In mid-April 2015, ESET’s Laboratory in Latin America received a report on an executable program named "Liberty2-0.exe" detected by us as Python/Liberpy.A. It was a keylogger, a threat that undermines the security of a system by reporting all keyboard events (keys the user presses), as well as mouse movements, to a server controlled by the attackers.
The preliminary threat analysis strongly suggested that it had been developed in the region, triggering two fundamental questions: Is there a 1.0 version? What is the scope of this attack?
Based on the name of the threat, we decided to look for indicators related to Liberpy, and found in our records another executable program with virtually the same name "Liberty1-0.exe", but detected as Python/Spy.Keylogger.G. The first variant appeared in mid-August 2014, providing important clues about the origins of this campaign, which were later confirmed by statistics and detections.
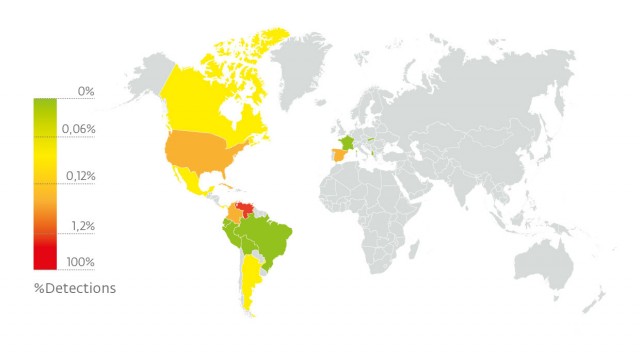
According to ESET Live Grid information, 98% of detections of these threats were in Venezuela, and based on the words and language found in the comments into the threat, we confirmed that this malware was aimed primarily at users in this country. At this point, the situation was more than clear; Liberpy was an operation aimed at users of a Latin American country in order to steal information from its users.
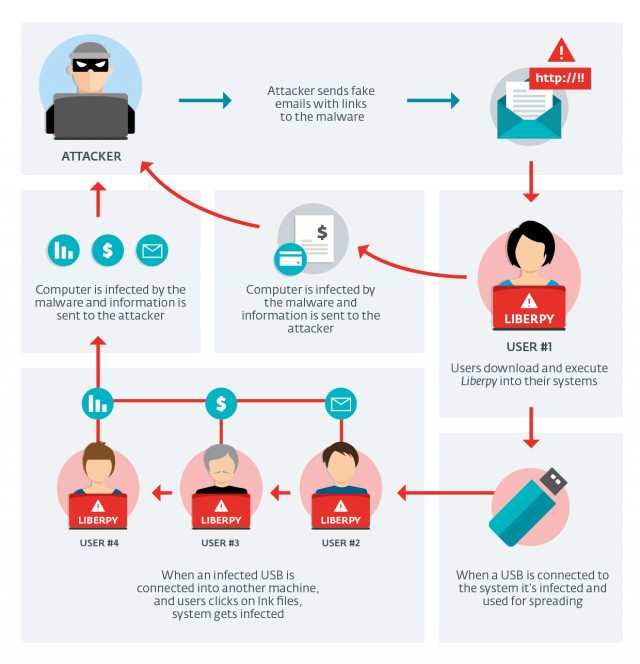
Liberpy was a HTTP based botnet, that stole users' information and that were spread via USB devices, and compromised more than 2000 systems in only a few months. Various Liberty’s campaigns began by sending potential victims fake e-mails containing attachments appearing to be package-tracking "software". Infected users began to join the botnet, and became new propagation nodes via infecting USB devices connected to their computers.
Attackers do not only rely on their fake email campaigns; Liberpy also continues to infect systems through techniques similar to those used by other malware families such as Win32/Dorkbot, JS/Bondat and VBS/Agent.NDH among others. This propagation mechanism -- hiding all files on a USB, and replacing them with shortcuts -- has been common in the region at least since 2011, and remains one of the main propagation vectors of malware via USB devices.
We observed that cybercriminals devoted their efforts to certain types of victims; in particular it seemed that their targets were users in a specific country or countries. When classifying the IP addresses that connected to our sinkhole, a total 2,047 bots were identified, out of which 1,953 were from Venezuela:
This paper will explain what Liberpy was capable of and how it managed to steal information from users in Venezuela, and some other countries in Latin America. Learn not only how to understand how Liberpy malware works, but also learn how to protect yourself from these kind of attacks.