A simple trick of social engineering could result in you handing over control of your website to a malicious attacker.
To show just how easy it is to fall for a spear phishing attack that could hijack your website's DNS entries and even give hackers the ability to edit your webpages, read on...
Here is an email I received last night, claiming to come from domain name registrar and website hosting company eNom. I have redacted some of my personal contact information although it is easy for anyone to look up in the WHOIS information for my website.
Subject: eNom - IMPORTANT! Verify your contact information for GRAHAMCLULEY.COMMessage body:
Dear GRAHAM CLULEY, 03/06/2016 11:09:32 pm
Your contact information [REDACTED] & [REDACTED] , has been set as the Registrant contact for a domain name registered through eNom.
Please click on the following link to verify your Contact Information[LINK]
This notice is being sent due to the ICANN Validation to confirm the WHOIS information on your domain(s).
Please note that failure to verify the Registrant contact information will lead to deactivation of the respective domain name(s) if not completed within 3 days from the date of that action.Once deactivated, the domain names will not function until the information is verified.
Domain: GRAHAMCLULEY.COM
Support:
For any support with respect to your relationship with us you can always contact us directly using the following Information.Sales Department sales@enomsupport.com
Support Fax 425.974.4791
eNom Headquarters 5808 Lake Washington Blvd. NE, Ste. 300, Kirkland, WA 98033, USA
http://enom.com
http://enomsupport.com
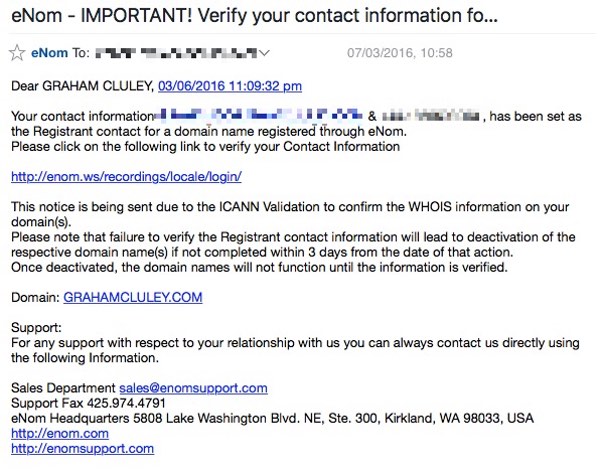
In short, the email is saying "Visit our website by clicking on this link, log in and confirm your contact information is correct."
Well, that in itself doesn't sound entirely suspicious.
But then the email continues to explain that if I dilly-dally and fail to do what they want within three daysmy website will be "deactivated". Yeowchh!
That sounds like a pretty good reason to click on the link and follow the email's instructions, doesn't it?
So, what do we find when we go to the link at enom.ws?
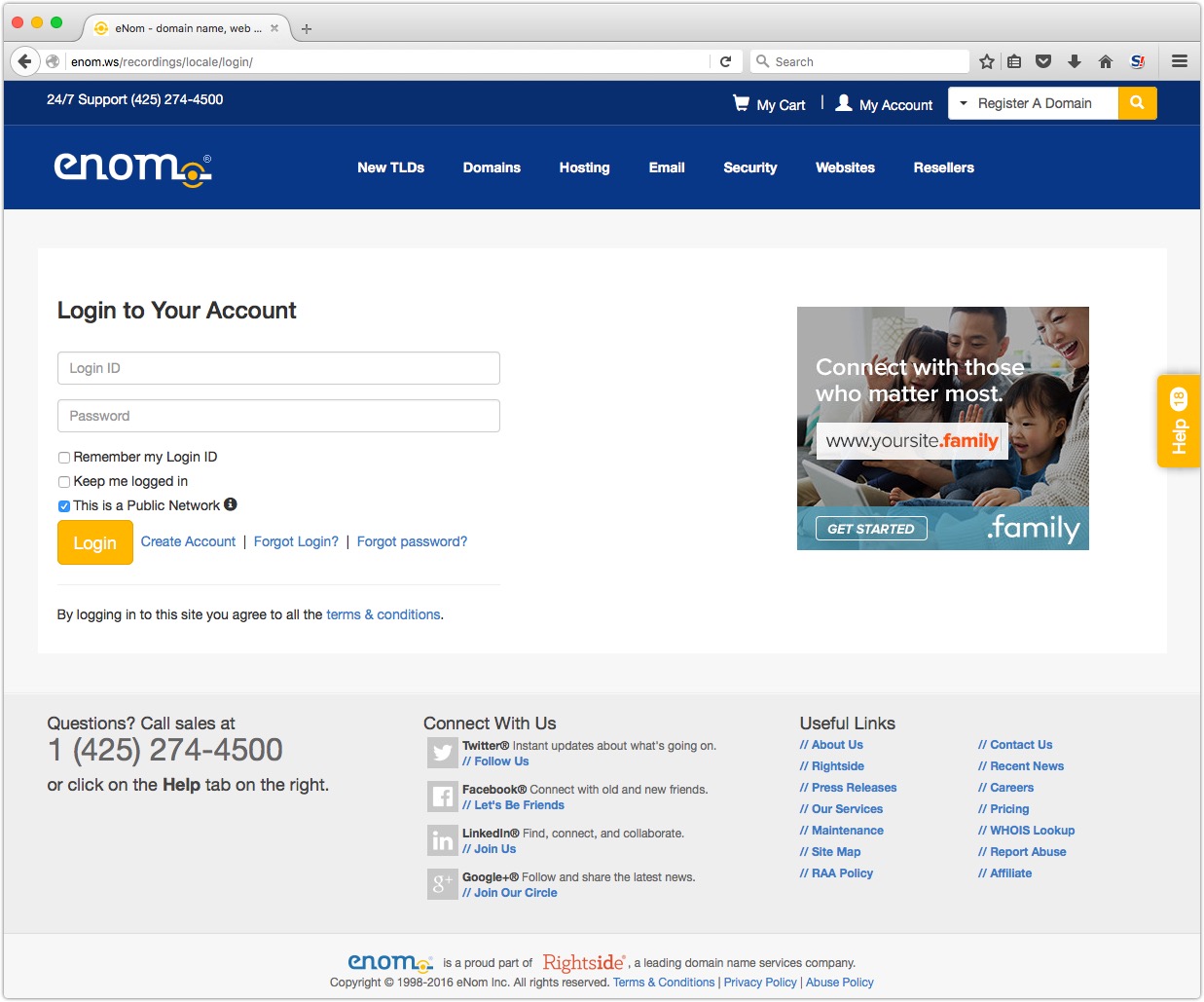
Sure enough there is a login form for me to access my eNom account, and confirm my details. It all looks very professional.
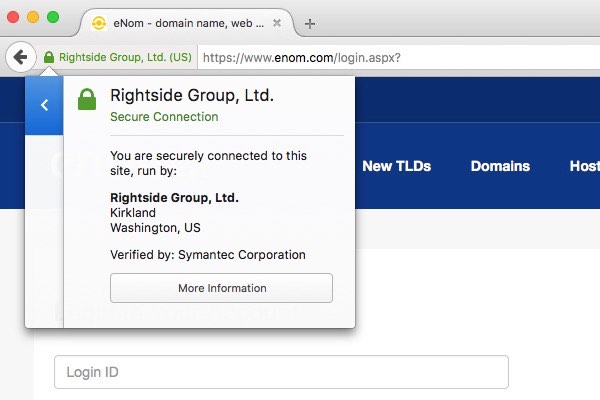
But hang on - is this site I'm looking at the same as enom.com? Can you spot any differences?
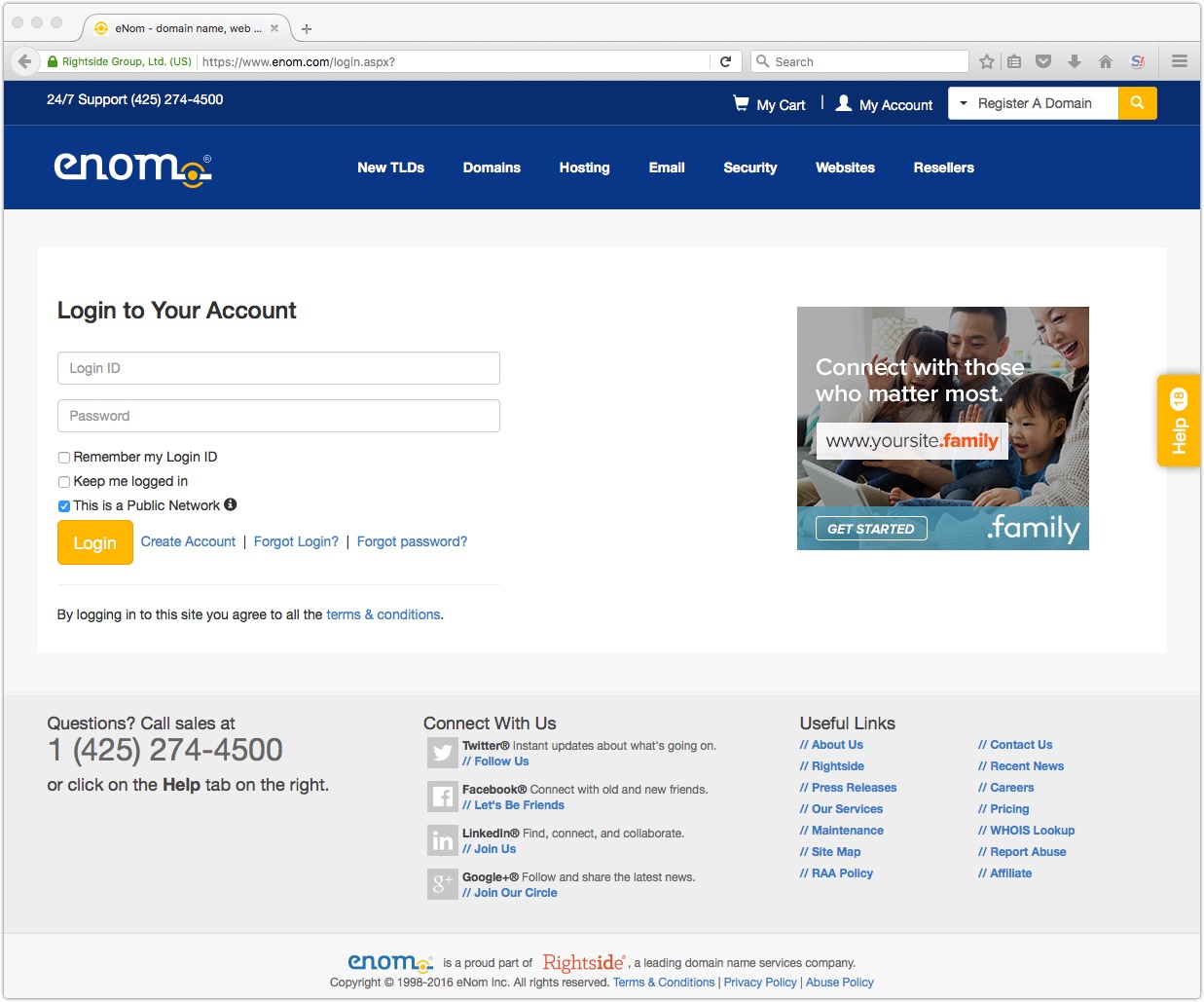
Everything is a little more obvious when you put the two sites next to each other.
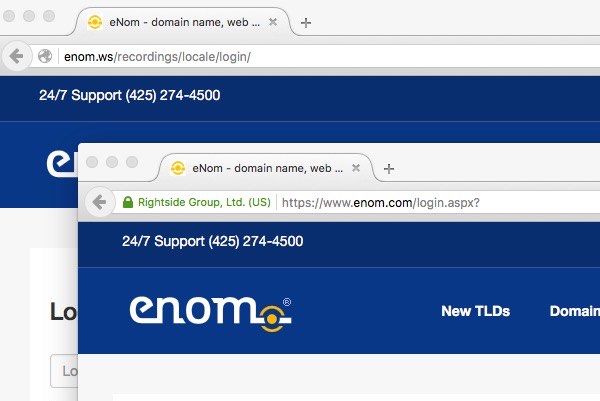
