We don’t seem to have talked here about tech support scams lately, but that doesn’t mean they’ve gone away, as the continuing flow of comments to our previous articles on the topic bears witness. (Indeed, I still get the occasional call of this type, along with PPI scams and offers to help me with my claim for a road accident I haven’t actually had.)
Since this is going to be quite a wide-ranging article, here’s a brief reminder of how the basic scam works, extracted from the paper presented by myself, Martijn Grooten, Craig Johnston and Steve Burn at Virus Bulletin in 2012.
The basic scam is very simple. The victim is cold-called and persuaded that that he needs to pay the company the caller represents to fix a problem with his computer remotely. The scammer claims to call on behalf of an authoritative entity, usually some kind of service provider and more often than not Microsoft.
[…]
When (or even before) the victim is persuaded that the call is genuine, the scam caller either claims that they have been notified of problems with the victim’s system, or offers to check that system for problems. More often than not, the pitch involves the misuse of system utilities … to ‘prove’ the existence of problems. It also usually involves persuading the victim to allow the scammer remote access to the system in order to check its condition and, in many cases, to install software that will ‘fix’ the problem.
Many of those comments are from people who’ve been contacted by scammers and have come across our articles while searching for more information. Clearly, despite the amount of attention we (and, more recently, other people in the security industry) have given to this type of scam, there are many people who’ve not previously experienced it, or did not immediately realize that it’s a scam.
Scamming the Scammer
Other comments come from people who are well aware of the scam, but have taken advantage of being cold-called to waste the scammer’s time and be generally infuriating (from the scammer’s point of view).
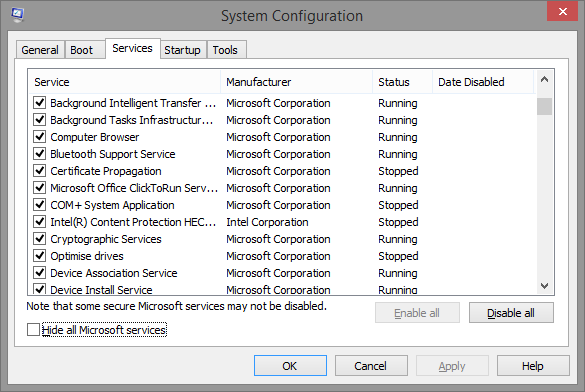
My colleague Aryeh Goretsky recently called my attention to an article by journalist Steve Ragan centred on a recording of a conversation he had with a scammer. I’ve heard many such recordings in recent years, but this one includes an interesting gambit for persuading the victim that his system was under attack. I’ve seen and written about many such gambits, of course, but this one was new to me. The scammer asked him to run the System Configuration utility msconfig. When he did so, the scammer told him to click on the Services tab and told him that the services showing a ‘Stopped’ status were a symptom of the ‘problem’ with his computer.
Actually, it’s perfectly normal for some services to be stopped because they aren’t needed under the configuration of Windows that you choose to run, or because it isn’t necessary for them to run all the time. Unsurprisingly, Ragan was quite aware of this, but took the opportunity to indulge in a little scammer-baiting.
Dangerous Business, Scammer-Baiting…
When the scammer realized that she’d been led up (or down) the garden path by someone who was well aware of the fraudulent nature of the call, she tried to tell him that she was able to hack his system because she knew its CLSID. A waste of an empty threat, since she could hardly expect a security journalist not to know what a CLSID really is (even if it is misspelt in the article), and that it can’t be used to identify a specific system, let alone expose it to attack. Still, it appears he got off lightly: a Canadian who declined to avail himself of a scammer’s services was threatened with assassination, while there have been reports of other threats of rape and violence like this. In fact, a less aggressive scammer advised me several years ago to take a holiday right now, as I would soon be dead, so this particular anti-sales tactic isn’t all that new.
Here are a couple of related links:
http://www.geek.com/news/listen-to-a-microsoft-tech-support-scammer-threaten-to-kill-a-man-1617055/
Here be Dragons: the Scammer’s Revenge
The sort of damage that we tend to see reports of ranges from direct financial loss due to payment for unnecessary and sometimes damaging installations, through the installation of intentionally malicious software and theft of sensitive data, to the intentional trashing of the system, or rendering it inaccessible using some form of encryption in the manner of classic ransomware. One way in which support scammers often impact seriously on victims happens when a victim is incautious enough to allow access to their PC, then decides not to pay for the scammer’s help. I’ve seen frequent reports where this scenario has arisen and the scammer takes advantage of the remote connection to trash the system. A tech-savvy scammer – and they do exist, unfortunately – can render the victim’s system unusable. The scammer may even booby trap the system immediately he gains access, either in order to trash it if the victim doesn’t play ball, or so that he can get access to the PC (and the victim’s credit card) again in the future.
