Recent phishing scams targeted both Gmail and Yahoo, and now attackers have their sights set on PayPal with some very convincing bait. With fake websites and email campaigns that look real, it’s easy to be fooled, and potentially have your identity and money stolen by scammers. Here’s how it happens.
First, there’s an email with logos and verbiage that sounds great (that is, "look and sound authentic"). Notice, however, errors in grammar and syntax that suggest the author isn’t a native English speaker. That’s one of the clues.
When unsuspecting users click the Log In button, the victims-to-be aren’t taken to PayPal properties, but through a shortened link like this:
That, in turn, leads to a landing page here:
… where they are presented with a real-looking fake login screen that even has an SSL certificate to suggest it’s authentic. But don’t be fooled.
Notice the domain has nothing to do with PayPal sites, but rather are scam URLs. As with other campaigns, scammers typically use a myriad of dynamically generated domain names — sometimes slight variations on the real name — which is another clue that something isn’t right.
Once you enter your information, you are presented with another message with fake information appearing to corroborate the text of the email:
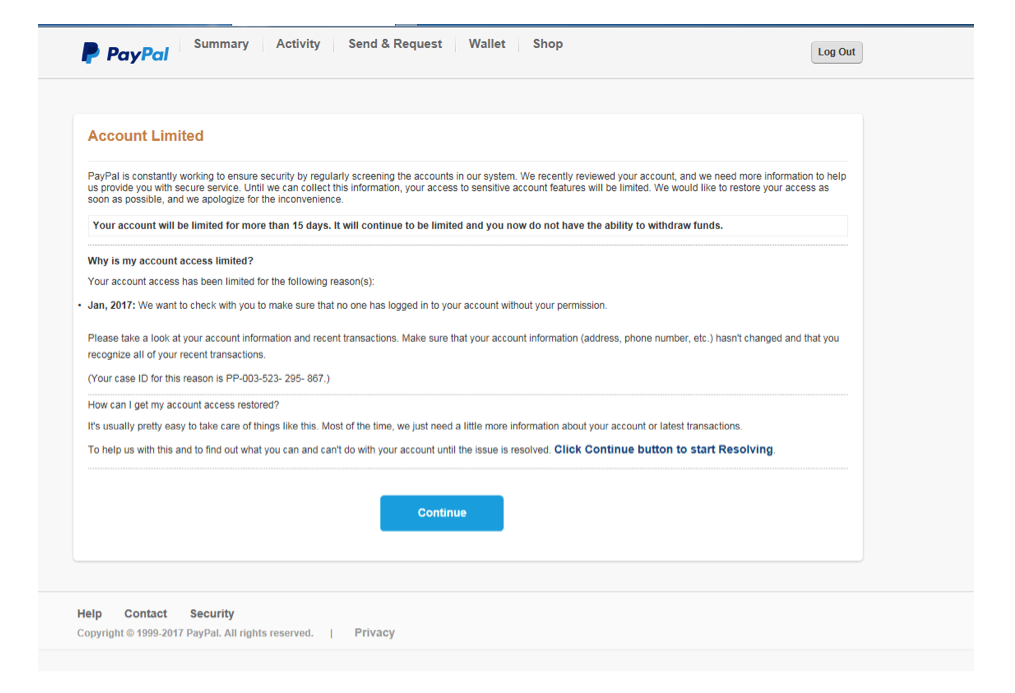
Here they present a sense of urgency along with more frightening scare to try to coerce you into giving the attackers more information. If you click “Continue”, you are taken another page asking for even more targeted information, which could aid the scammers in their attempts to steal your identity:
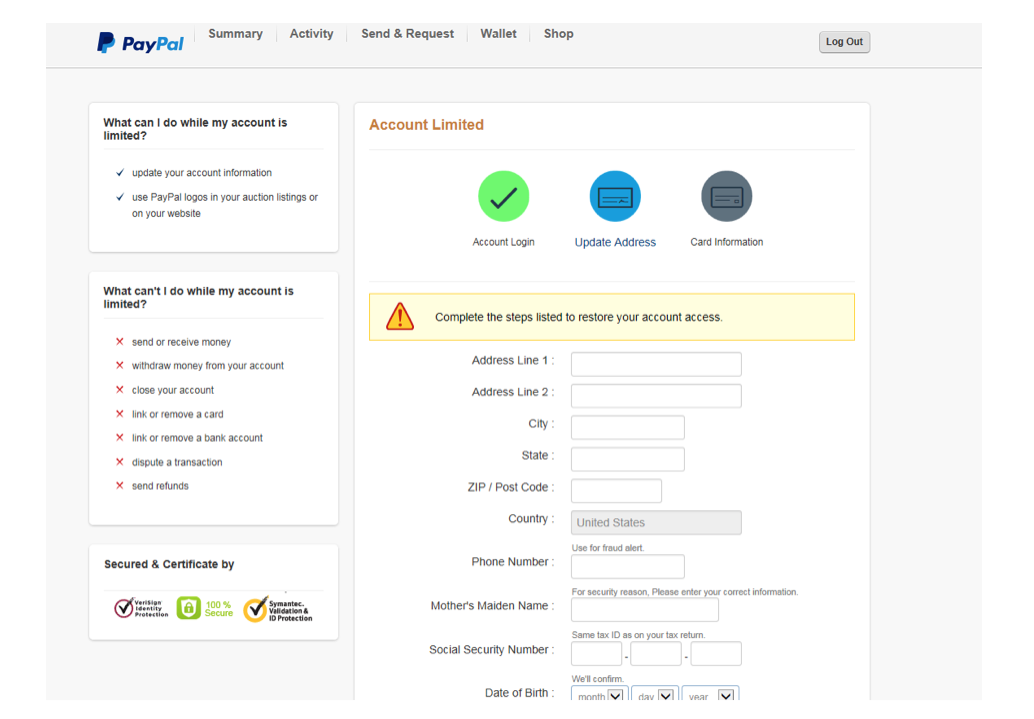
Notice they are even asking for your Social Security Number, which would only apply in the US, but then ask you what country you’re in. Also, they continue the sense of urgency stating you will be unable to interact with PayPal until you give them the information requested.
