Introduction
After our recent joint blog Support scams now reign in Spain, Josep Albors was contacted by a Spanish online newspaper asking for further information and general commentary. So here, first, is my general commentary on the evolution of the tech support scam and why the current high incidence of reports in Spain (and, to a lesser extent, other parts of the world) is so significant. The subsequent article in El Confidencial can be found here (in Spanish).
How support scams became a statistic
Tech support scams implemented through cold-calling started as a triumph of a diseased imagination, closer to an old-fashioned virus hoax like Good Times than to real malware. You could compare them, in a way, to malware that spreads by pretending to be some form of security software – a social engineering trick that goes back to the 1990s and earlier. However, early tech support scams are monetized without the aid of real malware. They are almost pure social engineering and depend on finding victims with very little knowledge of how computers and (usually) Windows really work. Though some of the tricks they used (and still use) to persuade the victim that there is a real problem on his or her system are quite clever, they rely on misrepresenting the output of legitimate utilities, rather than using malware.
"The newer generation of scammer, however, uses programs that are nearer to malware, in order to drive the victim into calling the scammer rather than vice versa."
The newer generation of scammer, however, uses programs that are nearer to malware, in order to drive the victim into calling the scammer rather than vice versa. Mostly, they stop short of using real ransomware, but they generate messages that deceive the victim into thinking that his system is seriously threatened. While this can be an effective attack, it does mean that there is now a malicious program in play that can be detected by security software. (Clearly, it isn't usually appropriate for legitimate system utilities to be detected as malicious.)
This enables us to offer some technical protection where before we were mostly only able to publish warnings and attempts to educate. But it also means that we can offer some reasonably accurate estimates of how much this type of attack is being used. We can't state accurately how many people are actually falling victim to it, but we have a pretty good idea of how many people we're protecting from it.
Q&A
The journalist in question also asked a number of questions arising from the blog, which we thought might be of interest to others. Since my ability to write Spanish is minimal, Josep took on the task of responding directly, but I haven't been able to resist adding a few comments of my own for this article. And, of course, any errors in translation are mine.
Scam with a bit of a (ping) pong
- You say that this is an old scam – and that you've been talking about it since – but it sounds to me as if it is even older. It almost sounds like the PingPong virus. :D
Tech support scams go back earlier than 2010 – Steve Burn was writing about them in 2009 and presumably there were instances even before that – but it was the year when we first started to receive reports about it at ESET. What does seem clear is that since then it seems to have become a pretty lucrative business for criminals.
[DH: For the benefit of our younger readers, Ping Pong was an early (c. 1987) boot sector virus (BSV) also known by other names such as Italian, Vera Cruz, Bouncing Ball and Turin. It was most notable for the visual effect from which it got the name Ping Pong. It was a real (and at one time notorious) virus. However, BSVs as we knew them at that time, are hardly ever encountered now (though they are to some extent related to modern bootkits). There is, of course, no way in which such an infection could be detected or diagnosed by system tools as deceptively misused by tech support scammers.]
Fake support, not fake victims
- Your article gives percentage statistics for these attacks, which in Spain would be 37.8%. Percentages of what? What figures are we talking about and how do you obtain these metrics? Are these cases detected by your antivirus or are there people who have informed you of the facts? Where are these figures recorded? How many REAL victims would there be?
The percentage you mention is taken from detection statistics received from installations of ESET security products, as installed by more than 100 million users worldwide. They represent reports from all systems on which the user has chosen to leave ESET's Live Grid® telemetry active at installation. This not only provides a means of tracking known threats, but also acts as an early warning to protect against suspicious code and as a reputation system that improves performance.
"What we're reporting here is specific malware, not every possible way in which victims might be drawn into the scam."
That is why we say that in Spain, of the total detections made during February by ESET security solutions, 37.8% belong to this class of threat. While this can't include detections on protected systems where Live Grid is not activated, or on systems protected by other security vendors, it does give us a pretty good picture of what threats are being detected out in the real world and in what numbers. We don't, however, give out exact numbers as it's rather easy for that information to be misinterpreted as absolute statistics. (In other words, we don't want to see ourselves quoted as saying that 11,345 computers were threatened by [some virus or other] last month: it's very unlikely that every threatened machine in the world belonged to one of ESET's customers.)
