At a recent conference on "the future of wearables" I was asked to speak about security. I think my presentation surprised some people because I didn't focus on the security of wearable devices themselves. This article summarizes what I said, with a link to my slides and some free resources you might find helpful.
 For those to whom "wearables" is a new term, it is shorthand for "wearable computing device or digital sensor." This could be anything from a smartwatch to a FitBit motion sensing bracelet to a Bluetooth-enabled button you clip to your jacket to monitor your exposure to harmful UV rays (like the prototype seen on the right). According to Statista, global sales of wearables now exceed 20 million per quarter.
For those to whom "wearables" is a new term, it is shorthand for "wearable computing device or digital sensor." This could be anything from a smartwatch to a FitBit motion sensing bracelet to a Bluetooth-enabled button you clip to your jacket to monitor your exposure to harmful UV rays (like the prototype seen on the right). According to Statista, global sales of wearables now exceed 20 million per quarter.
Most people consider wearables to be a subset of the Internet of Things (IoT). More than any other IoT technology, wearables epitomize the junction of data and people, typically generating large amounts of personally identifiable information (PII). Wearables sense, process, and transmit data about you. That data could be your location, activity, movement, vital signs, and so on.
Wearables extend from over-the-counter consumer devices to certified medical appliances. It is projected that about 70 million of these things will be shipped worldwide in 2015, doubling to over 150 million in 2019. So what security risks are there in this type of technology? Well, if you're a company making wearables, the risks are considerable, and may not come from the wearable hardware or software.
All about the PII
The biggest security risk that I see right now, both to consumers who buy wearable devices and to companies that sell them, is unauthorized exposure of the personally identifiable information associated with them. As if to make this point for me, a story broke as I was preparing my presentation for the conference, a story that is likely to become a classic example of what can go wrong. I'm talking about the VTech story.
VTech has been selling computing devices for children for many years. Early offerings were learning tools styled to look like a laptop computer. Users of these devices could buy additional modules. Over time the company built an online portal to help families make the most of their purchases, registering them and the children who used them. Later, as Internet connectivity was added to devices, the portal enabled downloads, upgrades and sharing of messages and photos.
Although VTech only recently entered the wearable space, with a smartwatch for kids, the company was an early adopter of many marketing elements that an enterprising smart device or wearable company might deploy. Unfortunately, the systems VTech used to collect and store customer data were not built securely, a fact that was recently revealed by a researcher. In other words, a lot of PII had been exposed to unauthorized access for quite a long time. News of this caused VTech shares, traded on the Hong Kong stock exchange, to plunge.
All the unwanted attention, sparked by the massive exposure of PII, then led security researchers to examine VTech products and the software associated with them. Researchers quickly found several vulnerabilities, including weak encryption in a VTech app, and the presence of a vulnerable chip in some of the company's devices.
Lasting success starts with security
If you have a great idea for a wearable device, the path forward looks a bit like this: develop the hardware, develop apps that exploit the data collected by the hardware, and build databases to track the information, including customer details. All of this is hard work and requires investment, all of which you put at risk if you don't think about the security of the data from day one, and there are two main reasons for this: the bad guys and the good guys.
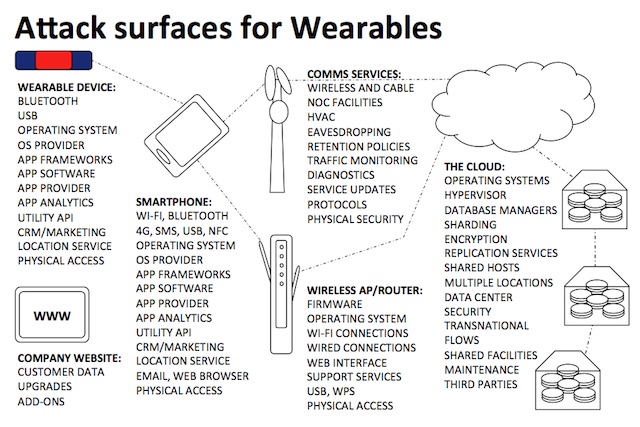
The “bad guys” are the criminals who are into technology to help themselves, not to help other people. Rather than working to create new products they work to steal data, sell stolen data, ransom data, and rent/sell tools to steal data. The data crime industry is fueled by information about people. Wearable products and companies are a source of information about people. Data criminals targets endpoints and servers. Wearables are endpoints that rely on servers for many of the benefits they deliver. In other words, the wearables business will be targeted by cybercriminals. The attack vector may be any of those shown here:
The “good guys” who are looking closely at the wearables phenomenon, at least in the US, are the Federal Trade Commission (FTC), the country’s leading consumer protection agency. Because the US does not have comprehensive data protection legislation, the role of protecting consumer data privacy has fallen to this agency. For example, when websites started to perform commercial functions such as retailing back in the 1990s, the FTC pushed for website privacy policies and appropriate protection of personal information on the web. This push took the form of workshops, advisories, warnings, and then law enforcement actions against companies that were found to be falling short of privacy and security best practices.
Companies need to be aware that the FTC has held several workshops on privacy and security in the Internet of Things space, of which wearables are a sub-sector. The FTC has also put out advice to companies on these issues – see the links in the resources at the end of the article. There are several publications available electronically and in printed form (you can order large quantities of sent to you free of charge). In other words, it is reasonable to assume that the FTC is gearing up to set some consumer privacy precedents in this space. It has already acted once, in the matter of TRENDnet’s SecurView cameras, a settlement worth reading if you are in the wearables space. At a minimum, wearables developers should be familiar with the FTC publication: Careful Connections: Building Security in the Internet of Things, the the main points of which are listed here:
- Start with the fundamentals.
- Take advantage of what experts have already learned about security.
- Design your product with authentication in mind.
- Protect the interfaces between your product and other devices or services.
- Consider how to limit permissions.
- Take advantage of readily available security tools.
- Test the security measures before launching your product.
- Select the secure choice as your default setting.
- Use your initial communications with customers to educate them about the safest use of your product.
- Establish an effective approach for updating your security procedures.
- Keep your ear to the ground.
- Innovate how you communicate.
- Let prospective customers know what you’re doing to secure consumer information.
To summarize, the bad guys are going to come looking for personal information generated or accumulated by wearables companies that they can steal. The good guys are looking for wearables companies that fail to keep their privacy promises to customers.
Resources:
- My presentation on "Wearables Success Starts with Security" at SlideShare.
- The FTC publication: Careful Connections: Building Security in the Internet of Things.
- The FTC publication: Start with Security: A Guide for Business.