How to check if your system is patched against EternalBlue
By now, most of us have heard about last week’s global ransomware attack, which spread all over the world on May 12th, 2017. It is a new variant of WannaCryptor, which is also known as WannaCry and WannaCrypt, and detected by ESET as Win32/Filecoder.WannaCryptor.D. And it has characteristics of a worm, capable of compromising other computers on the network.
This attack, which is still ongoing, although with less impact than before, has set a new milestone in the history of events related to malware outbreaks. A combination of factors – and some negligence – has enabled the massive damage that this “ransomw0rm” has caused.
In this post, we will address what we can learn from this event and what may come next. We also provide a simple script that allows you to check whether your Windows PC is patched against EternalBlue.
EternalBlue and WannaCryptor’s wormness
EternalBlue is the name of the exploit that enabled WannaCryptor's ability to self-replicate and, therefore, its rapid spread across the network. Reputedly, the NSA developed this exploit.
This is how this incident can be traced back to the leak of NSA’s cyberweapons, which have been allegedly stolen by the Shadow Brokers group. The group unsuccessfully tried to auction cyberweapons; they changed their minds, however, as the endeavor was not proving profitable and decided to sell the NSA tools individually.
On March 14th, Microsoft released MS17-010, fixing critical SMB vulnerabilities. At the time, it was not evident that the patch was in any way related to NSA cyberweapons. It wasn’t until April 14th, the day on which the Shadow Brokers unveiled many of the stolen tools, that it became clear.
The timing between the patching and the leaking of the exploits raised some speculation about the circumstances of the events. Nevertheless, the situation then was as follows: the vulnerability exploited by EternalBlue was patched and made available via Windows Updates, while the exploit itself was made public.
The race between patching and exploiting had started and it wasn’t by chance that the EternalBlue exploit has been increasingly used ever since.
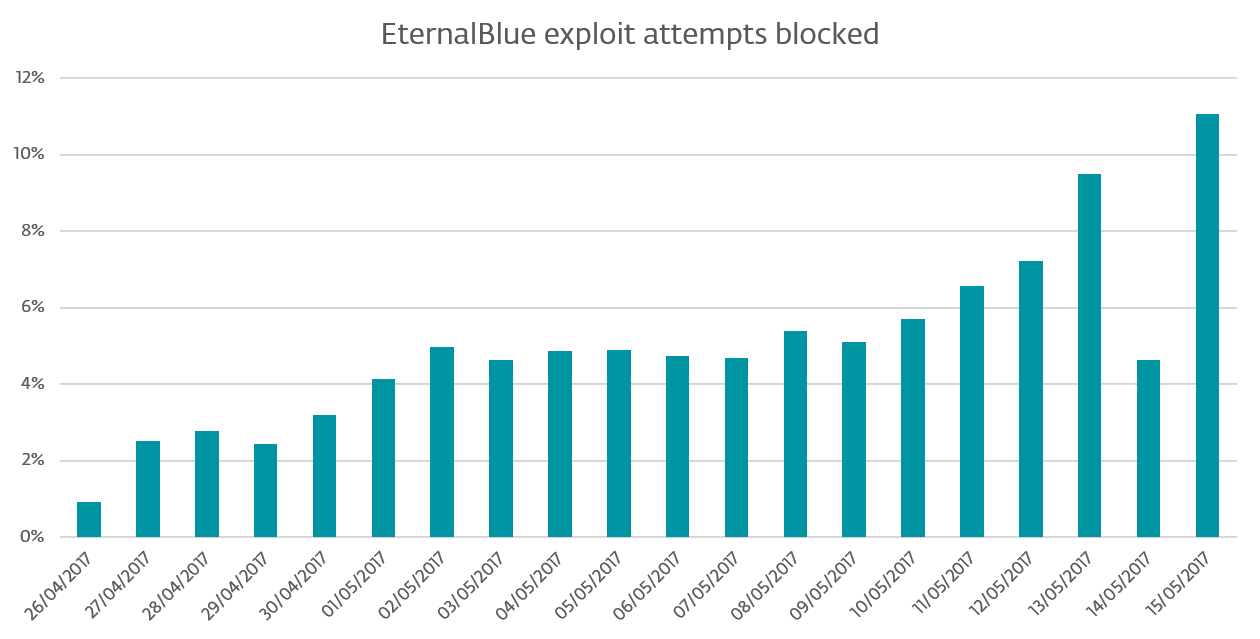
On May 12th, EternalBlue became an important component of the already-mentioned massive infection incident. All the elements were in the cybercriminals’ hands: the ransomware – WannaCryptor has been active since the beginning of April – and the exploit (EternalBlue).

