(Breach notifications, those emails and letters that "regret to inform you" criminals may have your credit card number or other sensitive information, have been delivered to tens of millions of Americans over the last 12 months. The contents of these notifications can be frightening, confusing, and sometimes just plain infuriating. Why? As the following article by guest writer Fer O'Neil explains, many states have laws that require companies to notify consumers of breaches, but few specify the content of those notifications.)
In General Terms: Remain Vigilant
That message, remain vigilant, is the direction that most American states have taken when it comes to the contents of data breach notifications, when they have any content requirements at all.
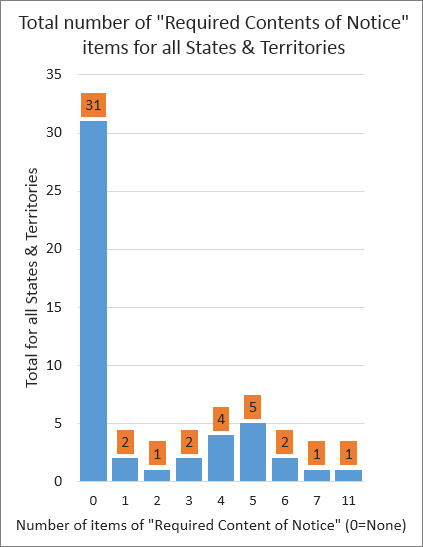 Using Intersection Inc.'s 2013 report "Intersections Consumer Notification Guide," I looked specifically at the information for the section "Required contents of notice" for each state and territory included in the report. My contention is that with all of the disparate laws and regulations concerning data breach notifications, the one aspect least addressed is the actual content of the messages sent to users.
Using Intersection Inc.'s 2013 report "Intersections Consumer Notification Guide," I looked specifically at the information for the section "Required contents of notice" for each state and territory included in the report. My contention is that with all of the disparate laws and regulations concerning data breach notifications, the one aspect least addressed is the actual content of the messages sent to users.
It seems like it would be self-evident that the content of a notification is just as important as say, who must be notified, but you can see by looking at each new data breach notification, this is clearly not so.
The first metric I looked at was the number of states and territories that had some required content of notice. I was a little surprised that 63% (31 of 49 reported) had None. The remaining 8 had an average of 2 between 1 and 11 (the majority had 4-5).
This means that for most states, they have no requirements or recommendations for what content is included in a data breach notification. The content itself is entirely left up to the company sending the notification.
For those that did have required contents of notice, I looked at the items and categorized them based on the most reoccurring elements. The table below shows that there are 5 categories of content that require notices to include the following:
- 13 to offer free credit reporting
- 4 require "Plain Language" use (California + 3 Government agencies)
- 4 require "clear and conspicuous" notices
- 9 require the notice to "describe in general terms"
- 6 require notices to advise users to "remain vigilant"
For the purpose of this post, I will not go into depth on all of these items, but I will illustrate why the current required contents are inadequate.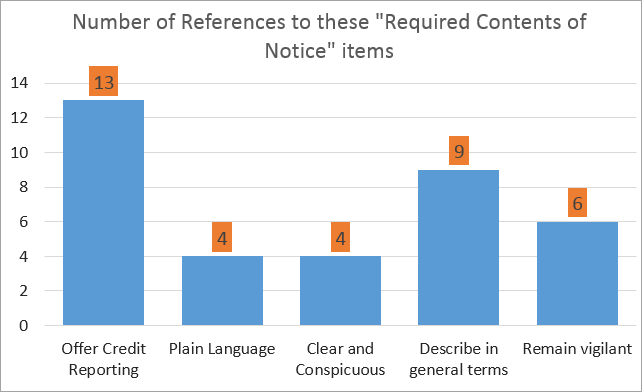
Offer free credit reporting
Although these services can help true victims step out from beneath the shadow of ID theft, the sad truth is that most services offer little in the way of real preventative protection against the fastest-growing crime in America.
Brian Krebs wrote an article that examined how effective free credit reporting services are for users affected by a data breach. While used properly and timely they can have some effect, ultimately the articles says that they "are basically PR vehicles for most of the breached companies who offer credit report monitoring to potentially compromised consumers."
Plain Language
Since there is no standard for plain language, making this a requirement doesn't hold much promise that users will receive a notification that effectively communicates the information they need to know. Furthermore, as my analysis showed, California was the only state to require plain language--the other entries were government agencies. The Federal Government has a plain language initiative, which accounts for this. However, legislating plain language use is not the same as ensuring that the notifications are written to the standard, especially as the "standard" changes from notification to notification and user to user. As I wrote previously on this topic, companies that send data breach notifications need writers that are capable of creating content that meets not only the legislative requirements, but more importantly the needs of the end users.
Observations
I have not seen any current or proposed legislation that discusses readability, formatting, or effectiveness of the content for understanding--no requirements for "quality". Instead, we are presented with requirements for companies, on their own accord, to "describe in general terms" and to advise users to "remain vigilant", whatever that placating verbiage even means.
As Congress works to enact federal legislation governing standards for data breach notifications, we would all do well to keep in mind the contents of the notices--for if you haven't received one yet, it is probably just a matter of time before you do. And when you do receive that email or visit the company's PR page, do you expect to understand what you read and have all your questions answered? If yes, how do you think this will happen?
I think the first step is to acknowledge that the content, form, and delivery of the notifications are a worthy topic of consideration, and recognizing that for effective, user-centered content, you need a writer capable of creating (and delivering) this content. Who's it going to be? I have a suggestion...
Fer O’Neil is a knowledgebase technical writer at ESET North America. He is currently working on his PhD in Technical Communication and Rhetoric at Texas Tech University. His research interests include how organizations communicate highly technical security- and privacy-related information to their customers. The views and opinions expressed in this article are those of the author and do not necessarily reflect the official policy or position of WLS nor ESET.