If by 'REAL victims' you mean people who have actually lost money to the scam, our telemetry doesn't tell us that because those are usually people who either aren't protected by our security software (or another vendor's, of course) or were lured into the scammer's web by other means, for example, cold-calling. What we're reporting here is specific malware, not every possible way in which victims might be drawn into the scam. We have no reliable way of estimating how many people are affected overall, since:
- We don't have access to reports made to other agencies, other vendors and so on.
- We can't reliably estimate how many people have been scammed, but haven't reported it at all. It's all too likely that there are some people who don't report being scammed because they have paid scammers for 'protection' and don't realize that they're actually no better protected now than they were before.
- The data here concerns ESET users who are alerted to the threat by security software and so are not usually affected because they close the web link that generates the alert and ignore the fake threat warning.
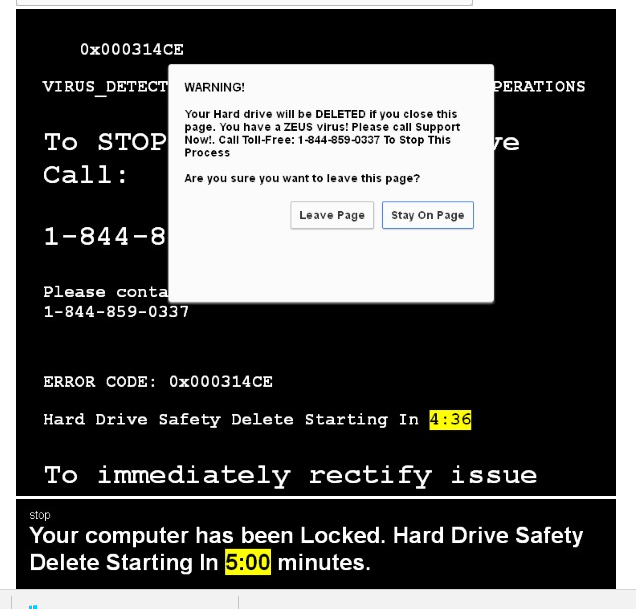
Figure 1: A Scary Fake Alert
What we can say is that HTML/FakeAlert presents as a really high percentage of currently-detected threats. This suggests that a significant number of internet users in Spain will have seen some of these fake alerts promoting technical support scam sites, whether or not they are protected from this particular malware. Not just in Spain, either. At the time of writing, HTML/FakeAlert is the second most commonly reported threat worldwide.
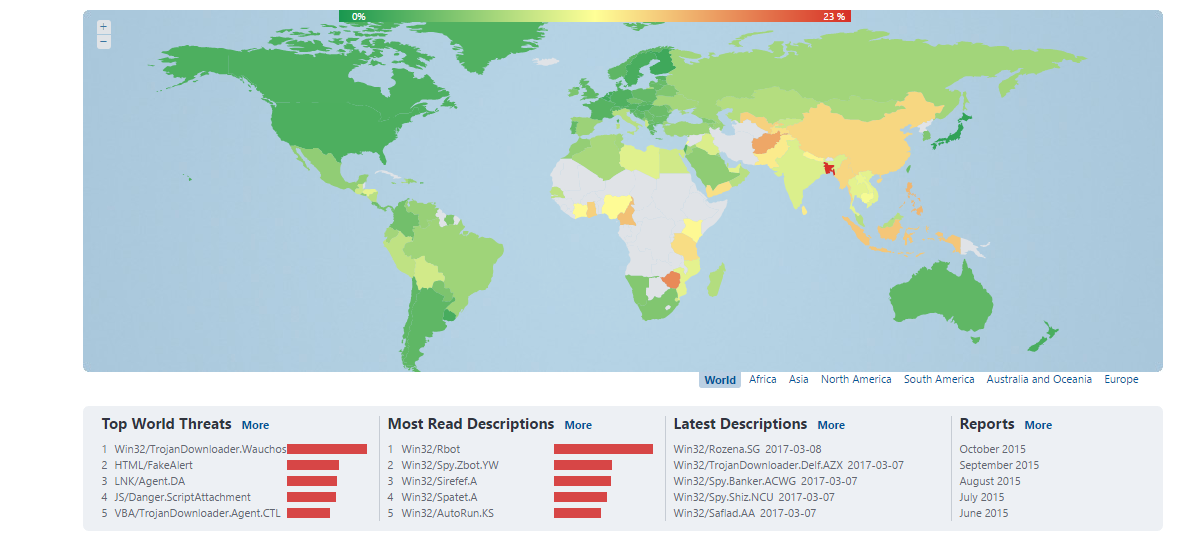
Figure 2: Top World Threats (early March 2017)
Statistics: Ebb and flow
- When did you start to notice this increase? Are we still seeing the threat at these levels right now or have they fluctuated upwards or downwards? You say this scam represents 50% of cyberscams in Spain – is that correct? What would be the second and third in volume?
