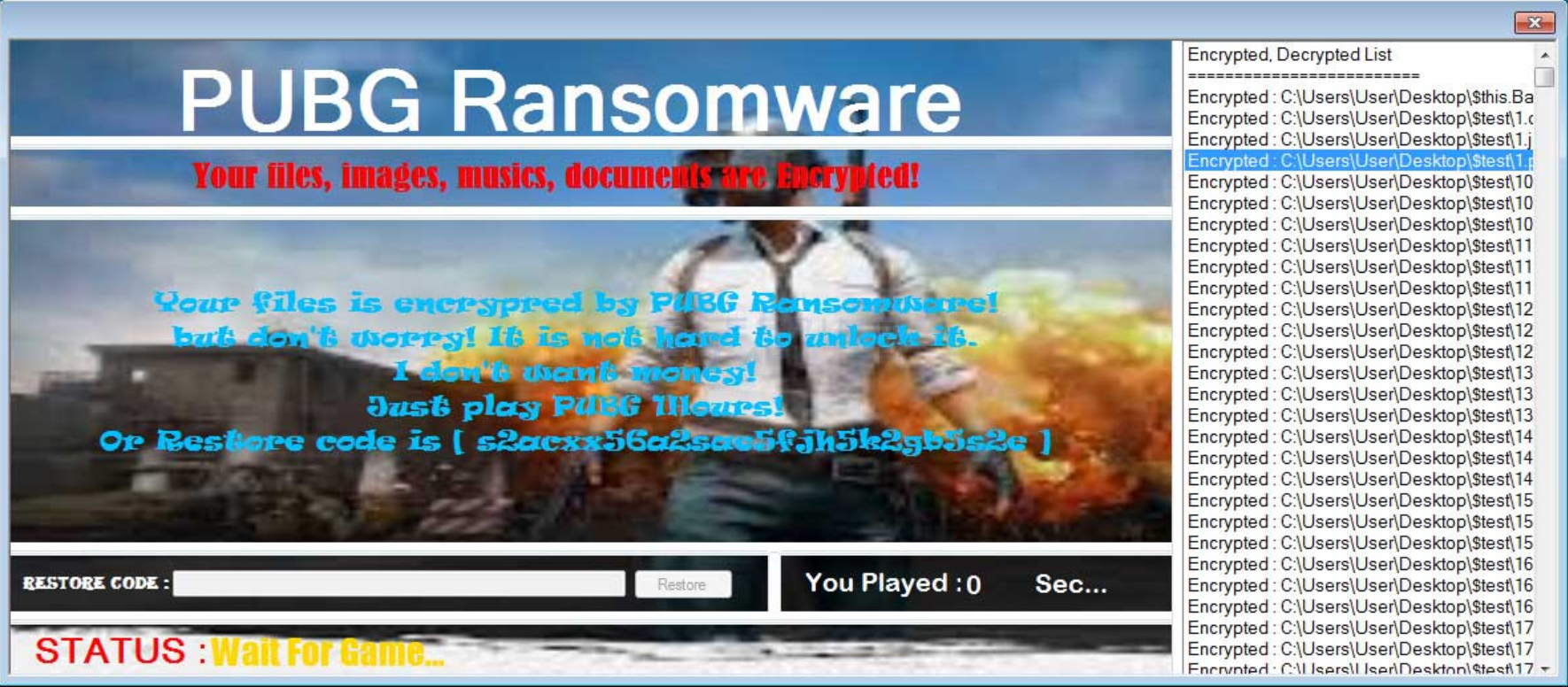
Ransom note (source: Bleeping Computer)
An analysis showed that the ransomware keeps tabs on processes running on the computer and checks if a process called “TslGame” is run. TslGame is apparently triggered whenever PUBG is launched, providing a way for the ransomware to determine, albeit somewhat simplistically, if the victim is playing ball. It’s unclear how this ransomware is being spread.
We reported in our mid-year review of last year’s cybersecurity landscape on another piece of ransomware that demanded that the user play a game. That creation, called ‘Rensenware’, required the victim to get a high score, at the “lunatic” level of a Japanese PC game in order to get the files decrypted.
All told, however, these curious tales should not detract from the magnitude of the threat that ransomware represents at present. Campaigns from not long ago are a stark reminder of how much damage extortion campaigns can wreak.
ESET Senior Research Fellow David Harley is keen to point out that this incident should not be treated lightly, "While this program has been referred to as ‘what could only be a joke’, it’s not really that funny. For a start, messing with a victim's data might conceivably go horribly wrong in some circumstances - it doesn't sound to be an impeccably well-coded program - we saw this time and time again in the heyday of the virus, where malware written by hobbyist virus writers had some (presumably) unintended but unfortunate effect. In any case, seeing a message like this could cause victims serious concern, if they didn’t understand exactly what was going on.
Even more important, this still looks to me like activity that would be regarded in principle as criminal in most jurisdictions, since it involves unauthorized access and modification. The fact that it probably wasn’t meant to be malicious doesn’t mean that it shouldn’t be taken seriously. The next such ‘joke’ might turn out to be even less humorous".





