Recently, here at our research lab, we have seen an increase in the number of JS/Chromex.Submelius threats detected. In countries like Colombia, Peru, Ecuador and Chile, the detection levels for this particular threat have been as high as 30% or 40% of the total threats for the entire country.
This is a trojan that redirects the user’s browser to a specific URL, which contains another kind of malicious content. Given the high detection levels for this threat, which primarily targets Chrome, currently one of the most popular web browsers, we set out to find out how the threat is being propagated and how a user might fall into its trap.
Watch whatever you want … but get infected at the same time
We found one example of how this threat is being propagated on a popular website for watching movies online. In one of the options for watching the content, when the user starts playing a movie, an additional window opens in the browser:
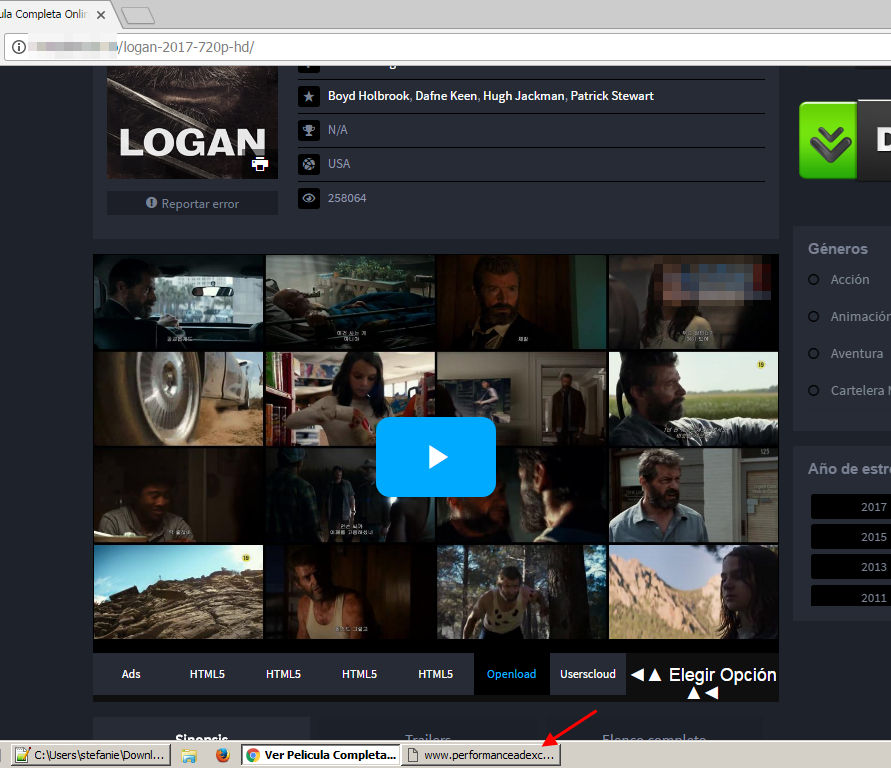
Anyone who has ever visited this kind of website will find nothing particularly unusual about this, as new windows often pop up saying things like “a virus has been detected” or “earn money by working from home”. In this case though, the browser does not redirect to another page with an ad as usual, but goes to a website which then asks you to go to another URL … and the message won’t stop appearing until you click “Accept”.