According to the data we collect and publish on our website Virusradar.com, this type of detection was first observed in Spain in July 2016, and the numbers have increased continuously since then. The figures fluctuate over time, but detections in Spain do, at times, currently peak to represent 50% or more of all detections. The figures don't reflect the prevalence of all scams as such: they represent the prevalence in one region of malicious software, which in this case is a very specific type of malicious software used in support scams.
"Many scam incidents, however, don't involve the use of malware at all, so ESET doesn't collect prevalence data that relate to those scams."
Many scam incidents, however, don't involve the use of malware at all, so ESET doesn't collect prevalence data that relate to those scams. We don't, for instance, have figures relating to cold-calling scams where the scammer didn't use software that can be described as unequivocally malicious. (When scammers misuse legitimate utilities like Event Viewer or ASSOC, it's not usually feasible to determine programmatically that they're being used inappropriately.)
Of the malicious programs prevalent in Spain that Virusradar.com does tell us about, however, in second place, at time of writing (and quite a long way behind), are the malicious attachments in JavaScript format that have been used by criminals in recent months to propagate variants of ransomware. Also commonly associated with ransomware and other threats is the Nemucod trojan, malware that criminals use to attack their victims' systems and to download other threats, without the knowledge of those victims.
Profiling the victim
- Does this affect home users or companies, mostly? Computers or mobiles?
The infected websites that display these false alerts cannot distinguish between domestic and corporate users. However, their main targets are users of home computers with little computer knowledge. While corporate users may also see the alerts sometimes, they may be better protected than the average home user against the malware that generates such alerts, and in any case are more likely to have a computer-savvy IT person to consult. Home users are generally more vulnerable to these attacks and more likely to fall for this type of deception.
These figures do not include malware that affects smartphones at the moment, although there are variants of ransomware that use similar techniques to get the user to install malware on their devices, and there have been reports of pop-ups and JavaScript dialogues targeting iOS and Android (and even macOS) users going back at least a couple of years. Here are two examples:
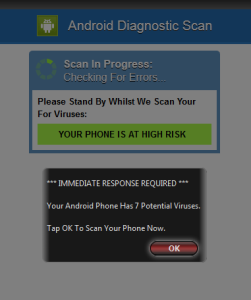
Figure 3: Fake Alert Targeting Android Users
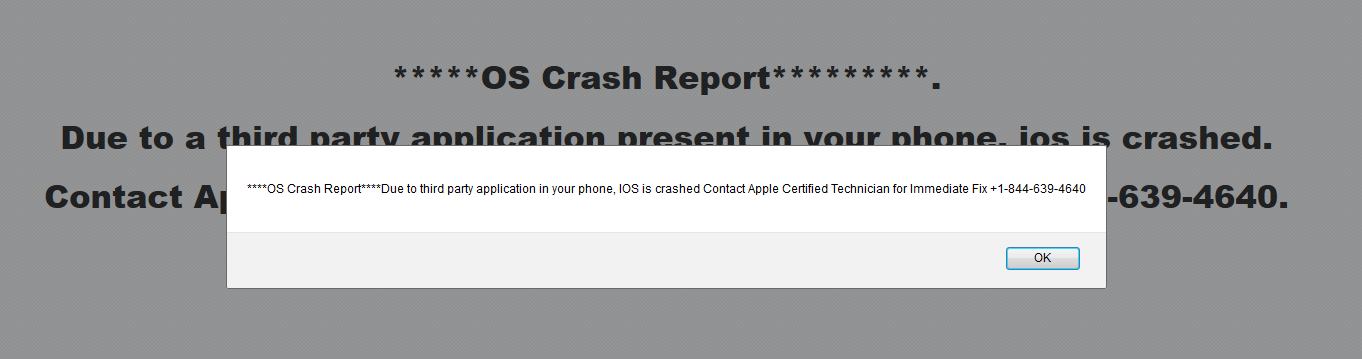
Figure 4: Fake Alert Targeting iOS Users
Vectors and victims
- From what I've read, these are viruses that arrive with deceptive links in email or via malvertising. Where is the highest incidence, in malvertising or links by mail? Is the malvertising specific to certain types of web page? Are they linked by geographical distribution, by age, or the interests of the victims?
