Whenever ESET malware researchers discover a new interesting attack, a new piece of malware, or an old threat evolving in an interesting way, we share the news on this blog. Every once in a while, though, we stumble upon something that stands out, something that doesn’t fall into the “common” malware categories that we encounter every day – such as ransomware, banking trojans, or targeted attacks (APTs) – just to name a few of those that are currently causing the most problems. Today, we’re bringing you one of those uncommon threats – a trojan devised to target players of online poker.
The last time I wrote about poker-related malware, it was about PokerAgent, a trojan propagating through Facebook that was used to steal Facebook users’ logon credentials, credit card information and the level of Zynga poker credit.
Today, we’re bringing you news about Win32/Spy.Odlanor, which is used by its malware operator to cheat in online poker by peeking at the cards of infected opponents. It specifically targets two of the largest online poker sites: PokerStars and Full Tilt Poker.
Modus operandi: Malware takes screenshots of the infected opponent
The attacker seems to operate in a simple manner: After the victim has successfully been infected with the trojan, the perpetrator will attempt to join the table where the victim is playing, thereby having an unfair advantage by being able to see the cards in their hand.
Let’s explain each of those steps in a bit more detail, as uncovered through our analysis.
Like a typical computer trojan, users usually get infected with Win32/Spy.Odlanor unknowingly when downloading some other, useful application from sources different than the official websites of the software authors. This malware masquerades as benign installers for various general purpose programs, such as Daemon Tools or mTorrent. In other cases, it was loaded onto the victim’s system through various poker-related programs – poker player databases, poker calculators, and so on – such as Tournament Shark, Poker Calculator Pro, Smart Buddy, Poker Office, and others.
Once executed, the Odlanor malware will be used to create screenshots of the window of the two targeted poker clients – PokerStars or Full Tilt Poker, if the victim is running either of them. The screenshots are then sent to the attacker’s remote computer.
Afterwards, the screenshots can be retrieved by the cheating attacker. They reveal not only the hands of the infected opponent but also the player ID. Both of the targeted poker sites allow searching for players by their player IDs, hence the attacker can easily connect to the tables on which they’re playing.
We are unsure whether the perpetrator plays the games manually or in some automated way.
In newer versions of the malware, general-purpose data-stealing functionality was added by running a version of NirSoft WebBrowserPassView, embedded in the Oldanor trojan. This tool, detected by ESET as Win32/PSWTool.WebBrowserPassView.B, is a legitimate, albeit potentially unsafe application, capable of extracting passwords from various web browsers.
Communication with its C&C via HTTP
The trojan communicates with its C&C, the address of which is hardcoded in the binary, via HTTP. Part of the exfiltrated information, such as the malware version and information identifying the computer, are sent in the URL parameters. The rest of the collected information, including an archive with any screenshots or stolen passwords, is sent in the POST request data.
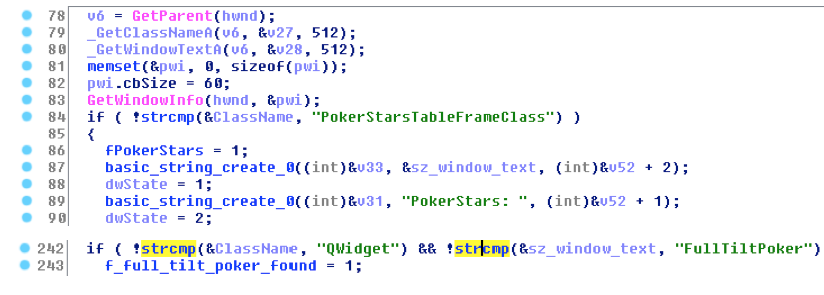
The screenshots from IDA Pro below show the parts of the malware code that search for PokerStars and Full Tilt Poker windows:
 Largest number of detections comes from Eastern European countries
Largest number of detections comes from Eastern European countries
We have observed several versions of the malware in the wild, the earliest ones from March 2015. According to ESET LiveGrid® telemetry, the largest number of detections comes from Eastern European countries. Nevertheless, the trojan poses a potential threat to any player of online poker. Several of the victims were located in the Czech Republic, Poland and Hungary. As of September 16th, there have been several hundred users infected with Win32/Spy.Odlanor: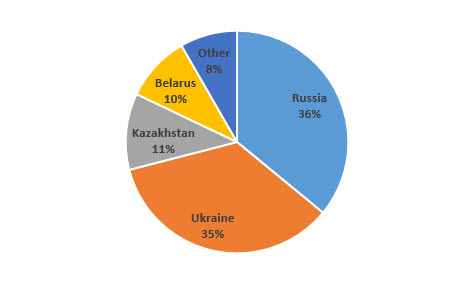
SHA1 hashes
18d9c30294ae989eb8933aeaa160570bd7309afc
510acecee856abc3e1804f63743ce4a9de4f632e
dfa64f053bbf549908b32f1f0e3cf693678c5f5a
Special thanks to Miro Babiš for the analysis.