We get many comments from people who actually let the scammer have access to their PCs, wanting to know what to do now. Unfortunately, this isn’t like a single malicious program (or variant) where we usually have a good idea of what the program will do as long as we’ve seen and analysed the same variant. While the underlying scam is fairly standardized, the actual ‘payload’ is not. The scam is carried out by many different organizations and individuals, using different scripts, and if victims do let them get access to their PCs, we can’t say what they did in a particular instance.
- They may steal files and data for further misuse and abuse, though stories of this actually happening are hard to verify. (Apart from credit card data, of )
- They may delete files and programs. There are even reports of scammers misusing the Windows utility Syskey so as to lock the victim out of his or her own system, though it’s hard to say how widespread this unpleasant gambit really is. (That’s a topic I plan to return to in the near future.)
- They may add programs to the system that are essentially harmless and even useful, though in such a case they’ll usually be software you could get for free elsewhere, or else pirated versions of legitimate software that may or may not work without proper licensing.
- They may install malware, though again I don’t have reliable reports of cases where this has actually been done. But clearly the possibility exists.
This being so, we can’t tell you what has been done in a particular case: there is no one-size-fits-all step-through solution we can offer to all those people whose PCs have been exposed, and we can’t offer one-to-one support through the blog. ESET customers can of course get advice by contacting ESET Customer Care from another computer or mobile device, via the web during business hours, or at any time by email using this form. If you’re not a customer but are in North America, you might want to consider ESET Support Services.
If you use a product from another vendor, of course, you might well want to contact that vendor’s support services. Free products don’t usually come with free support – except through user forums, where the quality of advice given may range from excellent to – well, not-so-excellent – but you may be able to pay for one-to-one help. If you don’t have a security product at all, your options are very limited. You might, of course, use one of the free online scanners around – ESET’s is here – but the range of actions the scammer might have taken is pretty wide. Even top-flight for-fee security software can’t be guaranteed to diagnose any and all problems a scammer might have introduced. Consider finding a reputable local tech service to come and take a look at it (preferably in person).
However, the best way of avoiding problems like these is to avoid giving access to your PC to anyone you can’t – or at least shouldn’t – trust. And the problem will be easier to deal with if you already have the means to boot from external media. It’s also worth considering using a third-party registry backup tool to supplement System Restore. And, of course, make a point of backing up files and data regularly: Aryeh Goretsky’s paper Options for backing up your computer is a good starting point for understanding how to set about this.
Reporting Support Scams
While it’s always interesting to read of the experiences our readers have had with support scammers, we’re not in a position to investigate specific incidents in depth. There are other organizations interested in your experiences, though, as a means of gathering background information, although not necessarily with a view to investigating a single incident.
Microsoft looks through the microscope
One commenter on one of my earlier blogs on the subject pointed out that tech support scams can be reported to Microsoft’s report/survey page here. As Ken W. points out, apart from the direct financial impact on their victims, the fact that the scammers more often than not claim to represent Microsoft (or a company somehow allied with Microsoft), which is bad for the real Microsoft’s reputation, so it’s not surprising that the company is seeking further information about known scammers.
Quite rightly, the report form discourages anyone filling it in from including ‘sensitive or personal information – such as your credit card number….’ but does ask in question 1 for information including the name of the company and individual making the phone call, and the company’s URL, phone number and street address. In fact, it’s common for support scammers – indeed, scammers in general – to be evasive about these details or simply to lie about them, but even if some of the information is false, it may be of forensic value.
The second question asks when the ‘communication with the company’ took place, which I suppose may also be use if any of the identifying information is of value.
The third question asks whether the contact was unsolicited – a cold call, as is most often the case with reports that reach me – or whether the victim (or intended victim) initially made contact with the company carrying out the scam. This is an interesting attempt to broaden the scope of investigations into support scamming. My own research into this area has mostly been confined to cold-call scamming, since that’s the kind of support scam that’s mostly reported to me, and I have only limited time to spend on scouring the Internet for web sites and Facebook pages that act as additional lures for the unwary, though Virus Bulletin’s Martijn Grooten, Malwarebytes’ Steve Burn and I did look in some detail at some such sites for a blog published in 2011 and a couple of subsequent conference papers (of which Craig Johnston was also a co-author) for Virus Bulletin* and CFET**.
