An ingenious team of Israeli security researchers at Tel Aviv University have discovered a way to steal secret encryption keys using a gadget so small it can be hidden inside some pita bread.
The device has been named, with a clear sense of humour, Portable Instrument for Trace Acquisition (PITA).
The researchers who have published their findings online, explain that they have developed the small PITA device that can pick up the electromagnetic radio signals emanating from a PC, tell whether the PC is idle or not, and in many cases distinguish the "different patterns of CPU operations and different programs."
The researchers say that, on some computers, they can:
"distinguish between the spectral signatures of different RSA secret keys (signing or decryption), and fully extract decryption keys, by measuring the laptop's electromagnetic emanations during decryption of a chosen ciphertext."
To which I say, yoinks!
The research team say that it is possible to identify when the computer is playing a game and other activity, displaying characteristic patterns of radio activity on a spectrogram, but it's clearly file decryption which is raising the most alarm.
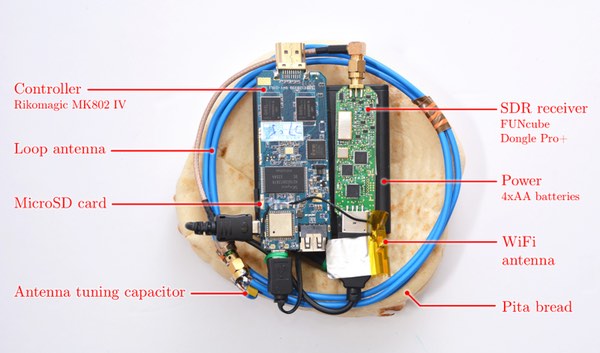
A targeted attempt to steal encryption keys would work like this.
The attackers would send a carefully-crafted encrypted message via email to the target. With the PITA device in place, monitoring the signals produced by the computer during decryption of the message, the secret crypto-key would be calculated.
"We successfully extracted keys from laptops of various models running GnuPG (popular open source encryption software, implementing the OpenPGP standard), within a few seconds. The attack sends a few carefully-crafted ciphertexts, and when these are decrypted by the target computer, they trigger the occurrence of specially-structured values inside the decryption software. These special values cause observable fluctuations in the electromagnetic field surrounding the laptop, in a way that depends on the pattern of key bits (specifically, the key-bits window in the exponentiation routine). The secret key can be deduced from these fluctuations, through signal processing and cryptanalysis."
The good news is that the gadget has to be very close to the target PC. In fact, even when the setup is enhanced with more powerful antennae, the researchers only found that they could steal the crypto-keys from a distance of 50 centimetres, although it is possible to imagine that more expensive (and bulkier) hardware could extend the range further.
What is impressive is not so much the stealing of the encryption keys, but the fact that they devised such a simple, cheap and portable way to do it. Oh, and the fact that they called it PITA.
The researchers say that they have disclosed details of the attack to the developers of GnuPG, and worked with them to develop suitable countermeasures. As a result, GnuPG 1.4.19 and Libgcrypt 1.6.3 (which underlies GnuPG 2.x) are said to be resistant to the key extraction method described in the researchers' paper.
Learn more in the researchers' technical paper: "Stealing Keys from PCs using a Radio: Cheap Electromagnetic Attacks on Windowed Exponentiation".




