In recent years, virtualization has come to be accepted within many enterprises. Its increasing popularity not only suggests a trend, but also hints at something bigger. It’s becoming an industry standard.
It’s easy to see why. For the most part, its implementation provides organizations with benefits that are mainly related to storage and processing capabilities in an increasingly shrinking infrastructure. In addition, it delivers on efficiencies, provides cost savings, is kinder to the planet and fits in perfectly with the digitalization of work. In short, it has a lot going for it.
However, before you jump in and initiate the migration process, there are a few things to consider to ensure that you maintain the reliability and availability of the services provided. Security is one such thing. Deliberating over this will help to avoid various threats and incidents that may affect and damage the operation of your virtualized system. This article highlights some key things to think about.
Security risks in virtualized environments – the hypervisor in the spotlight
"Computer threats can affect systems regardless of whether they are running in physical or virtual environments."
Computer threats can affect systems regardless of whether they are running in physical or virtual environments. However, there are environment-specific requirements that should be taken into account, related to the way in which security measures should be implemented, particularly when virtualized systems are administered by a hypervisor.
The hypervisor (also known as the virtual machine monitor) is a piece of software that can emulate the hardware on which the virtual machines operate. Therefore, it can either directly run on the hardware of physical machines or on operating systems.
Regardless of the way in which it operates, the risks are latent. We have already witnessed threats with the ability to escape the virtual environment, as in the case of Venom. Such a vulnerability may allow an attacker or a piece of malware to escape from the confines of the virtual machine environment and infect the host computer or other virtual machines running on that computer.
The vulnerability is present in the hypervisor's source code, so the breach can affect all major operating systems running on virtual environments. Basically, the vulnerability can be exploited due to a buffer overflow, after specially crafted parameter data are sent to the hypervisor controller, allowing the execution of arbitrary code and gaining access to the system.
Moreover, if the hypervisor is running on an operating system, the exposure to threats may be even higher, since it is not only able to attack virtualized systems but also the host operating system. In other words, we must deal with threats that are targeting virtualized operating systems, as well as those that attack traditional host operating systems.
Agent-based vs. agentless – which approach is better?
When you want to protect operating systems and the information hosted on virtual machines, it is possible to adopt different security approaches. The most appropriate option should be based on the infrastructure characteristics of each particular organization.
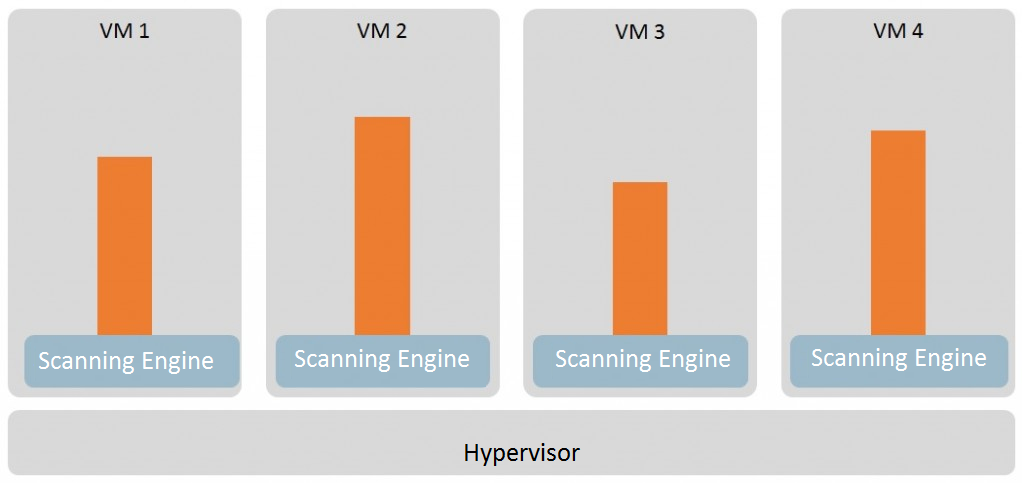
In the specific case of malware protection, a simple fix is to install antimalware software on each virtualized system, so long as the solution supports virtual environments. This approach is known as agent-based protection. However, it leads to a wasteful use of hardware resources.
As a matter of fact, having an antimalware tool installed on each system means each machine needs to have its own malware analysis and identification engine, as well as independent software and virus signature database updates. Moreover, in a virtualized environment, a simultaneous scan of all of the operating systems involved consumes a lot of resources that affect overall performance.