Unfortunately, such lures continue to flourish. In an article by Greg Keizer for Computer World, North Carolina computer consultant Nat Garrison Jr. was quoted as saying that three of his customers who fell for the scam had initiated it.
Two of them were trying to get technical support for Microsoft Outlook and the third was trying to add another license to his Office 365. All three of them used Google to find the phone number for Microsoft's technical support. They all got connected to someone with a strong Indian accent who wanted to remotely connect to their computers.
And the scope of the attack continues to broaden. Johannes Ullrich described for the Internet Security Center an example of typosquatting where mistyping http://login.microsoftlonine.com instead of http://login.microsoftonline.com redirected the potential victim to a site that popped up a warning along the lines of ‘WARNING Time Warner Cable Customer: your Internet Explorer browser and computer may be compromised by security threats’ and gives a number to call. (Ullrich assumes that the scam site ascertains the victim’s ISP by looking up his or her IP address with whois.)
Perhaps it’s worth quoting a passage from that article with Martijn and Steve, though its scope is narrower:
What is clear is that there are a lot of companies and sites out there offering support, and even if they aren’t the same people making scam cold-calls – which in some cases seems pretty unlikely – they are basing their appeal to visitors to their web sites on bona fides that are pretty difficult to verify. It’s not that difficult to set up one or more new Facebook accounts and pages: unfortunately, there’s no simple and foolproof way of telling which accounts might be “dummies” set up purely to promote a product or service. Even where an account looks genuine and well-used, it’s perfectly possible that the victim of a rogue service has been persuaded to “Like” it as part of the scam, and anyone could fake a testimonial using stock photos and made-up names. Unfortunately, it also seems likely that we’re increasingly going to find Facebook pages and blog pages with scraped or even frankly deceptive content similarly used to add credibility to web sites whose authenticity doesn’t stand up to scrutiny. But it’s harder to trace and verify the accounts behind social media sites than it is a registered domain, and even those have their challenges.
The next question asks (more or less) whether ‘the person you spoke with’ claimed to be representing Microsoft. Clearly, this is a concern for Microsoft in terms of bad PR, but it also gives them some leverage when it comes to identifying rogue partners and affiliates as well as companies claiming falsely to be affiliated. As long, that is, as the information given in answer to question 1 is reliable.
Question five asks whether the scammer accessed the possible victim’s PC remotely. While the scammer can sometimes convince the victim that he knows enough about that victim’s PC – for example by quoting the so-called ‘unique’ CLSID ZFSendToTarget=CLSID{888DCA60-FC0A-11CF-8F0F-00C04FD7D062} – to be able to convince him there’s something wrong with the system, it’s more or less essential in terms of performing the ‘service’ for which the scammer will charge. It’s also pretty essential when it comes to answering the 6th question: “Did the person you spoke with remove, stop, disable or cause any malfunctions on your computer?” You can, of course, persuade someone from a distance to cause damage or compromise to their systems, but the opportunities for profiting directly from a compromise on a PC to which you have no access are somewhat limited. By contrast, having remote access offers the ability to fix a problem (or, more likely, put up a pretence of fixing a problem) by editing or removing files, installing programs which may or may not be useful, and generally giving the impression that you’re doing something worth paying for. And, of course, for deliberately causing damage.
Actually, the wording may sound rather eccentric here: if the scammer removes, stops or disables malfunctions (as opposed to causing them), maybe they deserve your money. However, question seven asks ‘Since your interaction, does your computer function better, worse, or the same?’, apparently considering the possibility of a justifiable charge, and the next question asks whether the respondent paid for the service, whether or not they tried to get a refund. The final question asks whether you’re willing to be contacted for further information.
SANS and Sensibility
This isn’t the only attempt that has been made to get information about such scams, of course. SANS has had a report form up for some time - https://isc.sans.edu/reportfakecall.html - and it’s quite interesting that the questions posed there are significantly different, though they aren’t always clearly expressed:
- Was the call automated or did a person call you?
The options for a response are actually ‘automated’, ‘personal’, or Sms (sic): is the distinction here between a direct call from a real person, and an automated message ending in a prompt to hit a key so as to be contacted by a real person? In fact, support scam cold calls often use autodialling to ring several numbers at once: however, in my experience a live scammer connects with the first person to pick up and the other lines are dropped. There are, however, lots of scams that include automated messaging: in the UK, PPI scams frequently use an automated message to lure the victim into responding. Irritatingly, the use of a standard message often means that you actually have to contact them in order to find out which company you should complain about. I haven’t encountered a support scam where the same issues arise, but perhaps it’s different in the US. Clearly, there are regional differences in types of scam and telephone service provision that might a significant difference. - Was the caller male of female?
