The software development platform GitHub has suffered what is apparently the biggest distributed denial-of-service (DDoS) attack on record.
“On Wednesday, February 28, 2018 GitHub.com was unavailable from 17:21 to 17:26 UTC and intermittently unavailable from 17:26 to 17:30 UTC due to a distributed denial-of-service (DDoS) attack,” reads the announcement on the website.
At its peak, inbound traffic reached a staggering 1.35 terabits per second (Tbps), outflanking the previously record-setting assault of 1 Tbps at French web hosting provider OVH in September 2016.
Memcrashed
Unlike the attack against OVH, where the barrage of bogus traffic was unleashed by Internet-of-Things (IoT) devices hijacked into the Mirai botnet, the attack against GitHub didn’t exploit any compromised devices.
Instead, the attacker(s) co-opted widely-used Memcached database servers that have support for the UDP protocol enabled and are exposed to the internet without any authentication requirements in place, using a relatively uncommon attack method dubbed ‘Memcrashed’.
The servers are designed to speed up web applications and sites, but can also be abused as reflectors for amplifying traffic at a targeted service. The response can be 51,200 times bigger than the request, according to DDoS protection service Cloudflare.
The assault at GitHub involved spoofing the service’s IP address and sending repeated small queries to a number of Memcached servers. The servers duly replied – except that the elicited responses were hugely disproportionate.
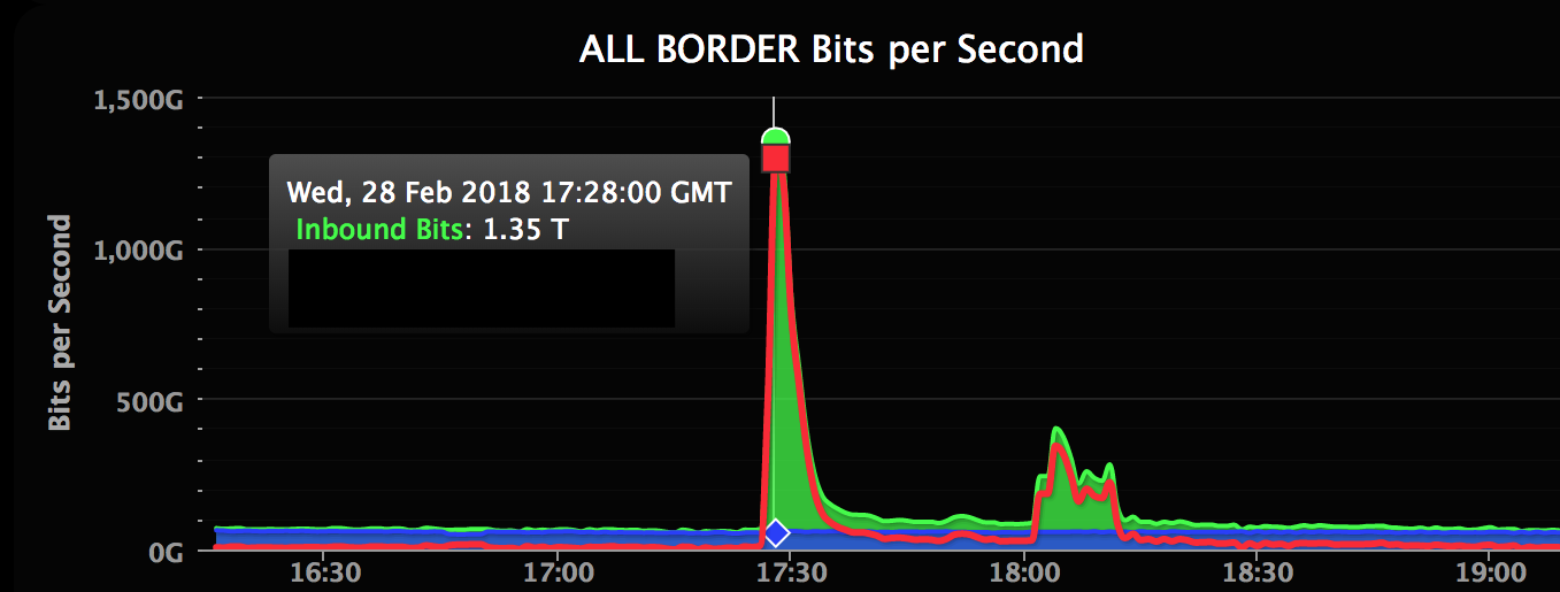
Inbound traffic to GitHub during the DDoS attack (source: GitHub, Akamai)
“Spoofing of IP addresses allows memcached’s responses to be targeted against another address, like ones used to serve GitHub.com, and send more data toward the target than needs to be sent by the unspoofed source,” reads GitHub’s post.
Shortly after the DDoS attack began, GitHub enlisted the aid of DDoS mitigation service Akamai Prolexic, which mitigated the junk traffic by re-routing it through its network and by blocking malicious requests. The assault then dropped off.
More and bigger to come?
At the time of writing, some 93,000 Memcached servers are reportedly accessible on the open internet and ripe for exploitation.
“[A]n attacker can access them, and send them a special command packet that the server will respond to with a much larger reply,” wrote Wired.
Akamai said that the reflection capabilities of Memcached make it “highly likely that this record attack will not be the biggest for long”.
The company added that similar attacks have hit a number of other organizations in recent days and that it has detected a significant increase in scans for open Memcached servers.
DDoS attacks are a weapon of choice for adversaries when they aim to force a target offline. They may also be intended as smokescreens hiding other incursions, however.
The list of infamous DDoS attacks also includes a series of onslaughts against DNS hosting provider Dyn in October 2016 that brought down a host of high-profile online services.