Even so, home users and especially companies could have circumvented the success of this ransomworm in many ways. Firstly, two months beforehand, the patch for EternalBlue was made available. Although it is not related to the ransomware’s encryption routines, it blocks the host from damage caused by another compromised host on the same network. Furthermore, proactive protections installed on the host, such as an exploit blocker or an (up-to-date) anti-malware suite could block infection attempts, and could stop the attack in cases where the malware breaks through the network defenses.
Finally, some degree of control over data that came in and out of hosts on a network could also be helpful. Many companies decided to turn off computers and send employees back home, fearing having their computers compromised. However, if they were able to isolate the hosts on their network and raise detection capabilities, the need for such extreme measures might have been sidestepped.
What comes next?
On Friday night, news about a “kill switch” feature in the ransomware came out. @MalwareTech noticed that the malware made a HTTP request that was supposed to fail before moving onto the encryption routine.
Since the domain was previously unregistered, all requests were failing, consequently enabling the ransomware to encrypt files. However, after registering the requested domain, @MalwareTech was able to redirect requests to replying servers and stop the (first variant of the) ransomworm’s propagation.
It didn’t take long for other variants show up. First, new versions appeared that patched the previous domain – by overwriting the binary data of the first version (using tools such as HEXEdit). Later, versions without the kill switch were also released.
So far, the earnings of this attack have amounted to little more than $50,000, which is negligible in comparison to the damage caused due to this outbreak. It once more made evident that exploiting vulnerabilities (not necessarily zero-days) may have a huge impact on normal business operation.

These fast responses by cybercriminals show that combating malware is no easy task. They strike quickly and are highly adaptive. Thus, after such successful attacks, we expect a replication of tools and methodology and everybody should be prepared for more attacks, especially in the near future.
In the long term, we will probably see more “worm-enabled” malwares showing up, and in the short term, we may well have intense waves of malware variants availing themselves of the EternalBlue exploit. Therefore, patch your system!
Is my system patched against EternalBlue?
Beyond this particular ransomworm case, it's utterly important to verify whether your computer is patched against EternalBlue – bear in mind that other kinds or families of malware might show up using EternalBlue in the near future.
For local verification: ESET has released a free tool to help determine whether your Windows machine is patched against EternalBlue.
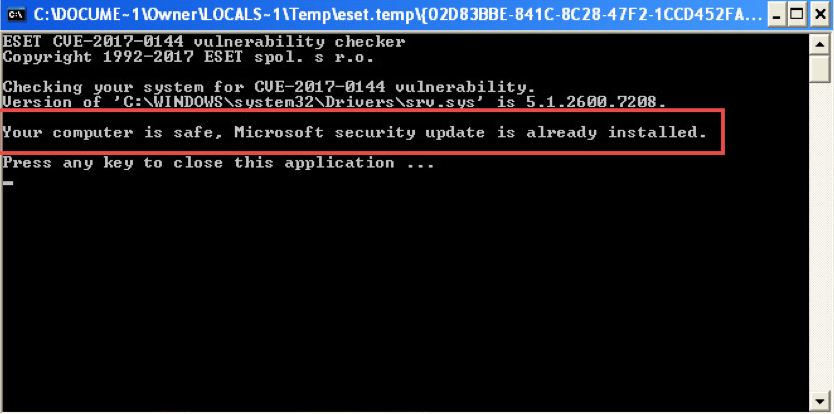
Follow the steps in our ESET Knowledgebase article to check your system for vulnerabilities using the ESET EternalBlue Checker.
For remote verification: A new script capable to test if a host is vulnerable to EternalBlue was added in nmap. As commented in the code, the script “attempts to detect if a Microsoft SMBv1 server is vulnerable to a remote code execution vulnerability (ms17-010)”.
NMAP v7.40 (or higher) should work with the following command:
nmap -sC -p445 --open --max-hostgroup 3 --script smb-vuln-ms17-010.nse X.X.X.X/X
Ultimately, patching is the best countermeasure against EternalBlue, since it addresses the root cause of the vulnerability targeted by the exploit.
For more on the WannaCryptor, aka WannaCry, ransomware attack, check out the following:




