As you may have heard, Apple unveiled several new products this September, including the iPhone 8, iPhone 8 Plus, and iPhone X, as well as the latest version of Apple's mobile operating system, the new iOS 11.
As usual, user interest was focused on the platform's new features: A new way to browse the file system, the ability to make payments to your friends via Apple Pay, new features for Siri, a document scanner, and augmented reality apps, to name but a few.
As of today's date, almost 14% of all mobile users use Apple. That makes it the second-biggest operating system in the world, so it makes sense for us to apply ourselves to analyzing what new security features the new iPhone offers.
Security improvements on the new iOS 11
In this new version of its operating system, Apple seems to have concentrated on improving user information confidentiality, by complicating the process by which an unauthorized stranger might try to gain access to files stored on the device.
These new security measures will undoubtedly not only impact the security of data stored on a phone that has been lost or stolen, but could also complicate the progress of criminal investigations requiring the forensic analysis of a phone.
So let's take a look at some of the improvements.
Password authentication to connect to a computer
"Without this password, neither attackers nor forensic experts will be able to make any backup copy of the phone."
Previously, to connect an iPhone to a computer, all a user needed to do was to accept the dialog box displayed on the screen asking whether the computer was trustworthy. For this to happen, the phone had to be unlocked, but this could be done through fingerprint identification (Touch ID).
From iOS 11, to complete the identification process a password known only to the user has to be entered after the user has confirmed that the computer is trustworthy. Without this password, neither attackers nor forensic experts will be able to make any backup copy of the information stored on the phone.
Without this password, neither attackers nor forensic experts will be able to make any backup copy of the phone.
This is particularly significant for criminal proceedings. For example, in the United States, passwords are treated as knowledge, so their confidentiality is protected by the First Amendment, unlike a fingerprint, which is regarded as physical evidence and can be demanded by the authorities.
Quickly disabling Touch ID
Another security-related feature is the option to quickly disable Touch ID for unlocking the phone. This will allow people who find themselves in situations where their phone's security is jeopardized to disable unlocking via biometric means, by pressing the home button five times in rapid succession. After doing so, unlocking the phone will require a security password.
This could prevent thieves from being able to unlock a phone by forcing their victim's finger onto the home button or via the facial recognition feature (Face ID) included in the new iPhone X, which gives users the option to unlock their phones just by looking at them.
As with the previous feature, this security measure could be used to impede or slow down criminal investigations by allowing users who find themselves in any situation where their phones might be seized by the authorities to lock their devices with a password, which cannot be demanded by legal means.
Emergency calls
Pressing the home button five times in succession not only password-locks the phone, but also brings up an option to call the emergency services.
This feature is not necessarily aimed at protecting data, but could be useful in situations where the user's life is in danger, allowing local emergency services to be contacted quickly.
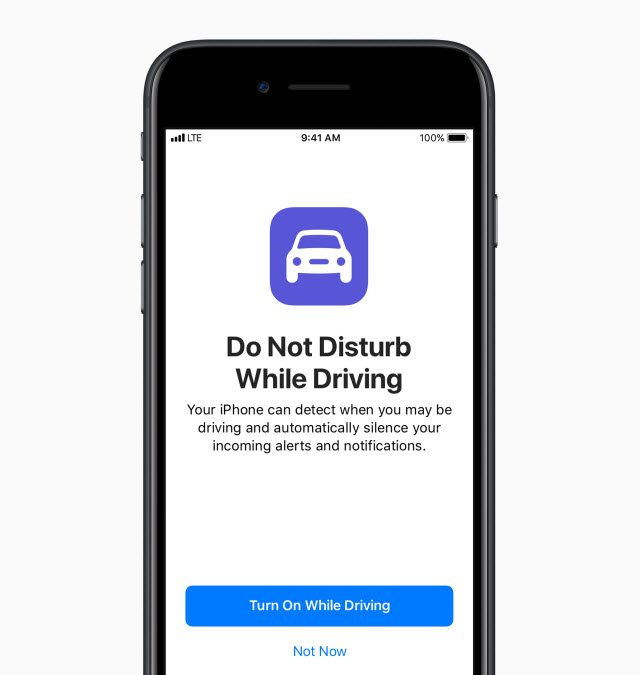
Similarly, the “do not disturb while driving” feature could help reduce the number of fatalities in car accidents caused by the distraction of our phones. It remains to be seen whether users will actually take advantage of this new feature.
These were the most notable security improvements with respect to the new iOS 11 and the implications they will have for its users.
Always remember to configure your phone in the right way, setting the lock and synchronization options appropriately so you can enjoy using the technology securely.