Over 117 million emails and passwords belonging to LinkedIn members have been put online for sale, it has been revealed.
Worryingly, this trove of information is not thought to have been obtained from a recent data breach.
In fact, it is believed that the data was accessed in 2012, when the professional social network was first breached.
At the time, it was understood that just over six million members had been compromised. However, it appears that the LinkedIn data breach is far bigger than anyone thought.
In a blog post, LinkedIn said that it has “moved swiftly” to deal with this, invalidating, for example, all passwords for accounts that were created before 2012.
Further to this, users all over the world have received an email from the company, which states that it has “taken action to protect your account”.
It adds that the next time members sign in to their accounts, a password reset will be required. However, it is important to note that users must actively log out.
WeLiveSecurity tested this process, and this is what came up when it tried to sign in normally:
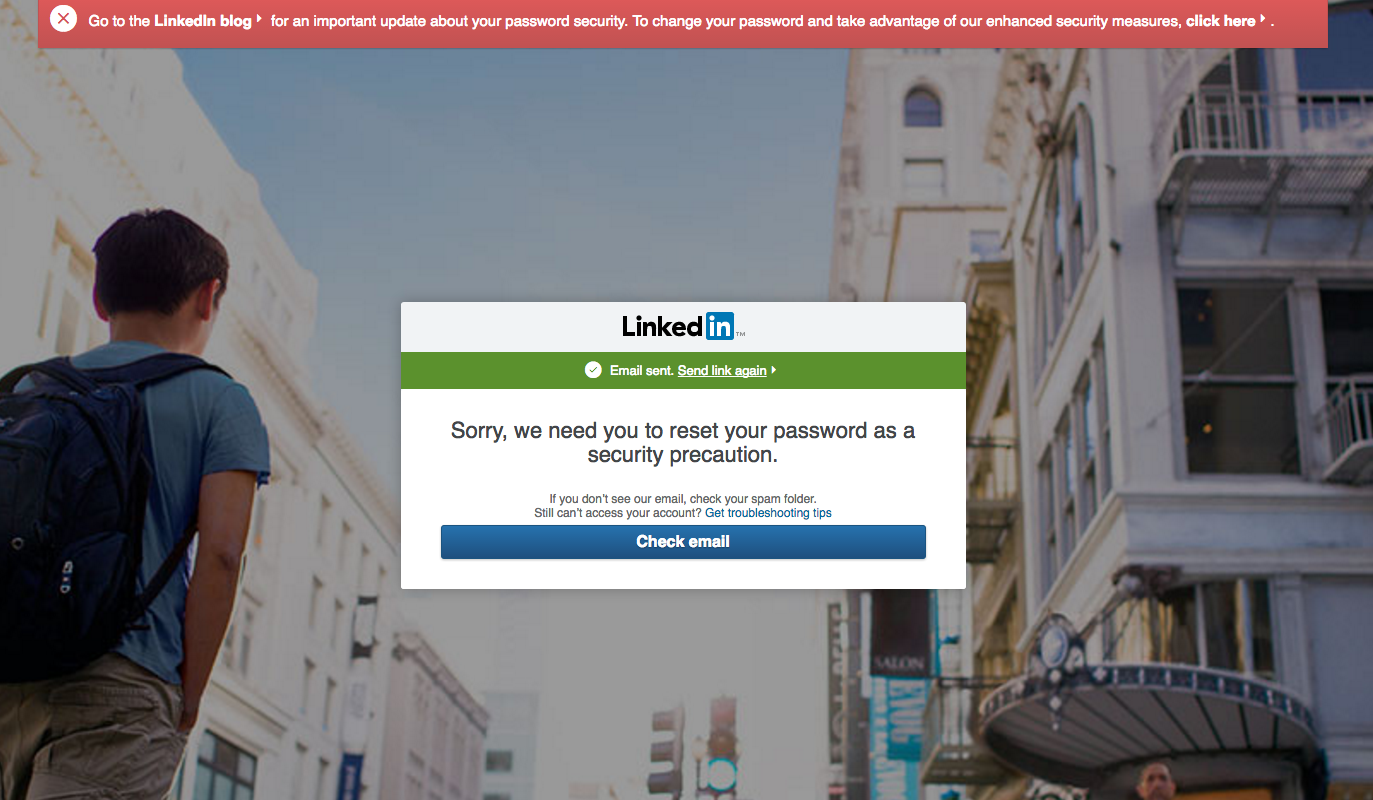
As it states, for a password reset, members need to check their email and follow the usual instructions.
WeLiveSecurity recommends that LinkedIn members opt for a strong passphrase, as opposed to a ‘usual’ password.
This quick guide offers an overview of how to do this.