The cases that we have been analyzing for the past few months usually use malvertising or redirect to fraudulent or compromised web pages. When we talk about malvertising, any website can show this type of malicious advertisement if it does not itself monitor and control the ads that it allows, no matter how popular the advertisers are. Regarding geographical or age distribution, criminals were initially looking for native speakers of English, primarily in the UK, US, South Africa and Australasia, but they began long ago to experiment with other regions and languages as well.
"Their favorite victims seem to be of advanced age and have little computer knowledge.
From our current observations, we do not believe that they distinguish between their victims by age in terms of distribution of the malware, but their favorite victims seem to be of advanced age and have little computer knowledge, which makes it easier for the scammer to sound convincing in conversation on the telephone, irrespective of whether the scammer or the victim initiated the phone call.
Smelling a RAT
- You say that when a victim calls the 'helpline', they install a remote access program on his system, but it is not clear how they do this. Could you give me a 'for dummies' explanation?
It is as simple as asking the victim to access a website and install a remote control program such as TeamViewer. This is an example of a perfectly legitimate program much used by companies and internal IT units for providing genuine technical assistance. If the victim believes that he is talking to an official technical support service center, he has no qualms about following the instructions of the 'support provider' at the other end of the phone.
The routine detection and blocking of legitimate tools is generally considered ethically inappropriate by security companies, though some vendors and providers see things differently. For example, TalkTalk, whose customers have had more than their fair share of exposure to support scammers, has chosen to block TeamViewer, a measure that may be more convenient for the ISP than for some of its customers.
RATs, Dungeons & Dragons
- I understand that if the customer decides that they do not want to pay, a Remote Access Tool may already have been installed, if they have followed the scammers’ instructions up till then. And then what? Are they then stuck with a trojan on their system? Do you have examples of such cases?
They are left with a remote control tool installed; a tool that has a legitimate use and that a large number of real support services use in their day to day work to resolve queries. It is unusual for the fake technician to re-access the machine once the payment has been made (or denied). That said, it isn't unusual for the scammer to attempt to trash the victims' systems while they're still connected remotely. It is also true that we have analyzed cases in which these kinds of tools have been used to install ransomware and force them to pay a ransom. Here's an example:
[Josep's example is a blog article in Spanish, but here's a translated extract. - DH]
… So, we were not surprised when we heard the news that cases have been reported in which criminals infect their victims with ransomware and later offer to help them to recover their files, while pretending to be an official Microsoft technical support service provider.
The first indication we saw of this scam variation came with the publication of a tweet by the researcher Jakub Kroustek , in which we observed a screenshot of a 'kidnap note' in which victims were told that their files had been encrypted and they should call a Microsoft support technician to make a payment of $349.99 to recover them.
'this is not Microsoft vindows support
we have locked your files with the zeus wirus
do one thing and call level 5 microsoft support technician at 1-844-609-3192
you will files back for a one time charge of $349.99'
Unfortunately for the victim, calling this so-called support line will simply cause him to be redirected to a website with a form prepared so that he can make the payment, but there is no decryption tool provided. This shows that criminals only want the victim's money and that this business model still has much more to do with traditional fake support services than with ransomware.
Not that ransomware gangs are more honorable or honest than tech support scammers, of course, but their business model is different. It's not unknown for ransomware gangs to demand money – sometimes, ridiculously large sums – for the recovery of files that they can't, in fact, recover, but the effectiveness of the attack relies on the victim's knowledge that in most cases but by no means all the scammer will provide a decryption key. If more scammers took the money but didn't help recover the files, the scam would be less successful because fewer people would pay up.