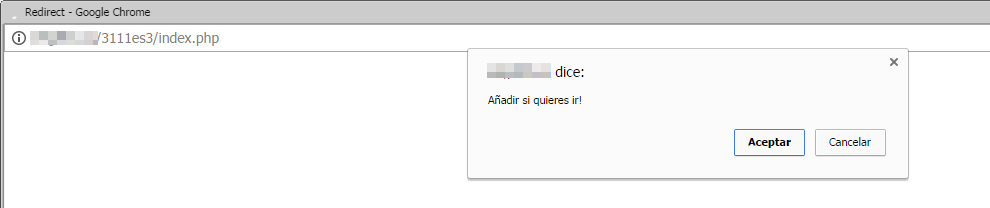
This new redirection points to a download of an extension from the Chrome web store. The following screenshot shows what the browser’s address bar looks like before the extension is installed:
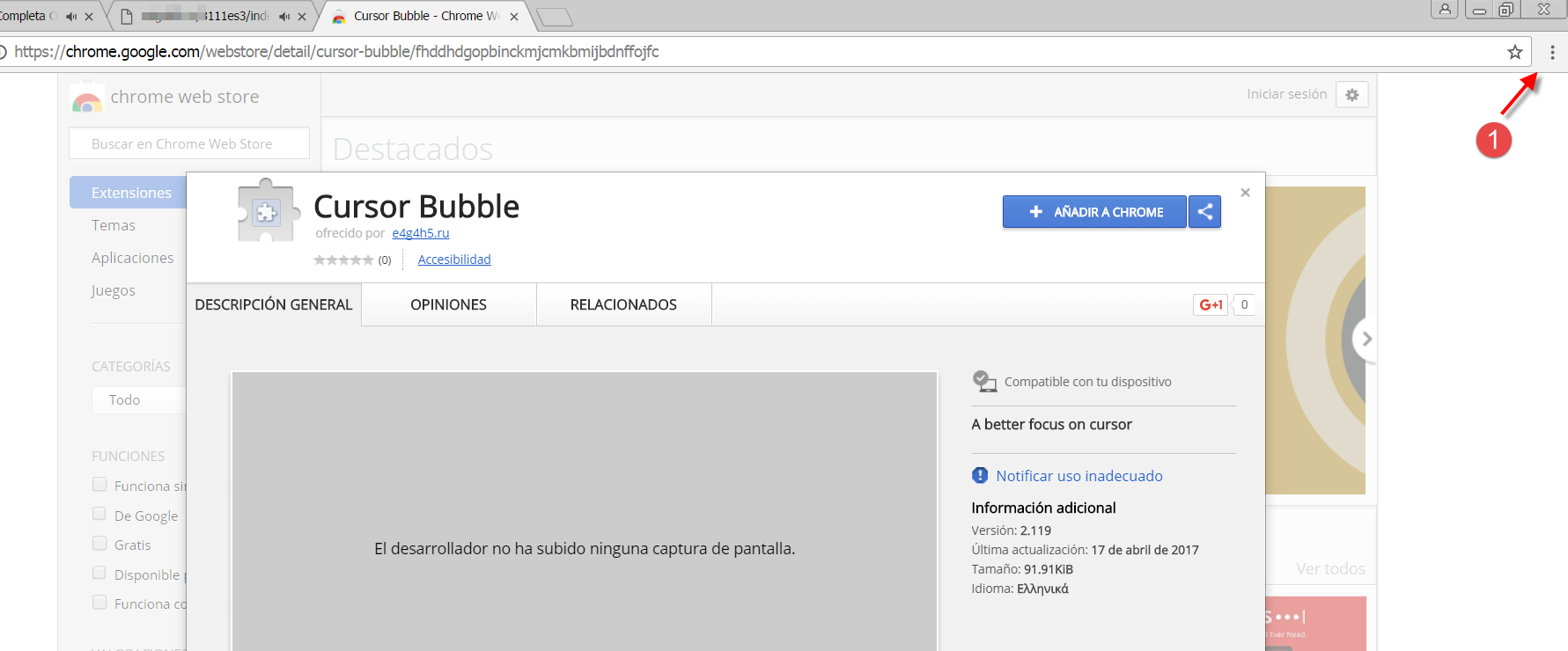
If the user accepts the download, a space appears next to the address bar with the extension icon, and, if you click on it, it takes you to a new page within the Chrome web store for a different extension. In this case, as you can see in the following screenshot, there are some recent comments saying the app is useless:
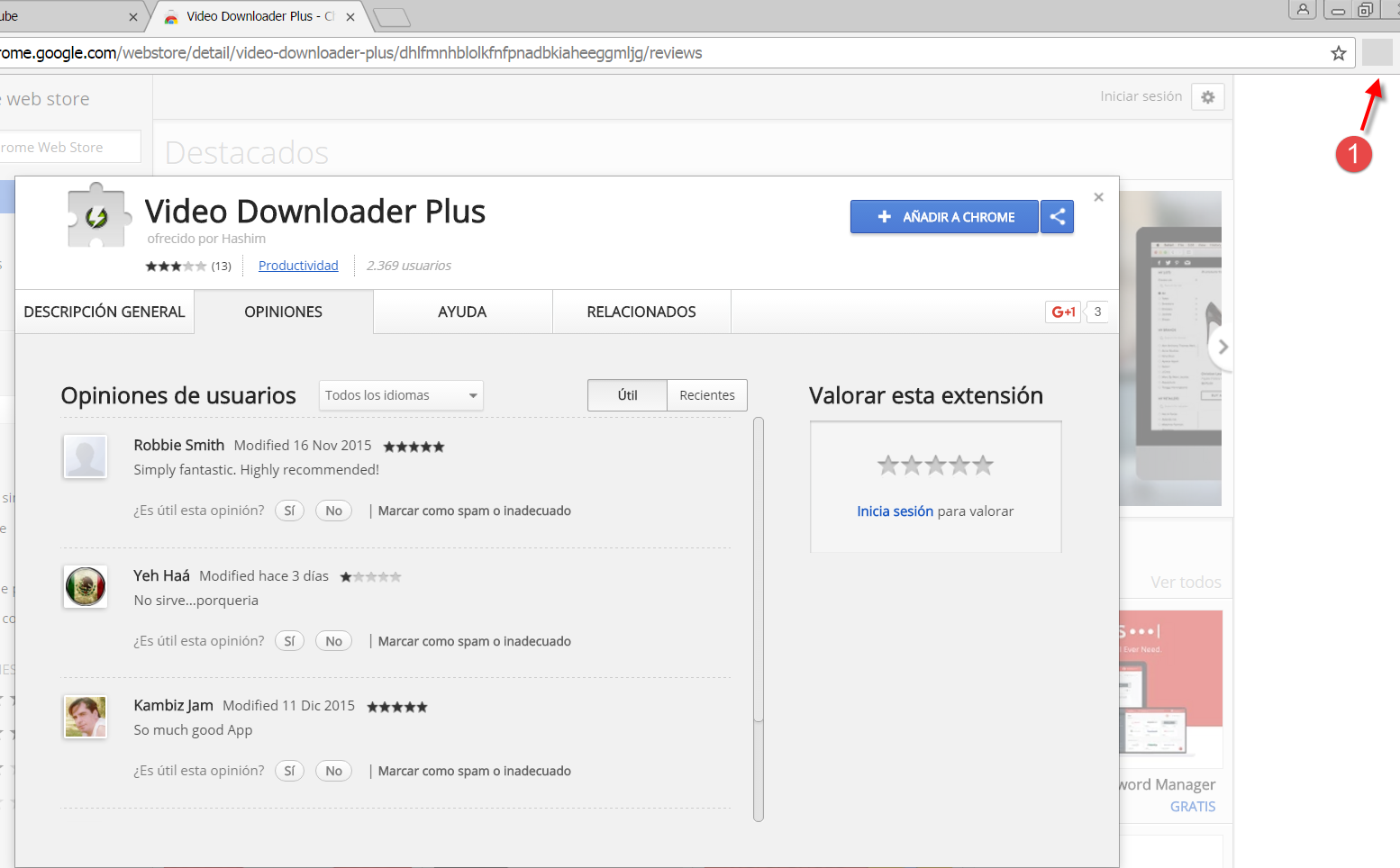
If the movie has started playing by this point, the user’s browser will have been infected. If we go and look at what extensions are installed in the browser, we find the one that was downloaded