The fallout continues from the actions of a group calling itself the Impact Team that last week dumped data stolen from the Canadian company Avid Life Media. Most of the data pertains to people who showed an interest in the Ashley Madison website, which Avid marketed as means to enable affairs. One of the key concerns for people who provided information to that site is that their interest in it will be made public, possibly impacting their professional and personal lives.
For a short while there was some small consolation in the fact that the bulk of the data was not accessible on the “normal, regular web” but that is changing rapidly. The data that was stolen can now be obtained without visiting the "dark web" although anyone attempting to download it faces numerous risks. Not least of those risks is getting more code than you bargained for, as you can see from this ESET Smart Security alert:
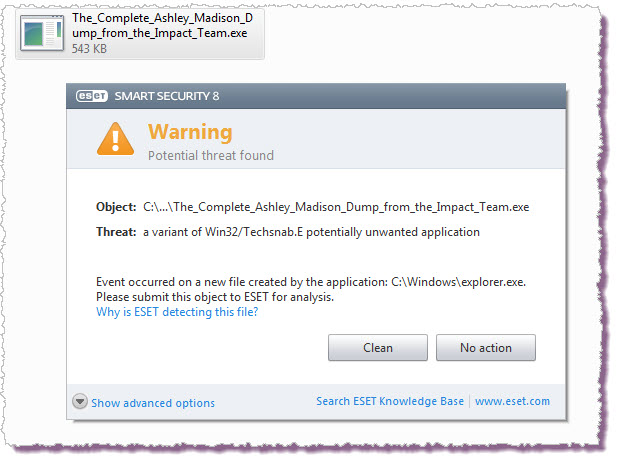 Despite that, there will be a lot of people getting access to this data in the coming weeks, and as ESET security researcher Stephen Cobb points out, this exposes individuals to blackmail, extortion, and other risks, both personal and corporate. Says Cobb, "This illegal data dump represents a bonanza for scam artists of every stripe, from every corner of the world; we are going to see everything from phishing emails to blackmail attempts, against a range of different parties, not just people who signed up at the site."
Despite that, there will be a lot of people getting access to this data in the coming weeks, and as ESET security researcher Stephen Cobb points out, this exposes individuals to blackmail, extortion, and other risks, both personal and corporate. Says Cobb, "This illegal data dump represents a bonanza for scam artists of every stripe, from every corner of the world; we are going to see everything from phishing emails to blackmail attempts, against a range of different parties, not just people who signed up at the site."
Some signs of this are already appearing. Internet security journalist Brian Krebs has documented in a recent blog his conversation with Rick Romero, information technology manager at the “virus free” email provider VF IT Services, who told him that criminals were attempting to utilize his service to blackmail Ashley Madison members. One such message read:
Hello,
Unfortunately, your data was leaked in the recent hacking of Ashley Madison and I now have your information.
If you would like to prevent me from finding and sharing this information with your significant other send exactly 1.0000001 Bitcoins (approx. value $225 USD) to the following address ...
Sending the wrong amount means I won’t know it’s you who paid. You have 7 days from receipt of this email to send the BTC [bitcoins].
If you need help locating a place to purchase BTC, you can start here …
Another example of a blackmail attempt was highlighted by CoinDesk, an online news provider that specializes in bitcoin and other digital currencies. One of its readers - and someone who had signed up to Ashley Madison - forwarded an email he had received from an extortionist. Similarly, they were given a week to respond:
Unfortunately your data was leaked in the recent hacking of Ashley Madison and I now have your information.
If you would like to prevent me from finding and sharing this information with your significant other send exactly 2.00000054 bitcoins (approx. Value $450 USD) to the following address ...
Anyone receiving such emails has been advised to contact the police, especially if they have any real concern that they are genuinely being blackmailed - i.e. they believe the threat is real - and that may eventually be a victim to fraud.
As for anyone who feels inclined to make light of the scale and scope of the Ashley Madison fallout, Cobb suggests they read this blog post by Troy Hunt, a security researcher who has for years provided people with a safe way to check if their email address was compromised in breaches, from Adobe to Forbes and beyond. Hunt is now being flooded with messages from people who see that their address is among those in the Ashley Madison dump. Many are seeking help. Hunt warns readers against going near any website or service that offers to remove your records from the data dump: that is simply not possible. He also notes, as have others, that Avid apparently allowed anyone to sign up people to the site, without verifying identity or even email. In other words, being "on the list" is not really evidence of anything.



