Time after time in our societies, we have experienced revolutions in the way we work, which affects Industry. The first of these, the Industrial Revolution, began in Great Britain at the end of the 18th Century and was led by replacing hand tools with machine tools, technological advances in water and steam power, and advancements in iron manufacturing. This industrial revolution, though, wasn’t the only one: following that, other revolutions occurred when mass production met electrical energy, and another when IT provided automation to production in factories.
That means we have been through several Industrial Revolutions and now it seems to be the time for another. This new step will be supported by new trends such as Internet of Things (IoT), Smart Fabrics and the so-called Cyber Physical Systems (CPS). Basically, this revolution will allow the production of more connected and intelligent objects through more autonomous systems.
Where does this come from and what is its goal?
The concept Industrie 4.0 has been used by the German Federal Ministry of Education and Research to describe this fourth step into the industrial revolution, which is a project looking forward to the future of industrialization, which is being supported by the German Government by an investment of 200 million euros.
And what’s the goal of the Industrie 4.0? To create smart products through smart processes and procedures. Put in a simpler way: the ‘smartization’ of this industry. It is strongly based in the Internet of Things and Services and some of the key areas are: energy suppliers, sustainable mobility, and healthcare, among others.
What role does Security play in this approach?
According to the report of the “Industrie 4.0 Working Group”, this new industry works under a new approach where smart products have a localization point, status, historical position, and different ways to reach its final state. That means a lot of data will be created that uniquely identifies these products. As stated in the report, all this infrastructure should be protected against unauthorized access, and any kind of misuse of this information should be prevented.
"Sharing information with partners becomes increasingly sensitive as the infrastructure to protect it must extend past the production."
The information will also be shared with commercial partners in order to get the best out of the commercial chain. However, this becomes increasingly sensitive since the infrastructure to protect this information must extend past the production.
Additionally, we’ve recently seen that some of those key industries have been hit over the past few months. For example, in healthcare: the second biggest health insurer in the US, Anthem Inc., suffered a breach that could have affected 80 million customers, and the Premera breach shows that new attacks are been conducted to target sectors that might lead to the compromise of personal information or even to physical threats via compromised devices.
What hurdles do we need to overcome in order to achieve the Industrie 4.0 concept?
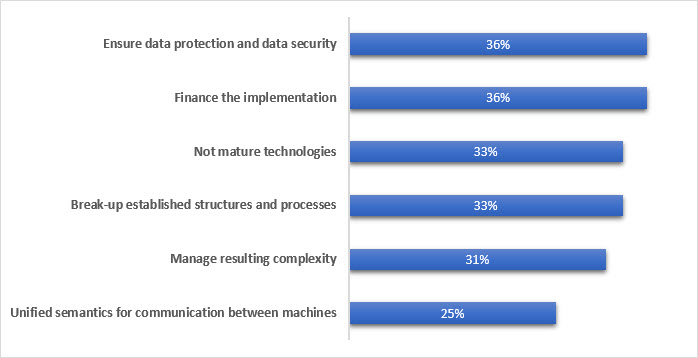
Source: IDC 2014; n=154 – Only companies that are familiar with the concept Industrie 4.0
Even though this “new Industrie 4.0” isn’t new and it happens to be well founded, there are still many hurdles to overcome before we can confirm we have reached it as a standard. As it can be seen in the IDC graphic, ensuring data protection and data Security is considered one of the two most important obstacles to overcome on the way to realizing the fourth industrial revolution. Finally, we see security concerns, along with conventional issues like financing, being considered as high-importance issues on the way to implementing the Industrie 4.0 standard successfully.
"That infrastructure should be carefully designed to support the full availability of this smartization without compromising the data."
This has many impacts in the Security Industry – as an important part of this progress is based on the Internet of Things & Services, which will require a more protected infrastructure combined with well-trained employees. The Security Industry is still struggling to raise awareness in Information Security in general terms – to combine these efforts with a new concept like Industrie 4.0 in order to provide a better support for these key sectors will not be an easy challenge, but it is essential to a healthier and more secure transition.
Known attacks on critical infrastructure
In recent years we’ve been seen attacks on critical infrastructure with different purposes: sabotage, stealing high-sensitive information for industrial espionage, and so on. Below we mention just two of these big cases that got lots of attention in the last few years, although many more have occurred.
2010: Win32/Stuxnet
Two of Stuxnet’s goals were to locate systems with Siemens Step 7 software – the industrial control systems that operated the centrifuges used by uranium-enrichment plants – and to change the speed of rotors periodically, which compromises the equipment by causing vibrations that can lead to physical damage and thus negatively affecting the enrichment process.
2012: Win32/Flamer
Flamer, sophisticated modular malware that has many similarities with Stuxnet, implements complex logic, and some parts of the main module use the same source code as Stuxnet. However, at 20 megabytes, it is several times larger than Stuxnet (less than 1 MB) – and parts of additional operations in its code was written in Lua, a scripting language normally used by game developers; other differences made Flame a unique piece. Some researchers even claimed that it was the most complex malware ever seen.
What can we do?
Besides of having IT Security laws that protect critical infrastructure for example, there are some measures to be taken regarding how the security of the information exchanged in the factories will be managed. One fundamental principle in the Industrie 4.0 is the smartization of the Industry, which involves creating smart products and processes followed by storage and processing of large amounts of information. That infrastructure should be carefully designed to support the full availability of this smartization without compromising the data. Endpoint protection, authentication methods and encryption will probably be some of the major topics considered over the next few years to help this emerging industry become the Secure Industrie 4.0.