first, and we see that its permissions include reading and changing all your data on the websites that you visit. This leaves an open window so that when the user visits any website some code is injected into it:
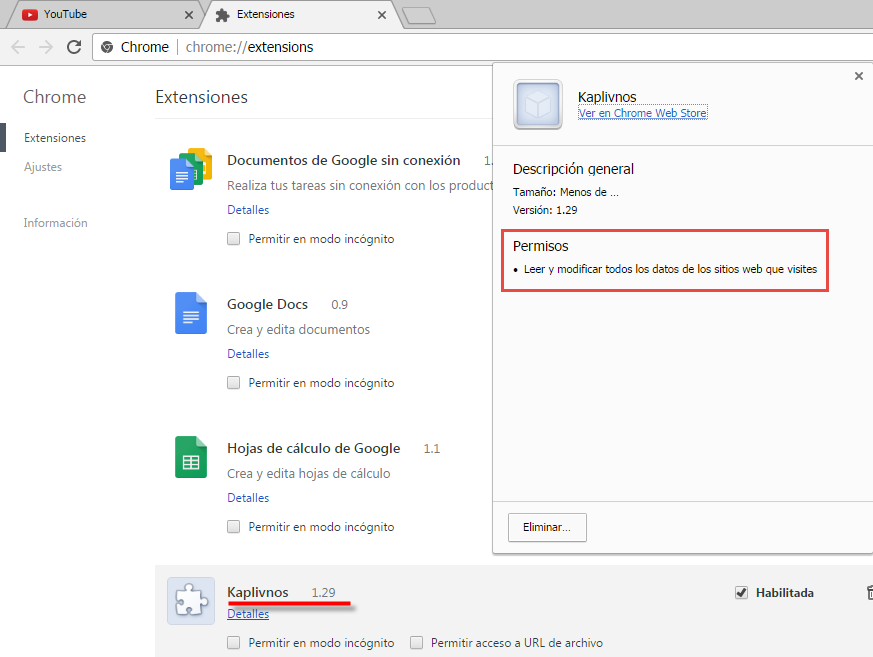
Then, while compromised users are browsing the internet, they will suddenly see new windows opening up with information about their systems, taking them to other websites containing downloads of malicious code, advertising, or other kinds of content. This becomes an endless loop, which ultimately will benefit whomever is behind the fraudulent extension.
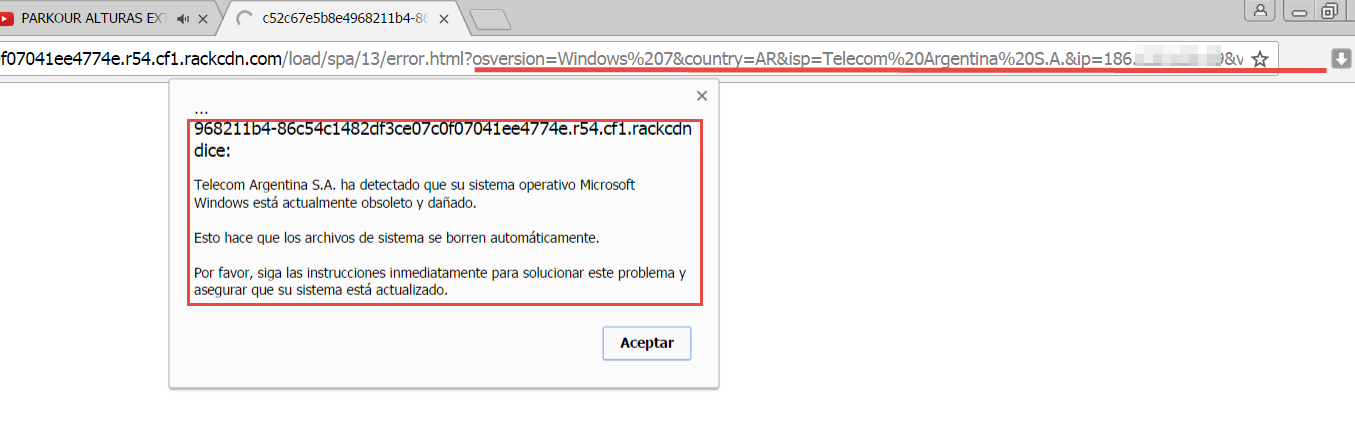
What can you do if you have downloaded the extension?
If you have downloaded this malicious extension you should remove it immediately from your Chrome browser. To do so, you can type “chrome://extensions” in the address bar and then, when you find the extension, simply delete it.
As a further precaution, you should also analyze your computer or device using a trustworthy security solution to rule out the possibility of having downloaded any other kind of threat to your machine.
As always, it is very important to be careful before clicking on anything and pay close attention to all websites you visit, especially if they ask you to download extensions. We have already seen other campaigns associated with YouTube, Facebook, and other websites that have worked in similar ways.
So, we can see that this kind of campaign is by no means an isolated case. In fact, there is a whole structure of redirection, which we will look at in more technical detail in a future article.
Image credits: ©Roger Casas-Alatriste/Flickr




