On the morning of Friday August 12th, ESET researchers noticed a huge outbreak of a new Spy.Banker variant, detected as Spy.Banker.ADEA. It happened at around 12pm CET.
This new variant is similar to previous ones used by other banking trojans in South America. During execution, the malware checks if the system’s settings are in Portuguese and proceeds with the injection of the banker’s payload.
The banking trojan spreads along with two modified versions of a popular utility software, which are used to extract usernames and passwords from browsers (Chrome, Firefox, Internet Explorer, and Opera), as well as credentials for local email clients like Outlook. For that, it uses emails with attached files that contain a variant of JS/Danger.ScriptAttachment, whose purpose is to download and execute other malware in the system.
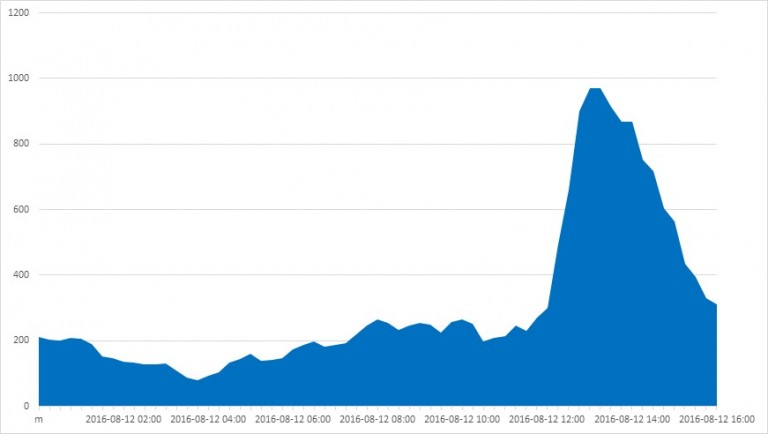
Figure 1: Outbreak of JS/Danger.ScriptAttachment in Brazil, on Friday August 12 at 12:00 CET.
JS/Danger.ScriptAttachment is the signature under which ESET detects some variants of the popular trojan downloader Nemucod. Trojan downloaders of the Nemucod family are used to spread several types of malware, including ransomware and now, on a massive scale in Brazil, banking trojans (they are also used for fraud).
Nemucod was particularly related to ransomware propagation, although we recently detected its use serving an ad-clicking backdoor.
Among the top threats in Brazil during July, trojan downloaders came in first place. As for Spy.Banker.ADEA, the banking trojan downloaded by Nemucod, Brazil stands as the main target.
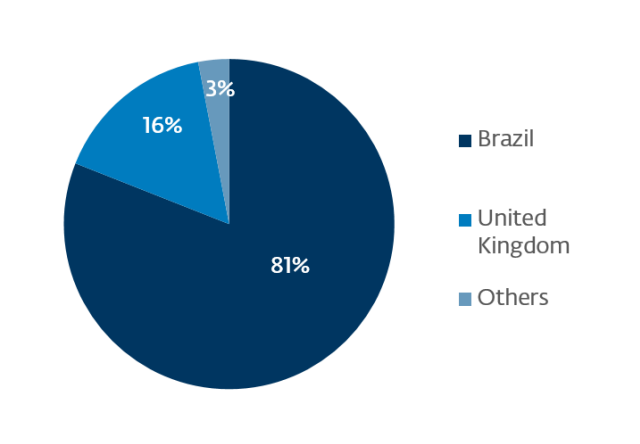
Figure 2: Main countries affected by the banking trojan Spy.Banker.ADEA
How to protect yourself?
As we explained in previous articles about this threat, staying safe has a lot to do with file extension blocking and identifying, so emails with .EXE, *.BAT, *.CMD, *.SCR, and *.JS attachments should be blocked. We also advise setting the system to show full extensions, to avoid dual extension spoofing cases and, naturally, use a reliable security solution.




