A 29-year-old man has been arrested at Luton airport by the UK's National Crime Agency (NCA) in connection with a massive internet attack that disrupted telephone, television and internet services in Germany last November.
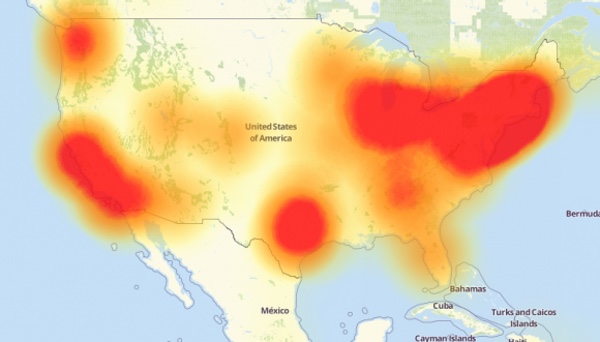
As regular readers of We Live Security will recall, over 900,000 Deutsche Telekom broadband customers were knocked offline last November as an alleged attempt was made to hijack their routers into a destructive botnet.
Someone was commandeering vulnerable Zyxel and Speedport routers, recruiting them into a botnet which they could then command to launch huge denial-of-service attacks against websites. The attack exploited a vulnerability in the TR-069 and TR-064 protocols, which are used by ISPs to manage hundreds of thousands of internet devices remotely.
In this particular case, attackers were able to fool the vulnerable routers into downloading and executing malicious code, with the intention of crashing or exploiting them. Compromised routers could then be commanded to change their DNS settings, steal Wi-Fi credentials, or bombard websites with unwanted traffic.
The NCA arrested the British man under a European Arrest Warrant issued by Germany's Federal Criminal Police Office (BKA) who have described the attack as a threat to Germany's national communication infrastructure.
According to German prosecutors, the British man allegedly offered to sell access to the botnet on the computer underground. Agencies are planning to extradite the man to Germany, where - if convicted - he could face up to ten years imprisonment.
At the same time as the attack on German routers, customers of Ireland’s biggest telcommunications provider, Eir, were also experiencing problems accessing the internet via their ZyXEL-built broadband routers in what is thought to have been a similar attack.
Attacks like this are part of a bigger trend.
2016 saw a series of high profile IoT-based DDoS attacks which caused widespread disruption of well-known websites via the Mirai botnet, the release of urgent firmware patches, and forced recall of vulnerable webcams.
It's clear that more manufacturers need to treat the issue of IoT security as a priority in 2017 and beyond.
But the way forward doesn't stop there.
We all as individuals need to take greater care over our router security, as it's clear that many people have their heads in the sand about the problem. If you need any greater illustration of that, consider ESET's own research which determined that at least 15% of all home routers used weak passwords and 20% have open telnet ports.