- What language did the call use?
This is interesting: it’s rare to hear of support scammers using languages other than English, and in fact there are reported instances of scammers ringing countries where English is not an official or ‘first’ language and refusing to use the language normally associated with those countries because ‘Microsoft will only let us speak English’. Quite recently we heard from a reader in Switzerland implying that the English-speaking scammer was confused because the intended victim was using a German-language version of Windows. - Did the caller have a strong accent (non native [sic] speaker)?
This question probably has a lot to do with the fact that support scams are almost invariably associated with India, and victims and commenters very frequently mention the scammer’s strong accent. It’s possible that the scammers’ preference for English has something to do with the fact that’s probably the only European language that is still an official language in some parts of India. - If the caller asked you to visit a URL, which URL was it?
Clearly a useful thing to know for investigative purposes, especially if the URL turns out to be owned by the scamming organization. Often, though, all they want is for you to connect to a site (usually legitimate) from which you can download remote access software so that they can move on to the next stage of the scam. - Did the caller ask for remote access to your system?
As already mentioned when we looked at the Microsoft form, this is pretty much a given. They might persuade you they’re genuine without access to your system, but the easiest way of providing you with a so-called service they can charge you for is to install something (which may or may not be malicious, though it often includes software which is legitimate but available for free from other sources. - Did the caller identify an organization they claimed to be affiliated with?
If they did, that’s clearly forensically useful. - [The next questions concern what information the caller asked for: credit card data in particular, but also other personal (or less personal) information.]
- What phone number did the call come from? (If you have caller ID)
Again, forensically useful as long as the number was (a) visible and (b) not spoofed. - And, usefully, there’s a free-form field as follows: Describe the call (any details not listed above, what information did you provide? What commands where you asked to execute?)
While there has been little direct information shared from the data entered there, SANS has published quite a lot about the scam in general recently.
Back in 2012, Lenny Zeltser edited an issue of SANS’s security awareness newsletter that provides a reasonable overview of the problem. Sometimes it’s too easy to get caught up in the minutiae of scammer techniques and tricks when quite simple advice is enough to enable people to protect themselves in most situations. (I’ll get back to that at the end of this article.)
Much more recently, Zeltser was one of the many people to have recorded or summarized his interaction with a scammer, and it’s a pretty useful article. For a start he refers to the increasingly common practice of finding ways to persuade the potential victim to call the scamming call centre, rather than cold-calling. This makes a lot of sense from the scammer’s point of view, since the pool of potential victims has been so over-phished by cold-callers in the past few years that many people now automatically assume that an unsolicited phone-call from someone with an Asian accent is suspicious. While we reported some time ago on the beginnings of this trend towards getting the victim to make the initial contact, this and some of Zeltser’s other articles suggest that the scam has progressed in sophistication. Among the decoy approaches he mentions are:
- The use of tweet bots to attract victims. Interestingly, he suggests that the crude nature of the tweeting used works as a filter, excluding those who are too tech-savvy to fall for the scam, and therefore saving the scammers from talking to people from whom they won’t make money, and who might even go out of their way to waste the scammer’s time. I’m not convinced that really is a deliberate strategy, but a somewhat similar hypothesis has been raised by Microsoft’s Cormac Herley with regard to 419 scammers.
- Typosquatting. (ISC diary entry by Johannes Ullrich.) Ullrich also mentions that at the time the diary entry was written, the 0800 number shown in the screenshot “will lead to a sales system trying to sell you a medial [sic] alert button if you are 50 years or older.” I imagine ‘medial’ was intended to be ‘medical’. Medical alert system scams are pretty common in the US, usually associated with ‘robocalls’ as in these two reports:
- http://www.usatoday.com/story/money/personalfinance/2013/06/09/scam-medical-alert/2397189/
- http://medical-alert-systems-review.toptenreviews.com/medical-alert-systems-how-to-avoid-scams.html
- While I’ve not seen similar scams reported in the UK so far, there are plenty of other scams that share robocalling techniques, cold calls, accommodation addresses and phone numbers with support scammers. And far too many of them target the elderly.
- And redirection of expired domains. Actually a variation on the well-worn theme of misleading pop-ups and audio messages, but no less disturbing in that it directs the victim to a malicious phone number rather than malware.
It’s not only customers who are slippery…
This conversation is particularly interesting in a number of respects.
- The scammer sounds very American, though the whereabouts of Help Desk National remains undetermined. Still, I’ve suspected for some time that the scam has been picked up and tweaked by scammers in countries other than India.
- ‘Steve’s’ evasions and refusal to be pinned down on who and where he was are typical of support scammers in India, but clearly identified here.
