Before the release of the Android version of Prisma, a popular photo transformation app, fake Prisma apps flooded the Google Play Store.
ESET researchers discovered fake Prisma apps of different types, including several dangerous trojan downloaders. The Google Play security team removed them from the official Android store at ESET’s notice. Prior to that point, Prisma copycats reached over 1.5 million downloads by fans.
Prisma is a unique photo editor released by Prisma labs, Inc. First released for iOS, it received excellent ratings among users on iTunes, the Apple app store. Android users were eager for it and many couldn’t wait to see it on Google Play where Prisma’s release was scheduled for July 24th, 2016.
As with many other popular apps on Google Play in the past, fake versions flooded the store before the official release date, riding the wave of user impatience.
Fake Prism apps’ functionality
Most of the fake Prisma apps found on Google Play didn’t have any photo editing functionality; instead they only displayed ads or fake surveys, luring users into providing their personal information or subscribing to bogus (and costly) SMS services. Some actually had very basic photo editing functionality but mainly served the user a stream of pop-up ads or displayed scareware activity to persuade the user the device was infected with malware.
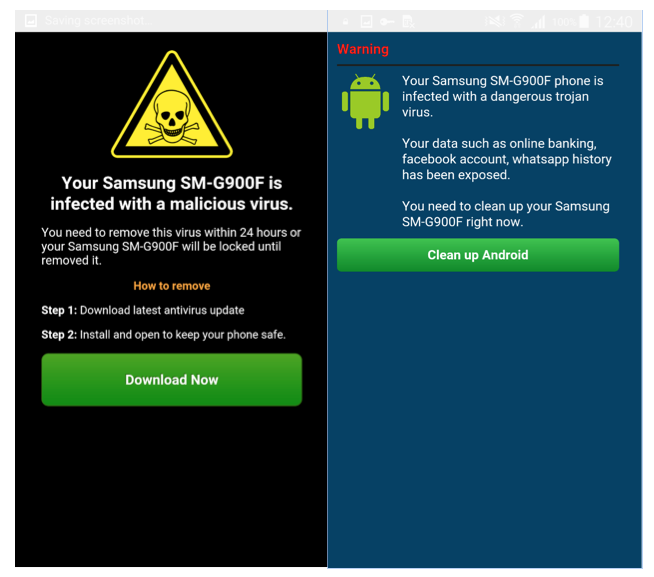
Figure 1: Scareware activity displayed after launch
The most dangerous fake Prisma apps found on Google Play before the (genuine) Prisma app release were the trojan downloaders detected by ESET as Android/TrojanDownloader.Agent.GY. Contrary to their counterparts with their annoying ads and surveys, these trojans work behind the scenes hiding their icons from the device.
They would send device information to the C&C server and on request, download additional modules and execute them. When we replicated this infiltration, the trojan downloaded and executed an additional module stealing sensitive information such as phone number, operator name, country name, language and so on. However, downloaded modules may have had different functionality implemented.
Among the five trojan downloaders discovered on Google Play, two have phishing functionality implemented that could probably be executed via the downloaded module. Displaying a fake request to update the device’s operating system to Android 6.0, users are lured into entering their Google account credentials into the fake login form.
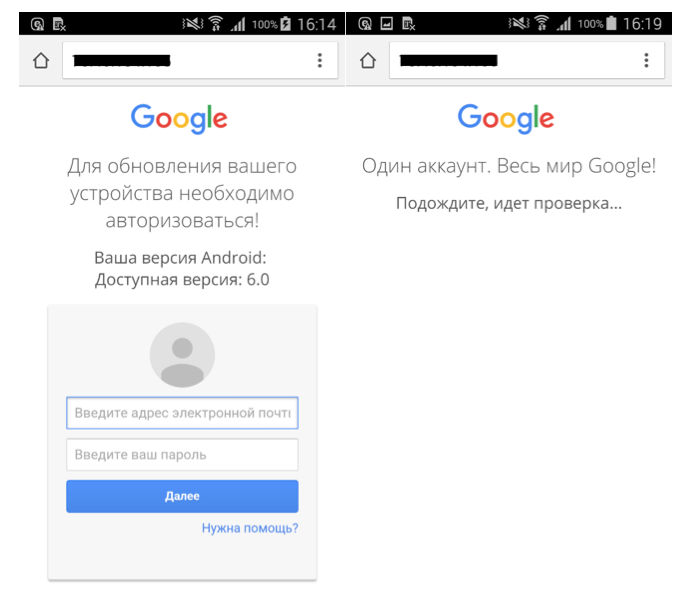
Figure 2: Phishing activity
Text translated:
“Для обновления вашего устройства необходимо авторизоваться!
Ваша версия Android:
Доступная версия: 6.0”
“To update your device, you must login!
Your version of Android:
Available version: 6.0”
“Один аккаунт. Весь мир Google!
Подождите, идет проверка...”
“One account. Google whole world!
Wait, there is a check...”
Because of their download capabilities, the Android/TrojanDownloader.Agent.GY family of malware poses a serious risk to more than 10,000 Android users who installed these dangerous apps before they were pulled from the Google Play store.
Figure 3: Trojans found on Google Play
Just before the release …
Because of Prisma’s success on the iOS platform, it was clear that this app would be eagerly awaited by Android users. Such situations often attract bad guys who put out fake apps – either copycats or various derivatives, from tutorials to cheats – on Google Play to ride the wave of excitement. Using misleading icons, app names, developer’s names and/or fake reviews, they make money from displaying ads, fake clicks, money scams … or, at worst, ransomware, delivered to the victim via a downloader trojan.
In the past, we’ve witnessed a lot of cases of apps riding the wave of popularity on Google Play. The latest examples were fakes of the Pokémon Go app. Also GTA 5 fans were targeted by fake apps before the famous game’s official release, and the same pattern was observed in connection with the popular MSQRD app that arrived with numerous copycats on the Google Play store. Many other popular apps – such as My Talking Angela, Dubsmash or Subway Surfers – were preceded by copycat porn clickers.
Conclusion
Trying to download a popular app before its official release is a really bad idea as the chances of downloading a genuine app is slim while the risk of downloading a malicious copycat is large. This is true, even from Google Play, with all of the tech giant’s security mechanisms behind it. For users it’s difficult to determine whether a given app is genuine or not. Bad guys often use very similar icons, app names, subscriptions and even screenshots to confuse users.

Figure 4: Example of a fake app (right) mimicking the original (left)
Recommendations by ESET experts:
Follow the most basic rules for “Android application hygiene”:
- Download from reputable sources only
- Check user reviews and focus on negative comments (keep in mind that positive ones may be fabricated)
- Read the app’s terms and conditions, focus on permissions
- Use a quality mobile security solution
When there is hype around your desired app, then also consider the following additional advice:
- Probably, you will face copycats along with the original app so be more careful than usual
- Thoroughly check the app’s name and the developer’s name - they must fit exactly, not only resemble what you expect




