A software engineer is urging Facebook to fix a data security loophole he discovered by mistake a few months ago.
Reza Moaiandin, technical director and co-founder of UK-based SEO company SALT.agency, recently said that this flaw could leave the social network at risk of being compromised.
Writing for the company’s official blog earlier this month, Mr Moaiandin explained that as a consequence of this defect, hackers could “decrypt and sniff out Facebook user IDs using one of Facebook’s APIs in bulk”.
Consequently, this would provide them with access to personal information belonging to Facebook users, including their name, telephone number, location and profile picture.
The expert continued by saying that as a result of this loophole, hackers would be able to bypass the hashed ID by directly communicating with Facebook’s GraphQL, a query language that was created by the tech giant in 2012.
“By using a script, an entire country’s … possible number combinations can be run through these URLs, and if a number is associated with a Facebook account, it can then be associated with a name and further details,” Mr Moaiandin elaborated.
“This could be a huge phishing problem if no limit is created. The communication with those APIs needs to be pre-encrypted and/or other measures need to be taken before this loophole is discovered by someone who could do harm.”
The software engineer has already contacted Facebook about the matter, which he initially did at the time of the discovery (April 2015). The Facebook engineer that got back in touch with him said that he was unable to “reproduce the behaviour” himself, meaning he was unable to comprehend the technical details of the problem and how it should be fixed.
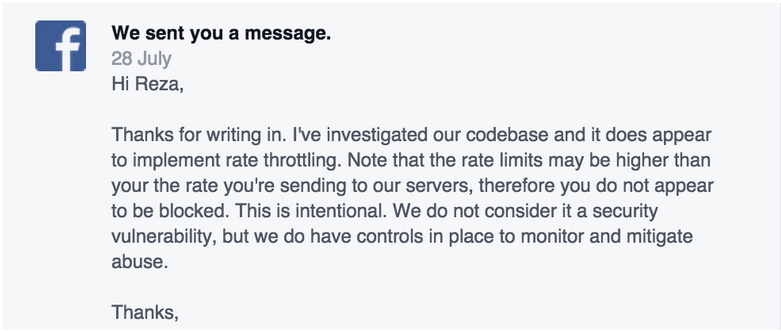
Nothing more came of this, and a few months later, in July, Mr Moaiandin contacted the social network again. This time, however, the discovery appeared to be dismissed as a serious security concern:
For now, nothing more appears on the horizon regarding this loophole, at least from Facebook's perspective. In the interim, Mr Moaiandin says he will update users if any further action is taken or, if indeed, an attacker does exploit the flaw.