What has happened?
LeakedSource is claiming that a database of over 32 million Twitter account credentials is up for sale on the criminal underground - containing details such as users' Twitter handles, email addresses, and plaintext password.
So Twitter was hacked then?
Jumping to that conclusion too early might be unwise.
Both LeakedSource and Twitter seem to be certain that Twitter itself was not breached. Instead, it seems more likely that the credentials were scooped up by malicious code that had infected users' computers or originated from a data breach at a third-party site.
Michael Coates, Twitter's Trust & Info Security Officer, used the platform to reassure users yesterday...
...and later followed up with a blog post:
We've investigated claims of Twitter @names and passwords available on the “dark web,” and we’re confident the information was not obtained from a hack of Twitter’s servers.
The purported Twitter @names and passwords may have been amassed from combining information from other recent breaches, malware on victim machines that are stealing passwords for all sites, or a combination of both. Regardless of origin, we’re acting swiftly to protect your Twitter account.
Twitter says that anyone whose credentials were exposed has now had account access blocked as a precautionary step, and that emails have been sent to users containing instructions on how to reset their passwords.
Ok. So maybe Twitter wasn't hacked. But are the stolen Twitter account credentials legitimate?
It's unlikely that all the passwords listed in the database will allow hackers to break into the associated Twitter accounts.
Whether that is because the details are incorrect or some of the data is stale and out-of-date is unclear - but if users were using the same password on different online accounts associated with the same username or email address they could continue to present a risk.
The truth is, however, that we simply do not know what proportion of the passwords listed in the database is accurate. The only company that can really confirm the quality of the stolen data is Twitter itself.
 What would be wrong (and commit a crime of unauthorised access in many countries around the world) would be to take the database and test each password against its associated account.
What would be wrong (and commit a crime of unauthorised access in many countries around the world) would be to take the database and test each password against its associated account.
For that reason, LeakedSource had to resort to manually contacting 15 of those people listed in the database to verify if it did include their real Twitter password. All 15 replied that the data was accurate.
In the statement published by Twitter today, the company reaffirmed that it had not been breached, but notably failed to give a number for just how many accounts had had their credentials exposed:
"In each of the recent password disclosures, we cross-checked the data with our records. As a result, a number of Twitter accounts were identified for extra protection. Accounts with direct password exposure were locked and require a password reset by the account owner."
In other words, Twitter is declining to say just now many Twitter accounts have been put at risk as a result of the credentials database being distributed in the computer underground, but at least a "number" of the 32 million credentials were valid, and would have allowed unauthorised users to hijack accounts.
Haven't a whole bunch of celebrities had their Twitter accounts hacked in recent days? Is that related?
You mean like Mark Zuckerberg, Kylie Jenner, Katy Perry, Keith Richards, George Harrison, Chelsea Handler, and Twitter co-founder Evan Williams? (I could go on...)
Yes, there have been a lot of high profile Twitter hacks of late. How much of this is because of password reuse and the recently reported mega-breaches at sites like LinkedIn, MySpace and Tumblr, or as a result of the credentials currently being offered on the computer underground is unclear.
So what *is* clear?
It's clear that not enough people are taking their account security seriously. That means having unique, hard-to-crack passwords for every online account you have (a good password manager can assist you in this).
LeakedSource has revealed the most common passwords in the database that is circulating, and it makes for predictably depressing reading.
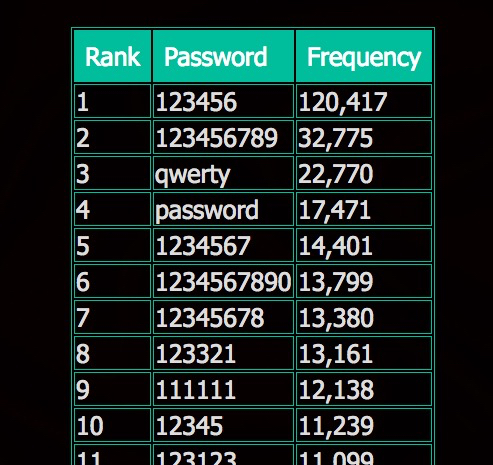
Passwords of this weak quality as this are as strong as tissue paper.
But more than that, sensible account security means enabling two-step verification (2SV) or two-factor authentication where available to benefit from a higher level of protection than relying on passwords alone.
Twitter calls its version of 2SV "Login Verification" and it requires users to not only give a username and password to connect to their site, but to also enter a one-time-password which is either sent to them as an SMS message to their mobile phone, or via a smartphone app like Google Authenticator.
The principle is that even if hackers come to learn your password, chances are that they don’t have access to your mobile phone and so will still not able to access your account.
Frankly, you’re playing a dangerous game if you have social media accounts and are not using additional layers of defence to help prevent them being compromised by hackers.