- He’s recommending a product called STOPzilla of which I’ve no personal experience. That doesn’t mean it’s not legitimate of course – some of the first support scammers I heard of claimed to be installing an ESET product, though if they did install them, they turned out to be cracked or pirated versions – but it’s discouraging that there is a complaints and reviews site devoted to the company.
- Misuse of Task Manager is hardly new: back in 2012 we heard of a scammer who told an intended victim that “it was a problem that CPU usage was running at 3%, and it should be running at 80%.” Here, though, Steve claimed that “Normal usage on a healthy computer should be as close to 40 processes as possible,” … “Because if that number is higher than that, that can indicate that things have attached themselves to your computer that are starting to affect your Windows functionality…” My system is currently running at 5 apps and 75 background apps, so I guess I’m in trouble. ;)
Conclusion – Some More Advice
So, I hear you ask, what about some more advice to potential victims? Here are some thoughts, some of them abstracted from previous blogs on the topic, on things that should ring alarm bells.
- Don't trust anyone who cold-calls. If you live in a jurisdiction with a "don't call me" opt-out registry of some sort, consider subscribing to it. Then, if someone calls you offering any sort of service, you have a means of assessing their honesty by their reaction to you asking them why they're cold-calling you.
- Terminating such a phone call rather than trying to find out more about it is often a highly rational approach to lessening the risks. In fact, any cold call should be regarded as suspicious until proven otherwise, and more so if it offers security advice. At the very least, verify the source and authenticity of any offer of service, and not to be panicked by warnings of immediate threat into making unwise decisions about whom to trust with your credit card details.
- If someone says you have a virus problem – or other system problem, come to that – ask them how they know. Thereare circumstances under which a service provider may have the ability to identify the owner of an infected machine, but most people -and companies – won't generally be able to do that. Or you could just put the phone down.
- If you think there really may be some truth to the call, find out exactly who is calling you. Support scammers tend to be evasive about who they really are and who they represent. But if they do give you details, don’t take their word for it. Verify. Or just put the phone down. In fact, I’m finding increasingly that scammers are more likely nowadays to terminate the call abruptly if you ask for details or question their instructions: worried, perhaps, that you might be wasting their precious time as so many of our readers have done***. Nevertheless, some still cling valiantly to their script long after anyone with a pair of neurones to rub together would have given up. I was particularly impressed with the persistence of one recent caller who continued with his script even after I led him to believe that he’d reached a fictitious computer crime unit. I think he only disconnected because I couldn’t stop laughing.
- Anyone can claim to be anyone on the phone. And if you have caller-ID, don’t take it for granted that the number you can see is genuine, even if it looks ok. Legitimate callers do sometimes withhold their numbers or simply show as International, but if they do so, it’s more important than ever to verify their identity.
- Even if they are who they say they are, that doesn’t mean their intentions are legitimate, and it doesn’t mean they have a right to call you.
Think. Why would you give access to your system to anyone who rings you out of the blue? Probably because you have one of these fraudsters on the other end of the phone trying to panic you into giving them access to your system and to your credit card. Because pressure through panic is one of the scammer’s favourite weapons. We sometimes see it said that Microsoft will never call you about a malware problem with your computer, but that isn’t strictly true, though the circumstances under which this might happen are very limited.
We do hear of ISPs contacting customers (directly or indirectly) telling them they have such a problem, and telling them that service will be withdrawn if they don’t correct it. Even under these circumstances, you shouldn’t let anyone frighten you into granting access to someone whose bona fides you haven’t been able to verify. After all, we have also heard of support scammers claiming to be an ISP or some other entity, making similar threats of service withdrawal.
What if it was you that made the initial contact? Well, how and where did you find the company you made contact with? If it was through some sort of pop-up message informing you that you have a virus and giving you a phone number to ring, there’s a good chance that you’ve been conned by the sort of web site described by Zeltser or Ullrich, as described above. Unfortunately, a guide to finding dependable local PC repair and maintenance services is way beyond the scope of this article. But certainly, it’s a job that calls for far more careful research than picking the first name that crops up on a Google search.
* My PC has 32,539 errors: how telephone support scams really work
** FUD and Blunder: Tracking PC Support Scams
***If you feel the urge to indulge in a little scammer-baiting, I strongly suggest that you don’t go as far as allowing them remote access to your machine. Some very IT-proficient people have allowed a scammer access to a virtual machine so that they’ve been able to recover the system even after he tried to trash it, but even then you need to know exactly what you’re doing.
All photographs by permission of David Harley and Small Blue-Green World