We are halfway through the year and it is a good opportunity to analyze the extent to which the ideas we gathered in the Trends 2017: Security Held Ransom report have come true. In that document, ESET researchers discussed the future possibilities of some aspects of cybersecurity, and now it’s time to see if everything we expected actually happened, and where we stand today.
Healthcare, target Numero Uno
“It’s been a busy – and occasionally painful – few months since our trends report was released at the end of last year, especially for those in the healthcare IT security community,” said ESET Security Researcher, Lysa Myers.
In October, the Mirai botnet performed massive Distributed Denial of Service (DDoS) attacks by utilizing insecure Internet of Things (IoT) devices. A few months later, a new ransomware family called WannaCryptor was discovered. It swept across the globe with dizzying speed, spreading by exploiting vulnerabilities in the Microsoft Windows implementation of the Server Message Block (SMB) protocol.
“Hospitals have had a particularly difficult time with ransomware in general, and this event was no exception,” explained Myers. In addition to traditional computers at medical facilities in the US and UK being hit, medical devices have also been affected. This shows that a worrying trend continues. Despite the industry incorporating more and more devices, each linked with confidential information and in many cases IoT functionality, security and privacy have, in general, remained a secondary concern.
A push for relevant legislation
Moreover, if we talk about privacy, we should go back to one of the trends mentioned in the 2017 report: the development of legislation that defines how a country's assets are protected, and that promotes cooperation between the public and private sectors, and at an international level.
The best example is the new General Data Protection Regulation (GDPR) established by the European Commission. This aims to give citizens power over how their information is processed and used. It guarantees the right to be forgotten, to opt out of profiling and to data portability.
The most interesting thing is that it not only applies to companies based in the European Union, but to all those who both have and process the data of its citizens – wherever they operate. China also saw a new cybersecurity law come into force, one that prohibits online service providers from collecting and selling the personal information of users. In addition, it grants them the right to have their data deleted.
Thus, we can see how efforts to legislate users’ rights to privacy continue to be globalized.
What about vulnerabilities?
On the Android platform, up until May 2017, 255 security breaches were discovered; just under half of those were unearthed in 2016 alone. This has prompted us to believe that this OS will close out the year with an equal or greater number of identified vulnerabilities than last year.
As regards malicious code, 300 new samples of Android malware have been discovered each month, with the number of detections made by May 2017 representing 26% of the total for 2016. However, variants of mobile ransomware such as Android/Lockerpin increased by 436.54%, affecting Asian countries in particular. In addition, malware keeps appearing in the Google Play Store, as was the case with banking trojans or the Android/Spy.Inazigram spyware, which stole Instagram credentials.
As for iOS, 224 security flaws were reported as of May, 63 more than in 2016, with 14% of them considered critical.
Stepping away from the world of mobile malware, we have to mention the WannaCryptor attack, which has resulted in more than 300,000 victims in at least 150 countries. In a sense, WannaCryptor played the role of canary in the coalmine, signalling the dramatic exploitation of a new set of threats. This ‘success’, came despite the fact that Microsoft had already patched (MS17-010) the vulnerabilities in question two months prior.
Regardless of the steps taken to protect users, the scale of the campaign was made possible because many (users) simply didn’t apply the patches which would have protected them from what ultimately turned out to be the infamous EternalBlue and DoublePulsar exploits.
The same exploits were allegedly developed by the NSA and leaked by the Shadow Brokers group in April 2017. Regardless, the use of these exploit kits is likely to continue to boost malware campaigns and cyberattacks more generally in the near future.
In the meantime, "Shadow Brokers promised to release more zero-day exploits and hacking tools, not only for operating systems, but also for browsers, routers and smartphones," said ESET LATAM Security Researcher Lucas Paus.
"Interestingly, perhaps to take advantage of the number of infections produced by WannaCryptor, the group now promotes a paid subscription for users to become private members in order to receive exclusive access to future releases of hacking tools."
Critical infrastructure
As expected, critical infrastructure attacks have continued, in 2017, to generate headlines and disrupt lives. In the last six months, however, this ecosystem has been revealed as an area of low-hanging fruit, with fundamental weaknesses coming to light.
As ESET researchers anticipated in the 2017 Trends Report, cybercriminals have continued to probe critical infrastructure via the internet to determine how best to attack it. Recent findings on Industroyer, the world’s first malware discovered that is designed specifically to attack power grids, soon to be highlighted at Black Hat 2017 in ESET’s main briefing, took the power grid offline in part of Ukraine’s capital Kiev in December 2016. The attack drew attention to the potential for malware to significantly impact electric power systems.
Well-engineered, the Industroyer malware is able to communicate directly with industrial control systems (in this case switches and circuit breakers) using communications protocols created decades ago without security in mind. This now means that nation states will have to wrestle with the implications of attacks on their critical infrastructure and are on the back foot in addressing the demonstrated gaps in protection. There is no longer any doubt that systems that are neither updated nor strengthened are in danger of attack.
With the Industroyer attack being quite limited in scope, many security researchers have come to view it as a large-scale test. Regardless of the intentions behind it, the main takeaway should be that this is a wakeup call for all those responsible for the security of critical infrastructure worldwide.
Critical infrastructure does not simply stop at physical targets like power grids. In the digital age, critical infrastructure will increasingly include ‘engineered systems’ such as supply chains and the internet itself.
The recent outbreak of the DiskCoder.C malware (aka ExPetr, PetrWrap, Petya, or NotPetya), further demonstrates the connectedness of these issues as supply chain security and critical infrastructure security come into prominence. The DiskCoder attack, masquerading as typical ransomware attack, was aimed at harming Ukrainian businesses and the whole economy of that country.