The enom.ws website linked to from the email I received is not using HTTPS in its login page - a security feature that you would expect a website that is taking account security seriously to have implemented.
On the enom.com website, however, we can see an Extended Validation (EV) certificate is being used, causing a green padlock to appear alongside the name of eNom's parent company, Ringside.
My suspicions that enom.ws is a fraudulent website become even stronger when I do a WHOIS search, and discover that the domain was only created yesterday!
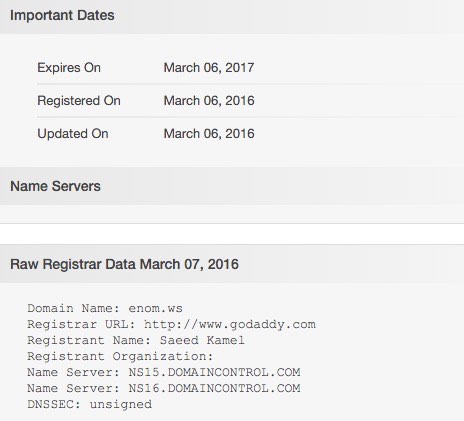
The real enom.com, meanwhile, was registered way back in the heady days of October 1997.
So, which one would you trust?
Hopefully you are learning not to click blindly on links sent to you in unsolicited emails, however keenly they might be encouraging you to do so. Instead, I hope you are going directly to the website itself and logging in to see if any actions are required.
Maybe you're going one step further like me and - if in any doubt - checking if the URL is the one normally used by the company, or has only been registered relatively recently. These clues can help you weigh up the likelihood of a link being suspicious or not.
Because if you do fail to take proper care, it would be all too easy to type your password into a phishing site and hand control of your website over to a online criminal gang.
Stay safe folks.