This is known as ‘AV storms’, a term used to describe performance problems caused by using conventional antivirus programs on virtual machines. They occur when either a scan or a virus signature database update is performed on multiple machines at the same time, which can lead to a sudden spike in resource consumption or to a performance reduction. In more critical cases, if the virtual systems overwhelm the available physical resources, they can even cause a denial of service.
Manual configuration can partly help solve this problem; but when tens or hundreds of virtual machines are involved, the task can be extremely slow. Nevertheless, there are options that can be implemented together with these solutions in order to boost performance while still offering the functions of the antivirus software installed on each virtual system. For instance, by performing an intelligent analysis that eliminates the need to scan duplicate files.
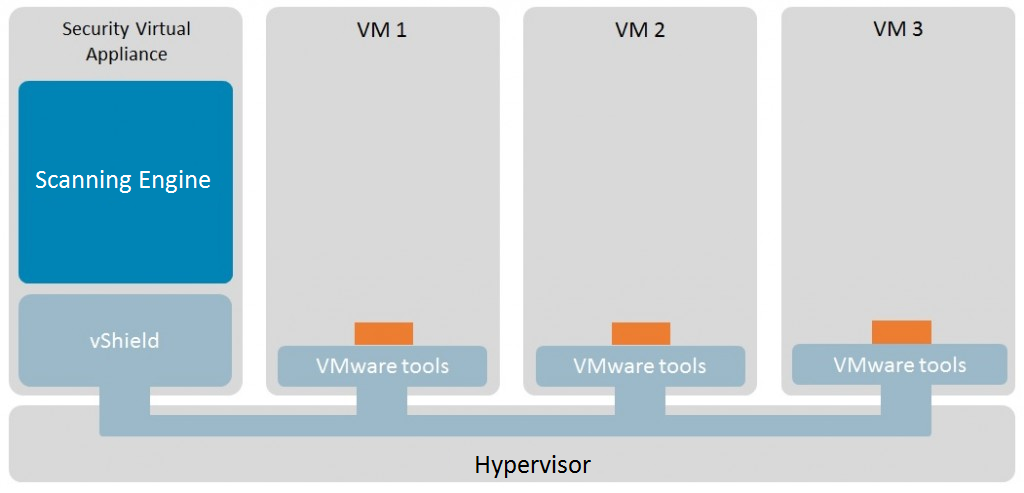
When the focus is on optimizing resources, one must consider an agentless approach. As its name implies, it does not require an agent being installed on each system. By contrast, it is based on the use of a specialized virtual machine – SVA (security virtual appliance) – which helps keep the malware scanning and identification engine running, as well as performing database updates. This is done in order to protect all the virtual machines managed by the hypervisor.
This technology – known as vShield – has been developed by VMWare, one of the most popular virtualization software vendors. The main advantage is low resource consumption, given that the basic antivirus functions are centralized in one single ‘appliance’ that protects all the virtualized systems.
Scanning tasks are optimized, among other reasons, because every newly generated virtual machine is protected almost instantly without the need to install additional software. In addition, migration or update activities are more easily performed, because they are only done on the SVA.
Furthermore, with an agentless solution, the problem of AV storms is mitigated, since the updates only take place on the SVA, while the scanning of virtual machines is carried out in a controlled manner. The Shared Local Cache technology that some solutions have prevents files on the virtual machine from redundant scanning, as once a file has been found to be clean, it is whitelisted and all other instances of that file are omitted from subsequent scanning.
Regardless of whether they are virtualized or physical systems, safety is paramount
As for security technology in virtual systems – and specifically speaking about antimalware solutions – first of all, it has to support virtualization technology, i.e. it works the same way it would on a physical system.
Before adopting a protective approach, the most important things to take into consideration are the hypervisor type that will be used, the available hardware and software resources, as well as the security needs and the chosen virtualization technology.
Finally, once you have virtual operating systems running along with antimalware tools, you must continue to apply widely recommended security measures, such as security policies or network connection filtering.
It doesn't matter whether it is a virtualized operating system, since most computer threats behave similarly in both physical and virtualized environments. The exception would be those threats designed to identify and bypass these types of environments – sometimes the malware contains mechanisms to detect whether it is being run in a virtualized environment, in which case it hides its true behavior to stay undetected.
As can be seen, both the agentless and the agent-based approaches offer advantages and disadvantages, which must be balanced when designing a protection strategy against malware in virtualized environments.