"A support scammer generally takes one shot at a potential victim rather than aiming for repeat business."
A support scammer generally takes one shot at a potential victim rather than aiming for repeat business and relies on that victim's not knowing the nature of the scam. If people, in general, knew as much about support scams as they do about ransomware, support scams would be less economically viable for the scammer.
In fact, it's been common for some years for support scammers to attempt to trash the systems of victims who chose not to pay but had allowed the scammer remote access to those systems.
Here's a (slightly edited) extract from an earlier article about how support scammers do cause direct damage to their victims' systems:
Here be dragons: The scammer’s revenge

The sort of damage that we tend to see reports of ranges from direct financial loss due to payment for unnecessary and sometimes damaging installations – through the installation of intentionally malicious software and theft of sensitive data – to the intentional trashing of the system, or rendering it inaccessible using some form of encryption in the manner of classic ransomware. One way in which support scammers often impact seriously on victims happens when a victim is incautious enough to allow access to their PC, then decides not to pay for the scammer’s help.
"A tech-savvy scammer – and they do exist, unfortunately – can render the victim’s system unusable.
I’ve seen frequent reports where this scenario has arisen and the scammer takes advantage of the remote connection to trash the system. A tech-savvy scammer – and they do exist, unfortunately – can render the victim’s system unusable. The scammer may even booby trap the system immediately he gains access, either in order to trash it if the victim doesn’t play ball, or so that he can get access to the PC (and the victim’s credit card) again in the future.
- They may steal files and data for further misuse and abuse, though stories of this actually happening are hard to verify. (Apart from credit card data, of course.)
- They may delete files and programs. There are even reports of scammers misusing the Windows utility Syskey so as to lock the victim out of his or her own system, though it’s hard to say how widespread this unpleasant gambit really is.
- They may add programs to the system that are essentially harmless and even useful, though in such a case they’ll usually be software you could get for free elsewhere, or else pirated versions of legitimate software that may or may not work without proper licensing.
- They may install malware, as described above …
Scammers cleaning up – not in a good way
- How much do these people try to charge to 'clean' the system? How do their victims pay? Do they charge you for an antivirus program or charge you for "protection" for one year?
The amount fluctuates widely and can range from less than 100 euros to more than 200. The payment might be made by credit card (which increases the chances of using it fraudulently) via PayPal or, in more unusual cases, using bitcoins.
These fake technicians usually charge victims for solving problems that do not actually exist on their systems, and to convince the user of a 'problem' they usually misrepresent perfectly normal alerts that are shown routinely in Windows Event Viewer. However, they may also try to sell some kind of annual subscription to a "protection" system, just like fake antivirus software did years ago.
Spanish and Scammish
- I understand that the key to this scam in this region is the people who work the phonelines at the call center, and who speak Spanish. Are they Spanish or South American? Do you have more information on the call center side?
Because they had little success among Spanish-speakers when the calls were made by English-speaking people (although they did try reading Spanish from scripts, spoken with a terrible Spanish accent), the swindlers decided to change their approach and to use Spanish-speaking agents.
In one of the cases in which we ourselves (Josep's team) called one of these call centers, supposedly located in Barcelona, the person we talked to had a Latin-American accent (although we were unable to identify exactly which country in that region). What we could deduce from the time we were on the phone is that they are trained to have a lot of patience, and to treat callers fairly cordially. We could also tell that they were not exactly alone in those call centers, since in the background we heard many other calls being answered.
This sounds very like some of the conversations I (David Harley) have had with scammers claiming to be in London or Manchester. These generally had strong Indian accents, but that doesn't prove they weren't in the UK, of course. However, trying to pin them down to a particular part of London or Manchester (both cities in which I've lived) strongly suggested that they had absolutely no knowledge of those cities. Nonetheless, the days when all support scamming came from India are long gone.
Why Spain and France?
- Why is Spain now a target? And why France? Is there any logical explanation?
We assume that they are expanding their activities beyond the borders of the English-speaking countries on which they were originally focused in search of a larger pool of fresh victims, and it seems to be the case that in Spain we are still in the habit of solving incidents of all kinds over the telephone. The growing success of 'virtual abduction scams' reported to the police shows that Spain is an attractive market for these criminals, since Spaniards seem to be more willing to pay than citizens of other Spanish-speaking countries. Something similar must be happening in France.