DiskCoder.C also made it into global systems via businesses interconnected with their Ukrainian partners who had already suffered the primary infection. While this might be considered collateral damage, this resulted in paralyzed systems at companies like Maersk or TNT Express, both major players in global logistics (and supply chains). Thus, the local attack on Ukrainian businesses still managed to damage shipping lines globally, and even closed port terminals in Western Europe and the US.
This means that the global transport infrastructure - which is a crucial component of global trade – suffered a hit and took a warning across the bow. It also demonstrates both the scale and critical impact that attacks like these can have.
This unfortunate case clearly shows that ESET’s prediction, that “malware-influenced power outages such as (those caused by the) BlackEnergy group and others affecting more critical infrastructure: power, water but also supply chains (…) could be more frequent than we thought”, turned out to be right.
This should serve as a wakeup call for securing whole supply chains. It’s an area underestimated by businesses: security experts have long been calling for a holistic approach, while organizations often focus on securing their own properties. The DiskCoder outbreak clearly shows that malware infections may come, albeit unintentionally from your business partner.
“The technical capability shown by Industroyer, along with the scale of the recent DiskCoder.C (aka Petya) outbreak, demonstrate that attacks directed at high-value targets in a nation state pose a high stakes threat to stability for citizens and businesses alike. Mitigation of these threats requires treating all targets with high damage potential, i.e. those with many business partners or with critical ones, with a similar level of importance as critical infrastructure systems,” commented Robert Lipovský, ESET Senior Malware Researcher.
The video game industry as a target and the need to raise awareness once and for all
Along with the further diversification of, and integration between, consoles, the other major trend in this industry is that the information, resources and profiles of gamers have become increasingly valuable.
In fact, Microsoft filed a complaint in the US Federal Court, stating that iGSKY, a Chinese gaming service, is “engaged in the international trafficking of stolen Microsoft Account (MSA) credentials, together with fraudulently obtained virtual gaming currencies for the Xbox video game console”.
Gaming and cyberthreats are moving ever closer, so much so that in 2017 we encountered one of the most unusual ransomware cases ever, Rensenware. Instead of demanding a financial ransom to recover the encrypted files, Rensenware required the victim to get a high score, at the “lunatic” level of a Japanese PC game in order to set the files free.
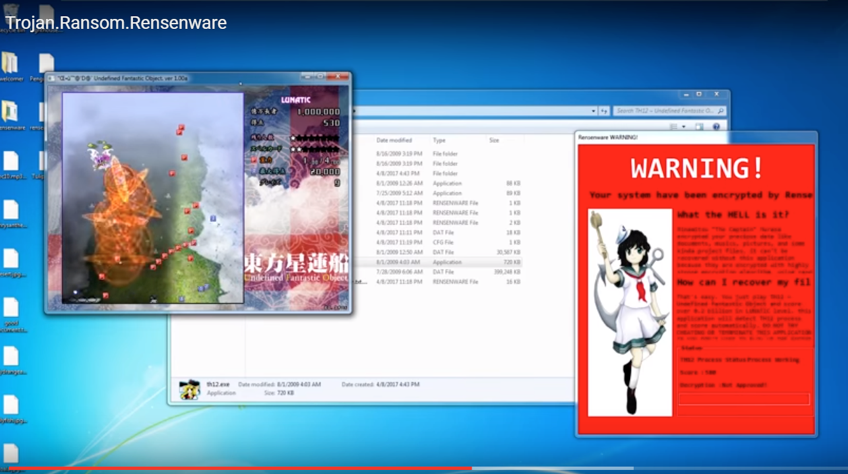
Screenshot of video showing Resenware on YouTube
Fortunately, after gaining spotlight on Twitter, Rensenware’s creator released a decryption tool.
However, video games are far from the only attractive attack scenario for ransomware, since it keeps spreading to multiple types of connected devices. In his section of the trends report dedicated to the Ransomware of Things (RoT) and looking back at attacks on connected cars, ESET Senior Security Researcher Stephen Cobb said: “It doesn’t take much imagination to see which step comes next. Want us to stop DDoSing the heating system? Pay up!”
Though the evolution of connected technology opens increasingly complex attack scenarios, it is the simplest and oldest attacks, the ones that rely on social engineering, which remain the most likely to achieve their goals.
Simple scams promising huge discounts, threats hidden in alleged mobile apps, and malicious extensions are some examples of campaigns that have managed to steal information from unwary users and make a profit.
“The techniques used by the attackers are the same as always: an email or a social media post that is attractive enough to catch the attention of the most curious of users”, stated ESET LATAM - Head of Awareness and Research, Camilo Gutiérrez.
Meanwhile, in the antivirus industry …
So-called legacy solutions – meaning anything with a long track record in effective malware detection – are still misrepresented in the media and elsewhere as purely reactive, compared to “machine learning”, touted as the magic fairy dust fallaciously claimed to be somehow unique to so-called next-gen products.
However, ESET Senior Research Fellow David Harley argues that exposure to truly independent testing – rather than self-testing with samples of dubious validity and obscure provenance – has revealed tarnish under this faux lustre. So much so that one company has promoted the absurd notion that testers only use known malware, which somehow disadvantages products that claim to detect unknown malware.
According to Harley, we are in a world of post-truth product testing where newer vendors are trying to manipulate tests and testers in ways that are as ‘new’ as a snake oil merchant is honest.
In conclusion, we can see how the predictions that ESET researchers made are becoming reality while we simultaneously gather proof that both legislation and multiple industries still need to be strengthened (with respect to the threat environment) to face current cybercrime scenarios.
Otherwise, attackers will keep finding ways to deploy and hide their malicious campaigns in the most surprising places – such as within the comments section of an Instagram profile of a pop music celebrity.




