We are pleased to present our annual report Windows exploitation in 2016. In this latest version of our report, we offer a fresh look at modern security features in Windows 10. The report, as usual, contains information about vulnerabilities that have been fixed in versions of Windows still supported by Microsoft, as well as exploitation trends for Windows and Microsoft Office.
We discuss several other issues in addition: first, the measures that Microsoft calls mitigations offer a powerful approach to preventing exploitation of various types of vulnerability. Windows 10 has introduced some new types of mitigation that are already used in Windows system components and web browsers. This topic is discussed in more detail.
Second, our report also includes a range of information about firmware security and considers security features that have been introduced both in hardware and in modern Windows versions. Also, a special section is dedicated to data that were released by the Shadow Brokers hackers and that are presumed to belong to the famous Equation Group.
Other information is also included in the report:
- Statistics about vulnerabilities fixed in Microsoft-supported versions of Windows, its components, web browsers and the Office suite.
- Information about the types of updates issued, what this tells us about exploitation trends, and how these 2016 statistics compare to 2015.
- A detailed look at exploit mitigations in recent Windows versions, including, CFG, KASLR and Virtualization Based Security.
- Information about the security effectiveness of major web browsers and the use they make of internal Windows mitigations.
- A separate section about the exploitation of legitimate third-party drivers to obtain SYSTEM privileges on an OS.
- Information about new EMET mitigations.
In the figure below are statistics relating to vulnerabilities that have been fixed. It is interesting to note that the number of vulnerabilities fixed for the web browsers Internet Explorer and Edge and for Windows user mode components (UMC) is roughly the same. Many vulnerabilities were fixed in drivers and the Windows kernel too: for example, Win32k and kernel mode drivers.
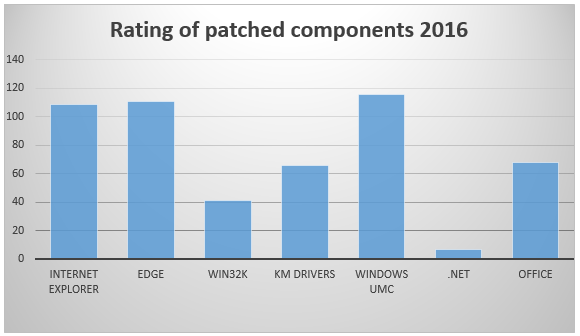
Further, as you can see in the chart below, the most frequently updated component is Windows UMC. Attackers can use unpatched vulnerabilities for remote code execution or to elevate privileges of malicious components, when they successfully gained access to a system.
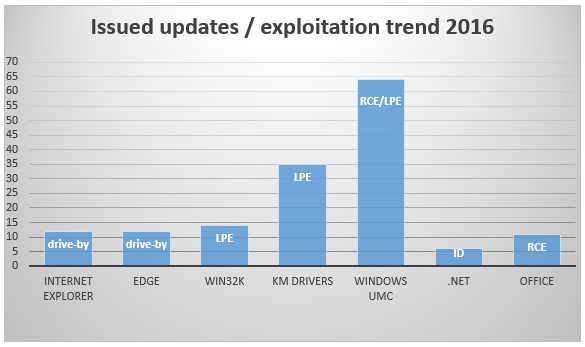
We want to remind users once again about the importance of security updates for software, OSes and PC firmware. We believe that Microsoft and other software vendors are trying to issue patches for critical vulnerabilities quickly; also, they are introducing new security features for blocking exploits actions proactively.