[The abductions to which Josep is referring here are not real kidnappings, but phone scams where the criminal tries to persuade victims that a close relative has been kidnapped, and demand a ransom. I hadn't come across this scam previously, but Josep tells me that these calls, often made from prisons in Latin America, have been seen in greater numbers in the past two years. And not, it seems, only in Spanish-speaking countries.
While a Guardian article by Sam Levin suggests that the scam was used earlier to target the families of US citizens on vacation in Mexico, it details one of the growing numbers of similar incidents fully transplanted across the border to California and elsewhere in the US. The fact that these calls are made in English suggests the possibility that US criminals have adopted a 'foreign' scam in the same way that they have tech support scams. While virtual kidnapping seems to me to be an order of magnitude uglier than support scamming in terms of the trauma it can inflict upon its victims, there are clear similarities between virtual kidnapping, Londoning, and tech support scams, in that they all extort money from the victim to address crimes that haven't actually been committed. In other words, the assertion of a criminal act is in itself the crime. (I'd be tempted to call these metacrimes, if the term hadn't already been appropriated with a number of other meanings.) – David Harley]
Finding the Fraudster
- Is it easy to track down the perpetrators of these crimes? My understanding is that if there is malvertising there will be some way of tracing them through IP addresses – or is that not the case? Do you know whether there have been arrests made?
You can track down the phone numbers that these scammers provide so as to get in touch with them and see who has hired them. When the scammer makes the call it's more difficult since they tend to hide the caller number or use generic numbers that are used by many organizations – admittedly, certain numbers seem to be particularly popular with scammers of all varieties. However, that doesn't make identifying a particular scam call any easier, and doesn't prove that the owner of the line is behind the scam. There have even been cases where the number provided belonged to a public organization and was only being used temporarily to redirect calls to a call center without the knowledge of the legitimate owners of that line.
While the companies behind scam sites can often be traced through their IP addresses and/or domain name registration, the pursuit of those companies, even where DNS registration is not anonymized, can be very difficult across national/international borders.
We can confirm, though, that there have been police operations related to this scam resulting in arrests. For example, a few days after publishing a post on our blog on this issue in early October, an operation was carried out by the Mossos d'Esquadra in Barcelona, which ended with the arrest of several people related to this type of scam. In the US, court action has been taken with some success against foreign companies with assets in America.
Sense and Skepticism
- What can our readers do to avoid falling into this trap?
Basically, follow your own common sense and distrust unsolicited offers of support: reputable websites don't and can't check your system for malware unless you actually ask them to, as in the case of an online scanner such as ESET's. Pop-up messages directing you to 'help lines' are really just a means of avoiding the well-worn and well-documented cold-calling approach and diverting the cost and effort of contacting potential scam victims to the victims themselves.
"follow your own common sense and distrust unsolicited offers of support"
If you really have a problem or have doubts about the security of your system, contact the official support numbers that companies make available to their users on their websites. Be aware, though, that support scammers (like other scammers) go to considerable lengths to get their pages noticed by search engines. If you want help from a security company, try to make sure that it's the real company you're contacting, not some scammer claiming to offer support for a product with which he has no legitimate affiliation.
In the end, everything is reduced to a healthy skepticism: don't take for granted the goodwill and technical competence of people and companies who turn up unexpectedly on your PC or at the end of your phone. Many of the effects of malicious activity that most of us see nowadays are based on social engineering, the art of manipulating the victim through psychology: mistrusting technobabble, high-pressure salesmanship and scaremongering is a good idea, whatever they're trying to sell you. And once you realize that the pop-ups and scary messages are not to be trusted, you don't have to put up with all that fraudulent salesmanship.
Ultimately, the scammer's job is to convince you that he knows more about your system than he really does or can, as a preparation for persuading you to allow him remote access to your system. Start off by assuming that he can't know whether your system is secure and don't volunteer information that makes it easier for him to sound knowledgeable, check out some of the ways in which he might try to persuade you that you have a security problem, and don't give anyone remote access unless you're absolutely certain that they're legitimately offering services that you're actually signed up for.