It’s easy to see how users could be fooled by such a campaign, but we hope this information can be used to raise awareness, should someone you know encounter campaigns like this in their inbox.
If you’re concerned about PayPal security, you should log directly into PayPal.com itself and update your security settings, and if you know someone who has fallen victim, the first step should be to change their PayPal password before more damage occurs.
Whether you’re a PayPal user or not, keep in mind that cybercriminals are spending more and more effort to make their phishing websites look exactly like the real vendors’. As has been heavily reported recently, Gmail users were recently hit with a sophisticated phishing scam that fooled even savvy users due to its ability to mimic a legitimate Gmail login prompt. We are likely to see more phishing campaigns targeting users of well-known sites.
How to protect yourself
First, do not click links or open attachments in unsolicited email—if email supposedly from e.g., PayPal, says you have a problem, open a new browser tab or window and log directly onto PayPal by typing in the web address.
Second, if you get such an alert while you are browsing, verify that the URL in the address bar looks as you would expect—if the alert appears to come from PayPal, be very suspicious if the address bar doesn't start out http://www․paypal․com/ or https://www․paypal․com/. Instead, go directly to the website by typing in its address.
Third, since phishing becomes more of a problem when the same password is utilized across multiple sites and services, consider deploying two-factor authentication (2FA). By requiring a one-time password generated by a user’s smartphone as a second form of authentication, 2FA helps block unauthorized access. Our blog WeLiveSecurity covers what two-factor authentication is and why you need it here.
To learn more about social engineering techniques such as phishing and how to protect your business, download ESET’s tech brief, Social Engineering and Why It Happened to You.




